Intel ME 11.7 Consumer PCH-H Firmware v11.7.0.1229
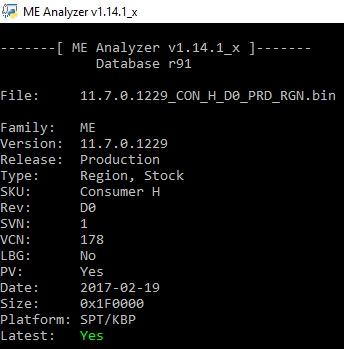
Intel ME 11.7 Consumer PCH-LP Firmware v11.7.0.3290
Note: So far I’ve seen 1 Lenovo, 1 HP and 13 ASUS systems to have been officially updated to ME 11.7 without the changelog saying so. Thus, I’ve brought back the Consumer 11.7 firmware which should be used by those systems which are on 11.7 firmware, as the undertext of the first post says. Questions regarding upgrading/downgrading which are the result of not reading the first post (VCN issues for example), will not be answered by me.
@ nederfox:
Welcome nederfox and thank you for your pretty cool contribution. That is definitely easier than to mod AMITSE. I did the same as lordkag at another ASRock board (X79) which can be found here but I never saw the result. Anyway, your finding is interesting, thank you for sharing it.
@ ilario:
I asked that in order to figure out if something needs to be improved at the first post to become more understandable. You showed a picture of Intel’s SA-00075 Vulnerability check tool but your system uses Consumer firmware so it’s not vulnerable to begin with, as mentioned at the first post. As you can see from MEInfo you currently have 11.0 PCH-LP firmware so pick the equivalent from the first post.
@ forceadmin:
As far as I can tell, there are two different problems with that laptop. One is the loose battery connection sensor or similar which is old Dell BIOS related. The other is that the ME firmware seems to be corrupted. During BIOS update, Dell tries to update the ME but it does not respond and thus the process stops. To repair the ME firmware we need read/write access to its region at the BIOS/SPI chip, which is usually locked. Have you tried command “fptw -d spi.bin” via Flash Programming Tool (FPT)? Does it complete or do you see an error (cpu access)? If you see an error, try this: boot into an EFI Shell (not DOS) and execute command “setup_var 0x2D4 0x1”. After reboot, try command FPT “fptw -d spi.bin” again, does it complete successfully?
Thanks! Updated from Intel ME 11.6 Consumer PCH-LP Firmware v11.6.29.3287 ->> TO->>Intel ME 11.7 Consumer PCH-LP Firmware v11.7.0.3290
My system : 100-series SKL-U , i7-6500U (mobile)
MEInfo Output:
Intel(R) MEInfo Version: 11.6.29.3287
Copyright(C) 2005 - 2017, Intel Corporation. All rights reserved.
Intel(R) ME code versions:
BIOS Version D3CN35WW
MEBx Version 11.0.0.0005
GbE Version Unknown
Vendor ID 8086
PCH Version 21
FW Version 11.7.0.3290 LP
LMS Version Not Available
MEI Driver Version 11.7.0.1014
Wireless Hardware Version 2.1.77
Wireless Driver Version 19.51.2.4
FW Capabilities 0x31111240
Intel(R) Capability Licensing Service - PRESENT/ENABLED
Protect Audio Video Path - PRESENT/ENABLED
Intel(R) Dynamic Application Loader - PRESENT/ENABLED
Intel(R) Platform Trust Technology - PRESENT/ENABLED
Intel(R) AMT State Disabled
TLS Disabled
Last ME reset reason Global system reset
Local FWUpdate Enabled
BIOS Config Lock Enabled
GbE Config Lock Enabled
Host Read Access to ME Disabled
Host Write Access to ME Disabled
Host Read Access to EC Disabled
Host Write Access to EC Disabled
SPI Flash ID 1 EF4018
SPI Flash ID 2 Unknown
BIOS boot State Post Boot
OEM ID 00000000-0000-0000-0000-000000000000
Capability Licensing Service Enabled
OEM Tag 0x00000000
Slot 1 Board Manufacturer 0x00000000
Slot 2 System Assembler 0x00000000
Slot 3 Reserved 0x00000000
M3 Autotest Disabled
C-link Status Disabled
Independent Firmware Recovery Disabled
EPID Group ID 0xF85
LSPCON Ports None
5K Ports None
OEM Public Key Hash FPF 0000000000000000000000000000000000000000000000000000000000000000
