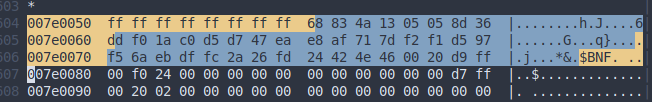
Its very simple. By comparing different versions of the bios, you will be able to locate the checksum. In my case where the address is absolute and no magic bytes precede it, it (the checksum) is followed by $BNF.
To give you an idea of it,
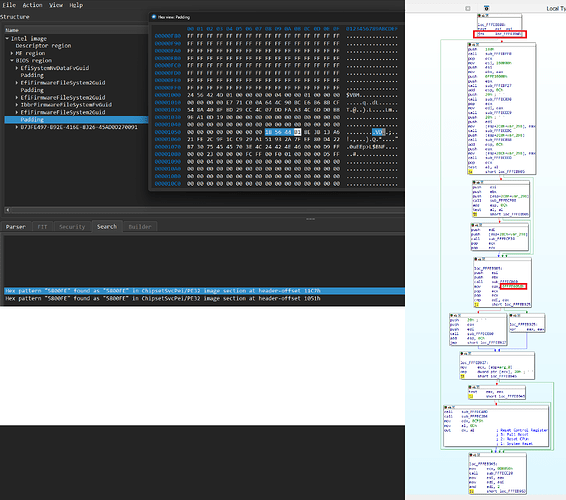
Then you will need to locate the absolute address of the string in UEFITool. To accomplish which you only need to search for part of the checksum (4 leading bytes should suffice here)
![]()
The search result should come up with a header offset
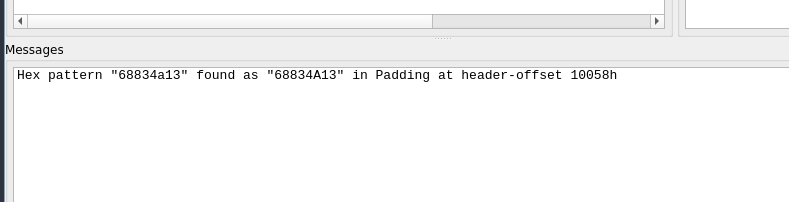
You may proceed with this data, but you might run into an ordeal of finding the correct instruction in IDA, so it’s best to calculate the absolute address (You might need UEFITool NE for this)
Assuming that you are on a little-endian arch, you’ll have to search for it in a reverse order
Now search for the modules with the absolute address you got:
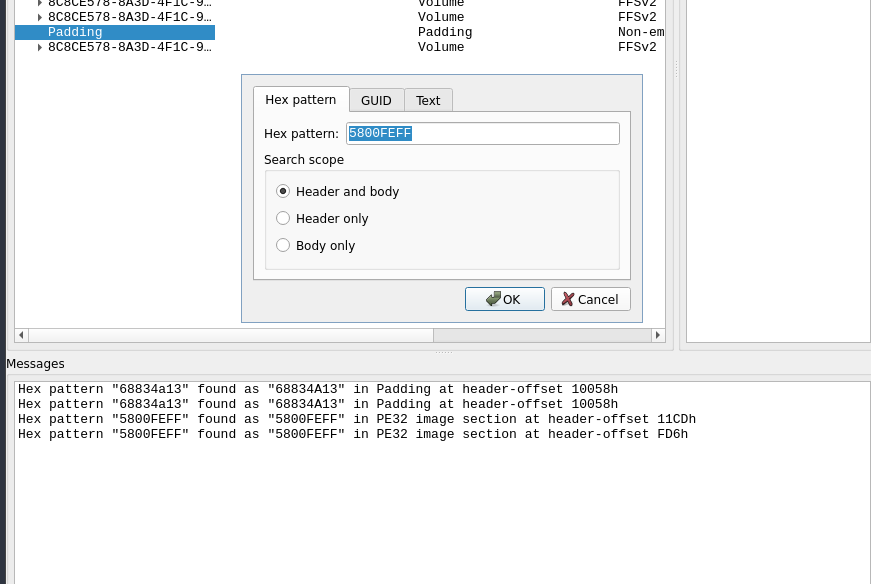
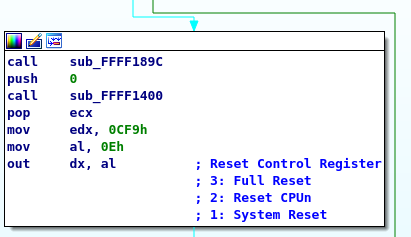
After which, something should appear in the search result panel. At this point, follow the guide uploaded by the author and please be noted that the assembly code might differ a bit, but that’s fine as long as you can identify the same pattern as in the pictures provided by the author. To pinpoint the part of the code to be modified, you may search for the address in hex in ida free and the jz instruction will be in the vicinity. I hope anyone stumbling upon find this message helpful.
Tips:
If you see this block of codes, it means you are near to finding the target: