If you cannot further unlock the BIOS, then you have to patch 0xe2 and so on.
BIOS this time turned out to be overprotected
@vismut1822 - It may be OK to do menu edits, we don’t know until you try second file I sent you first
As for MSR 0xE2 patching, yes, I can make you BIOS with that, but you also would need changed BIOS settings too (ie NVRAM edit, to disable CFG Lock) and ideally when we do that we’d also edit setup and the module that controls actual menu you see, to change CFG lock default too.
But, this setup and menu module change is not required, provided you do not load defaults and only use the BIOS as-is after NVRAM edit, you can change other stuff, just not load optimized or it will reset NVRAM
Not sure what “and so on” is referring to?
The initial BIOS I sent you that bricked, may be due to how I rebuilt the BIOS, that is why I sent you 2nd BIOS to test, to find out the cause. If you never test it, then pointless to make more mod BIOS, until we first know if method/tool I used first time is the issue, or editing that module only is the problem
I just checked and MSR 0xE2 mod gets two hits in this BIOS, one in SiInit which is OK to edit, but the other is in BIOSAC and this is in extreme Boot guard covered area (RED) + in a PEI volume so requires direct hex edit
MSR 0xE2 may be OK with only first one edited + CFG Lock disabled, you’d have to test and see outcome.
I checked, and CFG lock is ONLY in setup (enabled by default), which is not the module I edited for you previously in first test BIOS, so it may be OK to edit this without bricking, only more testing to find out is required.
You’ll have to get used to brick/recover, if you want to mod and test all this stuff,l otherwise you’ll only be thinking about trying it and never getting anything accomplished or attempted to sort out etc.
* Edit - And, ideally, I’d like to send you a third file to test if #2 fails, with just a default settings change, instead of reveal item attempt, to also confirm or not if the manner I unsuppressed the item is the issue or not.
So. I just flashed the second bios mod (vismut1822-USBtestM2).
I caught the same brick. It also won’t start
@vismut1822 - Thanks for testing, please also test this one, so we know for sure that editing that specific module is not possible
Wait! Before that, I think maybe I see what’s possibly going on, we may be violating Boot Guard by flashing in the entire BIOS region at once, this touches two volumes boot guard covers!
Sorry I did not realize this sooner!
Please make the following FPT dump and send me the file, I will then make you two files to flash back and test.
One will be same edit I sent you before, other will be one I was discussing in last post, just changing a setting default, not unsuppressing anything.
FPTw.exe -a 0x9A0000 -l 0x500000 -d MainDXEVol.bin
This way, hopefully will not brick, and should be OK
Here is the link to the dump. https://ufile.io/mnfedw3m
I also want to ask a question. After your modification, what should I sew through? Through the programmer? If so, which of the two chips?
@vismut1822 - For now, we’re only dealing with the 8MB Winbond chip, but unless recovering you don’t need to use flash programmer. And for now, flash-in with FPT only
If both these brick too, we maybe should do follow up test where I compile all BIOS to one, edit, then split, then you program back both. But, since this is a clean split I don’t think that is required on this model.
Flash back like this, and please test in this order. The first = new, simple setting change only to same file, second = same change as initial - unsuppress attempt.