OEM Public Key Hash ME 0000000000000000000000000000000000000000000000000000000000000000
ACM SVN FPF 0x0
KM SVN FPF 0x0
BSMM SVN FPF 0x0
GuC Encryption Key FPF 0000000000000000000000000000000000000000000000000000000000000000
GuC Encryption Key ME 0000000000000000000000000000000000000000000000000000000000000000
FPF ME
— –
Force Boot Guard ACM Disabled Disabled
Protect BIOS Environment Disabled Disabled
CPU Debugging Enabled Enabled
BSP Initialization Enabled Enabled
Measured Boot Disabled Disabled
Verified Boot Disabled Disabled
Key Manifest ID 0x0 0x0
Enforcement Policy 0x0 0x0
PTT Enabled Enabled
PTT Lockout Override Counter 0x0
EK Revoke State Not Revoked
PTT RTC Clear Detection FPF 0x0
@ plutomaniac:
When I ran fptw -d spi.bin, I got “Error 26: The host CPU does not have read access to the target flash area. To enable read access for this operation you must modify the descriptor settings to give host access to this region”. I don’t have any experience with EFI Shell and there was not an option for that in the BIOS. After some research, I was able find a shellx64.efi binary file and boot to a Shell> prompt from a USB drive. However, when I ran command setup_var 0x2D4 0x1, it gave me "‘setup_var’ is not recognized as an internal or external command, operable program, or batch file."
What am I doing wrong?
@ ilario:
Intel ME 11.0 Consumer PCH-LP Firmware v11.0.26.3000
@ kostar20071:
Thank you for the report, everything looks ok.
@ forceadmin:
Try the one attached. Just copy the "efi" folder at the root of the USB. The command here is "setvar" instead (probably at the other shell you found too).
EFI_Shell.rar (248 KB)
@Ferrous
Actually I don’t know what is this, I think there is another method but I’m afraid to try it without asking you.
I intend to use AMI Firmware Update Utility in efi mode using this command
AfuEfix64.efi E1762IMS.70X /me /meuf
I got the idea from this link
http://www.msi-bios.com/msi-bios-flash-utility-id-15.html
but I don’t understand “- /ME command fail - When BIOS support MER commands.” written in the “What’s new:” section
@The_Engineer The FD is locked, so the ME Region is R/W protected.
@Ferrous
so this makes me think that the firmware itself is not corrupted but it is an access problem or what!!!
Is W protection what makes the me fw n/a ?
If for example I tried that
AfuEfix64.efi E1762IMS.70X /p /b /n /k /r /me
and me failed,will this brick my computer or prevent it from booting?
@ plutomaniac:
Thank you. Using your EFI Shell, I ran “setvar 0x2D4 0x1” and received the following:
setvar: Invalid argument - '0x1’
setvar: Unable to set - 8BE4DF61-93CA-11D2-AA0D-00E098032B8C - 0x2D4
Please advise.
@ forceadmin:
Based on the options which can be seen at your BIOS, there is a hidden one called "ME Disable" which will probably allow you to dump its region.
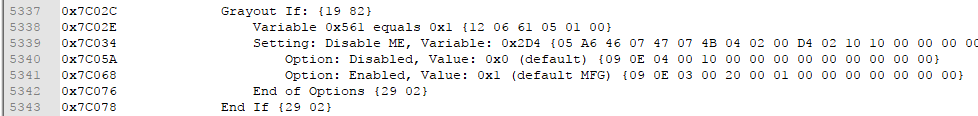
Download the shell attached below (yet another one). I don’t know what the variable above 0x2D4 is, inside the if clause, but maybe try to set 0x561 to 0x1 as well before the needed 0x2D4. If you enter “setup_var 0x561” and “setup_var 0x2D4” you should see the current values of the variables, which should be 0x0 as in Disabled. We need them to be 0x1 which means Enabled, thus “ME Disabled” is true. So enter “setup_var 0x561 0x1” and “setup_var 0x2D4 0x1” and hopefully it completes successfully. Afterwards enter “exit” and press the power button to restart the laptop.
Grub_NVRAM_editor.zip (751 KB)
@ Plutomaniac:
Thank you so much. I was finally able to set both 0x561 and 0x2D4 to 0x1 from 0x0 using the GNU GRUB shell that you provided.
