This system is in Manufacturing Mode level.
I think if we commit it to normal mode we will find that Boot Guard is Enable.
Thx
I’m not really knowledgeable on BootGuard, I only know the basics. Certainly the system is not FPF committed so BootGuard is not active. You would need to re-sign BG with the OEM Private Key in order to modify protected ranges. So if you mod the BIOS at protected ranges then the BG signature will be invalid and the BIOS, ACM (or whatever verifies this) will report a problem, possibly because that system is supposed to come with BG enabled. I assume that the error shown is some sort of check to notify the OEM BIOS team of BG miss-configuration because if the system was FPF committed, the platform would not even post, depending on the BG level of course.
Thanks plutomaniac! Maybe @CodeRush can advise deeper on the subject?
Do you think, since it is not committed at the PCH level, can I remove/disable in the BIOS before commit, or does not that matter at all now since OEM has put the hashes into BIOS level already?
Can these be zero’d, and then ACM/BG entry locations be removed from the FIT table? Would that possibly let us around the issue? Good thing here is he has flash programmer, so we can really test anything we want to try.
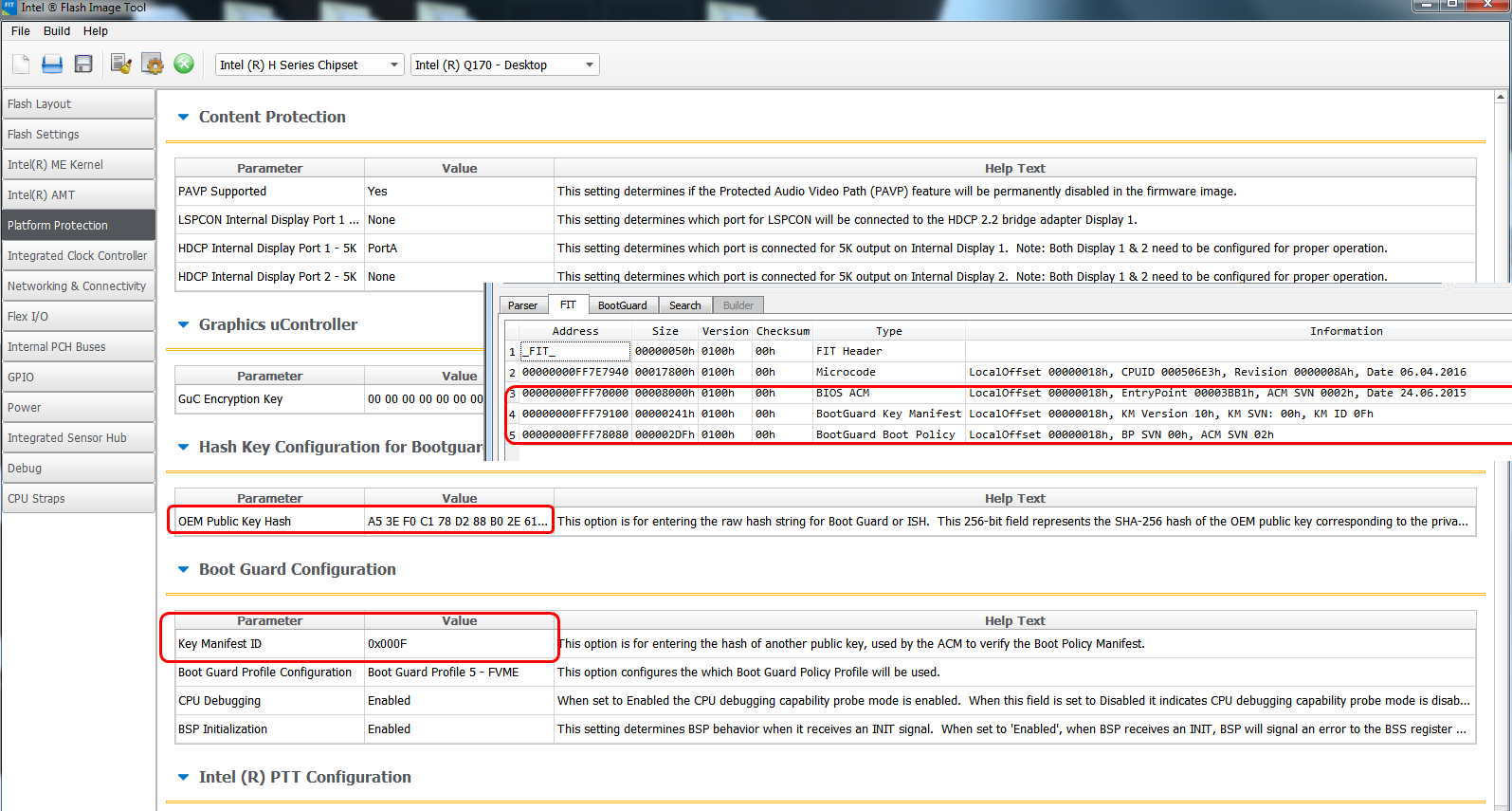
If we can’t do the above, sounds like we cannot edit this BIOS then @simoutekd
Bootguard would need to be burned into the PCH at commit, I am not sure if that is something you/they manually set, and then once commit it takes place, or if we can avoid that at commit.
I guess, for this particular Dell model/sample, editing how you wanted it out, we’ll have to move onto the other two models you mentioned instead.
If something is not committed then yes, it can be removed/disabled. BG protection relies on the permanent state/nature of FPF.
The settings in CSME firmware are relevant only when it is time to commit. When the OEM/user issues a FPF commit by ending manufacturing mode (fpt -closemnf), whatever is set at the CSME firmware is fused into the PCH. The BIOS/FIT side of things should match what’s in the FPF. So yes, if you remove the CSME settings and disable BG there (profile 0 no FVME) as well as remove the equivalent stuff from BIOS/FIT, it should leave BG disabled. Remember though that that you can always commit. For example, if you get it at such state and then issue a -closemnf then BG would be permanently disabled and cannot be re-enabled. The problem here is the BIOS/FIT side of things but I lack the proper knowledge to tell you have exactly needs to be removed.
