@ttkx , I recently acquired a 3650 M4 and am in the same situation as you. Have you had any luck in the last two months on this project?
I’m looking to add NVMe support to my IBM x3650 M4 7915.
I just extracted the system BIOS via a CH341a, and have attached a link for my extracted BIOS (unmodded v3.10 from IBM) . If anyone wants to do this themselves, the BIOS chip is a Spanlion S25FL128P1F labeled U28_SKT, with “SYS BIOS 16M” printed near by on the motherboard, and my SOP16 test clip pulled ROMs with the same MD5 three times in a row right away.
I’m looking into adding the NVMe module from the x3650 M5 now, and would very much appreciate any advice sent my way. I’ve added NVMe modules into BIOSs before, but with how proprietary and convoluted this IBM has been to work on, I feel like asking for a second opinion is a good idea before I proceed.
Extracted BIOS:
http://s000.tinyupload.com/?file_id=02950752623222884042
MD5: E9D4AB580C051FD73ABBE99F238E0C12
x3650 M5 NVMe Module:
http://s000.tinyupload.com/?file_id=32167449529353661011
MD5: 7F3FD828D7973072CB51A3644CE72DF4
@monkeyyninja - Merged over here, since same system/request
If you want to put in NVME module from other stock BIOS, such as M5 you mention, there would be three modules not a single (I did not look at your “M5” files)
Do you want me to stick in the M5, or do the usual NVME mod? If you want me do to the M5 swap in, you’ll need to link me to that BIOS so I can grab all the NVME modules (please put in max compressed zip if you upload)
* Edit - This is a dual image BIOS, but in either image, there is not sufficient space to insert regular or small NVME Mod. I could possibly remove something and then make it work, but I’ll have to dig around and see what could possibly be removed.
* Edit 2 - Maybe MATROX MGA-G200 vBIOS can be removed if you do not use onboard graphics, or Intel Boot Agent if you don’t use Boot on LAN or Wake On Lan?
Nothing else looks like ideal candidate in these volumes, even Logo’s are not in the same volume (my first target to resize/remove etc)
Wow, I hadn’t expected anyone to get back with me so quickly, much less in such detail!
I do not plan on needing LAN boot, so if we can substitute the NVMe module for that I would be completely happy.
Thanks again!
@monkeyyninja - You’re welcome! We can try that and see. Have you erased chip and wrote back your dump yet, to confirm your read/write with programmer is OK?
Maybe best to do that first, to rule out that in advance in case edit fails and we are not sure if due to mod or due to programmer
If you attempt to do this, I would also make another dump with ASProgrammer first, to compare with your initial dumps to make sure same/same.
Actually, to do that, you’d need to make new dumps at same time with original CH341A software and then ASProgrammer 1.141 too, without powering up between either dump, that way chip contents are same
What software version did you use to make the initial dump? If looks OK, but I don’t have anything to compare to, and that also doesn’;t mean write using same version will be OK to.
Best we at least get a dump/compare going with ASProgrammer too, in case write fails with CH341A software then you can try ASProgrammer too.
For now, you do that, and I will work on mod BIOS 
 Wont take me long though
Wont take me long though 
I started out with ASProgrammer, so I’ll re-verify with the stock programmer and do a write-back of the stock image after. Haven’t tried writing anything yet, in fact I intentionally left the write protect pin on my test clip tied to ground in case I got something wrong.
@monkeyyninja - What software/version did you dump the file you sent with? I’d say try a compare of two new dumps using 1.34 and ASProgrammer 1.41, just to be sure both match, then if so at least one of them should be OK to write back safely
If you don’t have it already, 1.34 is included in this package - http://s000.tinyupload.com/index.php?fil…213094641136166
Mod BIOS is done, no spacial issues once removed Intel Boot Agent module 

Sure thing! I started out doing three dumps with ASProgrammer 1.4.1, which all had the same MD5. As soon as the system finishes what I have it doing now I’ll pull the BIOS a couple times with the stock tool and compare the hashes. May be a while, though.
