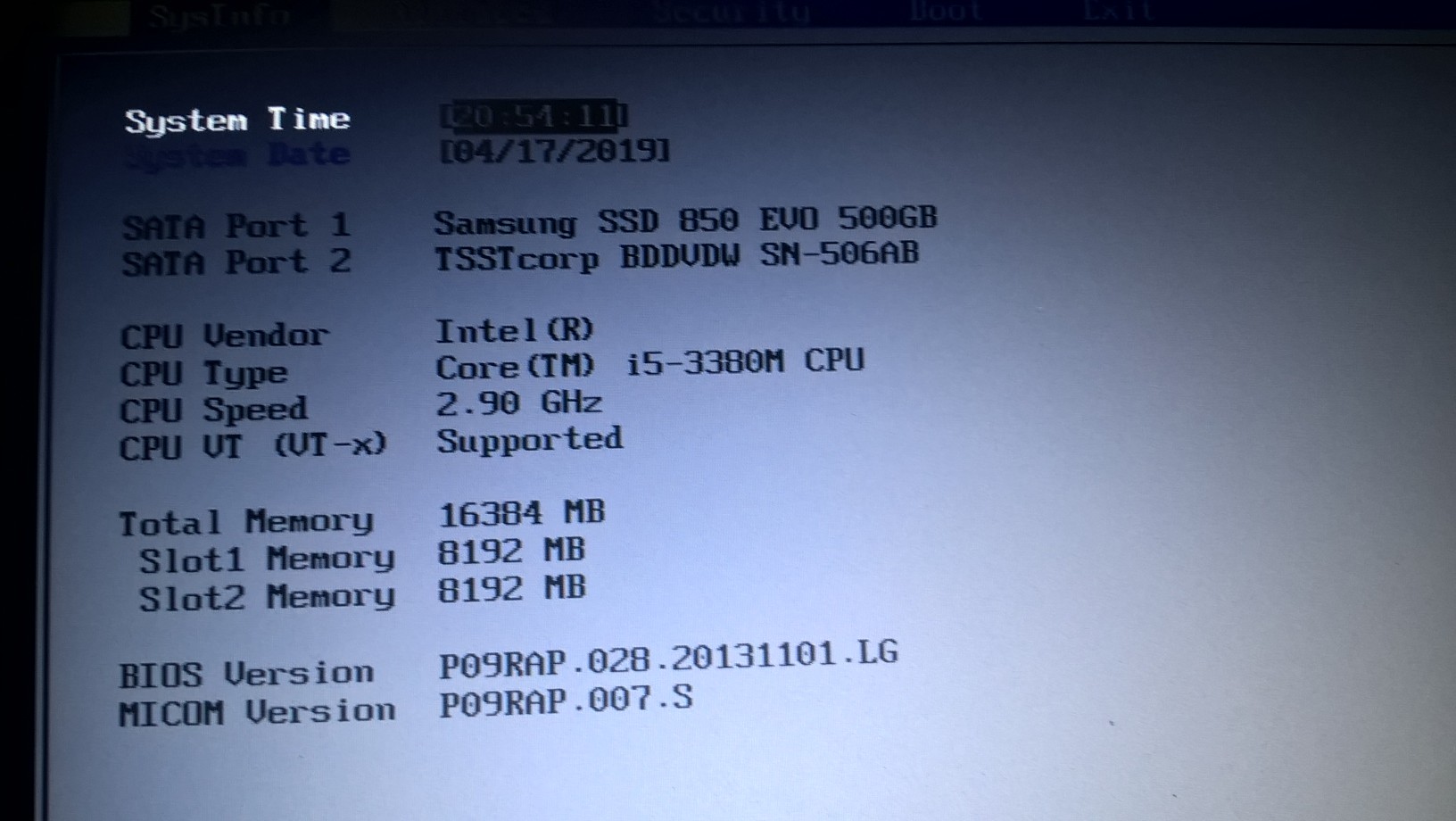
Thanks for your answer! Of course there are many ways to update this bios and for most of us it might feel a lot safer to flash a complete bios they could check beforehand!
I ran into another "problem;: The older NP300E5A HM65 Notebook has a switch to enable SATA GEN3 Mode on the first SATA port. The newer NP300E5C (HM75) dosn’t have that switch and the default is SATA2 (3Gb/s) I’m afraid I won’t ‘feel’ the difference, but it feels better anyway and I learned a little about EFI- shell and EFI- variables…
I read a lot about EFI variables and how to enable advanced menus in bios- but I’d have to admit: No clear understandig so far
