@osk866 There’s nothing wrong with this image it seems.
I’d recommend to look into this thread for the different versions:
[Guide] Clean Dumped Intel Engine (CS)ME/(CS)TXE Regions with Data Initialization
There are always some specific recommendations for the different ME versions (but since you don’t want to clean ME firmware you don’t have to follow all steps always). For ME 8 it reads:
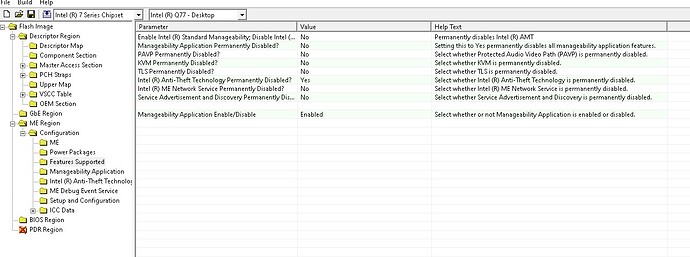
For ME 8 settings are named different, here you ‘disable’, so the answer is almost always "no"
And for disabling Anti-theft do the 2 mentioned changes in PCH strap 2 in addition!
- There may be some trouble with some (newer) SPI chips- some flash programs can’t read different chip-types correctly, read the post of @Lost_N_BIOS ( After reading BIOS chips, Dell Latitude 3510 won’t start ) I don’t know of any consistent and complete information source which program won’t read which chips, unfortunately…
- You might check with "fptw??.exe -fwsts" if the ME filesystem is corrupted before dumping. This will also display correct chipset of the system. Alternatively MEInfo -verbose does also display ME filesystem corruption, but I’m not sure if that’s true for older versions like ME8.
- Use the newer FIT version for this ME 8
- Colours in UEFItool: Regions covered by bootguard (can be disabled in menu ‘view’) No BootGuard- no colours