Because 11.6.0.1009 has an older date than 11.5.0.1019, Device Manager says that you are updated. You don’t have to update to anything. Drivers 11.0 would work just fine on such a system. If you want to try the early 11.5 or 11.6 then you can do so but for now I would either stick to 11.0 or 11.5 as it’s newer than 11.6 branch driver we have and we don’t know the difference, if any.
@plutomaniac
Can I stay with driver already installed? 11.0.6.1194?
Could you tell me how to check ME firmware version?
EDIT: One more question: on Intel Download Center there is no newer driver than 11.0.6.1194. Why?
Thanks for your clear advice, we will not use the installer also, so we will stay on 11.5-version , untill a newer driver arrivés…
Is there any disadvantage in not installing the manufacturer provided driver for Intel Management Engine in favour of the latest driver available on this thread? I am asking this especially in context of a Clevo Laptop system with Z97 Chipset and Core i7 4790K desktop processor. Can there be any performance issue like system fans not working properly if I install the latest driver from this thread?
@ bamboos:
Yes, you can and probably should stay at 11.0 for now. You can check your fw version with MEInfo tool or by drag & dropping your BIOS/SPI image to ME Analyzer. All the details are at the first post. Intel’s website doesn’t always host the latest drivers, it’s usually the opposite.
@ akm:
The drivers are not OEM-customized so unless a release is buggy, newer is always better. I suggest you use the latest as seen at the first post.
When I trying to use MEinfo I got this:
“Error 82: Unknown or unsupported hardware platform”
EDIT: Nevermind, I downloaded wrong version of ME Tools ![]()
@Plutomaniac
Could you tell me, does all drivers etc from this thread are directly from Intel, or other source?
And another question: Drivers which I downloaded from Intel says it’s for Intel NUC… may it cause any problems in the future? Some performance drops etc? Or this is not only for Intel NUC?
The drivers are all made by Intel, work at all systems and are found either at Intel’s or various other OEM’s websites. No incompatibilities, non system-specific, no performance drops etc. Just install the drivers found here and you are good to go.
@plutomaniac
Thank you for the answer.
Last question: Actually my motherboard have P67 chipset. Can I sefely use drivers from Intel’s website, while their description says: “for Intel NUC” ?
I am trying to update the ME firmware on older 6-series chipset PC, and it just won’t let me. I am getting error 8716 all the time.
I simply type “FWUpdLcl.exe upd.bin”. There’s no -f switch for this old version, and according to the help all I have to do is specify the update file.
edit:
Even better now: I downloaded the other ME tools for this particular chipset, and this time it flashed. The problem is, after the reboot, the ME interface disappeared from Device Manager and when I run MEinfo, I now get “Error 9255: Fail to read FW Status Register value 0x0” error message.
@ Octopuss:
I need more information. What 6-series PC exactly? These can use either ME7 or ME8. What ME firmware do you currently have? What exact version of FWUpdate and other tools were you trying to use initially? You said that FWUpdate does not have -f parameter which was a thing at ME6 (5-series) and lower tools. So obviously you are using the wrong tools. What tools did you use the 2nd time and what firmware did you flash exactly?
It’s an old H55 board. Did I write 6-series? I meant 5.
There are two ME tools archives, the working one was the older, 6.0 rather than 6.x I believe.
I flashed Intel ME Firmware v6.2.50.1062 (1.5MB).rar
I cannot verify if you system indeed has 1.5MB firmware as I don’t know the model but I assume you made sure of that yourself. Now, the 6.0 System Tools are not older (in fact they are a lot newer than the 6.x we have) and they target different platforms which use Ignition firmware and not 1.5MB or 5MB. Ignition tools (6.0) are not compatible with non-Ignition ones so you need to use the 6.x system tools. Also, it’s not possible to have used 6.0 because Ignition SKU did not use FWUpdate and thus there is no such tool there. As for your problem, try running Flash Programming Tool with command fptw -greset and check MEInfo and MEManuf again after the system has reset.
