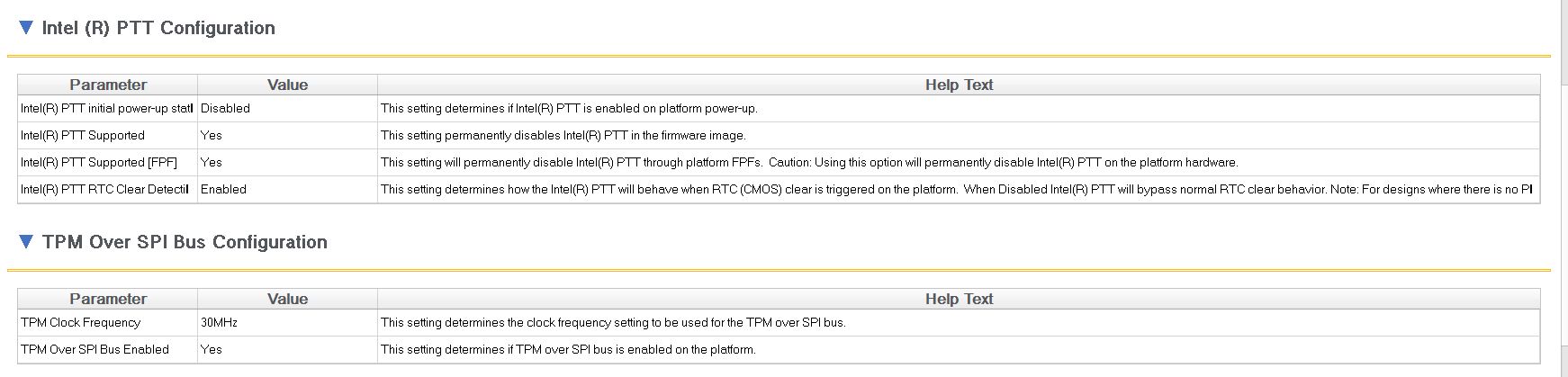
Hello Wizards,
I’ve got what I guess would be a strange request for help to enable ME that Dell has disabled.
I have a Dell XPS 9550 laptop that I would like to get TPM 2.0 working on. The CPU is Intel i7-6700HQ and ark[1] suggests to me the hardware supports this. The BIOS menus have no visible TPM or PTT settings or anything else that I can click to get this functionality. tpm.msc tells me that a TPM module can not be found on this computer. I looked back at the order sheet Dell gave me when I bought/configured the machine and I see:
340-AFPJ : TPM Not Enabled GVH5N INFO,TOKEN,DTP,NO-TPM,WW
Inside the case of the laptop there’s a sticker[2] “ME Disabled.” I assume Dell has somehow done some soft lock out of the ME/PTT/TPM functionality for the machine.
MEInfo shows the following:
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
>MEInfoWin64.exe
Intel(R) MEInfo Version: 11.8.86.3909
Copyright(C) 2005 - 2020, Intel Corporation. All rights reserved.
Intel(R) ME code versions:
BIOS Version 1.14.0
MEBx Version 11.0.0.0010
GbE Version 0.8
Vendor ID 8086
PCH Version 31
FW Version 11.8.86.3909 H
Security Version (SVN) 3
LMS Version Not Available
MEI Driver Version 2120.100.0.1085
Wireless Hardware Version Not Available
Wireless Driver Version Not Available
FW Capabilities 0x31111140
Intel(R) Capability Licensing Service - PRESENT/ENABLED
Protect Audio Video Path - PRESENT/ENABLED
Intel(R) Dynamic Application Loader - PRESENT/ENABLED
Intel(R) Platform Trust Technology - PRESENT/DISABLED
Re-key needed False
Platform is re-key capable True
TLS Disabled
Last ME reset reason Global system reset
Local FWUpdate Enabled
BIOS Config Lock Enabled
GbE Config Lock Enabled
Host Read Access to ME Disabled
Host Write Access to ME Disabled
Host Read Access to EC Disabled
Host Write Access to EC Disabled
SPI Flash ID 1 EF4018
SPI Flash ID 2 Unknown
BIOS boot State Post Boot
OEM ID 68853622-eed3-4e83-8a86-6cde315f6b78
Capability Licensing Service Enabled
OEM Tag 0x00000000
Slot 1 Board Manufacturer 0x00001028
Slot 2 System Assembler 0x00000000
Slot 3 Reserved 0x00000000
M3 Autotest Enabled
C-link Status Enabled
Independent Firmware Recovery Disabled
EPID Group ID 0x1F83
LSPCON Ports None
5K Ports None
OEM Public Key Hash FPF 234EB9DE1AC240CC1376378CA22D245372D665B40F93D148141A66E9B76293EF
OEM Public Key Hash ME 234EB9DE1AC240CC1376378CA22D245372D665B40F93D148141A66E9B76293EF
ACM SVN FPF 0x2
KM SVN FPF 0x0
BSMM SVN FPF 0x0
GuC Encryption Key FPF 0000000000000000000000000000000000000000000000000000000000000000
GuC Encryption Key ME 0000000000000000000000000000000000000000000000000000000000000000
FPF ME
--- --
Force Boot Guard ACM Enabled Enabled
Protect BIOS Environment Enabled Enabled
CPU Debugging Enabled Enabled
BSP Initialization Enabled Enabled
Measured Boot Enabled Enabled
Verified Boot Enabled Enabled
Key Manifest ID 0xF 0xF
Enforcement Policy 0x3 0x3
PTT Enabled Enabled
PTT Lockout Override Counter 0x0
EK Revoke State Not Revoked
PTT RTC Clear Detection FPF 0x0
You might notice that I'm running a ME firmware that's more recent than what's included in Dell's latest they've released for this in their BIOS package 1.14.0[3]. I updated the ME firmware myself hoping it would get things working, but it didn't.