Sure as long as you don’t commit to FPF by accident or similar in the meantime. A programmer won’t help to reverse any changes in such case.
Great, thank you for the detailed reply and info plutomaniac! So, as a test, I can remove whatever I want before he puts to commit state, within the ME settings first and then FIT table next, then we can test and see if fixes the error.
Which it should if editing and removing is that simple! And based on what you said, and since it’s still in manufacturing mode, I think we can do this! We’ll do a few rounds of testing, and then once we think we’ve got it sorted out I’ll ask you to check it all out before he closes manufacturing mode.
@simoutekd - please make sure to leave this in manufacturing mode until we’re 100% done and confirmed all our edits are working, and the removal of the ACM/BG stuff is all working OK. I will make you new BIOS tonight to get us started on this!
Yes Okay don’t worry I will fellow all your instructions.
Also, before you order more of these Dell Systems, or the other Dell models you mentioned, see if you can ask the seller to send you only systems that are still in manufacturing mode.
That way we can always do this, otherwise if committed already and ACM/Bootguard is active then we wont be able to put the final mod BIOS on those systems.
All Dell desktops are in manufacturing mode.
Also All HP Eliteone 800G2 are in Manufacturing mode. Same like Dell
I think this is good for us because we can change what we want before we commit system and this is what I was telling you from the beginning.
This is a big chance for us that we got all those systems in uncommited mode and I think we just need to find a way how to disable security check before we commit them.
I think this link is good for you and can help.
https://embedi.com/blog/bypassing-intel-boot-guard/
Thank you
Salim
That’s great for these Dell, but I think the HP we have a much bigger issue to solve with the Surestart stuff. I’m sure I can disable all the Dell Bootguard/ACM, we don’t have to worry about that on the HP (at least that we’ve noticed).