Updated my Skylake Core M to 11.5.1.1006.
The logfiles from MEManufWin64 and MEInfoWin (verbose):
2
3
4
5
6
7
8
9
10
11
12
13
14
15
Intel(R) MEManuf Version: 11.0.0.1205
Copyright(C) 2005 - 2016, Intel Corporation. All rights reserved.
Warning 463: A test returned from FW does not match known test by the tool: App(12) Comp(0) Test(0)
Error 463: A test returned from FW does not match known test by the tool: App(%d) Comp(%d) Test(%d)
Warning 463: A test returned from FW does not match known test by the tool: App(12) Comp(0) Test(1)
Error 463: A test returned from FW does not match known test by the tool: App(%d) Comp(%d) Test(%d)
Warning 463: A test returned from FW does not match known test by the tool: App(12) Comp(0) Test(2)
Error 463: A test returned from FW does not match known test by the tool: App(%d) Comp(%d) Test(%d)
MEManuf Operation Passed (with warnings)
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
166
167
168
169
170
171
172
173
174
175
176
177
178
179
180
181
182
183
184
185
186
187
188
189
190
191
192
193
194
195
196
197
198
199
200
201
202
203
204
205
206
207
208
209
210
211
Intel(R) MEInfo Version: 11.0.15.1003
Copyright(C) 2005 - 2016, Intel Corporation. All rights reserved.
FW Status Register1: 0x90000255
FW Status Register2: 0x020B0506
FW Status Register3: 0x00000020
FW Status Register4: 0x00084000
FW Status Register5: 0x00000000
FW Status Register6: 0x00000000
CurrentState: Normal
ManufacturingMode: Enabled
FlashPartition: Valid
OperationalState: CM0 with UMA
InitComplete: Complete
BUPLoadState: Success
ErrorCode: No Error
ModeOfOperation: Normal
SPI Flash Log: Not Present
Phase: ROM/Preboot
ICC: Valid OEM data, ICC programmed
ME File System Corrupted: No
PhaseStatus: CALL_NEXT_MODULE
FPF and ME Config Status: Not committed
FW Capabilities value is 0x31111240
Feature enablement is 0x31111240
Platform type is 0x41110321
No Intel vPro Wireless device was found
Intel(R) ME code versions:
Windows OS Version : 6.2.9200 ""
Table Type 0 ( 0x 00 ) found, size of 24 (0x 18 ) bytes
BIOS Version 1.0
Windows OS Version : 6.2.9200 ""
Table Type 0 ( 0x 00 ) found, size of 24 (0x 18 ) bytes
Table Type 1 ( 0x 01 ) found, size of 27 (0x 1B ) bytes
Table Type 2 ( 0x 02 ) found, size of 15 (0x 0F ) bytes
Table Type 3 ( 0x 03 ) found, size of 22 (0x 16 ) bytes
Table Type 8 ( 0x 08 ) found, size of 9 (0x 09 ) bytes
Table Type 8 ( 0x 08 ) found, size of 9 (0x 09 ) bytes
Table Type 8 ( 0x 08 ) found, size of 9 (0x 09 ) bytes
Table Type 8 ( 0x 08 ) found, size of 9 (0x 09 ) bytes
Table Type 8 ( 0x 08 ) found, size of 9 (0x 09 ) bytes
Table Type 8 ( 0x 08 ) found, size of 9 (0x 09 ) bytes
Table Type 8 ( 0x 08 ) found, size of 9 (0x 09 ) bytes
Table Type 8 ( 0x 08 ) found, size of 9 (0x 09 ) bytes
Table Type 8 ( 0x 08 ) found, size of 9 (0x 09 ) bytes
Table Type 8 ( 0x 08 ) found, size of 9 (0x 09 ) bytes
Table Type 8 ( 0x 08 ) found, size of 9 (0x 09 ) bytes
Table Type 8 ( 0x 08 ) found, size of 9 (0x 09 ) bytes
Table Type 8 ( 0x 08 ) found, size of 9 (0x 09 ) bytes
Table Type 8 ( 0x 08 ) found, size of 9 (0x 09 ) bytes
Table Type 8 ( 0x 08 ) found, size of 9 (0x 09 ) bytes