If first fails, then second will as well for sure, so maybe can skip if you want and we’ll have to consider the full BIOS edit, split, then program back, to confirm 100% this module can’t be edited, or just wrong method at first >>
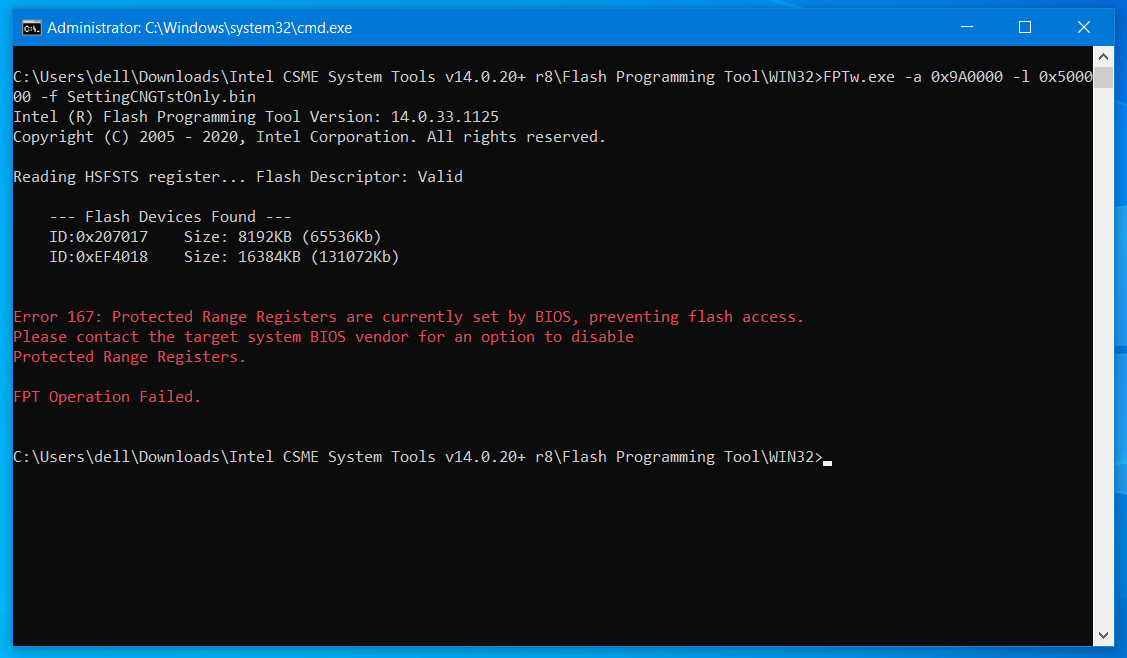
FPTw.exe -a 0x9A0000 -l 0x500000 -f SettingCNGTstOnly.bin >> This, just change Default Option of “Warnings and Errors” >> From >> Continue on Warnings and Errors >> To >> Prompt on Warnings and Errors
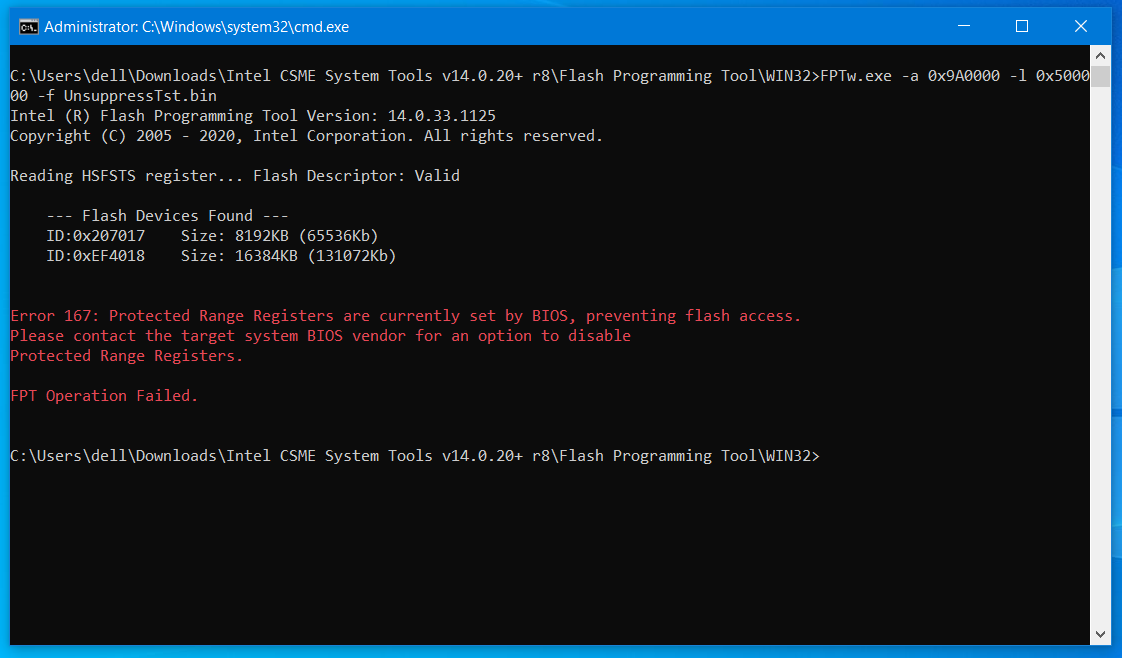
FPTw.exe -a 0x9A0000 -l 0x500000 -f UnsuppressTst.bin
http://s000.tinyupload.com/index.php?fil…306184363740205
If first file above boots OK, but second does not, then this means I need to look at and change how I’m trying to unsupress the items (they/ALL items are HEAVILY suppress/gray out if before each, many times), often at a reference link, then at the actual setting too, for every single item
Hey, FYI, I see this in the EC FW, so you may be able to somehow recover using this hotkey combo and some file (maybe RVC, if you can find it on their site) >> Flash Recovery Ctrl + Esc pressed
So, maybe helpful to you if you figure out how to use, so maybe you can recover without programmer. Usually, this kind of file and documented method, is outlined at Dell’s site for models that have this, so you should be able to find something about it somewhere for this model since I see it in the BIOS.
