Aa, you have Windows 7, ok
And for Windows 10 is better or not ?
Why not…One could try as it will not harm the system OS anyway, just update the .dll
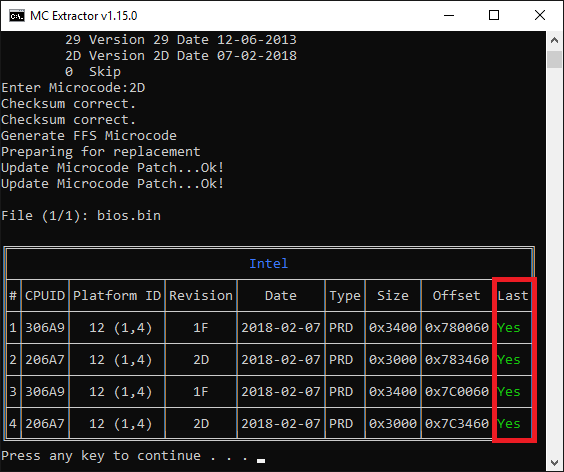
Strangely, on 6-7 series there is no FIT to read the microcodes for a specific offset.
Yup, been trying to change my micro-code(to the first one, want to try and see if I can OC this thing, but same occurs with any other version of micro-code), getting invalid size errors and UBU is removing all the micro-codes and only leaving two, both on the address of Broadwell micro-code.
UBU_v1.69.15.1 and MMTool 5.00.00.7.
See the before, after and using the m option:
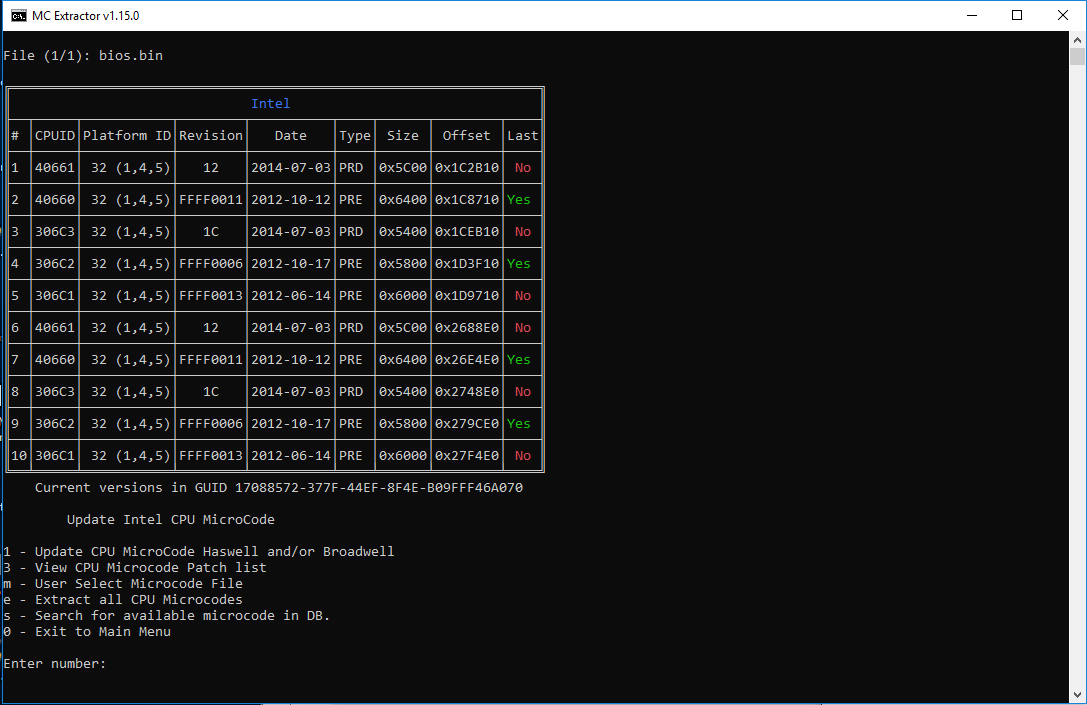
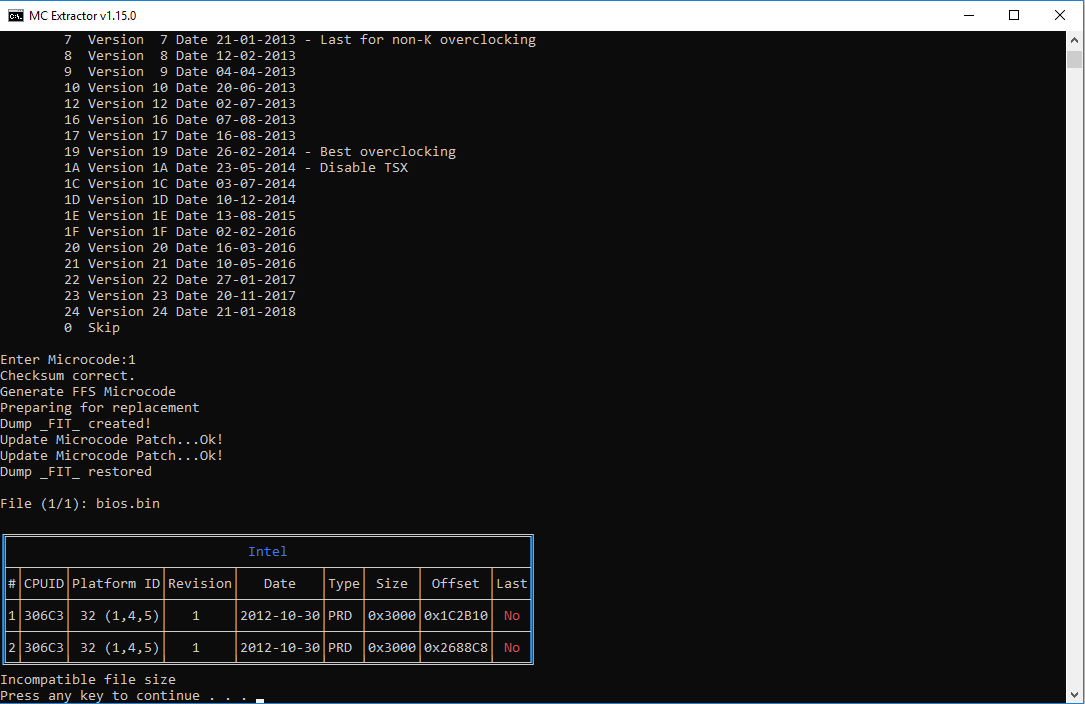
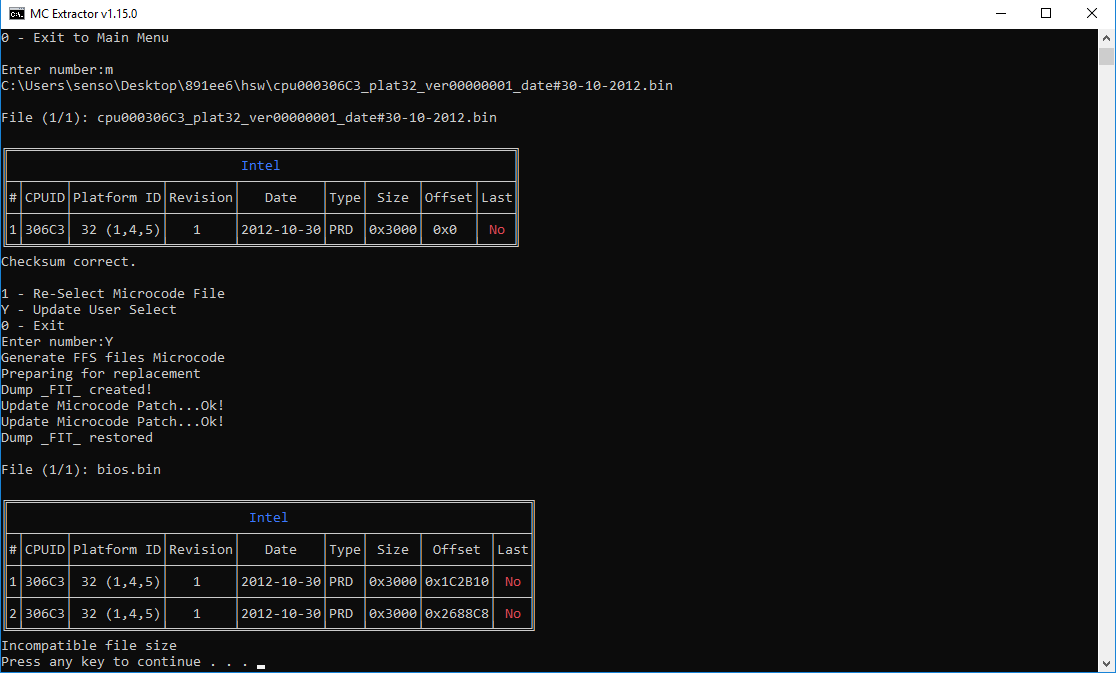
If there is any extra info needed to debug this, I’m glad to provide it.
@RvdH @N6O7 @tistou77
I saw your conversation regarding the Microsoft “kb” updates for Spectre; if you did not already know, keep in mind that those updates are not needed if you have already updated the microcodes of your BIOS. See this article for more discussion.
@SoniX