Sorry I did not get new test BIOS made for Dell again yesterday, I will try to get that made for you tonight shortly
Thanks for link, I will read. I also planned to read all the Intel ME NDA PDF on how that is setup or not too, but I think without even reading I know and mentioned above how to easily remove and disable this.
However, after reading that link, if edits like that are required, which it seems those have been reported and fixed, making changes like that are above my skillset.
Hopefully changes like those are only needed if you’re trying to work around an actively enabled machine already in committed state, which I assume that is what type of systems they were testing on.
So hopefully my intended method will work, at least for our situation.
@simoutekd - sorry for delay, here is initial 14x BIOS to test  [smoking] https://www.sendspace.com/file/p9n7pk
[smoking] https://www.sendspace.com/file/p9n7pk
Please test all 25 version first, in orders presented, hope you don’t mind all this testing.
I’d appreciate if you could test those first, even though we think they might fail due to UEFITool 25 version giving different error than the 24, I’d like to know if this is actual “new” error or only due to newly detected stuff in 25.1 that 22.4 isn’t noticing.
Then please test all 24 in orders presented. I’m hoping some of these work well before you get to 4-4 final BIOS, because at that point a new issue is presented, hopefully you don’t even have to get into the V4 folders and V1-V3 from one of the 22/25 folders solves it all!
Hello
I think that file we are using for dell is already for commited system.
Why: because Service Tag is already registered on bios which mean system is committed. I don’t know why.
I will send you picture for system when we power-On for first time and what we need to do.
Also I will send you MeInfo file before and after system committed. Like that you can see difference.
Also I will send you Bios file for system before it is commited and you will find that Service Tag number is not there. We can use the new file to make our MOD and tests.
Here is the Link for New Bios Backup of Dell system not committed yet and also MeInfo files before and after system is committed.
If you want me to update Bios to latest version from Dell then send you the final bios backup let me know it. Like that we can avoid that other update it after making changes.
https://fs03u.sendspace.com/upload?SPEED…TINATION_DIR=24
Sorry I don’t know why this happen.
Thank you
Salim
I’m pretty sure Service tag is part of the BIOS, I didn’t look into removing because it hadn’t been mentioned. This is something you can set manually in BIOS, when it’s not locked in, or change with tools/BIOS edit.
I can probably remove manually I think, and there is tools for that too, that you would run on your end. I think maybe it can be done from either side, you or me
You sent me BIOS for system you said was not committed, and ME info you sent too. Please explain what happened, did you commit or what?
You only had the one system correct, I thought, and then you sent me meinfo and dump BIOS.
What is this BIOS, some other system now? Yes, please explain more, and please update to latest BIOS etc, but do not commit anything, then send that dump.
So all 14x BIOS was waste of time? How is that? Did you have two 7040T systems when you backed up one and it was wrong system?
Do you need this tool, would it help the other system issue?
I think EE-Erase would erase the service tag currently there, and I can find other version I’m sure if this only applies to laptops, which I think this “read me” is from portable package as it mentions.
Also, Dell Client Configuration Utility might help too, but this one below probably best (desktop version though)
**********************************************************
Dell Internal Use Only
NOT FOR EXTERNAL DISTRIBUTION
**********************************************************
What does this utility do?
----------------------------------------------------------------------
This utility is used to re-program the system service tag on certain
Dell Portable systems. The utility may only work on systems which
already have a service tag programmed. If no service tag currently
exists, the utility may return an error message and fail.
To program the service tag on a system that does not already have one:
- For Value-line systems:
Run EE-Value.exe /S=XXXXXXX, where XXXXXXX is alphanumeric and all
letters are capitalized.
- For SmartStep/Smart PC 200N/250N:
Run STAG_W1.EXE /W XXXXXXX, where XXXXXXX is alphanumeric and all
letters are capitalized.
- For Molokai:
Run SERTAG.exe /W XXXXXX, where XXXXXX is alphanumeric and all
letters are capitalized.
