Hi
I just want to change ram table pointer but when I change anything laptop boots twice with a bip and shuts down.
which is in this section of file
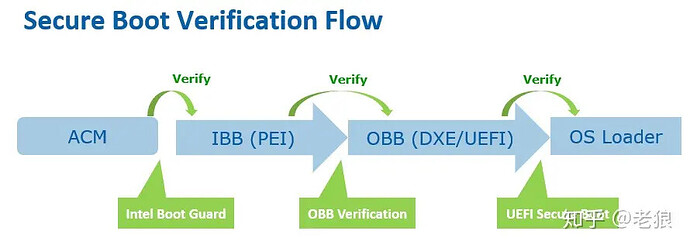
but I don’t how to bypass this bootguard. I have used intel fit in order to disable boot guard and some other settings to make it happen but still nothing helps
model: asus x513eqn
Thanks in advance.
Edit by Fernando: Thread moved into the “BIOS Problems” Sub-Category and thread title customized
Hi I appreciate your response
I thinks it’s not boot guard preventing from edit
I tried asus x513ea bios dump from internet and it booted up but some functions like charger didn’t work.
I can also put bootguard to profile 0 from intel fit tool and laptop boots fine.
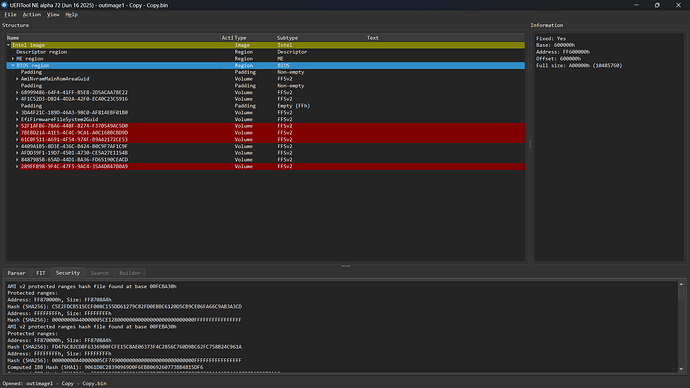
my guess is that aim v2 procetion is main reason
on uefi tool in security section it mentions
"
AMI v2 protected ranges hash file found at base 00FCBA30h
Protected ranges:
Address: FF870000h, Size: FF8708A4h
Hash (SHA256): C5E2FDCB515CCF008C155DD61279C82FD0EBBC6120D5CB9CE06FA66C9AB3A3CD
Address: FFFFFFFFh, Size: FFFFFFFFh
Hash (SHA256): 00000000A40000005CE12800000000000000000000000000FFFFFFFFFFFFFFFF
AMI v2 protected ranges hash file found at base 00FEBA30h
Protected ranges:
Address: FF870000h, Size: FF8708A4h
Hash (SHA256): FD476C82CD8F63369B0FCFE15C8AE06373F4C2856C760D9BC62FC758B24C961A
Address: FFFFFFFFh, Size: FFFFFFFFh
Hash (SHA256): 00000000A40000005CF74900000000000000000000000000FFFFFFFFFFFFFFFF
Computed IBB Hash (SHA1): 38BBA9CCCE42280AA65FDFE06646A8DCEB8E278E
Computed IBB Hash (SHA256): 0E0BD56E8BDCC40DB039F6A451835978AE7FB35AFB783CAA8A18713674D0630C
Computed IBB Hash (SHA384): 76981A7215310D08684E3E6D55979F9EA604794BD73510071F2B13E116A54DBEA9C67C6A36A1DAC690B65B874B6B2765
Computed IBB Hash (SHA512): C5FF57EAE6D4ECCA2D0C8A4D324FC8BE6590DA0E067E626176BD7739C0D089D3725C25063FBD78833E0140154CFC9C205D143E72F43EE9B16E79FBDA96049D2E
Computed IBB Hash (SM3): B6CC9BF21D42351B12C39C4590F162B1C13B6EF6A665AEC1C97462E46CD93042
Startup ACM found at base F80000h
ModuleType: 0002h
ModuleSubtype: 0001h
HeaderSize: 00000380h
HeaderVersion: 00030000h
ChipsetId: B00Ch
Flags: 0000h
ModuleVendor: 8086h
Date: 19.08.2022
ModuleSize: 00023000h
AcmSvn: 0007h
SeSvn: 0014h
CodeControlFlags: 00000000h
ErrorEntryPoint: 00000000h
GdtMax: 00000020h
GdtBase: 00003E40h
SegmentSel: 00000008h
EntryPoint: 0000E0EEh
KeySize: 00000180h
ScratchSpaceSize: 00000340h
ACM RSA Public Key Exponent: 10001h
ACM RSA Public Key:
EB3BB1A2D5404ED8EC8122FE5BF2955A6DAD5DB174C5F9B606F45748F04F6D44
13C9907B69B7589DDDE5E077C0C4C4E8797FDC2DDCF5A09BF2ABFFB38299B882
D9E7623D756FB43BE8D145E63AF7599F9C56594CCBA374862280A5EE710BDB15
639CFB24BBD9029C425D980C41EB2B3702D77886FEC1EA670B07C8590D3D4D5A
D6F26D3A754FC30DDD6B48F4C3608804AB72FFEDAAE9B98EA834CB6098F3807A
2B061DA4F7FE00C1ABC7D97BA450D35536241D733D0B1E606F2437C280EF4027
21B2A0A0EDA2705D7C1B0B6ADF58FB8B5FB67138C1F4BC3804A38C8C33CAE4D3
6313C01B2A48488BDFE043323804DDF0052EE576BF410AD004B36D79DAE02134
D7F9B900A602CC24FE5C90BB418D162AA063FF09E0187D0461153975167EAAD0
7F7343ACDEC2295F77F75005D47999B67B9E6D6EBA91851DE69FB63AE26ADEBA
4FA80C6FB053C6EC10B1DA05A06F60DE384AB4BB77053FF7E877099579AB94E8
FF997E0BFA8E0B3CC6DC61B085F0620F66F7D7F8C5C4A138CB251D1076760FB9
ACM RSA Signature:
E977EA90870F857D31FCB98E88A7B490C52A3054BBD38A84747200350079BB31
A6584E7FAE11FAC9BE37A9B4F338C0819ADAAE1365C5AB71C5E92654465CF6E3
8A80DB1F717024B2E4CD0258124885596AC8FA70BC1A54DFABF12FD26F569D2E
627EA514C3D069BAB3A8B1F3F0F58FED511F9092DBDEE04FAA46C86F19FE6DB2
2FBA8F058FDB5B1D1737AF332CFE0F6B264CDCDE5EA7752C24F5B9FFE9FFF4AD
C7B965C81E296388E7B18D53DD61CB7885987FB8F513F81E78206898C55A4FE3
CDDE356CF60664EC20BD5CC7EEDF0861950F46FB2CB6B08B3B3A4F34850E157C
AB45FC92CF1233C39BE55DFEA542D6B384AEE810364FB8B645315C7B45D89C1F
22B9A3F122123F63C5D23860139C8115FD0D0E8BCE7D0F061D50A8ADC3F654E3
28590F3F391E97F9F6FC253C2AED7287B928638134B996BCF2A18997DE3BFEA9
D111571A08A1AA2B1F38B3B8CCDB21664318391E12E2AA7EBFDCBC65427870CD
FD70136F6EF9E5DA81330A00A15805FBA6709A92982300B3CC552CB2BC835917
"
is aim v2 impossible to bypass too?