I did not know that! Interesting. It is strange how the right mcode was called when there were that many before; however, I’m satisfied enough to have found a workable solution (User Select). I believe that should suffice for others with similar platforms as well - yet if you would like to take a closer look, just let me know and I’ll be happy to provide you before/after images of my BIOS. My guess is you have your hands full already. Thanks again for all your help!
@senso
Try using UBU_v1.69.16. If that doesn’t work, try using option “M - User Select” mode and picking the specific mcode .bin file you want (located in UBU subdirectories). This worked for me on my Z68 board as per my post #3743.
@ygbsm Tried that, same results, UBU removes ALL the micro-code entries and complains about wrong size the same way.
@senso
microcodes marked as [PRE] are not replaced, only [PRD]
That leaves 2 microcodes, at 2 locations
But it removes all of them, and doesn’t fix the offsets like it should, I have seen printscreens where after saying wrong size it runs something(mFIT I think) that fixes the offsets.
Given that error I wont try to flash that BIOS or I will end up with a 4KG brick and I dont really want to pull the flash and program it outside.
@SoniX @Fernando
Sorry for the newbie question, but I recently discovered that my computer is not protected by the “Spectre” vulnerability and I don’t know what to do.
My operating system is Windows 7 x64 SP1, the CPU is an Intel Core i7 2600k (Sandy Bridge), the mainboard is an ASUS P8P67 PRO rev 3.1, bios 3602.
The “InSpectre #release 7” software reports the following data:
System is Meltdown protected: YES
System is Specter protected: NO!
Performance: SLOWER
CPUID: 206A7
I was wondering if:
1) a cpu microcode updated for the Sandy Bridge cpus exist;
2) if UBU contains it and what version of the microcode I should use;
3) if the microcode update solves the vulnerability and/or mitigates the impact on PC performance.
Thanks and kind regards.
I can’t give update info but if you DL latest UBB (currently non beta UBU_v1_69_16.7z), look in the 1055 folder (UBU_v1_69_16\Modules\mCode\1155).
Now check Intels pdf for your muc and platform
https://newsroom.intel.com/wp-content/up…te-guidance.pdf
you see they have support for Sandybridge with CPUID=206A7, platform = 12 and new muc=0x2D
So there is new mucode in the 1055 folder of UBU, I just can’t help you with MmTool version an how to do that, as I have not done it.
