Hello. Need help with reflashing IME firmware 8.1.0.1263. I can’t find the requires files to do it. My chipset is intel p67
@Fernando or @plutomaniac - can you look at this article?
http://www.guru3d.com/news-story/intel-p…ck-to-2008.html
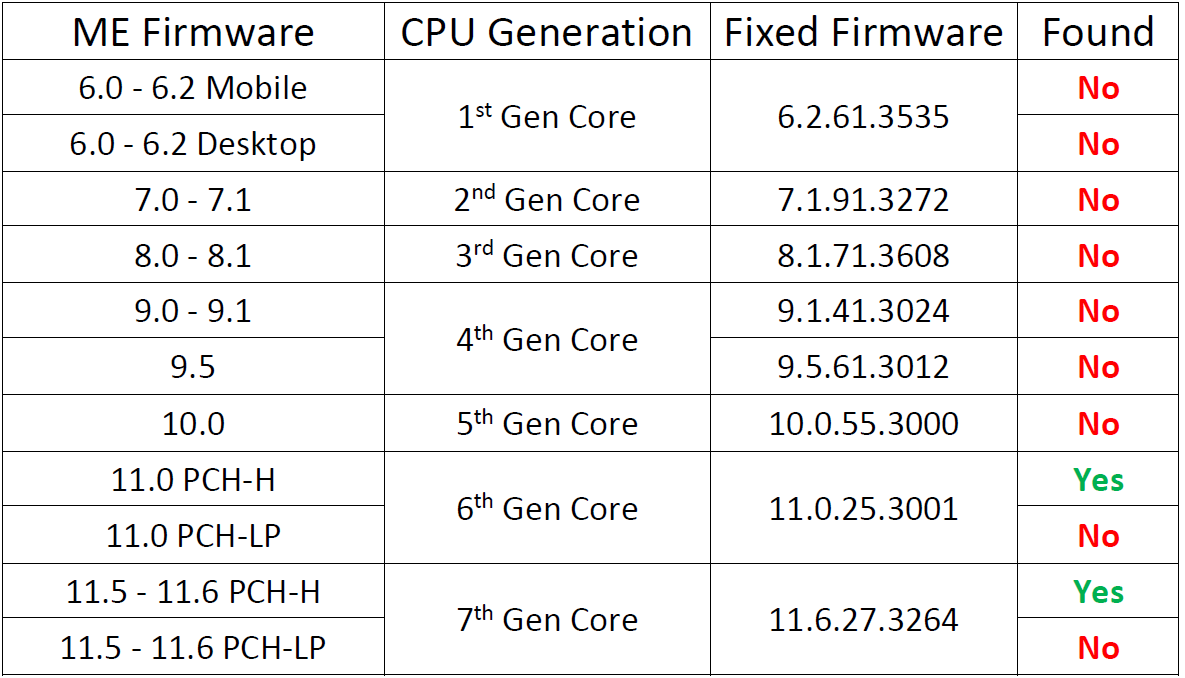
Anybody found the fixed management engine firmwares yet?
Apparently the fixed versions are:
- 6.2.61.3535
- 7.1.91.3272
- 8.1.71.3608
- 9.1.41.3024
- 9.5.61.3012
- 10.0.55.3000
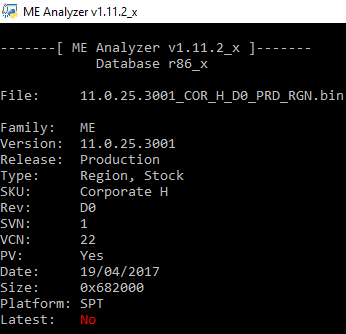
- 11.0.25.3001
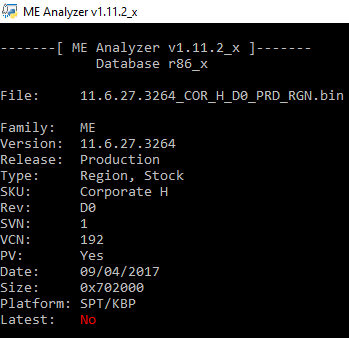
- 11.6.27.3264
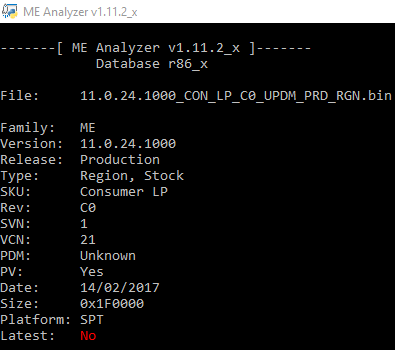
Intel ME 11.0 Consumer PCH-LP Firmware v11.0.24.1000
Intel ME 11.0 Corporate PCH-LP Firmware v11.0.24.1000 (UPDM1 & UPDM2)
Lenovo has published a security advisory in which they state when updated Management Engine firmwares will be available: https://support.lenovo.com/de/de/product_security/len-14963
So the obvious has come to pass: http://www.tomshardware.com/news/intel-a…rous,34300.html
I wonder if this doesn’t affect AMT 1-5 as well and its too old for intel to care.
At least if the manufacturer doesn’t release a fix you can load one yourself because of this forum.
Where could you find 10.0.55.3000 release? 10.0.50.1004 LP right now on a dell xps 13. Do I need to update?