Did you have to do anything other than remove the Intel Boot Agent module and insert the compressed universal NVMe module? The multi-part BIOS had me a bit worried that modding it would be a mess.
@monkeyyninja - You can only compare dumps taken at same time, without system being powered on again between dumps. So whatever you compare will need to be taken again right now.
No, it was no other changes, simple edit, here is my change log I wrote out as I did the edit a few ways.
1. Removed Intel Boot Agent GE (v1.3.72 + 1.5.82) x2 Volumes @ 8E13BCDB-619F-4FC3-91D9-7C402781DC27
2. Insert NVME Full Size x2 Volumes @ 94EB3254-E9F6-43EA-A8A3-BAB6E780A258
Info - UEFITool 25 or PhoenixTool 2.73 both used for test build-outs, checksums fixed with either and both create same resulting file >> Use UEFITool 25.0
Do you want me to upload the mod BIOS, or do you want to do it yourself, and or wait to decide until you compare more software/version dumps and then erase/write test?
In regards to the multi-image BIOS, it may be only one section needs edited/applies to your system, but I was not sure which and assumed you may not be either, so I edited both.
If you wanted to try and figure out which applies to your system, it may be possible via CPU microcodes IF your CPU is one of the CPUID’s that differ between the two areas (206D6, 206D7, 306E4) If not then we’d have to update one of the others in separate mod just to see which gets used.
If your CPU model is one that uses one of the CPUID’s mentioned above, check via HWINFO64 what microcode is being used now/live and we can tell which BIOS image applies to your system (upper or lower)
Here’s how to check current microcode with HWINFO64
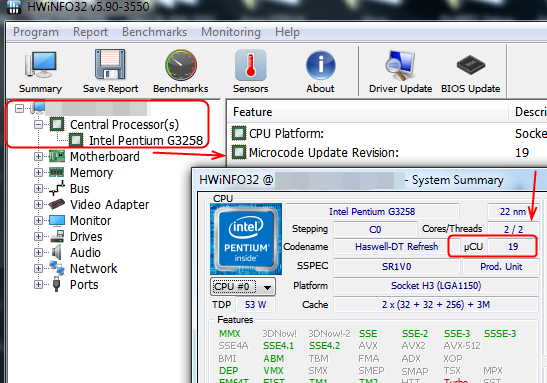
Quick update,
I performed a couple more extractions with ASProgrammer and the stock programmer. Each md5 with ASP was identical, while each was different with the stock. I reflashed one of the pulls from ASP and the system booted w/o issue. I’m going to start working on the NVMe mod and attempt to flash it, as well.
@monkeyyninja - What do you mean “The stock” Programmer? What software and version, if you are not sure please look in “Help” and it should show version there.
Sounds like there is an issue with “Stock” software, and “Stock” whatever that is would fail write too, since you wrote back ASP dump with ASP (I assume) and it worked OK. Good to hear this 

Keep with that then, or when you redo any dump/compares again, compare 1.34 as I mentioned with ASProgrammer and see if they dump same too or not.
But main thing now, you know ASP dumps and writes good, so only dump and write with it, until you confirm 1.30 or 1.34 also can read/write properly too (If you waste time to confirm 
Unfortunately I’ve had no luck with the custom BIOS. I’ve tried inserting the NVMe module in multiple different places, including at the end of the two main DXE volumes, and the system refuses to take the new image. I get an error about CRTM signatures and the system fails-over to the backup ROM.
Any ideas?
@monkeyyninja - Upload your mod BIOS (in zip), so I can see what you’ve done, compare with mine etc. Did you use UEFITool 25.0?
There is only one place to put it, at the end of the main DXE volumes, which I gave GUID for on previous page.
It very well may be signed and we can’t edit 
You do have secure boot disabled, AND any encryption or TPM disabled in BIOS before you dumped and during the flash attempts correct? If not, do that now, then make new dump, then edit and try again.
* Edit - Hey, what is your CPU, in case we only need to be editing one area of the BIOS
* Edit 2 - If we can’t mod, you can still use NVME on this system, you just can’t boot from it, but you can use it as secondary/storage/data drive.