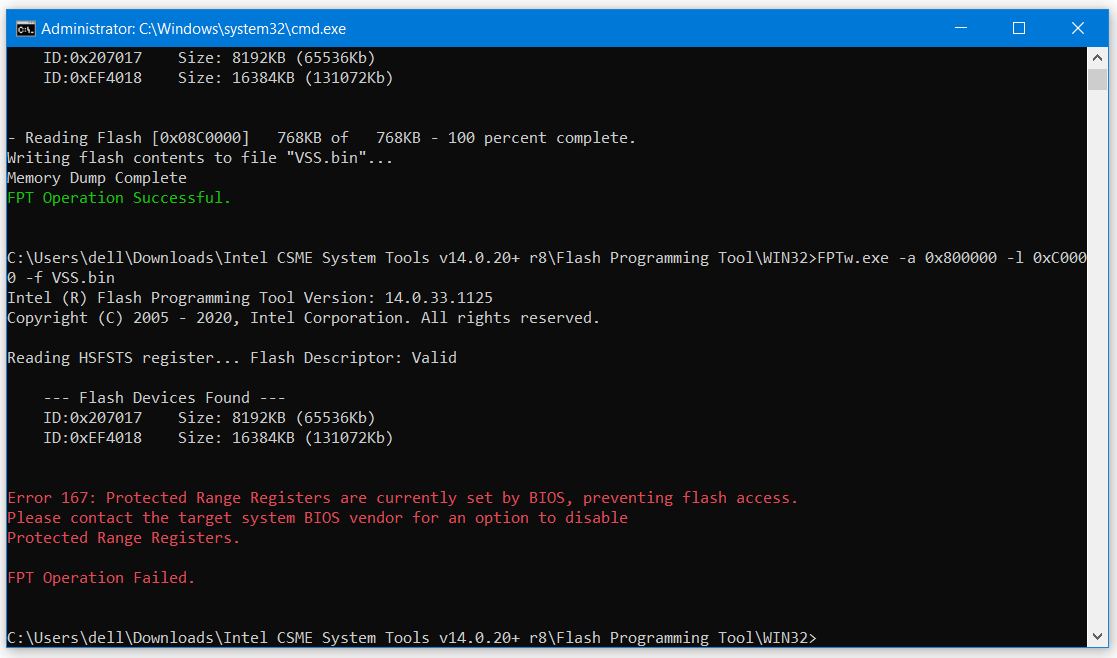
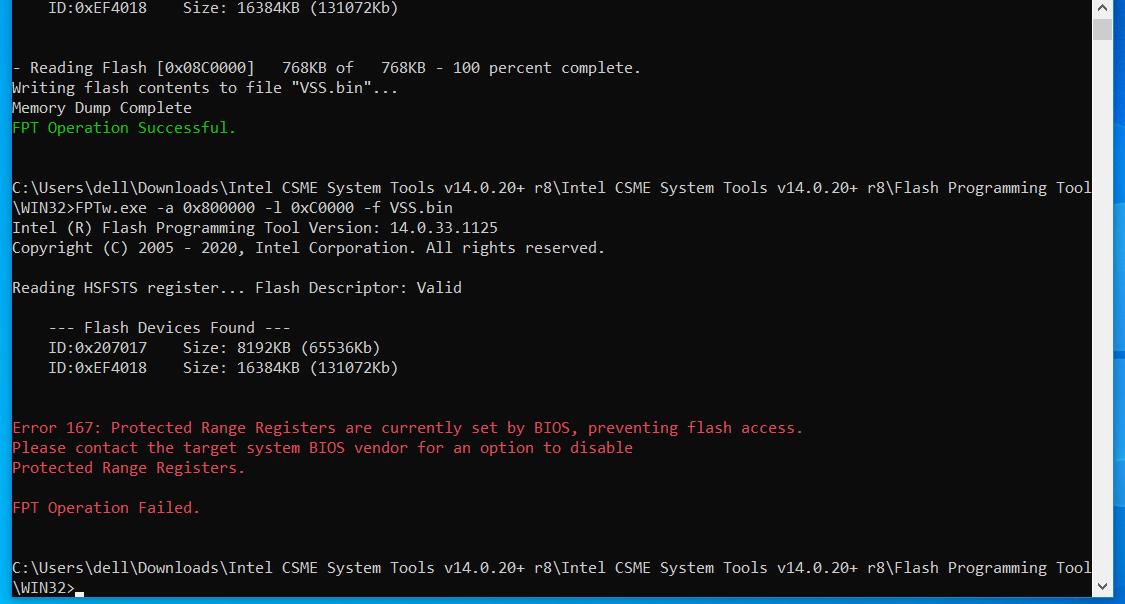
When trying to flash it, it displays error 167
@vismut1822 - How did you flash BIOS region before when I sent to you? Was you using programmer only/always? Is there a 2-3 pin FD/FDO/ME/Service/Management jumper?
If yes, put on jumper, reboot to windows three times, and on third boot do the FPT stuff again.
If no jumper, please dump below, and test writing it back, then send me the created file >>
FPTw.exe -a 0x800000 -l 0xC0000 -d VSS.bin << To dump
FPTw.exe -a 0x800000 -l 0xC0000 -f VSS.bin << To test write back
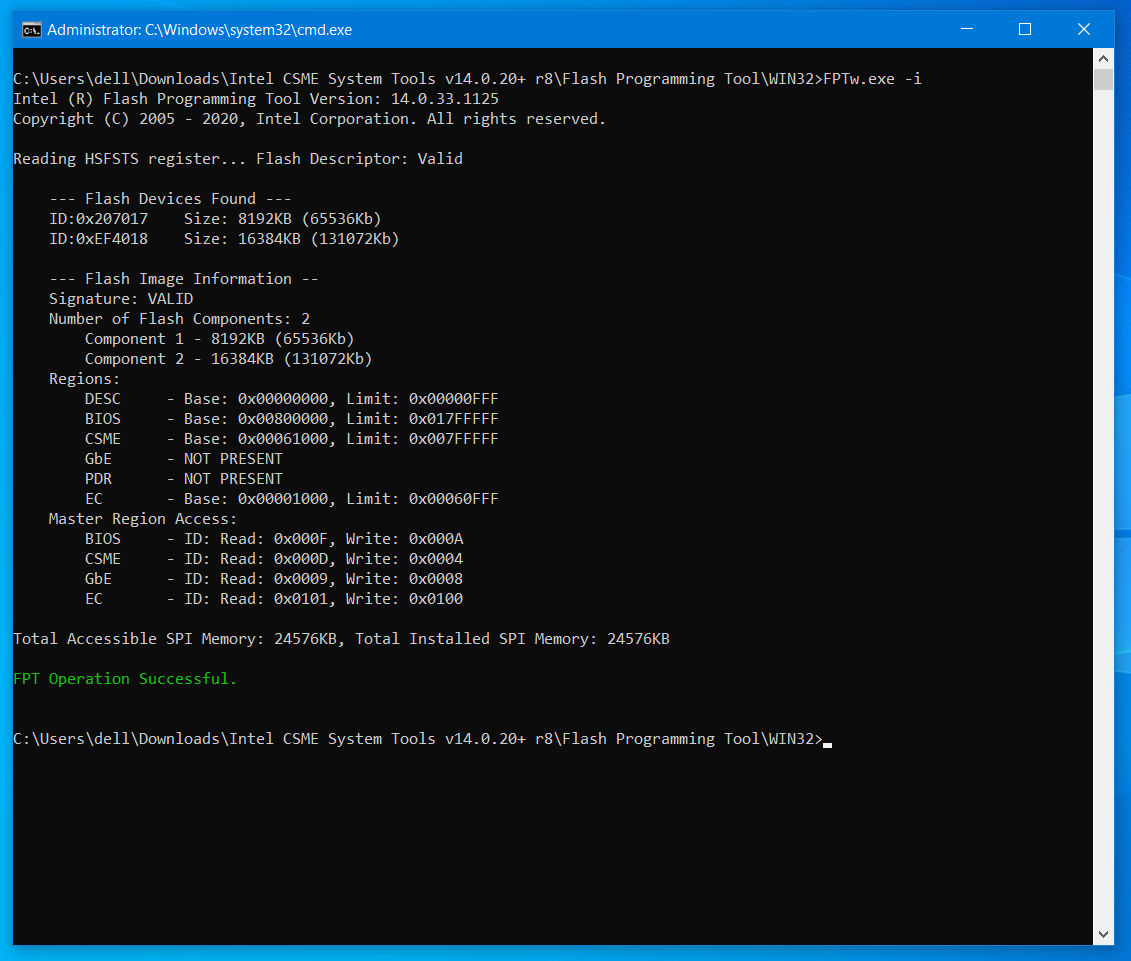
Also, show me image of >> FPTw.exe -i
If we have to use only programmer, then I will make you some new BIOS to program in for testing, once success with something and we figure out the cause of failure here with the edits, then I will try to find and bypass this 167 issue, if I can find it
Also, be sure secure boot is disabled until we are done, and there is no BIOS password set.
So.
You asked about the jumpers on the board.
I carefully studied it, removed all the RAMs, but did not find the jumpers.
About passwords and Secure Boot. I have these functions disabled
I just did as you asked for a dump, tried to flash it. I got error 167 again

Hey.
I apologize for distracting.
What thoughts with modification?
