lfb6
July 12, 2024, 6:10am
15
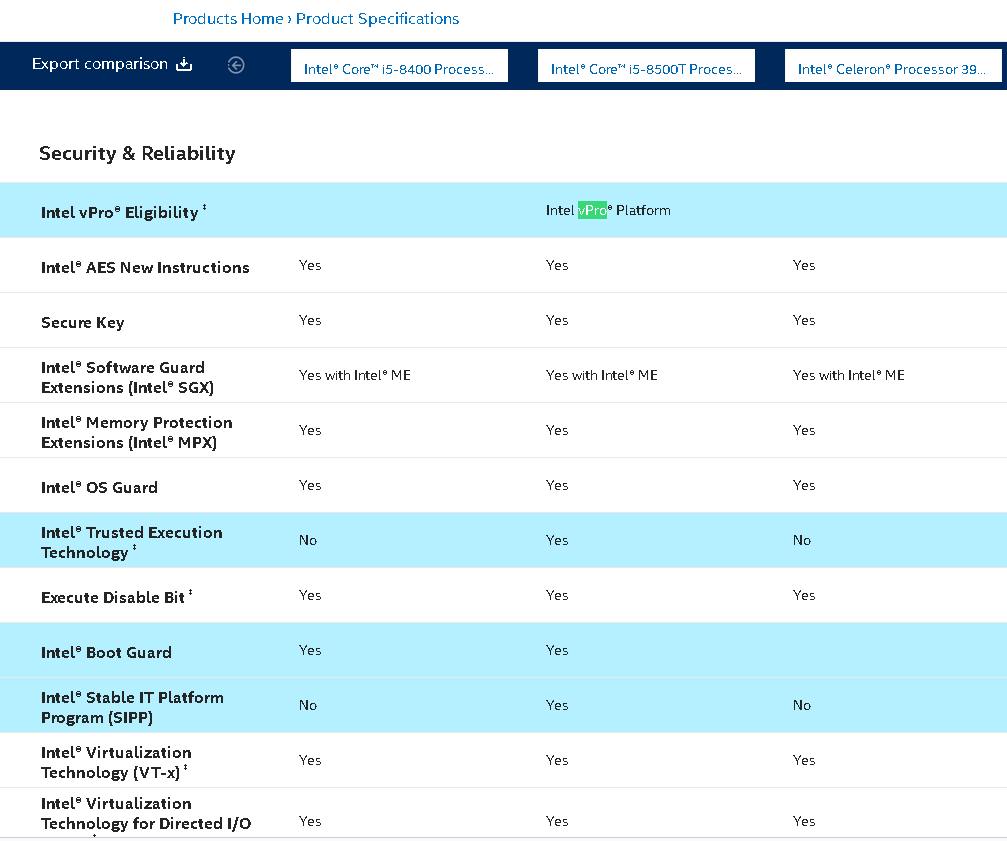
Not with a Celeron.
Hwinfo gives more detailed information:
Unfortunately Intel doesn’t any longer list all the capabilities of a processor family for a cpu but lists a capability only if the processor does have it.
I you are very interested you may open your dump in FIT or rund MEInfo on your machine
Intel (Converged Security) Management Engine: Drivers, Firmware and Tools for (CS)ME 2-15 Last Updated: 2022-09-08
Intel Management Engine Introduction: Built into many Intel-based platforms is a small, low power computer subsystem called the Intel Management Engine (Intel ME). This can perform various tasks while the system is booting, running or sleeping. It operates independently from the main CPU, BIOS and OS but can interact with them if needed. The ME is responsible for many parts of a…