Before I updated the ME firmware to the latest I could find, I dumped the original with
FWUpdLcl64.exe -save fw.bin
I can run that through ME Analyzer to get:
╔═══════════════════════════════════════════╗
║ ME Analyzer v1.253.0 r262 ║
╚═══════════════════════════════════════════╝
╔════════════════════════════════════════════╗
║ fw.bin (1/1) ║
╟─────────────────────────────┬──────────────╢
║ Family │ CSE ME ║
╟─────────────────────────────┼──────────────╢
║ Version │ 11.8.70.3626 ║
╟─────────────────────────────┼──────────────╢
║ Release │ Production ║
╟─────────────────────────────┼──────────────╢
║ Type │ Update ║
╟─────────────────────────────┼──────────────╢
║ SKU │ Corporate H ║
╟─────────────────────────────┼──────────────╢
║ Chipset Stepping │ D, A ║
╟─────────────────────────────┼──────────────╢
║ TCB Security Version Number │ 3 ║
╟─────────────────────────────┼──────────────╢
║ Version Control Number │ 284 ║
╟─────────────────────────────┼──────────────╢
║ Production Ready │ Yes ║
╟─────────────────────────────┼──────────────╢
║ Workstation Support │ No ║
╟─────────────────────────────┼──────────────╢
║ OEM Configuration │ No ║
╟─────────────────────────────┼──────────────╢
║ Date │ 2019-07-22 ║
╟─────────────────────────────┼──────────────╢
║ File System State │ Unconfigured ║
╟─────────────────────────────┼──────────────╢
║ Chipset Support │ SPT/KBP ║
╟─────────────────────────────┼──────────────╢
║ Latest │ No ║
╚═════════════════════════════╧══════════════╝
I can also dump the ME firmware I'm running now with
FWUpdLcl64.exe -save mefw_new.bin
And run that through ME Analyzer to get:
╔═══════════════════════════════════════════╗
║ ME Analyzer v1.253.0 r262 ║
╚═══════════════════════════════════════════╝
╔════════════════════════════════════════════╗
║ mefw_new.bin (1/1) ║
╟─────────────────────────────┬──────────────╢
║ Family │ CSE ME ║
╟─────────────────────────────┼──────────────╢
║ Version │ 11.8.86.3909 ║
╟─────────────────────────────┼──────────────╢
║ Release │ Production ║
╟─────────────────────────────┼──────────────╢
║ Type │ Update ║
╟─────────────────────────────┼──────────────╢
║ SKU │ Corporate H ║
╟─────────────────────────────┼──────────────╢
║ Chipset Stepping │ D, A ║
╟─────────────────────────────┼──────────────╢
║ TCB Security Version Number │ 3 ║
╟─────────────────────────────┼──────────────╢
║ Version Control Number │ 301 ║
╟─────────────────────────────┼──────────────╢
║ Production Ready │ Yes ║
╟─────────────────────────────┼──────────────╢
║ Workstation Support │ No ║
╟─────────────────────────────┼──────────────╢
║ OEM Configuration │ No ║
╟─────────────────────────────┼──────────────╢
║ Date │ 2021-03-14 ║
╟─────────────────────────────┼──────────────╢
║ File System State │ Unconfigured ║
╟─────────────────────────────┼──────────────╢
║ Chipset Support │ SPT/KBP ║
╟─────────────────────────────┼──────────────╢
║ Latest │ Yes ║
╚═════════════════════════════╧══════════════╝
I've also tried poking through the BIOS .bin that I unpacked from Dell's bios update .exe looking for hidden EFI variables to twiddle with this[4], but there seem to be so many relevant ones, I don't know which to try forcing and I'm a bit worried here that I could brick it by changing those.
So any advise anyone can offer for how I can get TPM working on this laptop would be really great!
[1]: ark.intel.com/content/www/us/en/ark/products/88967/intel-core-i7-6700hq-processor-6m-cache-up-to-3-50-ghz.html
[2]: attached
[3]: www dell.com/support/home/en-uk/drivers/driversdetails?driverid=90khw&oscode=wt64a&productcode=xps-15-9550-laptop
[4]: github.com/datasone/grub-mod-setup_var