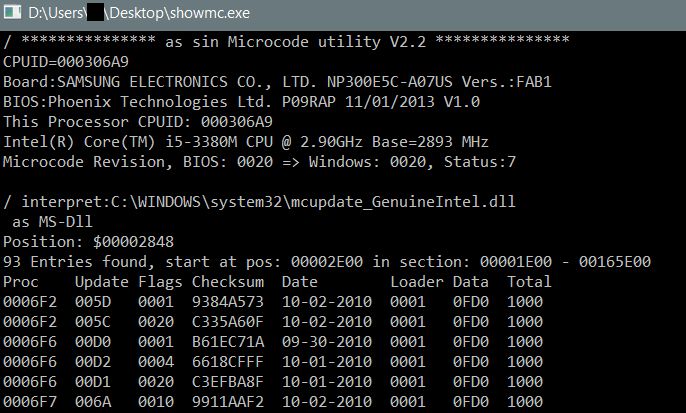
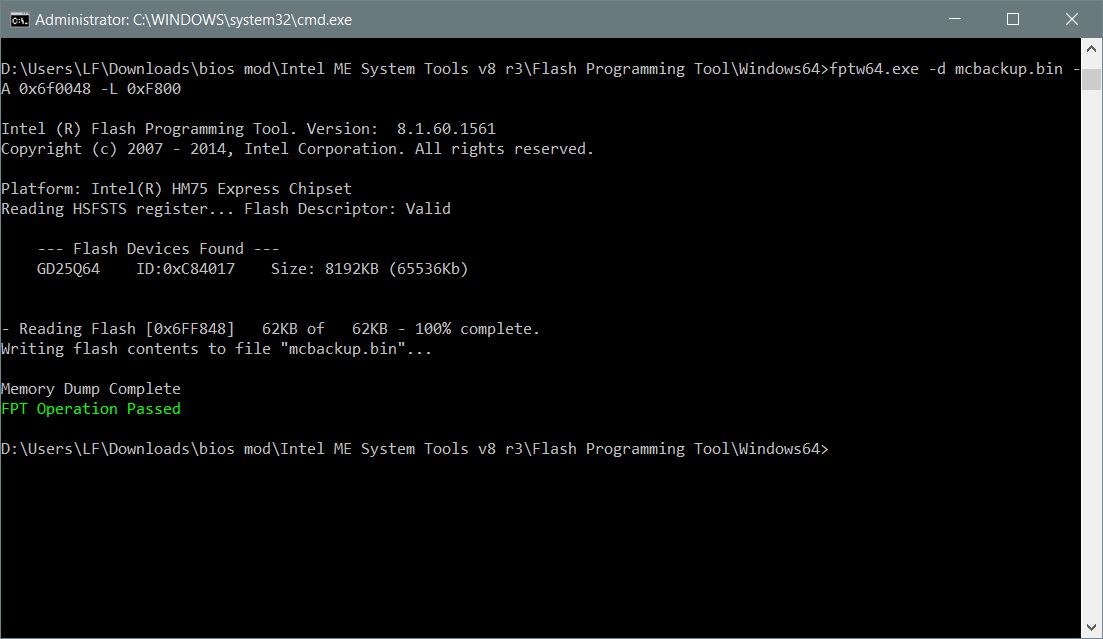
- Backup the bios: fptw64 -bios -d backup.rom
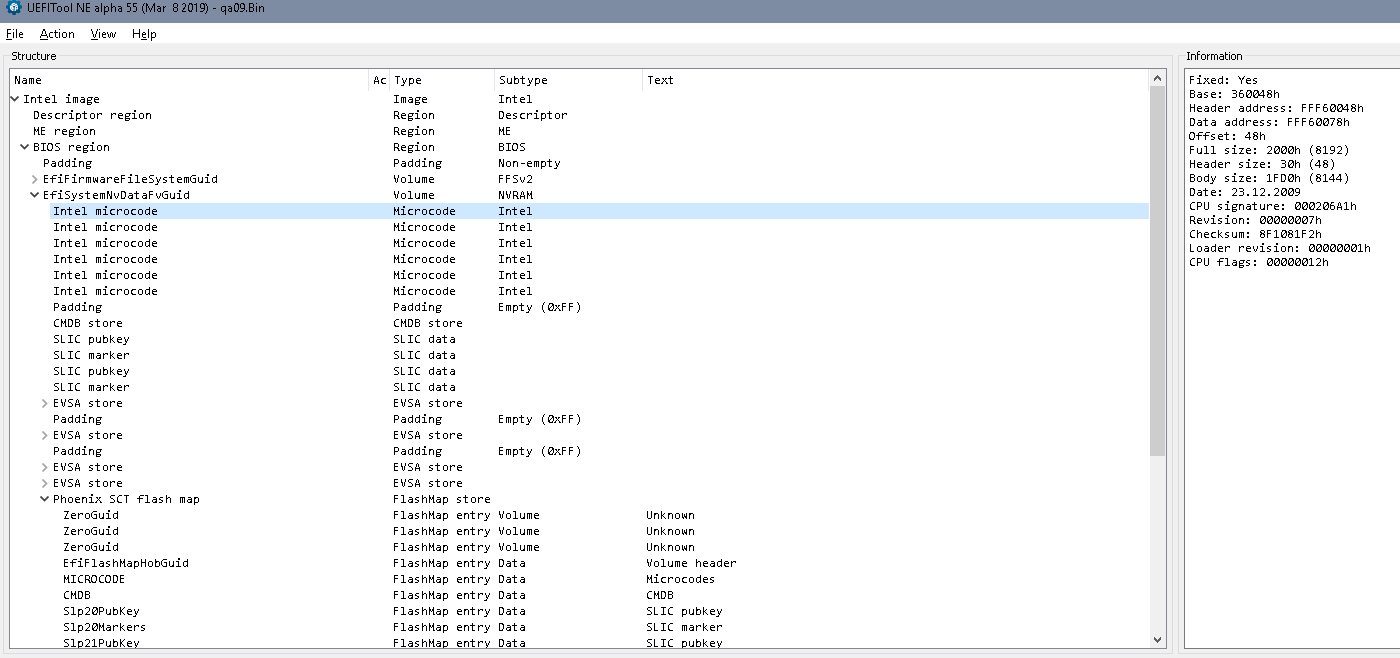
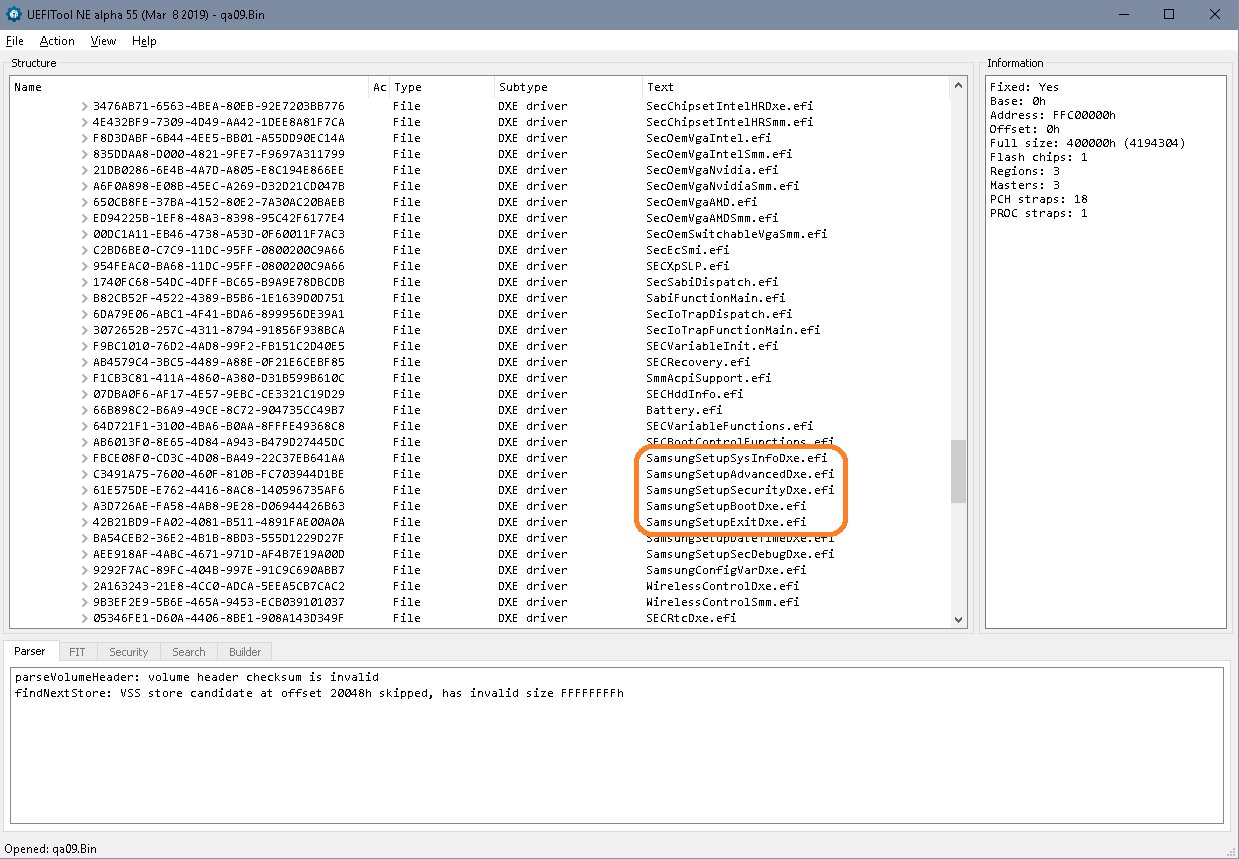
- Find the settings store for the advanced settings- searched the backup with UEFItool NE for GEN3 and found 3 regions
A. C3491A75-7600-460F-810B-FC703944D1BE SamsungSetupAdvancedDxe.efi
B. 2D6F37BF-9AFC-4AA5-A026-32B2FCF30FB9 PlatformDxe.efi
C. CFEF94C4-4167-466A-8893-8779459DFA86 PlatformHiiAdvancedDxe.efi
- Extracted all these regions, ran Donovans Universal IFR Extractor-0.7 over them and got
for B) almost no forms
for C) not SATA but PEG, but
A) has the advanced settings!
SATA GEN3 Mode
Suppress If {0A 82}
64 Bit Unsigned Int: 0x1 {45 0A 01 00 00 00 00 00 00 00}
Gray Out If {19 82}
Security: Permissions: [85B75607-F7CE-471E-B7E4-2AEA5F7232EE] {60 92 07 56 B7 85 CE F7 1E 47 B7 E4 2A EA 5F 72 32 EE}
Not {17 02}
End {29 02}
One Of: SATA GEN3 Mode, VarStoreInfo (VarOffset/VarName): 0x148, VarStore: 0x6, QuestionId: 0xD, Size: 1, Min: 0x0, Max 0xFF, Step: 0x0 {05 A6 17 00 18 00 0D 00 06 00 48 01 00 10 00 FF 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00}
One Of Option: Disabled, Value (8 bit): 0x2 (default) {09 0E 2C 00 10 00 02 00 00 00 00 00 00 00}
One Of Option: Enabled, Value (8 bit): 0x3 {09 0E 2B 00 00 00 03 00 00 00 00 00 00 00}
End One Of {29 02}
End If {29 02}
End If {29 02}
complete output
UEFI Protocol Detected
String Packages
Offset: Language:
0x35C en-US (0x0)
0x1769 fr-FR (0x1)
0x17B4 ja-JP (0x2)
0x17F5 ko-KR (0x3)
0x18BE ru-RU (0x4)
Form Sets
Offset: Title:
0x190C Advanced (0x2 from string package 0x0)
Internal Forms Representation
Offset: Instruction:
0x1910 Form Set: Advanced [5FB10979-5AE2-4622-A98E-270956BB8D35], ClassGuid0 [93039971-8545-4B04-B45E-32EB8326040E] {0E A7 79 09 B1 5F E2 5A 22 46 A9 8E 27 09 56 BB 8D 35 02 00 2A 00 01 71 99 03 93 45 85 04 4B B4 5E 32 EB 83 26 04 0E}
0x1937 Guid: [0F0B1735-87A0-4193-B266-538C38AF48CE] {5F 15 35 17 0B 0F A0 87 93 41 B2 66 53 8C 38 AF 48 CE 03 01 00}
0x194C Guid: [0F0B1735-87A0-4193-B266-538C38AF48CE] {5F 15 35 17 0B 0F A0 87 93 41 B2 66 53 8C 38 AF 48 CE 04 00 00}
0x1961 Default Store: en-US, DefaultId: 0x0 {5C 06 00 00 00 00}
0x1967 Default Store: en-US, DefaultId: 0x1 {5C 06 00 00 01 00}
0x196D VarStore: VarStoreId: 0x1 [5FB10979-5AE2-4622-A98E-270956BB8D35], Size: 0x5, Name: ADVANCED_INFO {24 24 79 09 B1 5F E2 5A 22 46 A9 8E 27 09 56 BB 8D 35 01 00 05 00 41 44 56 41 4E 43 45 44 5F 49 4E 46 4F 00}
0x1991 VarStore: VarStoreId: 0x2 [E6A849B2-36EC-4C2F-9B84-CD89907EECB1], Size: 0xA0, Name: SamsungSetup {24 23 B2 49 A8 E6 EC 36 2F 4C 9B 84 CD 89 90 7E EC B1 02 00 A0 00 53 61 6D 73 75 6E 67 53 65 74 75 70 00}
0x19B4 VarStore: VarStoreId: 0x3 [E947FCF9-DD01-4965-B808-32A7B6815657], Size: 0x46, Name: System {24 1D F9 FC 47 E9 01 DD 65 49 B8 08 32 A7 B6 81 56 57 03 00 46 00 53 79 73 74 65 6D 00}
0x19D1 VarStore: VarStoreId: 0x4 [7D4ADCE1-930D-40C7-9CD2-6D2148413DC7], Size: 0x33, Name: CpuProtocolSetupVar {24 2A E1 DC 4A 7D 0D 93 C7 40 9C D2 6D 21 48 41 3D C7 04 00 33 00 43 70 75 50 72 6F 74 6F 63 6F 6C 53 65 74 75 70 56 61 72 00}
0x19FB VarStore: VarStoreId: 0x5 [4DFBBAAB-1392-4FDE-ABB8-C41CC5AD7D5D], Size: 0x105, Name: Setup {24 1C AB BA FB 4D 92 13 DE 4F AB B8 C4 1C C5 AD 7D 5D 05 00 05 01 53 65 74 75 70 00}
0x1A17 VarStore: VarStoreId: 0x6 [04BD8413-15F9-43F3-9675-4618E03240E3], Size: 0x224, Name: PchProtocolSetupVar {24 2A 13 84 BD 04 F9 15 F3 43 96 75 46 18 E0 32 40 E3 06 00 24 02 50 63 68 50 72 6F 74 6F 63 6F 6C 53 65 74 75 70 56 61 72 00}
0x1A41 Form: Advanced, FormId: 0x1 {01 86 01 00 02 00}
0x1A47 Suppress If {0A 82}
0x1A49 True {46 02}
0x1A4B One Of: , VarStoreInfo (VarOffset/VarName): 0x2, VarStore: 0x1, QuestionId: 0x1, Size: 1, Min: 0x0, Max 0x0, Step: 0x0 {05 A6 2A 00 2A 00 01 00 01 00 02 00 00 10 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00}
0x1A71 One Of Option: , Value (8 bit): 0x0 {09 0E 2A 00 00 00 00 00 00 00 00 00 00 00}
0x1A7F End One Of {29 02}
0x1A81 End If {29 02}
0x1A83 Suppress If {0A 82}
0x1A85 True {46 02}
0x1A87 One Of: , VarStoreInfo (VarOffset/VarName): 0x3, VarStore: 0x1, QuestionId: 0x2, Size: 1, Min: 0x0, Max 0x0, Step: 0x0 {05 A6 2A 00 2A 00 02 00 01 00 03 00 00 10 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00}
0x1AAD One Of Option: , Value (8 bit): 0x0 {09 0E 2A 00 00 00 00 00 00 00 00 00 00 00}
0x1ABB End One Of {29 02}
0x1ABD End If {29 02}
0x1ABF Suppress If {0A 82}
0x1AC1 QuestionId: 0x1 equals value 0x0 {12 86 01 00 00 00}
0x1AC7 QuestionId: 0x2 equals value 0x0 {12 06 02 00 00 00}
0x1ACD And {15 02}
0x1ACF End {29 02}
0x1AD1 Gray Out If {19 82}
0x1AD3 Security: Permissions: [85B75607-F7CE-471E-B7E4-2AEA5F7232EE] {60 92 07 56 B7 85 CE F7 1E 47 B7 E4 2A EA 5F 72 32 EE}
0x1AE5 Not {17 02}
0x1AE7 End {29 02}
0x1AE9 One Of: CPU Power Saving Mode, VarStoreInfo (VarOffset/VarName): 0x20, VarStore: 0x2, QuestionId: 0x3, Size: 1, Min: 0x0, Max 0x1, Step: 0x0 {05 A6 03 00 04 00 03 00 02 00 20 00 00 10 00 01 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00}
0x1B0F One Of Option: Disabled, Value (8 bit): 0x0 {09 0E 2C 00 00 00 00 00 00 00 00 00 00 00}
0x1B1D One Of Option: Enabled, Value (8 bit): 0x1 (default) {09 0E 2B 00 10 00 01 00 00 00 00 00 00 00}
0x1B2B End One Of {29 02}
0x1B2D End If {29 02}
0x1B2F End If {29 02}
0x1B31 Suppress If {0A 82}
0x1B33 True {46 02}
0x1B35 One Of: , VarStoreInfo (VarOffset/VarName): 0x4, VarStore: 0x1, QuestionId: 0x4, Size: 1, Min: 0x0, Max 0x0, Step: 0x0 {05 A6 2A 00 2A 00 04 00 01 00 04 00 00 10 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00}
0x1B5B One Of Option: , Value (8 bit): 0x0 {09 0E 2A 00 00 00 00 00 00 00 00 00 00 00}
0x1B69 End One Of {29 02}
0x1B6B End If {29 02}
0x1B6D Suppress If {0A 82}
0x1B6F QuestionId: 0x4 equals value 0x0 {12 06 04 00 00 00}
0x1B75 Gray Out If {19 82}
0x1B77 Security: Permissions: [85B75607-F7CE-471E-B7E4-2AEA5F7232EE] {60 92 07 56 B7 85 CE F7 1E 47 B7 E4 2A EA 5F 72 32 EE}
0x1B89 Not {17 02}
0x1B8B End {29 02}
0x1B8D One Of: Hyperthreading, VarStoreInfo (VarOffset/VarName): 0x0, VarStore: 0x4, QuestionId: 0x5, Size: 1, Min: 0x0, Max 0x1, Step: 0x0 {05 A6 05 00 06 00 05 00 04 00 00 00 00 10 00 01 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00}