- For all other systems:
Run ASSET.COM /S XXXXXXX, where XXXXXXX is the new service tag.
USAGE:
----------------------------------------------------------------------
Boot from the diskette and follow the on-screen prompts to erase and
program a new service tag.
See the comments in AUTOEXEC.BAT on how to automate the process.
General Information:
----------------------------------------------------------------------
This diskette contains 6 main programs or program types:
1. SVCTAG.EXE
2. 6 varieties of EE-ERASE
- EE-CP.EXE
- EE-CPA.EXE
- EE-CPB.EXE
- EE-LS.EXE
- EE-LS2.EXE
- EE-VALUE.EXE
- STAG.EXE
- STAG_W1.EXE
3. 3 varieties of ASSET
- ASSET.COM
- EE-VALUE.EXE
- STAG_W1.EXE
4. NICSET.EXE
5. FDD_RCL.EXE
6. SVCTAG.INF
1. SVCTAG.EXE is called from autoexec.bat. It is a utility that
determines if the system on which it is being executed is supported
by the disk. If so, it determines which type of system it is, using
the system ID byte. This information is gathered from either SMBOIS
calls or XBIOS calls, if SMBIOS fails. The utility also uses these
calls to determine if a service tag is currently programmed on the
system. If one isn’t programmed, there is no need to run EE-ERASE
so the utility goes directly to the ASSET program.
2. Based on the information gathered, SVCTAG.EXE launches the
appropriate version of EE-Erase.
Each of these utilities can be run stand-alone. For EE-CPA.EXE, the
-forcetype command line switch may be required.
3. The appropriate version of ASSET program is then launched.
SVCTAG.EXE first asks the user the enter the new service tag (twice
for verification) then passes that value to ASSET when it is
launched.
The ASSET programs can be run as a stand-alone utilities as noted
above.
4. NICSET.EXE is launched by SVCTAG.EXE after EE_ERASE if the system
is a Latitude C610 or Inspiron 4100. NICSET is needed in order to
unhide and enable the onboard NIC, which is disabled by EE-ERASE.
5. FDD_RCL.EXE is the launched from AUTOEXEC.BAT after SVCTAG.EXE. It
performs a Recalibrate operation on the floppy diskette drive.
The purpose of this utility is to ensure the FDD head is moved to
track 0 in preperation for transport.
It is important to power off the system immediately after this
utility is run in order to guarantee the head remains at track 0.
6. SVCTAG.INF is the text file contains vendor name, system id, ee-erase,
erase options, asset and asset options. This file is processed
by svctag.exe. The program goes through this file line by line
and searches for system id and BIOS vendor string which match the
system ID and BIOS vendor string read from the system on which
the utility is being run. If a match is found, the corresponding
line will be parsed and the executables and command line options
from that line will be used to erase and program the service tag.
Supported Systems
All Dell Portable Systems
Hi
I told you last time that I will receive more Dell optiplex 7040 in stock and I will get also 3040/5040 models.
I received this lot 2 days before and inside this lot was 5 pieces of 7040mt.
I used my old system 7040mt for your Modded bios 25/24 but I didn’t saw that this system was already committed because if you can see TAG number that mean it was committed.
I tested all your 25 bios with this system and they all work fine without any problems but didn’t test 24 bios.
I cannot confirm 100% that it is working because maybe it is recovering without showing that.
So this is why I used a new system of 7040 to show you how system come before and after it is committed.
You can see a picture which ask us to enter service Tag to commit sustem and select between options. Once we enter all details and apply then system is committed and will run in normal mode and never can change it.
Bios file which I sent to you is before I commit system 7040 in order to keep a virgin copy without TAG and other details.
MeInfo files are for system before and after system was committed like that you can see difference by your eyes.
Now I still have 4 Dell 7040 in office in non-committed mode which I can use to test.
Other commited models I can sell with intel 6th Gen CPU no problem.
Hope you understand me.
