Hi! Any success?
Hi, I have a raw BIOS (not RSA signed) (it’s intended for a manufacturer OEM). There is also an RSA signed BIOS. Of course they are not from HP. Perhaps these documents are helpful for your research?
Hi! I am not sure, because HP has very different way of RSA protection. HP has some signature method of protection. Every image in bios is signed with some hash protection signature S256, and the other level of protection is hashed generated previously keys, and on the top of all the hash of all keys. Also, HP has two, or three algorithms of protection, it seems like one is on EC flash in padding, is unique (it goes from factory), the next one is protecting EC firmware (updatable) and the third is for everything (updatable).
I am not expert in this, but somehow this algorithm can be reverse engineered to bring modding capabilities to bios.
Interesting, how to enable “SureStart Development (Lab) Mode” ?
00C0B6_EC START.zip (7.3 KB)
interesting code related to SureStart
function sub_46c {
stack[16] = rbx;
stack[24] = rdi;
if (rcx == 0x0) {
rax = 0x8000000000000002;
}
else {
*(rcx + 0x8) = 0x900000;
*(rcx + 0x10) = 0x1000000;
*rcx = 0xffffffffff700000;
*(rcx + 0x28) = 0x1ab000;
*(rcx + 0x20) = 0x753000;
*(rcx + 0x18) = 0xffffffffffe53000;
*(rcx + 0x50) = 0x697000;
*(rcx + 0x58) = 0x1000;
*(rcx + 0x48) = 0xffffffffffd97000;
*(rcx + 0x38) = 0x6c9000;
*(rcx + 0x40) = 0xa000;
*(rcx + 0x30) = 0xffffffffffdc9000;
*(rcx + 0x68) = 0x713000;
*(rcx + 0x70) = 0x40000;
*(rcx + 0x60) = 0xffffffffffe13000;
*(rcx + 0x80) = 0x6d3000;
*(rcx + 0x88) = 0x40000;
*(rcx + 0x78) = 0xffffffffffdd3000;
*(rcx + 0xa0) = 0x1ab000;
*(rcx + 0x98) = 0x4ec000;
*(rcx + 0x90) = 0xffffffffffbec000;
*(rcx + 0xc8) = 0x430000;
*(rcx + 0xd0) = 0x1000;
*(rcx + 0xc0) = 0xffffffffffb30000;
*(rcx + 0xb0) = 0x462000;
*(rcx + 0xb8) = 0xa000;
*(rcx + 0xa8) = 0xffffffffffb62000;
*(rcx + 0xe0) = 0x4ac000;
*(rcx + 0xe8) = 0x40000;
*(rcx + 0xd8) = 0xffffffffffbac000;
*(rcx + 0xf8) = 0x46c000;
*(rcx + 0x100) = 0x40000;
*(rcx + 0xf0) = 0xffffffffffb6c000;
*(rcx + 0x110) = 0x698000;
*(rcx + 0x118) = 0x268000;
*(rcx + 0x108) = 0xffffffffffd98000;
*(rcx + 0x120) = 0xffffffffffaf0000;
*(rcx + 0x130) = 0x40000;
*(rcx + 0x128) = 0x3f0000;
*(rcx + 0x140) = 0x3f0000;
*(rcx + 0x148) = 0x1e000;
*(rcx + 0x138) = 0xffffffffffaf0000;
*(rcx + 0x158) = *(rcx + 0x158) & 0x0;
*(rcx + 0x160) = 0x8000;
*(rcx + 0x150) = 0xffffffffff700000;
*(rcx + 0x170) = 0x5c000;
*(rcx + 0x178) = 0x1000;
*(rcx + 0x168) = 0xffffffffff75c000;
*(rcx + 0x198) = *(rcx + 0x198) & 0x0;
*(rcx + 0x1a8) = *(rcx + 0x1a8) & 0x0;
*(rcx + 0x1b0) = *(rcx + 0x1b0) & 0x0;
*(rcx + 0x1c0) = *(rcx + 0x1c0) & 0x0;
*(rcx + 0x180) = 0xffffffffff75d000;
*(rcx + 0x188) = 0x5d000;
*(rcx + 0x190) = 0x393000;
*(rcx + 0x1a0) = 0xffffffffffffffff;
*(rcx + 0x1b8) = 0xffffffffffffffff;
*(rcx + 0x1d0) = 0x698000;
*(rcx + 0x1d8) = 0x30000;
*(rcx + 0x1c8) = 0xffffffffffd98000;
*(rcx + 0x1e8) = 0x431000;
*(rcx + 0x1f0) = 0x30000;
*(rcx + 0x1e0) = 0xffffffffffb31000;
rax = 0x0;
}
return rax;
}
Hi! Any success?