Table Type 8 ( 0x 08 ) found, size of 9 (0x 09 ) bytes
Table Type 8 ( 0x 08 ) found, size of 9 (0x 09 ) bytes
Table Type 8 ( 0x 08 ) found, size of 9 (0x 09 ) bytes
Table Type 8 ( 0x 08 ) found, size of 9 (0x 09 ) bytes
Table Type 8 ( 0x 08 ) found, size of 9 (0x 09 ) bytes
Table Type 8 ( 0x 08 ) found, size of 9 (0x 09 ) bytes
Table Type 8 ( 0x 08 ) found, size of 9 (0x 09 ) bytes
Table Type 8 ( 0x 08 ) found, size of 9 (0x 09 ) bytes
Table Type 8 ( 0x 08 ) found, size of 9 (0x 09 ) bytes
Table Type 9 ( 0x 09 ) found, size of 17 (0x 11 ) bytes
Table Type 9 ( 0x 09 ) found, size of 17 (0x 11 ) bytes
Table Type 9 ( 0x 09 ) found, size of 17 (0x 11 ) bytes
Table Type 9 ( 0x 09 ) found, size of 17 (0x 11 ) bytes
Table Type 9 ( 0x 09 ) found, size of 17 (0x 11 ) bytes
Table Type 10 ( 0x 0A ) found, size of 6 (0x 06 ) bytes
Table Type 11 ( 0x 0B ) found, size of 5 (0x 05 ) bytes
Table Type 12 ( 0x 0C ) found, size of 5 (0x 05 ) bytes
Table Type 32 ( 0x 20 ) found, size of 20 (0x 14 ) bytes
Table Type 34 ( 0x 22 ) found, size of 11 (0x 0B ) bytes
Table Type 26 ( 0x 1A ) found, size of 22 (0x 16 ) bytes
Table Type 36 ( 0x 24 ) found, size of 16 (0x 10 ) bytes
Table Type 35 ( 0x 23 ) found, size of 11 (0x 0B ) bytes
Table Type 28 ( 0x 1C ) found, size of 22 (0x 16 ) bytes
Table Type 36 ( 0x 24 ) found, size of 16 (0x 10 ) bytes
Table Type 35 ( 0x 23 ) found, size of 11 (0x 0B ) bytes
Table Type 27 ( 0x 1B ) found, size of 15 (0x 0F ) bytes
Table Type 36 ( 0x 24 ) found, size of 16 (0x 10 ) bytes
Table Type 35 ( 0x 23 ) found, size of 11 (0x 0B ) bytes
Table Type 27 ( 0x 1B ) found, size of 15 (0x 0F ) bytes
Table Type 36 ( 0x 24 ) found, size of 16 (0x 10 ) bytes
Table Type 35 ( 0x 23 ) found, size of 11 (0x 0B ) bytes
Table Type 29 ( 0x 1D ) found, size of 22 (0x 16 ) bytes
Table Type 36 ( 0x 24 ) found, size of 16 (0x 10 ) bytes
Table Type 35 ( 0x 23 ) found, size of 11 (0x 0B ) bytes
Table Type 26 ( 0x 1A ) found, size of 22 (0x 16 ) bytes
Table Type 28 ( 0x 1C ) found, size of 22 (0x 16 ) bytes
Table Type 27 ( 0x 1B ) found, size of 15 (0x 0F ) bytes
Table Type 29 ( 0x 1D ) found, size of 22 (0x 16 ) bytes
Table Type 39 ( 0x 27 ) found, size of 22 (0x 16 ) bytes
Table Type 41 ( 0x 29 ) found, size of 11 (0x 0B ) bytes
Table Type 41 ( 0x 29 ) found, size of 11 (0x 0B ) bytes
Table Type 41 ( 0x 29 ) found, size of 11 (0x 0B ) bytes
Table Type 7 ( 0x 07 ) found, size of 19 (0x 13 ) bytes
Table Type 7 ( 0x 07 ) found, size of 19 (0x 13 ) bytes
Table Type 7 ( 0x 07 ) found, size of 19 (0x 13 ) bytes
Table Type 7 ( 0x 07 ) found, size of 19 (0x 13 ) bytes
Table Type 4 ( 0x 04 ) found, size of 48 (0x 30 ) bytes
Table Type 16 ( 0x 10 ) found, size of 23 (0x 17 ) bytes
Table Type 17 ( 0x 11 ) found, size of 40 (0x 28 ) bytes
Table Type 17 ( 0x 11 ) found, size of 40 (0x 28 ) bytes
Table Type 19 ( 0x 13 ) found, size of 31 (0x 1F ) bytes
Table Type 20 ( 0x 14 ) found, size of 35 (0x 23 ) bytes
Table Type 20 ( 0x 14 ) found, size of 35 (0x 23 ) bytes
Table Type 130 ( 0x 82 ) found, size of 20 (0x 14 ) bytes
Table Type 131 ( 0x 83 ) found, size of 64 (0x 40 ) bytes