Or, you can use DUET or Clover USB bootloader methods, and then you CAN boot from
After further testing, I can consistently erase and flash the stock v3.10 BIOS without issue. However, the moment I attempt to boot an edited BIOS, even if all I did was remove a tiny module or change a single attribute, the system fails to boot and reports a signature issue after it finishes it’s automated BIOS recovery. I assume somewhere there’s a checksum or security key that needs to be changed in conjunction with the BIOS. Anyone have any experience working with something like this?
Edit: Just saw your reply, this machine is running two Xeon E5-2690v2. Also, it does look like I had the TPM enabled. I’ll flash the stock BIOS, re-extract and mod, and try flashing again. I had deleted the IDE module, as that is a feature I’m even less likely to use than PXE, and added in the uncompressed NVMe driver to the end of the DXE volume. I’ll upload what I’ve been doing after I re-extract with the TPM off.
Edit 2: I just read up on how the TPM checks if the BIOS firmware changed on each boot. I feel dumb for not thinking of that earlier.
@monkeyyninja - Yes, that may be true, but in mods I did checksums are corrected, however signatures may not be, if it’s signature checked. We can test single settings change in two places (one in setup, one in NVRAM), so see if both are covered by signature or not. We can also test microcode update x1, to see if that is covered or not
Then if all fail, we know entire BIOS is signature checked. But yes, you need to disable secure boot, TPM, remove any BIOS password too, then make new dump and try again and see if same - before we do any of these other “check to see” type of tests, because if any of those things set/enabled, then mod BIOS will fail always.
Thanks, so your CPU is 306E4, we can edit top microcode then you check and see if changed, if not then we edit bottom microcode and you check. This way we can find out which BIOS section actually applies to your system, and then only edit that.
But, we can only do this test if you can flash in mod BIOS. Once you disable TPM, secure boot, remove password etc, send me new BIOS dump and I will make these two test BIOS for you to try so we can see if this is signature covered or not, and if not then we’ll be able to tell which BIOS area applies to your system.
Derp!!! We can tell now, check with HWINFO64 like I showed on page one, what microcode do you see? If Rev 417, then top section of BIOS applies to you, if 42E then bottom section applies to you.
We can still however test edit these later, to see if signature is covering all BIOS or not, but duh, we can check this way which area of the BIOS is for your system
Yes, please send me dump copy once you disable all that stuff and reboot back to BIOS, then shut down for dump. Maybe/hopefully that was the issue, not signature checked BIOS!
Sure thing, I’ll upload the TPM-disabled BIOS in a bit. Here’s a picture of my shit-show as entertainment while we wait on this rom to read
I’m going to owe you a beer after this
Edit: Here’s the No-TPM rom. Also, do you have to update the checksums manually or is that handled by UEFItool, and how do you check for whole-bios signatures? My CPUs microcodes are 42E
http://s000.tinyupload.com/?file_id=43892561294995070025
MD5: D7FA098AF6C50F5121F5FB22295BCF8D
Hey, looks good, I always like to see a random pile of hardware and system mid-surgery
Make sure you also did all the other things I mentioned before you dump (or do it now, then dump again) >> Disable Secure boot, remove any BIOS password you have set, Disable any Encryption or TPM
Also, once done, check HWINFO as mentioned for what microcode is being used, so we know which section we only need to edit.
Also of note, it looks like the TPM enable/disable on this system is handled by hardware and the BIOS just sets a flag. You can’t even toggle it unless the jumper on the mainboard is set correctly, and the BIOS complains about it every boot while it is. Additionally, there is 0 mention of Secure Boot anywhere in this system BIOS. I have Legacy + UEFI boot enabled and anything even vaguely related to security has been disabled/reset.
Is there a removable TPM add-in card, they often look like small WiFI cards and connect into a pinned header. If you find one, remove it and then make the dump. If CSM is enabled, or legacy+UEFI then secure boot must disabled, so no worries there.
See my edit above about CPU, in case you missed it.
Nothing removable as far as the TPM is concerned, just the jumper which allows you to disable it in the BIOS (and disabled it currently is). My CPU microcode is 42E.