None unfortunately. I couldn’t manage to get myself a programmer + a 2nd pc so I abandoned my research.
I did get the Engineering version of bios. The problem, the bios contain Engineering CPU and PCH codes. So it can’t run on normal Motherboard
N81- W25Q128FVSQ - DevEdition.bin.zip (8.2 MB)
just a thought. maybe you can try to swap ES version ME Firmware to production version via FIT and insert proper microcode.
tried, but no luck.
Microcodes are protected with RSA 256 signing
Great work over years and wish you the best to overcome the problem.
I found this thread while researching the way to edit bios for EliteDesk 800 G3
I wonder if 800 G3 is also RSA protected.
On the other hand, if algo is RSA256, isnt it possible to crack it?
Did further study as well.
Realize that HP has two different bios chip
8MB for EC and 16MB for BIOS
Raw dump can be opened with UEFITool.
Inside EC Firmware, there are lots of executable which can be analyzsed with IDA too.
I was hunting for recovery mode since this gets executed when BIOS is corrupted which makes me to believe it has to be exists on EC.
However, I couldn’t find any useful file except on very shady padding region.
Its located right after Microcode section where FIT exists.
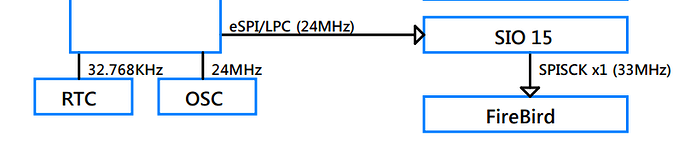
It has some SureStart strings as well as something call “Firebird” which Im not sure what it is.
I still dont know what kind of binary it is so cant really analyze properly with IDA yet but still working on it.
!! Firebird Aggressive mode !!
!! Firebird Requested G3 Reset !!
!! Firebird phase2 check !!
!! Firebird phase2 Completed with Led Blink = %d !!
!! Firebird Phase2 Finished Successfully !!
!! Firebird phase2 re-validation after BB recovery fails !!
!! Firebird phase2 Repair !!
!! Firebird phase2 Manual Recovery !!
!! Wait till S0 Firebird completes before Sx Firebird Entry !!
!! S0 Firebird completed - ignore FB results !!
!! Firebird phase4 check launched from S0 State !!
!! Firebird phase4 Completed with Led Blink = %d !!
!! Firebird Phase4 Finished Successfully !!
!! Firebird phase4 re-validation after BB recovery fails !!
!! S0 Firebird recovered BB - generate SCI !!
!! Firebird phase4 Repair !!
!! Firebird phase4 Manual Recovery !!
!! Firebird phase4 check launched from S%d State !!
!! Firebird phase4 Completed with Led Blink = %d !!
!! Firebird phase4 Manual Recovery !!
!! Firebird phase4 re-validation after BB recovery fails !!
!! Firebird Phase4 Finished Successfully !!
!! Firebird phase4 Repair !!
!! Launch Firebird to change EC_MPM! Enable:%u Disable:%u !!
!! S0 Firebird is running !!
!!! ERROR: Firebird Could not Repair BootBlock.!!!
!!Can not run Firebird P2!!
!!! ERROR: Firebird Could not Repair BootBlock.!!!
!!Can not run Firebird P4!!
!!Can not run Firebird lite eSPI Intel!!
Full Firebird AMD
Firebird Self Test requested on next boot…
Full Firebird Intel
Firebird Self Test requested on next boot…
Firebird Lite for AMD and Intel starts
Firebird busy - rejecting command %d
Firebird busy - rejecting command %d
Set Firebird Policy Rejected. EC_MPM = %02hXh CloseTrustedAPI = %02hXh
!!! ERROR: Firebird Could not Repair BootBlock. Forcing G3 Reset!!!
!!! ERROR: Firebird Could not Repair BootBlock. Forcing G3 Reset!!!