However, when I ran "fptw64 -d spi.bin", I got the same CPU error as before.
I also tried running "fptw64 -greset" again and received the same error as before there as well.
Should I try to flash the A10 BIOS again or am I out of options?
@ forceadmin:
If you tried to dump exactly at the next reboot (that trick only works for 1 boot) and it did not work, you are out of software options. Out of curiosity, if you do the trick and at the next reboot boot into the shell again and check the variable values, are they 0x1 now? Other than that, to repair the ME firmware now would require physical access to the motherboard. You can either temporarily (until next reboot) enable read/write access by sorting two pins of the audio chip while the system starts or you can use a hardware programmer to manually desolder, program and resolder the BIOS/SPI chip of the board.
There’s an idiom about “beating around the bush”, which is what you’re doing here. Both Ferous and I before him have explained to you that you cannot use software tools to reflash the ME region. What I said here is still the only solution to this problem. If the FD is locked and there are no BIOS options, mobo jumpers, hot-keys, setup_var options etc, then dealing with the hardware itself is the only way. I understand not wanting to cause any problem to the laptop but there is nothing else to try, to my knowledge.
Also, there is no need to tag me at my own threads as I monitor them regardless. Last but certainly not least, it is not allowed to publicly attach or link to Intel Confidential documentation in this forum.
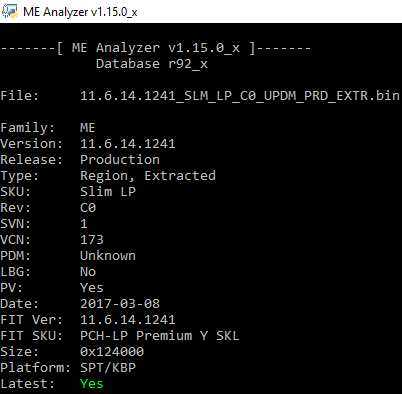
Intel ME 11.6 Slim PCH-H Firmware v11.6.14.1241
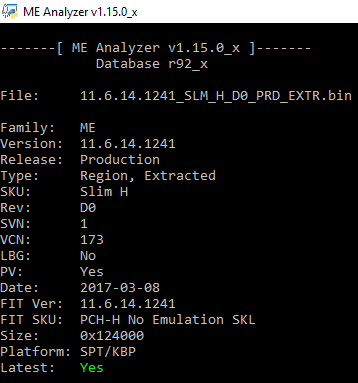
Intel ME 11.6 Slim PCH-LP Firmware v11.6.14.1241
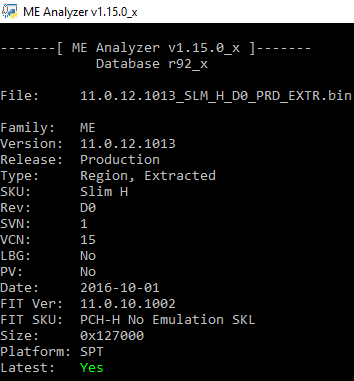
Intel ME 11.0 Slim PCH-H Firmware v11.0.12.1013
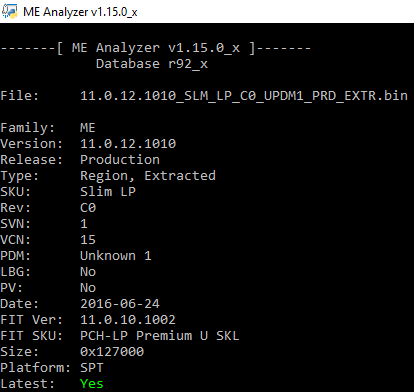
Intel ME 11.0 Slim PCH-LP Firmware v11.0.12.1010
Note: The Slim SKU is only being used at Apple systems so far. ME Analyzer v1.15.0 or later is needed.
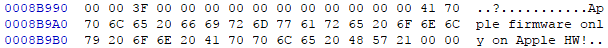
Alright, we get it Apple. We get it…  (Apple’s Graphics uController Encryption Key, an option in FIT)
(Apple’s Graphics uController Encryption Key, an option in FIT)
@ Plutomaniac:
I appreciate all of your help. To be honest, I had a brain cramp and failed to press the power button after entering “exit” at the shell prompt after changing the values to 0x1. I simply let it boot to the next EFI option, which was into the Win 10 DVD repair. I then restarted from the troubleshooting menu. After everything failed again, I shut it down completely.