@vismut1822 - You didn’t answer my first questions above?? The two before jumper was mentioned. And on jumper, it may not be by the memory, I only mentioned that as a place to not forget to look.
If you want to try to continue past error 167 without using programmer, do the following
Using RU method >> Go to section 2.2 and make bootable USB with RU program, then read 2.3-2.5
http://forum.notebookreview.com/threads/…-issues.812372/
Only you will make changes in “PCHSetup” GUID 4570B7F1-ADE8-4943-8DC3-406472842384 NOT in “Setup” as the guide outlines
Go to the two following offsets in PCHSetup, if either is 01, change to 00 then save and reboot back to windows and try FPT again
0x17
0x6DA
If you just want to use programmer instead, let me know and I will make you BIOS to program in
So.
As for RU, I could not start it. Instead of starting, the usual DELL logo hangs
Secure boot is disabled.
I don’t understand why it won’t start.
Also you asked me what you can do the modification through the programmer.
I don’t want everyone to take apart the back cover of a laptop.
I am ready to sew with the programmer only if there is 100% confidence that it will be possible to flash it the first time.
In this case, if there is no such confidence, then we will use FPT.
But how to use it if I can’t start RU.
You also asked that I did not answer the previous two questions.
I personally did not find jumpers. Maybe it is, only on the back of the motherboard. But I refuse to disassemble the motherboard. And there is no certainty that it will be on the back side.
I want to unlock all the defenses of this BIOS as much as possible. But how can we do this, if even the simplest program such as RU cannot be started…
----------------------------
I don’t understand, for modifying the BIOS we are not given Measured Boot and Verified boot?
And why do we get a brick through the programmer? Maybe this is the culprit of Boot Guard?
And can FPT help us (if we can bypass error 167 at all?) In modification, since the programmer cannot cope with its task?
I took a close look at my motherboard and found out more about the jumper.
In general, in most cases on motherboards, it lies next to the RAM.
Looking for information on my laptop, I found high resolution pictures of my motherboard
After looking at the photos, I finally realized that there are no jumpers.




@vismut1822 - To run RU, you need to disable Secure boot, and boot in legacy mode. Can you boot to DOS? If not, how are you making the DOS USB Stick? If Rufus, try this method instead, do only step #1-2
No, jumper would be on the front of the board only, so no need to check back 
No, in general it’s by bottom of board, near USB headers, only sometimes by memory, but again sorry, I did not know this was laptop so you will not find in laptop
However, this is the question I meant that you didn’t answer >> How did you flash BIOS region before when I sent to you? Was you using programmer only/always?