@thecrowler :
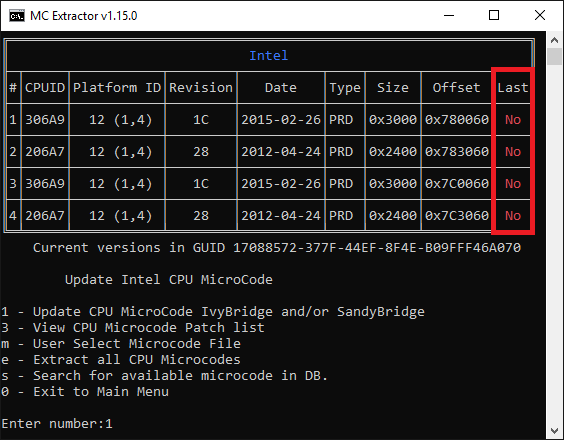
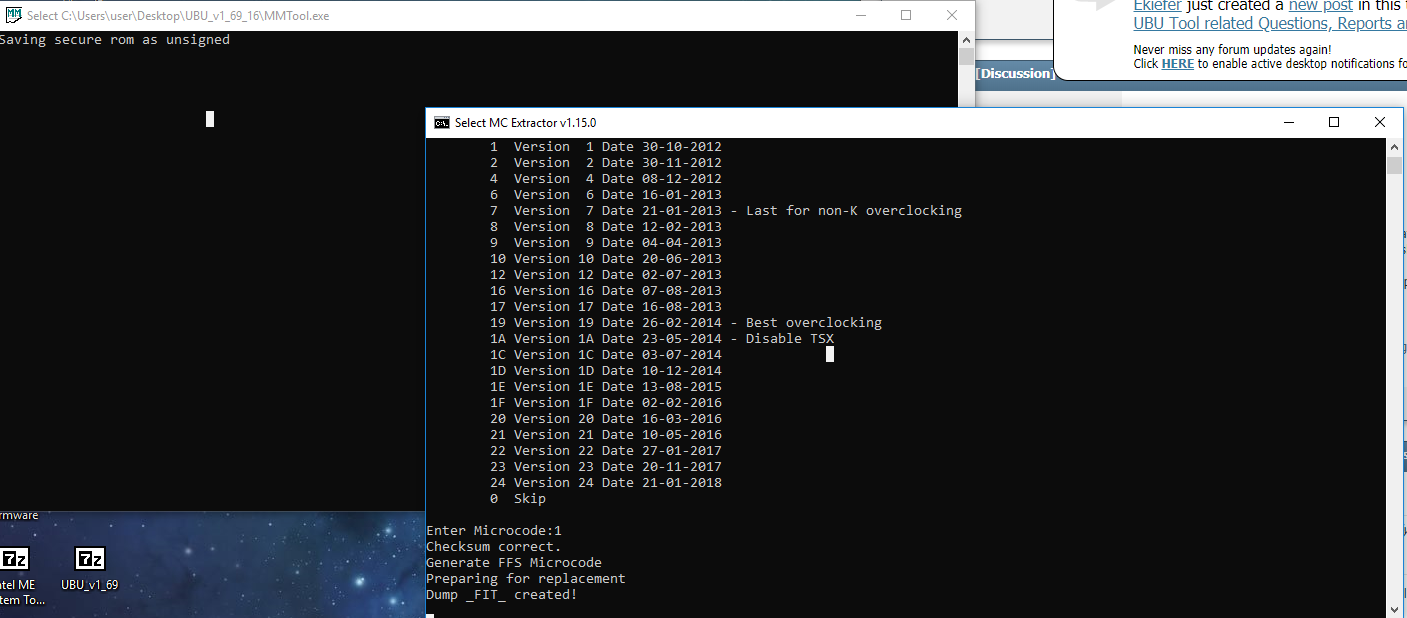
For testing purposes I just have tried to update the SandyBridge and IvyBridge CPU Microcodes by using the latest UBU v1.69.16.
Used BIOS: v3605 for my ASUS P8Z68-V mainboard
Used MMTool: Patched v5.2.0.24 (may not work with all Aptio4 BIOSes)
Result: The Microcode updates were done without any problem.