MEBx Version found is 11.0.0.0005
MEBx Version 11.0.0.0005
GbE Region does not exist.
GbE Version Unknown
Vendor ID 8086
PCH Version 21
FW Version 11.5.1.1006 LP
LMS Version Not Available
MEI Driver Version 11.5.0.1019
Wireless Hardware Version 2.1.77
Wireless Driver Version 18.40.0.12
FW Capabilities 0x31111240
Intel(R) Capability Licensing Service - PRESENT/ENABLED
Protect Audio Video Path - PRESENT/ENABLED
Intel(R) Dynamic Application Loader - PRESENT/ENABLED
Service Advertisement & Discovery - NOT PRESENT
Intel(R) NFC Capabilities - NOT PRESENT
Intel(R) Platform Trust Technology - PRESENT/ENABLED
TLS Disabled
Last ME reset reason Global system reset
Local FWUpdate Enabled
BIOS Config Lock Enabled
GbE Config Lock Enabled
Get flash master region access status...done
Host Read Access to ME Enabled
Host Write Access to ME Enabled
Get EC region access status...done
Host Read Access to EC Enabled
Host Write Access to EC Enabled
Protected Range Register Base #0 0x0
Protected Range Register Limit #0 0x0
Protected Range Register Base #1 0x0
Protected Range Register Limit #1 0x0
Protected Range Register Base #2 0x0
Protected Range Register Limit #2 0x0
Protected Range Register Base #3 0x0
Protected Range Register Limit #3 0x0
Protected Range Register Base #4 0x0
Protected Range Register Limit #4 0x0
SPI Flash ID 1 EF4017
SPI Flash ID 2 Unknown
BIOS boot State Post Boot
OEM ID 00000000-0000-0000-0000-000000000000
Capability Licensing Service Enabled
OEM Tag 0x00000000
Slot 1 Board Manufacturer 0x00000000
Slot 2 System Assembler 0x00000000
Slot 3 Reserved 0x00000000
M3 Autotest Disabled
C-link Status Disabled
Independent Firmware Recovery Disabled
EPID Group ID 0xF9D
OEM Public Key Hash FPF Not set
Retrieving Variable "OEM Public Key Hash"
OEM Public Key Hash ME EA6FA86514FA887C9044218EDB4D70BB3BCC7C2D37587EA8F760BAFBE158C587
ACM SVN FPF 0x0
KM SVN FPF 0x0
BSMM SVN FPF 0x0
GuC Encryption Key FPF Not set
Retrieving Variable "GuC Encryption Key"
GuC Encryption Key ME 0000000000000000000000000000000000000000000000000000000000000000
FPF ME
--- --
Force Boot Guard ACM Not set
Retrieving Variable "Force Boot Guard ACM Enabled"
Disabled
Protect BIOS Environment Not set
Retrieving Variable "Protect BIOS Environment Enabled"
Disabled
CPU Debugging Not set
Retrieving Variable "CPU Debugging"
Enabled
BSP Initialization Not set
Retrieving Variable "BSP Initialization"
Enabled
Measured Boot Not set
Retrieving Variable "Measured Boot Enabled"
Disabled
Verified Boot Not set
Retrieving Variable "Verified Boot Enabled"
Disabled
Key Manifest ID Not set
Retrieving Variable "Key Manifest ID"
0x0
Enforcement Policy Not set
Retrieving Variable "Error Enforcement Policy"
0x0
PTT Not set
Retrieving Variable "Intel(R) PTT Supported"
Enabled
EK Revoke State Not Revoked
PTT RTC Clear Detection FPF Not set
@Wootever
Ah, great. As I thought, 11.5 is for 100/200-series whereas 11.6 is only for 200-series. I haven’t found documentation which proves that yet but from the GbE included with 11.5 SPI images I’ve found (always the SKL one, whereas KBL for 11.6) and your test, it’s fairly obvious.
