The Thinkpad T14 G4 in the linked post had the 64/16 MByte configuration you mentioned. Even if you can find sources / relations for all the code and data duplicates, it’s unclear where hashes are stored. Lenovo’s known for having a security chip / using parts of the EC- chip as secure storage, now they might have hardware TPM in addition.
And that Tp T14 G4 had a discrete TPM and some hints that it’s been used for the duplicate data:
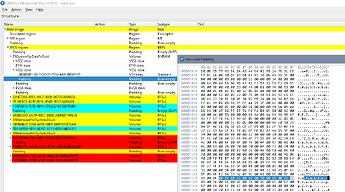
In addition there’s the second VSS2 store which looks kinda corrupted / unstructured in UEFIToolNE, but stores data related to recovery / tampering:
This store har references to parts of the 16 MByte file and the TPM (pics from the machine in this thread)
I’m mostly interested in recovery of these firmware images, but even emptying NVRAM or cleaning an ME seems almost impossible for these configurations.