0x1BB3 One Of Option: Disabled, Value (8 bit): 0x0 {09 0E 2C 00 00 00 00 00 00 00 00 00 00 00}
0x1BC1 One Of Option: Enabled, Value (8 bit): 0x1 (default) {09 0E 2B 00 10 00 01 00 00 00 00 00 00 00}
0x1BCF End One Of {29 02}
0x1BD1 End If {29 02}
0x1BD3 End If {29 02}
0x1BD5 Gray Out If {19 82}
0x1BD7 Security: Permissions: [85B75607-F7CE-471E-B7E4-2AEA5F7232EE] {60 92 07 56 B7 85 CE F7 1E 47 B7 E4 2A EA 5F 72 32 EE}
0x1BE9 Not {17 02}
0x1BEB End {29 02}
0x1BED One Of: EDB (Execute Disable Bit), VarStoreInfo (VarOffset/VarName): 0x3, VarStore: 0x4, QuestionId: 0x6, Size: 1, Min: 0x0, Max 0x1, Step: 0x0 {05 A6 07 00 08 00 06 00 04 00 03 00 00 10 00 01 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00}
0x1C13 One Of Option: Disabled, Value (8 bit): 0x0 {09 0E 2C 00 00 00 00 00 00 00 00 00 00 00}
0x1C21 One Of Option: Enabled, Value (8 bit): 0x1 (default) {09 0E 2B 00 10 00 01 00 00 00 00 00 00 00}
0x1C2F End One Of {29 02}
0x1C31 End If {29 02}
0x1C33 Gray Out If {19 82}
0x1C35 True {46 02}
0x1C37 Text: Statement.Prompt: , TextTwo: en-US {03 08 2A 00 2A 00 00 00}
0x1C3F End If {29 02}
0x1C41 Suppress If {0A 82}
0x1C43 True {46 02}
0x1C45 One Of: , VarStoreInfo (VarOffset/VarName): 0x0, VarStore: 0x1, QuestionId: 0x7, Size: 1, Min: 0x0, Max 0x0, Step: 0x0 {05 A6 2A 00 2A 00 07 00 01 00 00 00 00 10 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00}
0x1C6B One Of Option: , Value (8 bit): 0x0 {09 0E 2A 00 00 00 00 00 00 00 00 00 00 00}
0x1C79 End One Of {29 02}
0x1C7B End If {29 02}
0x1C7D Suppress If {0A 82}
0x1C7F QuestionId: 0x7 equals value 0x1 {12 06 07 00 01 00}
0x1C85 Gray Out If {19 82}
0x1C87 Security: Permissions: [85B75607-F7CE-471E-B7E4-2AEA5F7232EE] {60 92 07 56 B7 85 CE F7 1E 47 B7 E4 2A EA 5F 72 32 EE}
0x1C99 Not {17 02}
0x1C9B End {29 02}
0x1C9D One Of: Fast BIOS Mode, VarStoreInfo (VarOffset/VarName): 0x1C, VarStore: 0x3, QuestionId: 0x8, Size: 1, Min: 0x0, Max 0x1, Step: 0x0 {05 A6 0F 00 10 00 08 00 03 00 1C 00 00 10 00 01 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00}
0x1CC3 One Of Option: Disabled, Value (8 bit): 0x1 (default) {09 0E 2C 00 10 00 01 00 00 00 00 00 00 00}
0x1CD1 One Of Option: Enabled, Value (8 bit): 0x0 {09 0E 2B 00 00 00 00 00 00 00 00 00 00 00}
0x1CDF End One Of {29 02}
0x1CE1 End If {29 02}
0x1CE3 End If {29 02}
0x1CE5 Suppress If {0A 82}
0x1CE7 True {46 02}
0x1CE9 One Of: , VarStoreInfo (VarOffset/VarName): 0x0, VarStore: 0x1, QuestionId: 0x9, Size: 1, Min: 0x0, Max 0x0, Step: 0x0 {05 A6 2A 00 2A 00 09 00 01 00 00 00 00 10 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00}
0x1D0F One Of Option: , Value (8 bit): 0x0 {09 0E 2A 00 00 00 00 00 00 00 00 00 00 00}
0x1D1D End One Of {29 02}
0x1D1F End If {29 02}
0x1D21 Suppress If {0A 82}
0x1D23 QuestionId: 0x9 equals value 0x0 {12 06 09 00 00 00}
0x1D29 Gray Out If {19 82}
0x1D2B Security: Permissions: [85B75607-F7CE-471E-B7E4-2AEA5F7232EE] {60 92 07 56 B7 85 CE F7 1E 47 B7 E4 2A EA 5F 72 32 EE}
0x1D3D Not {17 02}
0x1D3F End {29 02}
0x1D41 One Of: Fast BIOS Mode, VarStoreInfo (VarOffset/VarName): 0x2A, VarStore: 0x2, QuestionId: 0xA, Size: 1, Min: 0x0, Max 0x1, Step: 0x0 {05 A6 0F 00 10 00 0A 00 02 00 2A 00 00 10 00 01 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00}
0x1D67 One Of Option: Disabled, Value (8 bit): 0x1 {09 0E 2C 00 00 00 01 00 00 00 00 00 00 00}
0x1D75 One Of Option: Enabled, Value (8 bit): 0x0 (default) {09 0E 2B 00 10 00 00 00 00 00 00 00 00 00}
0x1D83 End One Of {29 02}
0x1D85 End If {29 02}
0x1D87 End If {29 02}
0x1D89 Gray Out If {19 82}
0x1D8B Security: Permissions: [85B75607-F7CE-471E-B7E4-2AEA5F7232EE] {60 92 07 56 B7 85 CE F7 1E 47 B7 E4 2A EA 5F 72 32 EE}
0x1D9D Not {17 02}
0x1D9F End {29 02}
0x1DA1 One Of: AHCI Mode Control, VarStoreInfo (VarOffset/VarName): 0x22, VarStore: 0x2, QuestionId: 0xB, Size: 1, Min: 0x0, Max 0x1, Step: 0x0 {05 A6 11 00 12 00 0B 00 02 00 22 00 00 10 00 01 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00}
0x1DC7 One Of Option: Auto, Value (8 bit): 0x0 (default) {09 0E 13 00 10 00 00 00 00 00 00 00 00 00}
0x1DD5 One Of Option: Manual, Value (8 bit): 0x1 {09 0E 14 00 00 00 01 00 00 00 00 00 00 00}
0x1DE3 End One Of {29 02}
0x1DE5 End If {29 02}
0x1DE7 Suppress If {0A 82}
0x1DE9 QuestionId: 0xB equals value 0x0 {12 06 0B 00 00 00}
0x1DEF Gray Out If {19 82}
0x1DF1 Security: Permissions: [85B75607-F7CE-471E-B7E4-2AEA5F7232EE] {60 92 07 56 B7 85 CE F7 1E 47 B7 E4 2A EA 5F 72 32 EE}
0x1E03 Not {17 02}
0x1E05 End {29 02}
0x1E07 One Of: Set AHCI Mode, VarStoreInfo (VarOffset/VarName): 0x12, VarStore: 0x5, QuestionId: 0xC, Size: 1, Min: 0x0, Max 0x1, Step: 0x0 {05 A6 15 00 16 00 0C 00 05 00 12 00 00 10 00 01 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00}
0x1E2D One Of Option: Disabled, Value (8 bit): 0x0 {09 0E 2C 00 00 00 00 00 00 00 00 00 00 00}
0x1E3B One Of Option: Enabled, Value (8 bit): 0x1 (default) {09 0E 2B 00 10 00 01 00 00 00 00 00 00 00}
0x1E49 End One Of {29 02}
0x1E4B End If {29 02}
0x1E4D End If {29 02}
0x1E4F Suppress If {0A 82}
0x1E51 64 Bit Unsigned Int: 0x1 {45 0A 01 00 00 00 00 00 00 00}
0x1E5B Gray Out If {19 82}
0x1E5D Security: Permissions: [85B75607-F7CE-471E-B7E4-2AEA5F7232EE] {60 92 07 56 B7 85 CE F7 1E 47 B7 E4 2A EA 5F 72 32 EE}
0x1E6F Not {17 02}
0x1E71 End {29 02}
0x1E73 One Of: SATA GEN3 Mode, VarStoreInfo (VarOffset/VarName): 0x148, VarStore: 0x6, QuestionId: 0xD, Size: 1, Min: 0x0, Max 0xFF, Step: 0x0 {05 A6 17 00 18 00 0D 00 06 00 48 01 00 10 00 FF 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00}
0x1E99 One Of Option: Disabled, Value (8 bit): 0x2 (default) {09 0E 2C 00 10 00 02 00 00 00 00 00 00 00}