If you can’t get RU to boot, and we can’t use FPT (Already confirmed at post #27 + 29), then you will have to use programmer.
Sorry, I don’t understand what you’re asking about Boot Guard? FPT error is not related to boot guard, but rather FPRR (Flash Protected Range Register) or BIOS Lock.
I only see BIOS lock enabled at BIOS settings (setup, NVRAM), FPRR is not, so maybe if we disable BIOS lock 167 goes away, if not then it’s in a BIOS module and I may not be able to find to edit/bypass. Plus, it may be in area we can’t edit
We can maybe disable the cause of FPT error 167 IF the only way FPRR or BIOS Lock is set is in the BIOS settings, if it’s in a BIOS module as well then we may or may not be able to.
If it’s only in module, and I can find, then yes, maybe, IF it’s not in boot guard covered area
Here is two BIOS below, try this BIOS (winbondMVSSBIOSLock) first, program only 16MB chip and see if boots OK (if yes, test FPT #1-2 from post #28, delete any previous created file first!)
If fails to boot, then there is some check I’m not seeing, and maybe nothing we can do here
Also, then please test this BIOS (winbondSettingCNGTstOnly), this is one of the BIOS/changes from #26 but programmable since you could not test those via FPT
This is test to start checking again to see if we can edit BIOS menu or not. This does not have the bypass 167 changes made above, so both BIOS need to be tested, so we can know if BIOS above lets you FPT past 167 or not, then if so we’ll add that to this edit too if this one also works
