It’s a shame that the machine no longer boots. No matter what, I wish you a Merry Christmas and happy new year as well a-dead-trousers. Personally I don’t believe that your original though to update it was misguided but I suppose you’re unlucky and stumbled upon some sort of Lenovo security measure or flashing mishap. For now you should definitely enjoy the holidays but if you manage to resolve the issue and possibly figure out what went wrong, please let us know so that the same thing won’t hopefully happen to other people in the future. 
This work is amazing! Could I translate it to spanish and post it?
Thank you for your kind words. I don’t think there is a point in doing that for multiple reasons. No matter what, I would expect people to at least have a source link to the original forum thread.
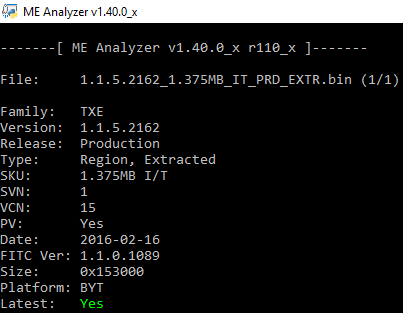
Intel TXE 1.1 1.375MB Firmware v1.1.5.2162 IT
Intel CSTXE System Tools v3 r6
Why there aren’t (CS)TXE firmwares available?
There aren’t any in this thread because Intel no longer has a FWUpdate tool for CSTXE-based Atom platforms (APL, GLK). The official update methods are either via OEM BIOS updates (Capsule) or when the system is in Download & Execute (DNX) mode. Another issue is that CSTXE is usually partially signed by the OEM and their RSA Public Key + Exponent hash is stored in the SoC (hardware, FPF). So, on such images, you cannot update the CSTXE firmware without the OEM Private RSA Key without the platform rejecting your new image. This is what I’ve understood but someone can correct me if I’m wrong.
Oh, ok. Thank you very much for the explanaiton
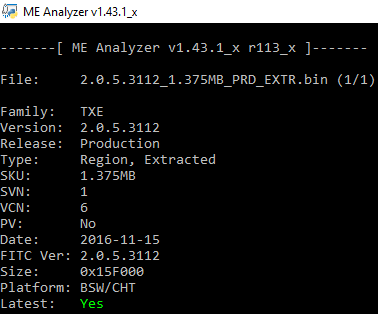
Intel TXE 2.0 1.375MB Firmware v2.0.5.3112
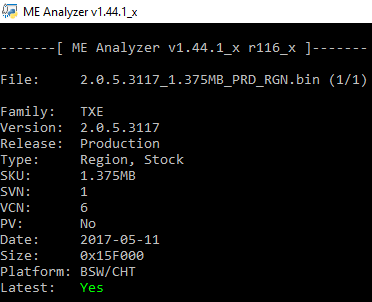
Intel TXE 2.0 1.375MB Firmware v2.0.5.3117
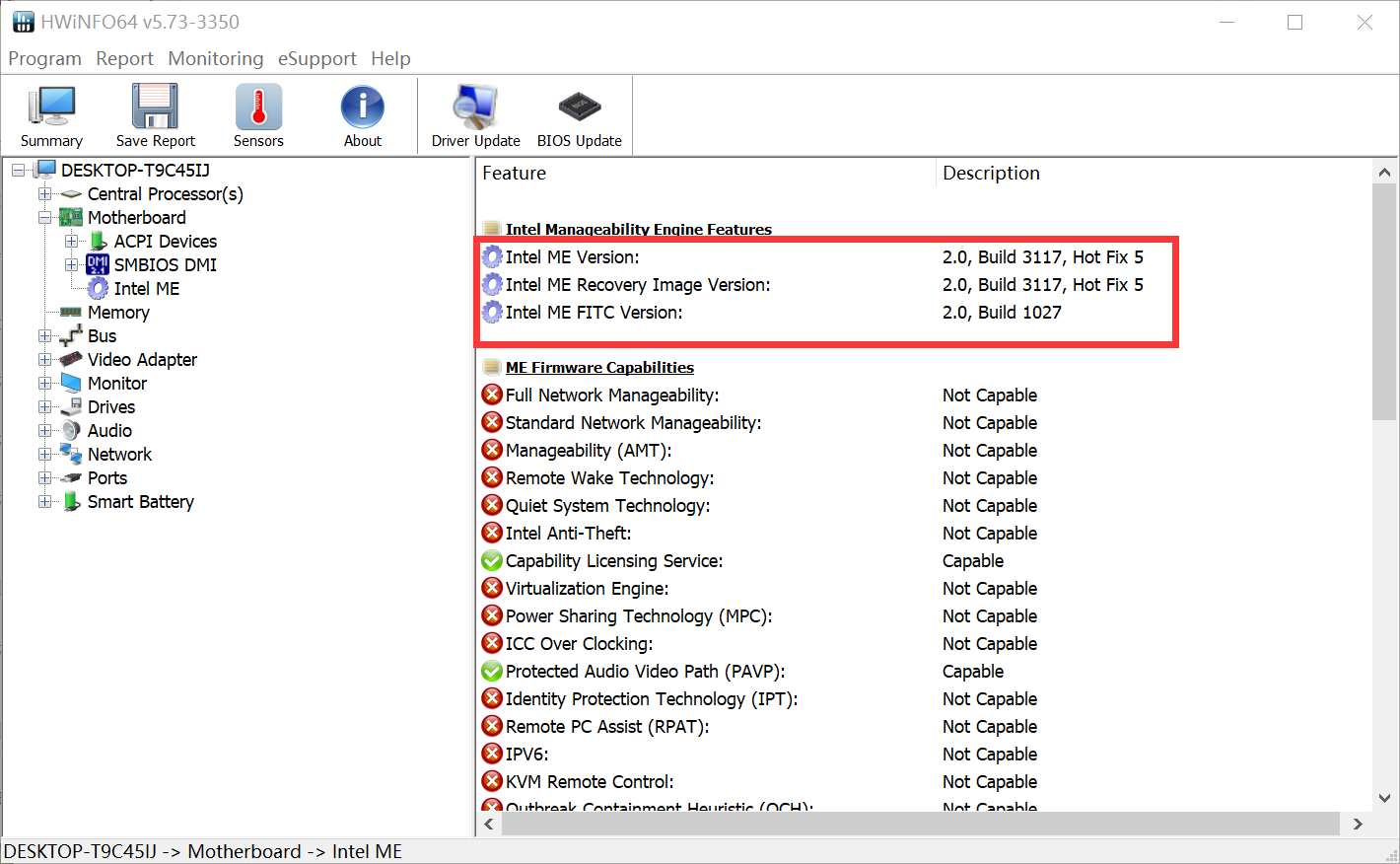
Hi! I’ve read the thread and made a conclusion that I can’t update TXE on my laptop by myself.
