First of all, i dont know what you’re flashing (26MB??? bios region only…?) or what cmd used…
I did told you to test it, writing right back the bios_region dump, in ealier post
fpt -bios -d bios_region , will retrieve a dump of bios region
If FD grants write access, this previous dump: fpt -bios -f bios_region
If these 2 operations were successful, then we know that FPT can write/flash the modded bios_region you dumped and performed the mods.
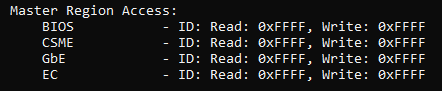
Read it to understand it…
And dont ask me about “ifdtool”, no expertise with it whatsoever.
What you’re trying to achieve i have no similar system or yet done similar operation in such HW generation… with such modern Bios(AMI v2 protected ranges)/ME16.1, just to let you know…
EDIT: Then if after that “AltMEDisable bit change” still cant write the bios region. its still OEM locked. Research it on the forum or outside for similar operations… i dint thought this would be easy and you shouldn’t also.
Make new posts/requests on specific/isolated operations/issues and wait for other users help.
Pont B of the linked guide show us the bits… in earlier hw generations i know that some users edit them in ME package tools/FIT tool…but this the latest 16.1 …
There were bios with BIOS Lock, CFG Lock etc… in hidden menus, these were also used.
EDIT: No… not useful on your operation, BIOS REGION MASTER ACCESS (fpt -i report), this is what we want.