0x1EA7 One Of Option: Enabled, Value (8 bit): 0x3 {09 0E 2B 00 00 00 03 00 00 00 00 00 00 00}
0x1EB5 End One Of {29 02}
0x1EB7 End If {29 02}
0x1EB9 End If {29 02}
0x1EBB Gray Out If {19 82}
0x1EBD True {46 02}
0x1EBF Text: Statement.Prompt: , TextTwo: en-US {03 08 2A 00 2A 00 00 00}
0x1EC7 End If {29 02}
0x1EC9 Suppress If {0A 82}
0x1ECB 64 Bit Unsigned Int: 0x1 {45 0A 01 00 00 00 00 00 00 00}
0x1ED5 Gray Out If {19 82}
0x1ED7 Security: Permissions: [85B75607-F7CE-471E-B7E4-2AEA5F7232EE] {60 92 07 56 B7 85 CE F7 1E 47 B7 E4 2A EA 5F 72 32 EE}
0x1EE9 Not {17 02}
0x1EEB End {29 02}
0x1EED One Of: Fan Silent Mode, VarStoreInfo (VarOffset/VarName): 0x23, VarStore: 0x2, QuestionId: 0xE, Size: 1, Min: 0x0, Max 0x1, Step: 0x0 {05 A6 19 00 1A 00 0E 00 02 00 23 00 00 10 00 01 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00}
0x1F13 One Of Option: Low, Value (8 bit): 0x0 {09 0E 1B 00 00 00 00 00 00 00 00 00 00 00}
0x1F21 One Of Option: Auto, Value (8 bit): 0x1 (default) {09 0E 1C 00 10 00 01 00 00 00 00 00 00 00}
0x1F2F End One Of {29 02}
0x1F31 End If {29 02}
0x1F33 End If {29 02}
0x1F35 Gray Out If {19 82}
0x1F37 Security: Permissions: [85B75607-F7CE-471E-B7E4-2AEA5F7232EE] {60 92 07 56 B7 85 CE F7 1E 47 B7 E4 2A EA 5F 72 32 EE}
0x1F49 Not {17 02}
0x1F4B End {29 02}
0x1F4D One Of: Battery Life Cycle Extension, VarStoreInfo (VarOffset/VarName): 0x25, VarStore: 0x2, QuestionId: 0xF, Size: 1, Min: 0x0, Max 0x1, Step: 0x0 {05 A6 1D 00 1E 00 0F 00 02 00 25 00 00 10 00 01 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00}
0x1F73 One Of Option: Disabled, Value (8 bit): 0x0 (default) {09 0E 2C 00 10 00 00 00 00 00 00 00 00 00}
0x1F81 One Of Option: Enabled, Value (8 bit): 0x1 {09 0E 2B 00 00 00 01 00 00 00 00 00 00 00}
0x1F8F End One Of {29 02}
0x1F91 End If {29 02}
0x1F93 Suppress If {0A 82}
0x1F95 64 Bit Unsigned Int: 0x0 {45 8A 00 00 00 00 00 00 00 00}
0x1F9F 64 Bit Unsigned Int: 0x0 {45 0A 00 00 00 00 00 00 00 00}
0x1FA9 Equal {2F 02}
0x1FAB End {29 02}
0x1FAD Gray Out If {19 82}
0x1FAF Security: Permissions: [85B75607-F7CE-471E-B7E4-2AEA5F7232EE] {60 92 07 56 B7 85 CE F7 1E 47 B7 E4 2A EA 5F 72 32 EE}
0x1FC1 Not {17 02}
0x1FC3 End {29 02}
0x1FC5 One Of: USB Charge In Sleep Mode, VarStoreInfo (VarOffset/VarName): 0x24, VarStore: 0x2, QuestionId: 0x10, Size: 1, Min: 0x0, Max 0x1, Step: 0x0 {05 A6 1F 00 20 00 10 00 02 00 24 00 00 10 00 01 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00}
0x1FEB One Of Option: Disabled, Value (8 bit): 0x0 (default) {09 0E 2C 00 10 00 00 00 00 00 00 00 00 00}
0x1FF9 One Of Option: Enabled, Value (8 bit): 0x1 {09 0E 2B 00 00 00 01 00 00 00 00 00 00 00}
0x2007 End One Of {29 02}
0x2009 End If {29 02}
0x200B End If {29 02}
0x200D Gray Out If {19 82}
0x200F Security: Permissions: [85B75607-F7CE-471E-B7E4-2AEA5F7232EE] {60 92 07 56 B7 85 CE F7 1E 47 B7 E4 2A EA 5F 72 32 EE}
0x2021 Not {17 02}
0x2023 End {29 02}
0x2025 One Of: USB S3 Wake-up, VarStoreInfo (VarOffset/VarName): 0x26, VarStore: 0x2, QuestionId: 0x11, Size: 1, Min: 0x0, Max 0x1, Step: 0x0 {05 A6 21 00 22 00 11 00 02 00 26 00 00 10 00 01 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00}
0x204B One Of Option: Disabled, Value (8 bit): 0x0 (default) {09 0E 2C 00 10 00 00 00 00 00 00 00 00 00}
0x2059 One Of Option: Enabled, Value (8 bit): 0x1 {09 0E 2B 00 00 00 01 00 00 00 00 00 00 00}
0x2067 End One Of {29 02}
0x2069 End If {29 02}
0x206B Suppress If {0A 82}
0x206D True {46 02}
0x206F Gray Out If {19 82}
0x2071 Security: Permissions: [85B75607-F7CE-471E-B7E4-2AEA5F7232EE] {60 92 07 56 B7 85 CE F7 1E 47 B7 E4 2A EA 5F 72 32 EE}
0x2083 Not {17 02}
0x2085 End {29 02}
0x2087 One Of: LID Open S3 Wake-up, VarStoreInfo (VarOffset/VarName): 0x27, VarStore: 0x2, QuestionId: 0x12, Size: 1, Min: 0x0, Max 0x1, Step: 0x0 {05 A6 23 00 24 00 12 00 02 00 27 00 00 10 00 01 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00}
0x20AD One Of Option: Disabled, Value (8 bit): 0x0 (default) {09 0E 2C 00 10 00 00 00 00 00 00 00 00 00}
0x20BB One Of Option: Enabled, Value (8 bit): 0x1 {09 0E 2B 00 00 00 01 00 00 00 00 00 00 00}
0x20C9 End One Of {29 02}
0x20CB End If {29 02}
0x20CD End If {29 02}
0x20CF Suppress If {0A 82}
0x20D1 True {46 02}
0x20D3 One Of: , VarStoreInfo (VarOffset/VarName): 0x0, VarStore: 0x1, QuestionId: 0x13, Size: 1, Min: 0x0, Max 0x0, Step: 0x0 {05 A6 2A 00 2A 00 13 00 01 00 00 00 00 10 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00}
0x20F9 One Of Option: , Value (8 bit): 0x0 {09 0E 2A 00 00 00 00 00 00 00 00 00 00 00}
0x2107 End One Of {29 02}
0x2109 End If {29 02}
0x210B Suppress If {0A 82}
0x210D QuestionId: 0x13 equals value 0x0 {12 06 13 00 00 00}
0x2113 Gray Out If {19 82}
0x2115 True {46 02}
0x2117 Text: Statement.Prompt: , TextTwo: en-US {03 08 2A 00 2A 00 00 00}
0x211F End If {29 02}
0x2121 Gray Out If {19 82}
0x2123 True {46 02}
0x2125 Text: Statement.Prompt: Purchase Date, TextTwo: {03 08 27 00 2A 00 28 00}
0x212D End If {29 02}
0x212F End If {29 02}
0x2131 End Form {29 02}
0x2133 End Form Set {29 02}
Problem is- it’s not the default store, so trying to read the variable as mentioned somewhere here like “setvar adress” didn’t work. But there’s mentioned VarStor 0x6 and in the beginning of the file is a list of stores:
VarStore: VarStoreId: 0x6 [04BD8413-15F9-43F3-9675-4618E03240E3], Size: 0x224, Name: PchProtocolSetupVar…
Searching for the guid or the name in Uefitool NE doesn’t help much, lets try an Efi shell on an USB stick:
There seem to be quite a lot of shells out there- was happy with an older one (EDKII UEFI Shell 2.0, link on this page), It has 2 options- setvar and dmpstore
SETVAR command syntax
Displays or modifies a UEFI variable.