Thank you
Salim
Yes, I knew you had more 7040 coming in, but didn’t know they were there already. I did not download anything from your previous link, was waiting to figure out what is going on. DST can be removed/reset etc, with special tools, do you need those?
Committed in that since (Dell), is something very different from committed how we think of here with Intel ME/PCH (Dell committed and Intel ME committed are very different things).
I assume you know that, but to keep things clear and understood from us both, moving forward lets not use the committed when talking about Dell with a service tag set, it’s confusing and can be undone/reset while ME Committed cannot be undone/reset at all without chipset replacement.
Please send me one single BIOS file you want to use now, for all 7040 moving forward… and we start over I guess?
On the 25 test, that is great all work, then no need to test any of the 24 files toss them out, and there was no need to test further after finding a single one that works, sorry if I did not mention that.
So of the 14 BIOS I sent you, you say 25NoFVME.bin works fine (Does not stop boot, due to Bootguard/ACM), like previous BIOS ME-ucode.bin did? If so, great, that’s easy to set while doing ME
Hi
Please note that now I have 5 Dell optiplex 7040 in stock. 4 pieces still in Manufacturing Mode and wz can use to do our tests.
Please find the Bios backup file from a New system which i never used before.
https://fs04u.sendspace.com/upload?SPEED…TINATION_DIR=11
Thank you
Salim
Thanks! Do you need Dell DST tools to clear/change the Dell service tag and any associated ID’s etc?
Here, anyway, I posted this tool for another user in case you find useful. If you test and it works on desktop let me know (otherwise I will be finding desktop version shortly I assume for the other user if it fails for him)
Dell Optiplex 3020 BIOS flashing (2)
Also, you never answered me on my last paragraph above in #153, I need to know the answer there before making anymore BIOS.
@simoutekd - Link above is not a working link to download file, please upload again to another host if you can only get long URL’s from sendspace (me too right now, not working, valid URL is given on new page in link, short URL) -
site is working for me now, uploading files I mean, then it gives me correct shot linked URL on page refresh for downloads to share. Still unable to download file you linked, that’s an interim URL from URL bar you get when uploading, good links to share for uploads will be in middle of page on refresh once upload is done.
Same for package from post #150, those are not sendspace uploaded file links, you have to upload and wait until it’s finished, then page will refresh and link to share will be in middle of page
I have Kaby Lake CPU on the way now!
Please can you tell me which question you need me to answer.
If this one @So of the 14 BIOS I sent you, you say 25NoFVME.bin works fine (Does not stop boot, due to Bootguard/ACM), like previous BIOS ME-ucode.bin did? If so, great, that’s easy to set while doing ME@
Yes I tested all 25 Bios files you sent to me and all started without any problem and windows is working perfectly.
I didnt receive any notification on screen when computer started.
Hope this is what you need.
This is file you asked for.
Let me test your tool on Desktop.
https://www.sendspace.com/file/sog9o6
salim
Sorry for not saying what question exactly, but yes you got it correct. That’s great, my first edit was the right one then, and 13x others were unnecessary [smoking] ![]()
I will find the desktop version, please try that one I linked above, linked in the other threads, and see if it work on these Dell too (It might).
Thanks for re-upload, I got the file this time ![]()
CCTK and DDC is an option too for the service tag resets, but since I do not have Dell systems here I am not sure how easy this is to use
https://www.dell.com/support/article/us/…it-cctk?lang=en
https://www.dell.com/support/article/us/…systems?lang=en
Also, see this, it’s old now but may still work on some systems, second download link works I grabbed the file. Then read down for steps to run the service tag utility
https://community.spiceworks.com/how_to/…nspirion-laptop
Also! Bonus from the comments at the above link!