Here are the pictures:
[[File:CPU Microcode Update IvyBridge+SandyBridge Pic1.png|none|auto]][[File:CPU Microcode Update IvyBridge+SandyBridge Pic2.png|none|auto]]
Although I haven’t yet flashed the BIOS, I hope, that the Spectre vulnerabiliy of my old Z68 mainboard will be shown as being fixed thereafter.
3) if the microcode update solves the vulnerability
Yes along with the Windows updates which require your antivirus to have updated a registry setting.
and/or mitigates the impact on PC performance.
Not on your CPU. My understanding is that the performance mitigations require both PCID and INVPCID. Sandy Bridge has PCID but not INVPCID. Haswell and newer have INVPCID. Click on the ghost in the upper left of InSpectre and select "Show Tech Details" to see PCID/INVPCID support.
Yes, My 3570k shows yes/no for those two, no INVPCID.
I take it performance wise doing bios update to mcu or when MS does microcode update, both will be same, meaning really no performance diff, just more secure doing it at bios level.
@SoniX
Gigabyte Z68XP-UD4 rev. 1.0
AMI ver. U1L (6-3-13) Aptio IV (of course, active image w/ updated orom and mcode)
All the original images are available here plus I have UBU updated images orom only and orom+mcode (Sandy Bridge).
So, I modded 5.2.0.24, it didn’t exploded, downloaded 1.69.16, this is what I get mid patching:
EDIT by Fernando: Unneeded fully quoted post removed (to save space)
I had used a VMWare utility to load a microcode update but none of the Meltdown Spectre checkers would acknowledge it. Perhaps when Microsoft does it they simply assert it somehow. I had heard that Microsoft added microcode updates to Windows Catalog but not to Windows Update.
I cannot imagine how the manner in which the microcode update gets implemented would make an end result performance difference either. I would prefer it be implemented in BIOS and that lead me to this website. 
That was the problem with VMWare method , plus how fast did it get loaded in OS.
Right, MS has a patch for only 1709 (latest) and only newest CPU’s, I think its 6xxx an up but not sure right now).
I think I am going to wait a while, but good to know it seems to work with these tools. I am on a old bios 1205 with my P8Z77V Pro MB, newest bios is 2104.
So it would not be waste either way, I just don’t want to brick MB, though it does have flashback option, so I guess that wouldn’t happen (can flash it w/o running system).
Meanwhile I have flashed the modded BIOS (look >here<) into my ASUS P8Z68-V mainboard.
After having done it, I let the OS (Win10 x64 RS4 Build 17115) install the latest Windows Updates.
Last step: I ran the latest Spectre tools (InSpectre v6640.7 and Ashampoo SpectreMeltdownCheck v1.1.2).
This is what I got:
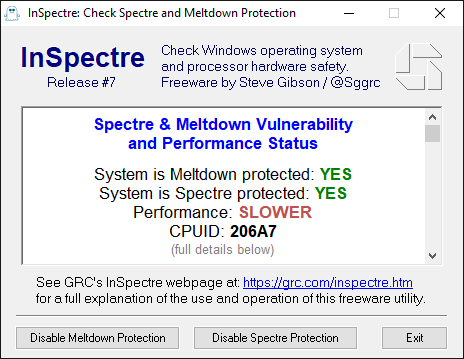
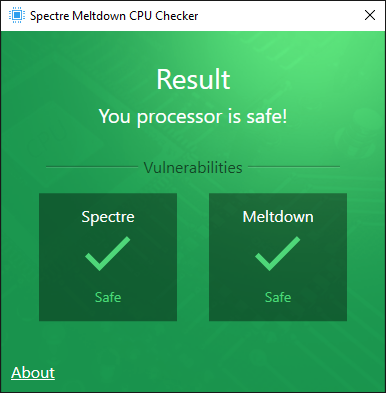
My test verifies, that it is possible to fix the Meltdown and Spectre Vulnerability issue of an Intel SandyBridge CPU by simply updating the related Microcodes with UBU v1.69.16.