I have posted here an engineering variation of bios, with early build of SureStart, maybe someone with proper knowledge can hack it to unlock editing of bios. Your device is also using sure start. And it also has three levels of protection: 1. While controller boots and read firmware from flash, it calculates the important images of bios, if they are wrong, then it will restore it from EC rom backup/ originally EC rom is only for restore, engineering bios can work without rom SPI. 2. When cpu started and before post, it is also making some calculations. 3. final after EFI environment is executed.
Some Efi applications has access to ram addresses, which stores the keys, ec firmware has also access, but to ROM addresses, also some efi applications has addresses to keys as for bios updates.
In my opinion is best to create a virtual region of bios, which will be scanned with fake keys and fake areas, or an algorhytm reverse enginering to create a tool for any generation of keys.
I also tried to look for Datasheet of NPCE586 but unable to find it.
However, a reputable person from badcaps noted that this chip is not programmable.
Some Nuvoton EC have public information and most of them does not have internal flash memory.
This also indicates that whatever its being executed by EC, it has to be from SPI.
When you say engineering bios can work without rom SPI, do you mean by the EC 8MB SPI?
I checked the file you posted and its full 16MB bios.
What Im still unclear is, which spi gets access first, 8MB? or 16MB?
Gotta keep digging haha.
Very nice! You gonna try it?
I dont even have any HP hardware yet haha
Im just shooting in dark to see if I can have fun with HP BIOS
Have you checked last padding area from EC firmware?
Also one thing to add,
I googled alot for NPCE586 although wasn’t successful.
However, all other NPCExxx family are CR16CPlus which is RISC (not ARM)
Elitedesk 800 G3 uses NPCD315H which can also be found on other products
As usual, no datasheet or document what so ever ![]()
https://www.ssi.gouv.fr/uploads/2022/11/anssi-cible-cspn-2021_30en.pdf
Above document explains why its so damn difficult to defeat Sure Start.
Similar document can be found for NPCD315 and NPCE586 but its French.
https://www.ssi.gouv.fr/uploads/2022/11/anssi-cspn-2018_06fr.pdf
https://www.ssi.gouv.fr/uploads/2017/12/anssi-cspn-2017_22fr.pdf
Modchip type of approach may work on this case but that is out of my skillset.
Edit1
https://www.ssi.gouv.fr/uploads/2017/12/anssi-cible-cspn-2017_22en.pdf
https://www.ssi.gouv.fr/uploads/2022/11/anssi-cible-cspn-2018_06en.pdf
Haha, I managed to find eng version of report by just guessing the url.
Edit 2
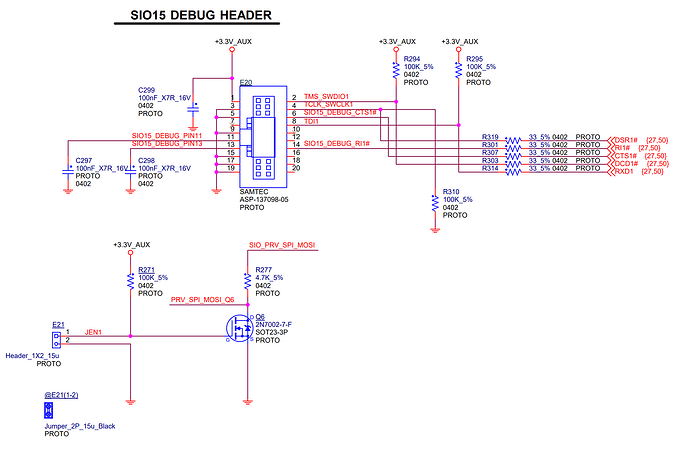
HP EliteDesk 800 G2 Schematic (Spitfire) revealed some debug header as well as unknown jumper.
Basically its NPCD315 SIO_PRV_SPI_MOSI (pin87) to GND with 4.7k ohm
For NPCE586, its PVT_SPI_MISO(pin94)
@bigguygeo
Im still waiting my 800 G3 to arrive so you can try ahead if you have spare time ![]()
Edit 4
Thanks, worked for me. HP ProBook 450 G7. MPM locked after DMI.
Dear x0rzavi,
Did you check the usage of HP Flash tool? HP Flash and Replicated Setup Utilities for Linux | HP Client Management Solutions Maybe this gives some kind of unrestricted access to flashing modded BIOSes