What method did you use to upgrade, FWUpdate v11.0 or FIT+FPT v11.0? If you used the latter, did you encounter any errors or similar? I remember that 11.0 FIT shows some ICC errors when loading newer branches (11.5 and 11.6). The warnings you see at MEManuf are probably due to the fact that it’s not KBL compatible. We certainly need a 11.5 or 11.6 system tools kit to show up at some point.
Damn, the forum software is so broken I can’t even use quotes.
Anyway.
I DID use the 6.0 tools, and I know for a fact I did flash the firmware with something that was not FWUpdate. I did it because it worked, unlike the 6.x tools where FWUpdate refused to work at all (as per my previous post).
I guess the board is kind of screwed now.
P.S. The board in question is Gigabyte H55M-UD2H - http://www.gigabyte.com/products/product…spx?pid=3309#ov
I used the latest FWUpdate to upgrade my Skylake to 11.5.1 FW ver. works fine.
Copyright(C) 2005 - 2016, Intel Corporation. All rights reserved.
Intel(R) ME code versions:
BIOS Version D3CN32WW
MEBx Version 11.0.0.0005
GbE Region does not exist.
GbE Version Unknown
Vendor ID 8086
PCH Version 21
FW Version 11.5.1.1006 LP
LMS Version 11.5.0.1020
MEI Driver Version 11.6.0.1009
Wireless Hardware Version Not Available
Wireless Driver Version Not Available
FW Capabilities 0x31111240
Intel(R) Capability Licensing Service - PRESENT/ENABLED
Protect Audio Video Path - PRESENT/ENABLED
Intel(R) Dynamic Application Loader - PRESENT/ENABLED
Intel(R) Platform Trust Technology - PRESENT/ENABLED
TLS Disabled
Last ME reset reason Global system reset
Local FWUpdate Enabled
BIOS Config Lock Enabled
GbE Config Lock Enabled
Host Read Access to ME Disabled
Host Write Access to ME Disabled
Host Read Access to EC Disabled
Host Write Access to EC Disabled
SPI Flash ID 1 EF4018
SPI Flash ID 2 Unknown
BIOS boot State Post Boot
OEM ID 00000000-0000-0000-0000-000000000000
Capability Licensing Service Enabled
OEM Tag 0x00000000
Slot 1 Board Manufacturer 0x00000000
Slot 2 System Assembler 0x00000000
Slot 3 Reserved 0x00000000
M3 Autotest Disabled
C-link Status Disabled
Independent Firmware Recovery Disabled
EPID Group ID 0xF85
OEM Public Key Hash FPF 0000000000000000000000000000000000000000000000000000000000000000
OEM Public Key Hash ME 0000000000000000000000000000000000000000000000000000000000000000
ACM SVN FPF 0x0
KM SVN FPF 0x0
BSMM SVN FPF 0x0
GuC Encryption Key FPF 0000000000000000000000000000000000000000000000000000000000000000
GuC Encryption Key ME 0000000000000000000000000000000000000000000000000000000000000000
FPF ME
— –
Force Boot Guard ACM Disabled Disabled
Protect BIOS Environment Disabled Disabled
CPU Debugging Enabled Enabled
BSP Initialization Enabled Enabled
Measured Boot Disabled Disabled
Verified Boot Disabled Disabled
Key Manifest ID 0x0 0x0
Enforcement Policy 0x0 0x0
PTT Enabled Enabled
PTT Lockout Override Counter 0x0
EK Revoke State Not Revoked
PTT RTC Clear Detection FPF 0x0
I used FWUpdate 11.0, might it be helpful to post the results from FIT+FPT as well?