https://ufile.io/i6hbb2js
So. I asked for the first modification (winbondMVSSBIOSLock)
The laptop started up from him.
I tried to make my dump and flash it (as from post # 28). But there were strange circumstances. Somehow magically the VSS.bin dump began to weigh 768KB !!! How can I understand?
I was still trying to flash it, but we got back to error 167 again.
Sadly I went to flash the second modification (winbondSettingCNGTstOnly)
But the cunning laptop refused to start over. Brick again
In general, error 167 cannot be defeated
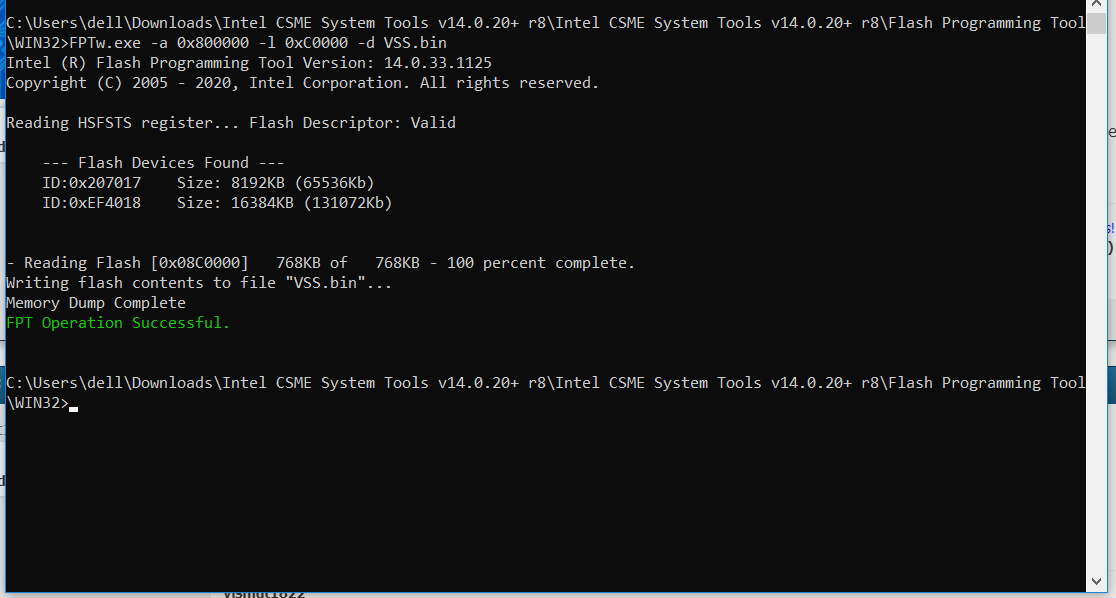
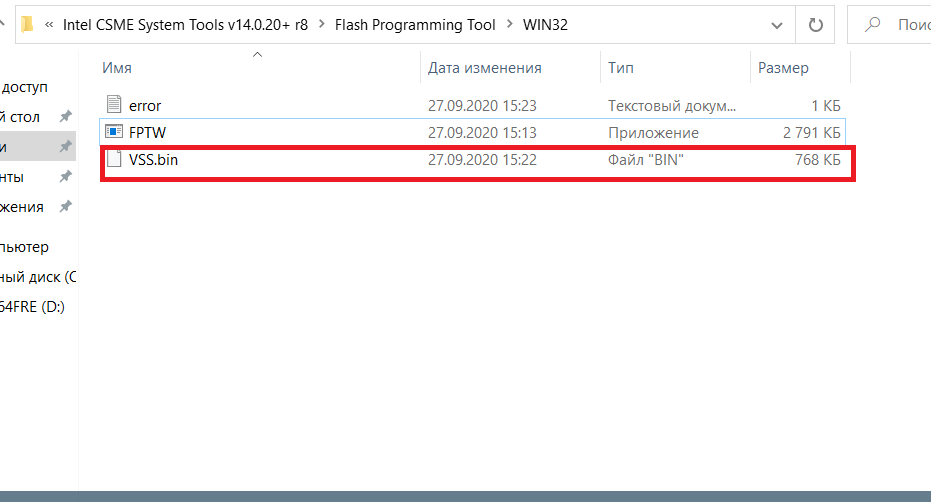
@vismut1822 - vss dump is supposed to be 768KB, this is expected. Program back in winbondMVSSBIOSLock, then try put system to sleep (S3, not hibernate) for one minute, then wake it up and try FPT 1-2 from #28 again (delete any previous created file first)
Since winbondSettingCNGTstOnly bricked, the only way we can change settings here is via NVRAM/Vss change, to current applied setting value only) << These changes can be made by FPT dump/reflash, maybe, if we can get past 167, if not then only via programmer dump/edit/reprogram
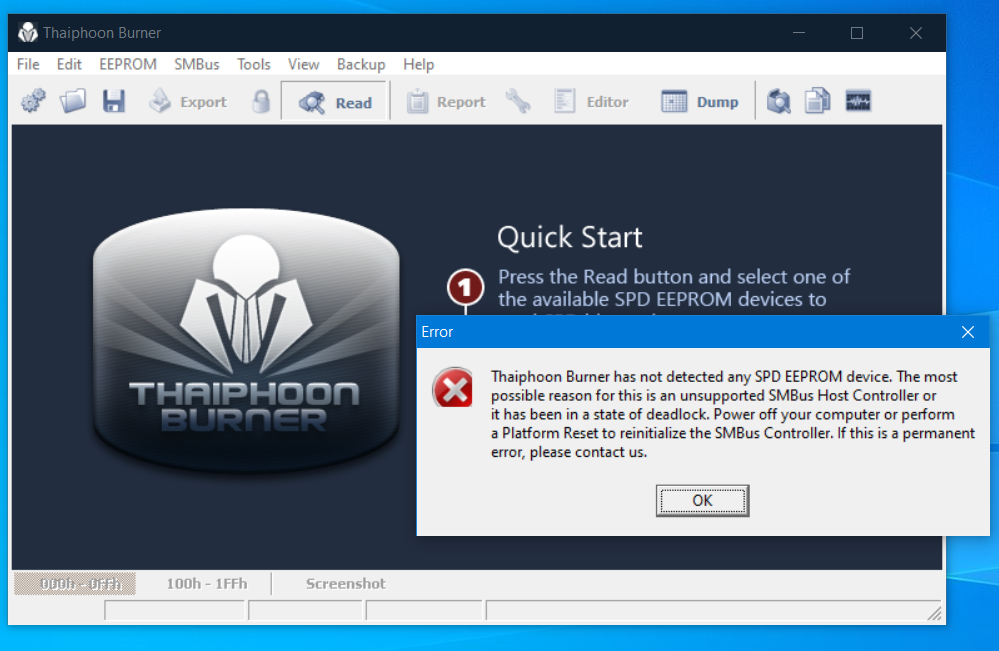
@Lost_N_BIOS Tell me, I want to start Thaiphoon Burner, but when I try to press SPD Read, it gives an error.
Can I get around it?