Me Analyzer info of my laptop:
I can do it only by updating bios, if my laptop manufacturer provide me updated bios, isn’t it?
Usually yes, only if the OEM has an updated SPI/BIOS. But it can also depend, what laptop model are we talking about?
Hi,Plutomaniac,excuse me,forgive my poor English,I have upgradged my TXE firmware successfully,thank you,but I have another question:I use HWiNFO64 to look Intel ME information,and the I find Intel ME Version and Intel ME Recovery Image Version is 2.0, Build 3117, Hot Fix 5,the same as I upgrade,but it is different from Intel ME FITC Version,it is just 2.0, Build 1027.What did I wrong in somewhere?Thank you very much.[[File:QQ??20180306015305.png|none|auto]]
Laptop model is Jumper EzBook 3 Pro - cheap chinese laptop from aliexpress. I think, that I wouldn’t have any BIOS updates from manufacturer (I try to request it, but no luck ![]() ). My aim is to eliminate intel-SA-00086 vulnerability by updating/editing bios of my laptop. Is there any chance to get TXE updated or disabled for my laptop?
). My aim is to eliminate intel-SA-00086 vulnerability by updating/editing bios of my laptop. Is there any chance to get TXE updated or disabled for my laptop?
@ xingyou12:
The FITC version does not matter as it’s the tool which adjusted the firmware settings.
@ Smartpol:
Do you have read/write access to the SPI/BIOS chip or a programmer which you can use? Please compress & attach a SPI/BIOS image for that model to see if the OEM used signing.
plutomaniac
Hi! Thanks for quick reply! I can use AfuEfix64.efi (I successfully made BIOS update with /P and /B keys for latest available BIOS, which I found at techtablets.com, but intel SA-00086 is still there ![]() ). The image of that BIOS is here 09_30_17_BIOS.zip in zip. I have ch341a programmer, but doesn’t sure, that it is compatible with my BIOS chip.
). The image of that BIOS is here 09_30_17_BIOS.zip in zip. I have ch341a programmer, but doesn’t sure, that it is compatible with my BIOS chip.
@ Smartpol:
The CSTXE firmware is signed but, in your specific case, not with an OEM key so hopefully I’ve updated it with CSTXE 3.1.50.2222 and re-signed it properly. I cannot guarantee that it will work but I think it will. So if you decide to test this, I suggest to make sure that you can recover via the programmer.
09_30_17_BIOS_fix.rar (3.75 MB)
I tried to update BIOS in built-in UEFI shell using “AfuEfix64.efi 09_30_17_BIOS_fix.bin /P /B” command as I did at previous update, every part of the updating process gave me ‘OK’ or ‘done’ result. After turning my laptop off I tried to turn it on but there was only black screen with power led light on. I think, that recover via the programmer is necessary but at first decide to try unplugging laptop battery. After this I try to power it on several times with strange behavior of power led without any display activity and viola! I got my laptop working with latest TXE firmware without intel SA-00086 vulnerability! Amazing! Big thanks for your help, plutomaniac!
P.S. 2 more questions:
1. How can I thank you more materially (maybe via paypal)?
2. Can I share this bios at techtablets with other people, who use this laptop?
Oh that’s great, you’re the first person to have updated the CSTXE 3 firmware in this forum since 2016, partially due to the fact that your SPI is not really signed. Yes, after reflashing the CSTXE firmware, the system must be reset. You can either do it by running “fptw -greset” after the reflash or manually by removing all power for 1 minute or so (AC + Battery, RTC is ok). Sometimes both are required and a few power on attempts to kick start the system again. So you did great as your perseverance to power it on proved that the signing worked.
By the way, aside from the updated CSTXE 3.1.50.2222 firmware which fixes INTEL-SA-00086, I also updated the CPU Microcode in order to add hardware fixes for Spectre variant 2 vulnerability (INTEL-SA-00088).
1. Thank you a lot for your offer. You can find a Paypal Donation button at my ME Analyzer or MC Extractor readme files over at github.
2. Yes of course. 
Thanks again, plutomaniac. I’ve just send you some support and thanks via paypal ![]()