Thanks
The updates have been provided only to the OEMs by Intel, none are publicly available yet. OEMs will need to test them and provide to the end users. Lenovo announced some from the next week, I expect Dell will take a couple weeks/months too.
Intel ME 11.6 Corporate PCH-H Firmware v11.6.27.3264 (INTEL-SA-00075/CVE-2017-5689)
Intel ME 11.0 Consumer PCH-H Firmware v11.0.22.1000 (EXTR → RGN)
Intel ME System Tools v11.6 r11
Apparently the Security Version Number (SVN) will change when the world gets destroyed, lol Intel… 
HP has now also released a security advisory with specific dates for updated ME firmwares: https://support.hp.com/us-en/document/c05507350
@plutomaniac at last I found cause/culprit.
The first clew I have as to what caused my issue with (A7) Me FW Downgrade - Request Me Spilock Failed was when I read the change-log on Intel Management Engine (ME) Firmware Version 11.6.27.3264 (S & H) (5 MB)
found at http://www.station-drivers.com/index.php…id=2829&lang=fr
OK that seems to be a corporate ME but none-the-less it has the clew I needed.
So a simple power cycle caused this issue of sending the ME on my board into recovery mode which results in above message being displayed.
We had already established that the ME was in recovery mode, but I never found the reason. and its absurd.
Asus still jerking me around. The ideal would be to get in direct contact with someone in Asus Taiwan, since US/EMEA are independent and do whatever they like i.e. burying head in sand and not being helpful, after 5 reports and ever increasing data attached to bug report (8 pages of logs/reports gathered with various tools.) at least I know what Im reporting is the issue with some relief and certainty.
Intel ME 11.0 Corporate PCH-H Firmware v11.0.25.3001 (INTEL-SA-00075/CVE-2017-5689)
Intel ME System Tools v11.0 r4
Added “Notice for INTEL-SA-00075/CVE-2017-5689 state” at the first post:
Big thanks to Pacman/SD for the new firmware! 
@ atomota:
If that was the case the problem would have been solved after updating to 11.6.25.1229. Remember that if the problem is at the ME data then ASUS won’t be able to fix it remotely by a BIOS update (as we extensively discussed before). If the problem is at the ME firmware then a simple update will solve it. Also, no need to tag me at this thread, I monitor it regardless.
This is all bloody confusing. What I can gather from Intel’s advisory:
- Remote privilege escalation is possible on AMT and ISM
- Local privilege escalation is possible on AMT, ISM and SBT
If ME is present but none of those management methods are present or provisioned, the system is not vulnerable.
To be sure, run the detection program that can be found here: https://downloadcenter.intel.com/downloa…Detection-Guide .
If you are vulnerable and this isn’t an AMT-managed corporate machine, just disable AMT in BIOS for now.
Here’s an article by the CTO of Embedi, trying to set the record straight as to what this is and isn’t. It’s unrelated to the "ME is a rootkit" rant from June 2016. https://threatpost.com/researcher-basele…ability/125390/
That "ME is a rootkit" rant is useful though to get a better understanding of the structure of ME. That’s here: http://boingboing.net/2016/06/15/intel-x…-ship-with.html
Older version ME FW 11.6.12.3202 Corporate H & LP showed up at HP today.
ENHANCEMENTS:
- Intel Management Engine (ME) Firmware update, required to address the
INTEL-SA-00075 / CVE-2017-5689 Vulnerability
Download HTML
Download EXE
I never updated to 11.6.25.1229, I was under the impression my board doesnt allow that so I never tried.
I think these firmware will come out only for Corporate systems. Consumers are not affected by such issues.
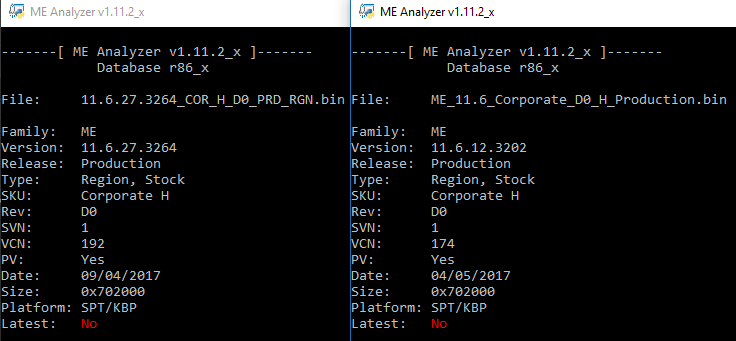
I don’t understand what this firmware is. It makes no sense. Intel and their partners all mention firmware 11.6.27.3264 and now we have another with build 3xxx (11.6.12.3202) which was built yesterday apparently (04/05/2017) based on an older hotfix version (11.6.12 instead of 11.6.27) and with an older VCN number of 174 instead of today’s 192. Why?
![]()
![]()
![]()
I don’t understand what this firmware is. It makes no sense. Intel and their partners all mention firmware 11.6.27.3264 and now we have another with build 3xxx (11.6.12.3202) which was built yesterday apparently (04/05/2017) based on an older hotfix version (11.6.12 instead of 11.6.27) and with an older VCN number of 174 instead of today’s 192. Why?![]()
![]()
![]()
My guess is that HP requested, received and started testing an early fix from Intel based on 11.6.12, spent some time testing but had to push it out early due to customer demand. As for the date, it is just a field in the manifest, so I think they just asked Intel to take the already tested version and only re-sign it.