After reading your last post, I booted it back up, went back into the shell, and checked both values. 0x1 had stuck for both. I tried “fptw64 -greset” and “fptw64 -d spi.bin” again. Both failed.
I re-flashed the A10 BIOS. This time, it paused for a moment at 0% Sending Intel Management Engine Firmware Update, then continued on to a new error, ME Firmware Update Failed: Image Loading. It progressed through that and continued with the flash, which resulted in BIOS Update Successful.
These things are now true:
1. There is no longer a MEBx option at the F12 boot menu.
2. Message FW Status Recovery Error no longer shows on boot.
3. The Device Manager no longer shows an error for the Intel Management Engine Interface. In fact, it doesn’t show the Intel Management Engine Interface in the System devices section of Device Manager at all now.
4. When I tried to re-install the Intel Management Engine Interface driver, it gave me options to uninstall or repair it. I chose to repair it and the result was a “fatal” error dialog box with no apparent effect. I then ran the installer again and chose to uninstall. It performed that successfully. I rebooted and tried to install the driver again. It now gives me the error, This platform is not supported.
5. I ran MEInfo and MEManuf again and both are now saying Unknown or unsupported hardware platform.
6. The BIOS information (see image) shows all firmware versions are now up-to-date.
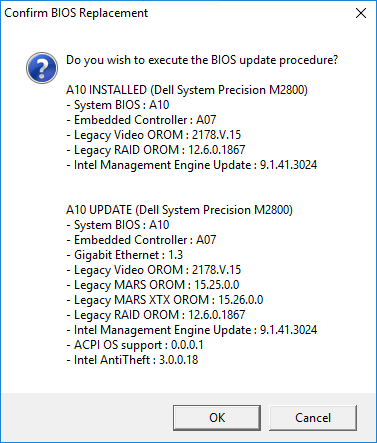
I am puzzled as to how the BIOS flash indicates that the ME firmware update failed, but the above image clearly shows it on the right version.
Just from the little bit of time that I’ve spent with the laptop since, it does seem to be running faster and behaving better from a power management standpoint.
I apologize for being such a pain. It still doesn’t seem to be 100% correct. Have I royally screwed it up or is there something else that can be done to set it all right besides tear it apart?
@forceadmin
That’s because you have disabled ME. Set those 2 option back to 0x0 and it will be back.
@ forceadmin:
Yeap, it is as Ferrous said. All of the things you said are normal when the ME is disabled with such an option. Your BIOS settings remained at 0x1 so now you need to set them back to 0x0. What’s very interesting is that the BIOS update did continue with ME Disabled so at least now you have BIOS A10 which should solve the other problem with the loose battery connection when removed from the dock etc. It is also possible that the new BIOS may have fixed some sort of incompatibility between itself and ME firmware, thus fixing the 2nd issue as well without a reflash of the latter, although it is not very likely. With ME Disabled option, I don’t think the OS or any tools run from it should be able to detect the version of the ME because they cannot communicate with it. We’ll see when you set the two variables back to 0x0 (and reboot).
@ plutomaniac
Attached file is dumped from a Supermicro ICH9R board w/ X7SBE Phoenix cME FirstBios Pro 2.0a dated 14.09.2011. I could dump the chip after desoldering its GND pin 
Currently ME Analyzer states this bios contains no ME nor a SPS?
x7sbe.rom.zip (784 KB)
@ nederfox:
It doesn’t have one. Back then not all systems had ME firmware as it wasn’t obligatory.
@ plutomaniac:
Thanks to you and @ Ferrous. I set both values back to 0x0 and attempted all flashes, resets, and tests that you have given me up to this point again. The same errors exist that were there before disabling ME. The only difference seems to be that when I run the BIOS .exe file from within Windows, the initial dialog box indicates that all firmware is now up-to-date (see previous screen capture).
Is there anything else to try from a software standpoint? If not, would it hurt to leave ME disabled? It really did seem to perform better when disabled.







 (Apple’s Graphics uController Encryption Key, an option in FIT)
(Apple’s Graphics uController Encryption Key, an option in FIT)