SETVAR variable-name [-guid guid][-bs][-rt][-nv] [=data]
variable-name - Specifies the name of the UEFI variable to modify or display.
-guid - Specifies the GUID of the UEFI variable to modify or display.
If not present, GUID EFI_GLOBAL_VARIABLE is assumed.
-bs - Indicates that the variable is a boot variable. Applies to a new variable;
otherwise, it is ignored.
-rt - Indicates that the variable is a runtime variable. Applies to a new variable;
otherwise, it is ignored.
-nv - Indicates that the variable is non-volatile. If not present,
then the variable is assumed to be volatile. Applies to a new variable;
otherwise, it is ignored.
=data - Specifies there is new data for the variable. If there is nothing after the ‘=’
then the variable is deleted. If ‘=’ is not present, then the
current value of the variable is dumped as hex bytes.
The data can consist of zero or more of the following:
xx[xx] - Hexadecimal bytes
^"ascii-string^" - ASCII-string with no null-terminator
L^"UCS2-string^" - UCS-2 encoded string with no
null-terminator
–device - Device path text format
NOTES:
- This command changes the UEFI variable specified by name and GUID.
- If = is specified, but data is not, the variable is deleted, if it exists.
- If = is not specified, then the current variable contents are displayed.
- If =data is specified, then the variable’s value is changed to the value
specified by data.
- -bs, -rt and -nv are only useful if the variable does not exist.
- If the variable already exists, the attributes cannot be changed, and the flags will be ignored.
DMPSTORE command syntax
Manages all UEFI variables.
DMPSTORE [-b] [-d] [-all | ([variable] [-guid guid])] [-sfo]
DMPSTORE [-all | ([variable] [-guid guid])] [-s file]
DMPSTORE [-all | ([variable] [-guid guid])] [-l file]
-b - Displays one screen at a time.
-guid - Specifies the GUID of the variables to be displayed in
standard text format. If not specified and -all is not
specified, the EFI_GLOBAL_VARIABLE GUID is assumed.
-sfo - Displays information as described in Standard-Format Output.
-all - Dumps all variables, including those
with a different GUID than EFI_GLOBAL_VARIABLE.
-d - Delete variables.
-s - Saves variables to a file.
-l - Loads and sets variables from a file.
variable - Specifies a variable name. This can be a literal name or
a pattern as specified in the MetaiMatch() function of the
EFI_UNICODE_COLLATION2_PROCOOL.
NOTES:
- This command manages the UEFI variables. The variables
displayed or deleted depend on the command line options, as specified in
the following table:
Variable GUID -all Description
— — — All variables with the GUID EFI_GLOBAL_VARIABLE will
be operated on.
— — X All variables (regardless of GUID or name) will be
operated on.
— X — All variables with the specified GUID will be
operated on.
X — — The variable with the GUID EFI_GLOBAL_VARIABLE and
the name Variable will be operated on.
X X — The variable with the specified GUID and name
Variable will be operated on.
- The variable value is printed as a hexadecimal dump.
- Option -d is used to delete variables. Option -s and -l are used to save
and load variables to and from a file. The variable name can be specified
when using these flags so that the operation only takes effect on
that variable.
EXAMPLES:
-
To dump all variables with the GUID EFI_GLOBAL_VARIABLE:
Shell> dmpstore
-
To dump all variables (regardless of GUID or name):
Shell> dmpstore -all
-
To dump the ‘path’ variable with the GUID ‘158DEF5A-F656-419C-B027-
7A3192C079D2’:
Shell> dmpstore path -guid 158DEF5A-F656-419C-B027-7A3192C079D2
-
To save all variables (regardless of GUID or name) to a file ‘VarDump.txt’:
fs0:> dmpstore -all -s VarDump.txt
-
To delete the ‘BootOrder’ variable with the GUID EFI_GLOBAL_VARIABLE:
Shell> dmpstore -d BootOrder
setvar PchProtocolSetupVar -guid 04BD8413-15F9-43F3-9675-4618E03240E3 will deliver the 224 bytes of this store and the byte I’m looking for should be on 0x148 with a value 02 and should be changed to 03.
VarStoreId: 0x6 [04BD8413-15F9-43F3-9675-4618E03240E3], Size: 0x224, Name: PchProtocolSetupVar…
One Of: SATA GEN3 Mode, VarStoreInfo (VarOffset/VarName): 0x148, VarStore: 0x6, …
One Of Option: Disabled, Value (8 bit): 0x2 (default) …
One Of Option: Enabled, Value (8 bit): 0x3 )
Dmpstore does the same, but has the option to save this store to / load from a file. The file has a header, I didn’t try to restore the variable store this way.
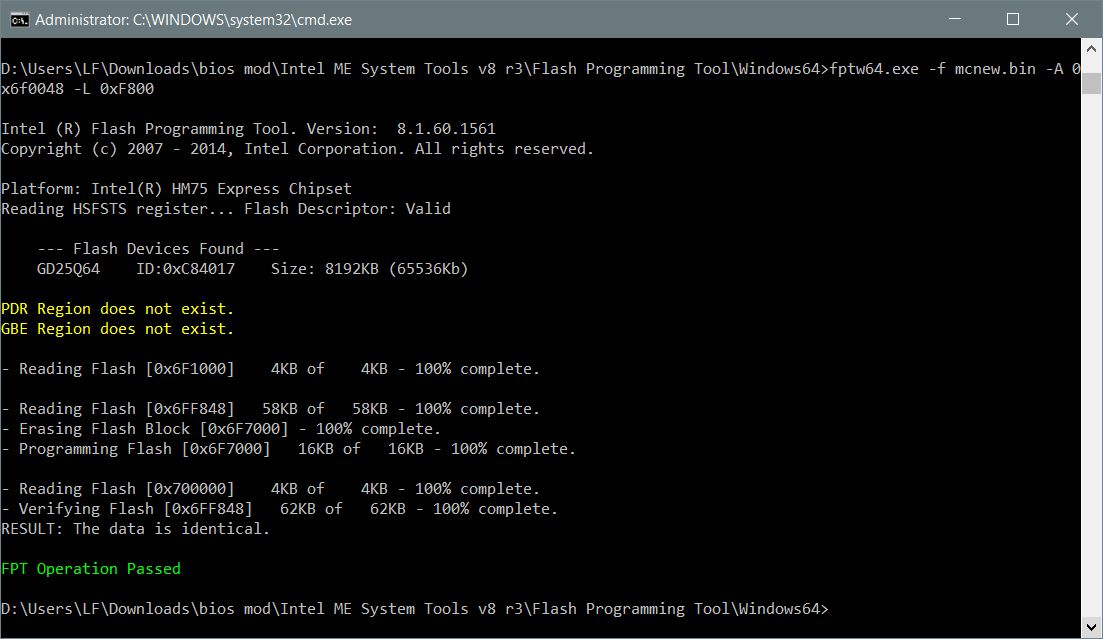
Now there are several ways to just change this setting:
- Change the byte in the store, save this store back via Dmpstore
- Find the stores in the bios, change it there and flash the complete bios. In this bios there are two places. As the store is described in the list of all stores as non-volatile and boot- variable that sounded reasonable.