@ Octopuss:
The 6.0 tools don’t have FWUpdate and you said you used another tool. That tool is certainly Flash Programming Tool (FPT) which is not a replacement of FWUpdate. FPT replaces the whole ME region and not just the parts that need updating like FWUpdate does. It also doesn’t care about platform settings stored at the ME. Before ME8, FWUpdate required only UPD images and not full regions (RGN or EXTR) so if you flashed an UPD image with FPT then the ME is bricked. You said that you flashed 6.2.50.1062 1.5MB firmware with FPT. I checked what ME your system uses and it’s actually 5MB Mobile (MB) and not 1.5MB.
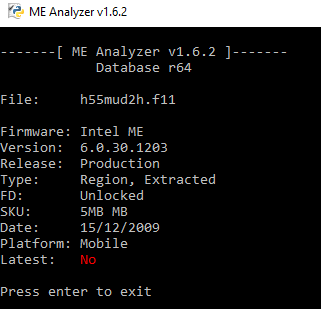
So now you have flashed the wrong firmware SKU (1.5MB) and type (UPD with FPT instead of FWUpdate, FPT works with EXTR or RGN only after merging settings with Flash Image Tool - FITC) with no platform settings (FPT doesn’t keep those unless the firmware is setup by FITC). I’m surprised the system still boots, that was possible back at 5-series but not 6-series or later. So you are lucky. Now, to restore (I think we can because Gigabyte tends to not lock the Flash Descriptor). From the 6.x tools, run FPT with command fptw -d spi.bin and attach the resulting file.
@ kostar20071 & Wootever:
Thank you very much for your tests and determination to be the first to do such an upgrade. Indeed it seems to work just fine, when we have 11.5 or 11.6 tools we should verify that those don’t report any warnings or errors as well.
Can you guys tell me what DEV_ID is shown at Device Manager > Intel(R) Management Engine Interface now (SKL + 11.5 firmware)?
@ Wootever:
Well if you want to test FIT+FPT/Programmer then sure but it probably won’t work properly. It would be more interesting to see whether 11.6 works as well (primarily with FWUpdate and if you want FIT+FPT/Programmer - however, the 11.6 we have is only EXTR so it might not be the best case to test). If I’m right and 11.6 is 200-series only then it won’t work. But since you can easily recover from bricks, you can try if you have the time and courage. If you try 11.6 with FWUpdate, note that the CON LP we have is EXTR so you might need to replace the ISHC region at the $FPT header with 0x20 FF again like we did back when you helped with the PDM/NOPDM testing.
Mobile 6th (100-Series) Generation Intel(R) Processor Intel Core i7-6500U . (I also noticed that all chipset drivers (Intel Chipset) inf s are inside SunrisePoint-LP directory)
Consumer LP
Driver ver: ME 11.5.0.1011
PCI\VEN_8086&DEV_9D3A&SUBSYS_382817AA&REV_21
Very nice, thank you kostar20071. So it seems that Intel’s comments at the 11.5 and 11.6 drivers are correct. I assume that they have forgotten to add “KBL/SPT-H” next to A13A and that’s why only 9D3A is written. It does show though that these DEV_IDs are for 11.0 Skylake + SunrisePoint (100-series) or 11.5 KabyLake + SunrisePoint (100-series).