Here is ATAG_A209 (Asset is included in the previously linked package I uploaded DSTCD, unsure if same or same version) I think all same files in above link too, same CD ISO, but I see ATAG_209 and Asset in CD.ISO are different sizes, so probably different versoins too
https://www.dell.com/support/home/us/en/…?driverid=h3mvy
I also read this about the ISO I uploaded previously, for using ASSET
Usage:
ASSET new_asset_tag Specify new asset tag
ASSET /d Delete asset tag
ASSET /o new_owner_tag Specify new owner tag (if applicable)
ASSET /o /d Delete owner tag (if applicable)
See also, all the Dell belong to YOU ![]() open in firefox or FTP app
open in firefox or FTP app
http://ftp.us.dell.com/utility/
See also, other user here solved his service tag issue manually for one machine (So you can do similar for your one, if none of the above works for you)
Dell Optiplex 3020 BIOS flashing (2)
* Edit @simoutekd - Please test and confirm all OK with this BIOS, bootguard fix applied, ME + Microcodes added (Both this time) + Fit correction - vBIOS next, and doing it right now!
https://www.sendspace.com/file/20jqhv
*Edit - is this the exact system? Asking in regards to checking/updating GOP/vBIOS
https://www.dell.com/support/home/us/en/…desktop/drivers
Also, there is 2018 BIOS there, vs the 2016 one you sent me from dump. Can we update to that, or should we not/wait?
We may run into vBIOS issues ![]() , if it’s not one thing it’s another!!
, if it’s not one thing it’s another!! ![]()
2016 BIOS dump = vBIOS Intel(R) SKL1043 (2016/5/13) VBIOS X14 for D7/Potomac to fix 0xB2 issue, PB=HDMI, PC=DP, PD=DP - I think it’s OK, guide says 1034 and above "Should" support Kaby Lake (Even though kaby not listed in vBIOS data black name, I say?) -
but also, we can update to this one >> SKL/KBL Mobile/Desktop PCI Accelerated SVGA BIOS Build Number: 1046 - I wonder/hope/will find out if those PB=HDMI stuff transfers during update process)
Latest 2018 BIOS = vBIOS Intel(R) SKL1001 (2018/5/10) VBIOS X16 for D7 to fix BITS326748 issue, PB=HDMI, PC=DP, PD=DP - Going backwards? Older version number, new date, larger size than above, maybe this system I linked above is not same system?
See, both have some "Fix Issue" notation, possibly due to exact fix for those mini-systems? We’ll find out I guess ![]()
Hello
Let me answer your questions.
1- Regarding Dell optiplex 7040 link you sent to me; yes it is the right model I have in office and I can update my bios version to the last one but first I need to insert TAG number or system will not allow me to update Bios version. If you think there is no problem after we insert TAG then I can do it.
2- I will Flash your New Bios file with my programmer tomorrow morning and let you know the final result.
Hope it will work for us this time.
3- Can we do the same with HP AIO or no because I think that SureStart is same like BG or it is using BG as a part of his Routine and just giving a name to it.
Thank you
Salim
We can always change Asset Tag or Service Tag, so that would be OK. But lets go ahead and wait until end, for now we’ll use 2016 BIOS you dumped already.
I don’t think Surestart is same as Bootguard at all, but it may involve some aspects of it too. I think more inspection is needed on that board, did you try to find other flash rom on there and dump yet?
I will check this though, and send you BIOS to test if I find it’s set. We already checked MEInfowin correct, and no measured or verified Boot set on PCH side at end of report? Of course, none of that was set for this Dell systems either, but we still had to fix, so maybe it’s possible.
Please check MEinfoWin on one of the HP’s, and see at end if measured or verified boot is enabled on the PCH/Left side at bottom of report. If not, then we can disable like the Dell and see if this helps or not.
Hello
How are you?
Today I used your last Bios file you sent to me with my Dell Optiplex 7040MT and it works fine without any problem.
100% working.
I made a new Bios backup with FTP after I powered on my computer with your New bios file just for you to check if there is any problem.
I used MMtool to check file and I can see that there is 2 MC for intel CPU.
I think this time we got it.
Here is a link for you for Bios file after my system started.
https://www.sendspace.com/file/c9lh50
I am just worried about what will happen after we commit system from Manufacturing mode to Normal mode by pressing ALT-F.
Thannk you
Salim