“Variable NV+BS ‘04BD8413-15F9-43F3-9675-4618E03240E3:PchProtocolSetupVar’ DataSize = 0x224”
- Change just the bits for the variable. That’s what I did, one needs to know the location in the bios, too.
I couldn’t find out why this entry for SATA GEN3 is not visible?! As far as I could see the conditions were not different form other entries that are visible?
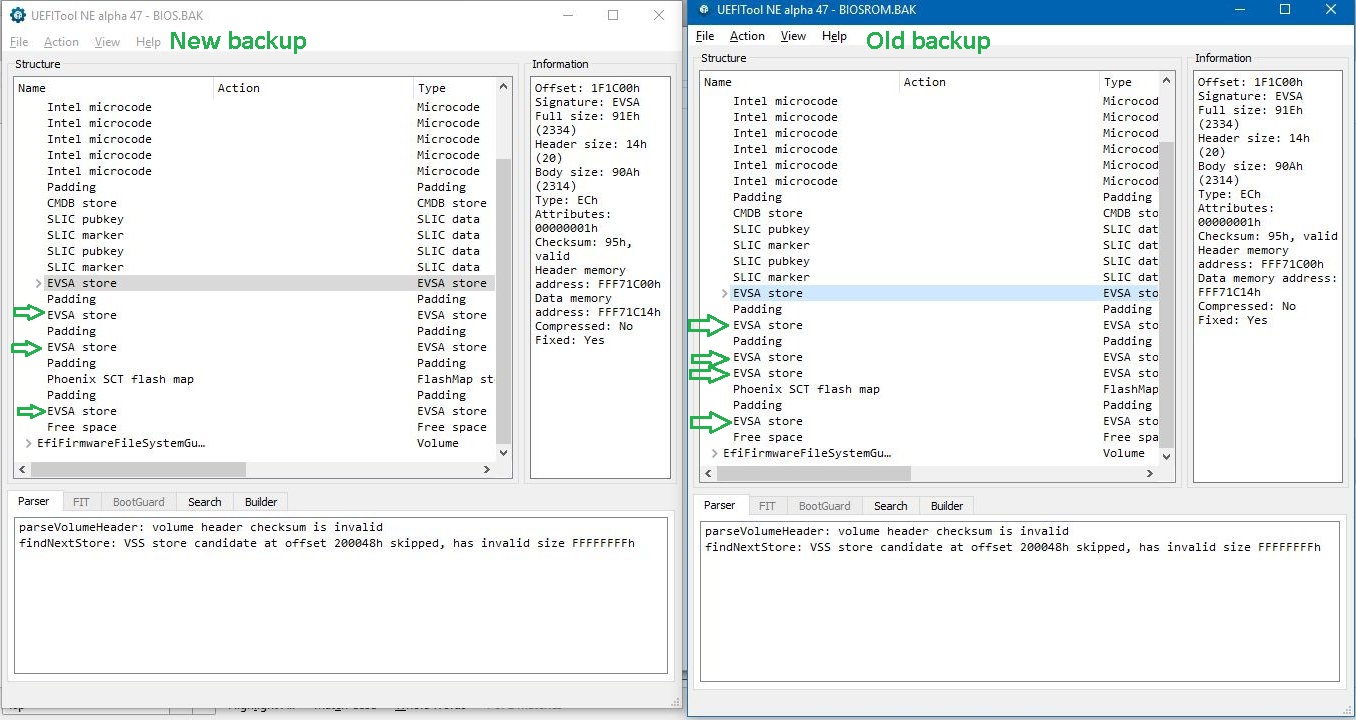
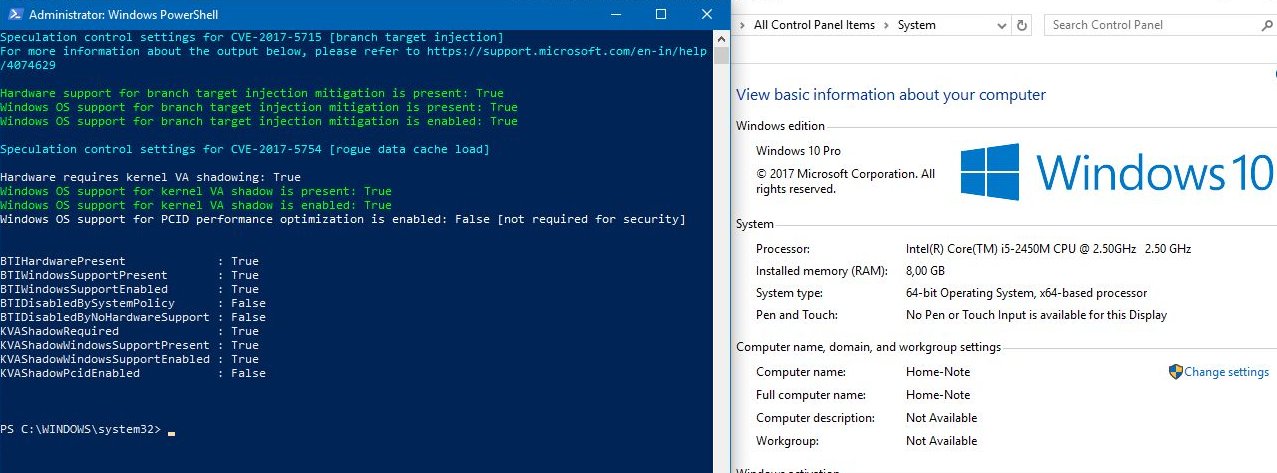
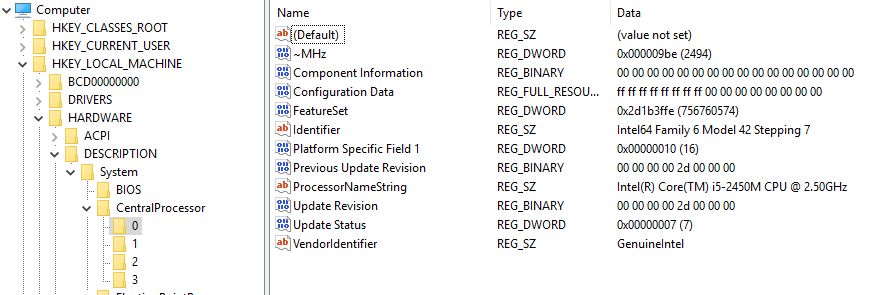
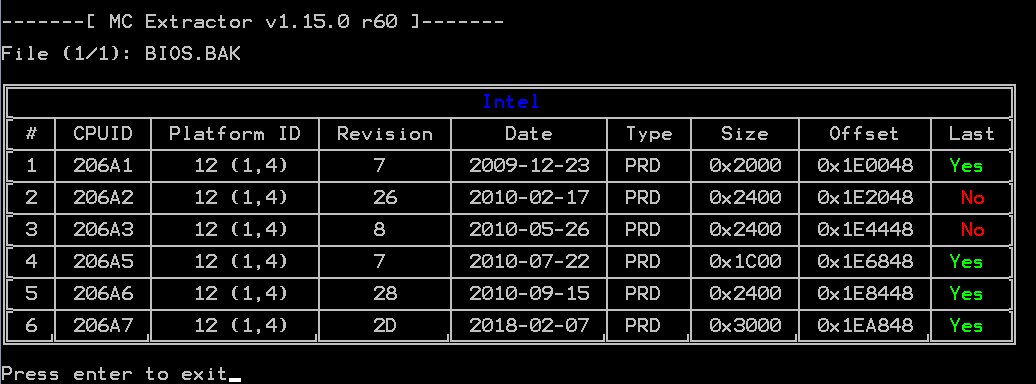
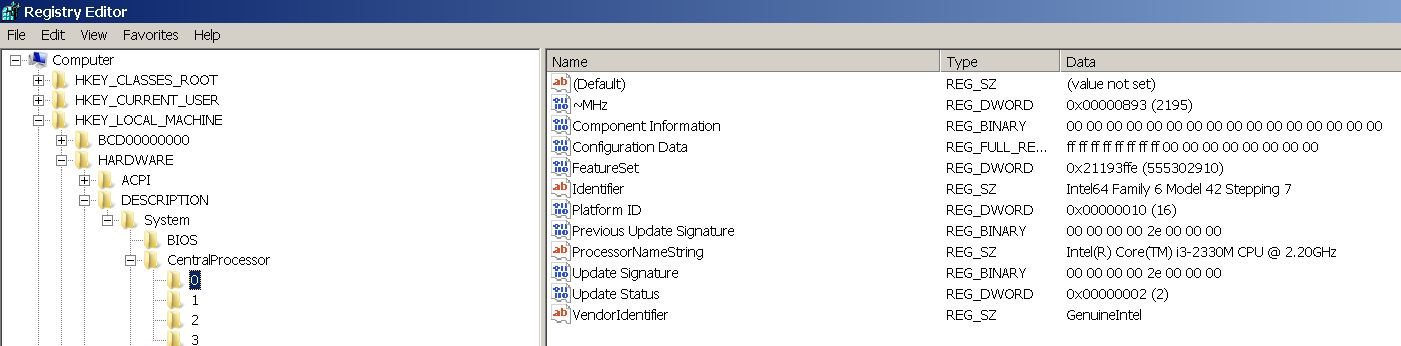
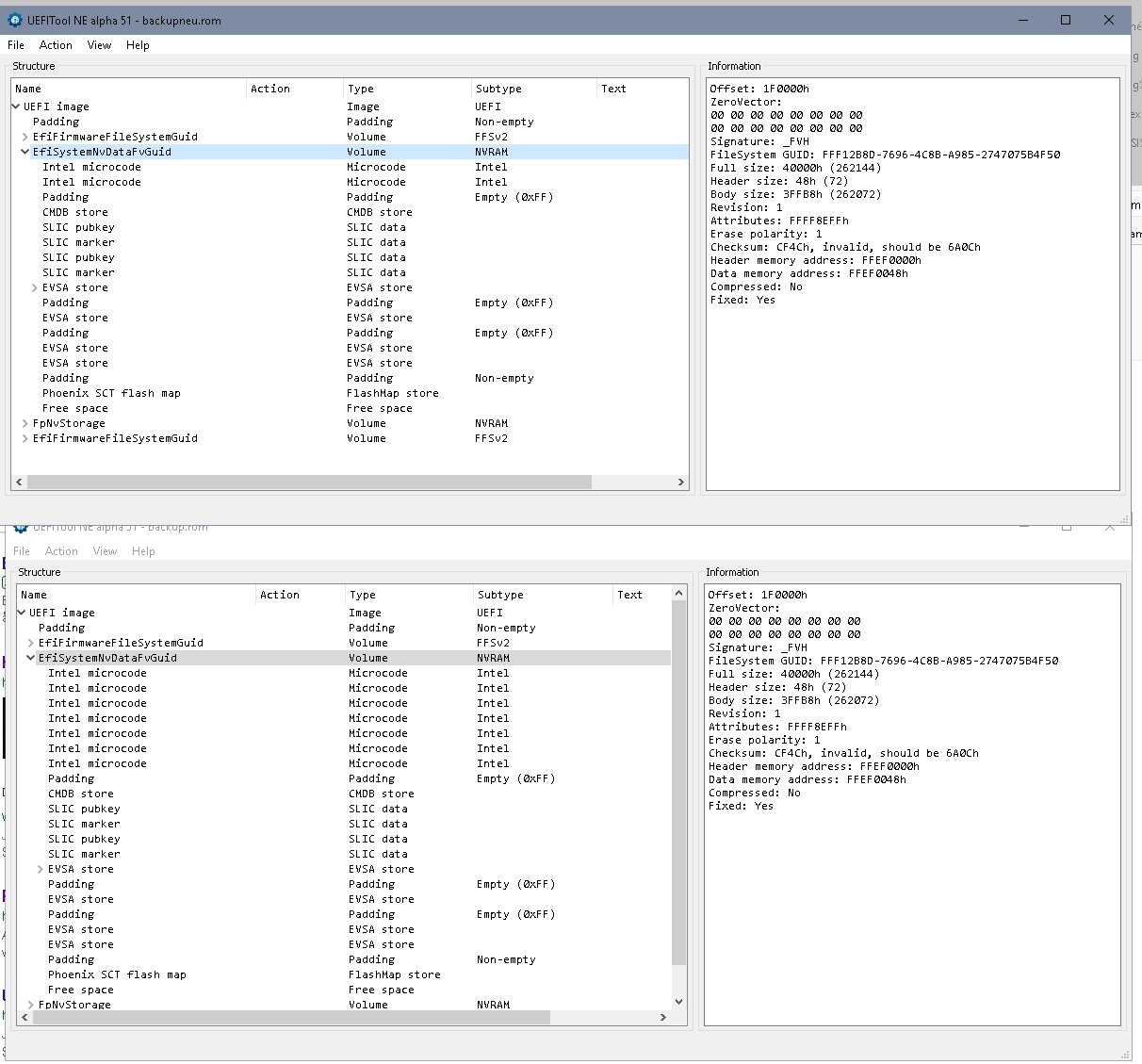

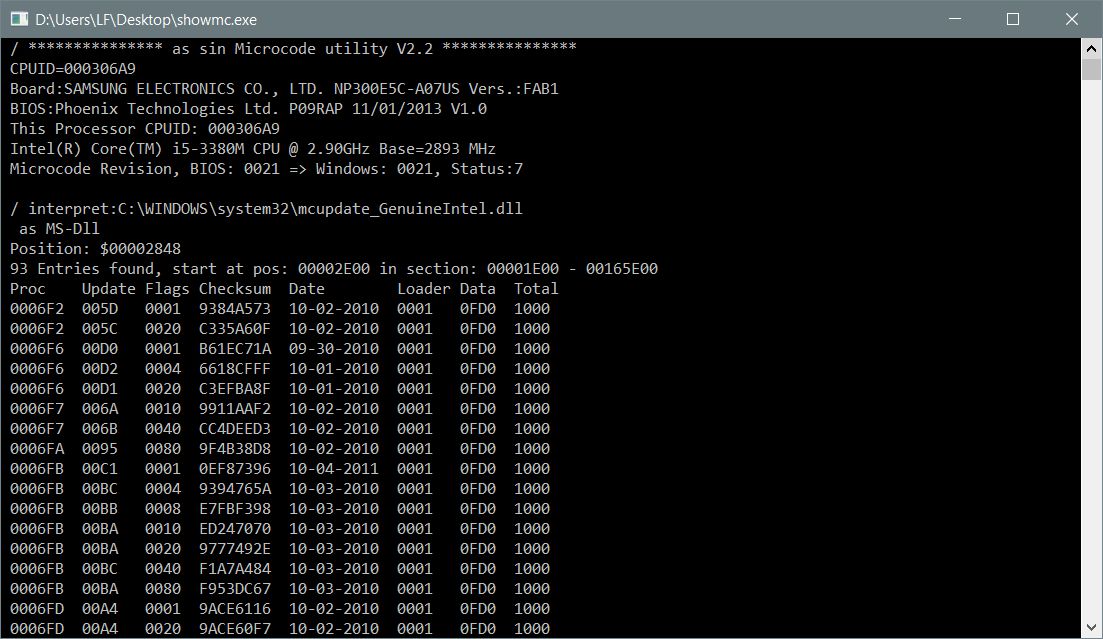
 I first tried to keep/ update all, but there was no room- so I chose to keep just these 2 codes.
I first tried to keep/ update all, but there was no room- so I chose to keep just these 2 codes.