Hi,
I recently flashed a modded, most up-to-date, BIOS onto my Dell Optiplex 7010 SFF. The modification which was done was to provide NVMe SSD support with the help of this guide ([Guide] How to get full NVMe support for all Systems with an AMI UEFI BIOS), together with @Lost_N_BIOS in this thread (Dell Optiplex 3020 BIOS flashing (4)).
It worked succesfully, but now I would like to get rid of all the security patches that came with Intel ME updates provided by the new BIOS version. To be more precise, I am talking about Spectre and its interacting with the OS. Now I understand that Intel ME is part of the boot process and can’t be removed, but one can prevent Intel ME from interacting with the OS if I understood that correctly and therefore get around Spectre. Am I right?
Now I found InSpectre tool. Running it as admin one can disable Meltdown and Spectre fixes on an OS level. The tool basically just edits some Registry Keys if I understand correctly. https://www.grc.com/inspectre.htm
On the other hand there is this python script called “me_cleaner” which basically edits the BIOS and kind of prevents Intel ME from interacting with the OS after booting. Correct? https://github.com/corna/me_cleaner
Now I would like to know if running InSpectre tool to disable Spectre gives the same result (or is the same) as running “me_cleaner”. Basically does InSpectre also prevent Intel ME from interacting with the OS, in a way as “me_cleaner” does?
Is it therefore enough to just run InSpectre and disable both Meltdown and Spectre fixes. Or do I have to use “me_cleaner” while also using InSpectre.
If so, how do I go about using “me_cleaner”?
I dumped my BIOS with FPTw. I modded it with UEFITool and used FPTw to flash the modded .bin by setting my PC in service_mode.
Any help and/or explanation on all this would be really nice! Did I understand correctly what these tools do and what Intel ME does?
@plutomaniac - Can you provide any help regarding this topic? If I understood correctly you are the expert here when it comes to Intel ME ![]()
InSpectre and ME_Cleaner are two very different and unrelated things. One is a virus block checking type tool which checks windows settings and CPU microcode version (InSpectre), and the other runs many aspects of your computer (memory speed, timings, CPU functions, fans, sensors etc) - ME FW
CPU microcodes are also part of the BIOS protection against stuff like that, not just ME FW. ME can be disabled, but I do not advise it, however it’s your system. If you want it disabled, I advise you do it properly with FITc and not with ME_Cleaner tools.
Someone else will have to answer you about how the tool works for disabling Spectre/meltdown stuff in windows, I haven’t a clue (ie pay no attention to any of it)
Sounds like you already used ME_Cleaner, and flashed in ME Disabled BIOS per whatever you choose with that script, so you’re all set. All the questions you asked above should have been asked, and answers waited on before you flashed anything BIOS related.
What is your reasoning behind any of your concerns above, internet fear-mongering get you?
Plutomaniac would be able to answer all that for you, but he is not available right now, and may not be around for a while longer (not sure how long) Best to google around research all the stuff you asked about, before doing what you did, not after
Haha don’t worry I didn’t do anything with ME_Cleaner yet
No that’s not the reason. I read and heard that Meltdown and Spectre have a significant impact on the system performance and I would like to get the most out of my PC. I only use it for gaming, so I don’t care too much about any "intruders", as I have nothing important on this PC to "share" hahaha ![]() So now I would like to know how to get rid of Meltdown and Spectre and I thought maybe InSpectre is enough.
So now I would like to know how to get rid of Meltdown and Spectre and I thought maybe InSpectre is enough.
Ok thank you for letting me know! And Merry X-mas!
Only early Spectre/Meltdown fixes caused noticeable slowdowns, at that was mainly due to Microcodes not ME FW
InSpectre disables it as the OS level, it’s explained on their site how that works. If you want to use older microcodes, then i need to first know your CPU model so I can tell yo if there is any pre-spectre/meltdown or not, then we can go from there.
If you put in older microcodes, you will have to stop windows update from replacing it, I’ll show you the edit (it may mess up OS now though, not sure, one report I saw broke there windows install 
Thanks, and Happy Holidays to you and your family as well 
Really? I didn’t find a lot of information on their webpage about the disabling feature. But I still don’t understand if disabling Spectre with InSpectre does the same thing as "disabling" Spectre from the BIOS side aka Microcode side. Do both methods stop interaction with the OS?
My CPU: 3rd Gen Intel® Core™ i7 3770 3.40GHz, 8M, VT-x, VT-d, TXT (vPro™), 77W
Yes sure we can try it! What exactly is the difference between older and newer microcodes? I always thought that a BIOS update bring updates for Intel ME (and therefore Spectre security updates, which slow the system) and Intel Microcodes (which mostly brings optimization and better performance). So I thought that it is GOOD to keep newer Intel Microcodes, because they bring better performance and at the same time it’s better to downgrade Intel ME (by BIOS Modding), because it slows the system down. Did I understand this wrong?
About windows update: I will do a fresh install of windows (with ethernet cable disconnected) and disable all windows update features in services.msc after I am done with the BIOS stuff.
Intel’s ME isn’t responsible for Spectre/Meltdown performance, uCode updates are.
Here’s wiki about ME : https://en.wikipedia.org/wiki/Intel_Management_Engine
Newer microcode has updates for Spectre/Meltdown, because that’s the level at which those issues are. You have make sure CPU process information in secure way, so that S/M can’t get what they want.
As Lost_N_BIOS explained. Recent uCode updates “fix” vulnerabilities on BIOS level, which makes them OS independent (you can’t “turned them off”).
I’m also pretty sure, there are no LGA 1155 (or LGA 2011-1) boards that had beta/official BIOS’es released with uCode fixed for Spectre/Meltdown.
Ok I understand. So only by downgrading uCode/microcode you can remove the performance hit that Spectre/Meltdown bring? But what does InSpectre tool do then? You have the two options to disable Spectre/Meltdown with that tool and get better performance also.
No.
A certain windows update will override uCode used by CPU if it’s too old, with version provided by Intel to Microsoft (Lost_N_BIOS mentioned this already…).
That’s where Disable functions in InSpectre come in.
You can disable Spectre and Meltdown fixes seperatly, from Windows/software side (that’s why you have two options to disable).
Also, it’s not “get better performance”, it’s about not losing it with fixes enabled.
Only Haswell and later CPUs can get “better perf.” with mitigations still enabled.
Again - NOT getting better performance overall, it just limits the impact on performance from enabling mitigations.
Lmao…I just realised… uCode = µCode = Microcode. Were talking about Intel Microcode all the time already and I was trying to figure where the difference is between Microcode and uCode 
Ok, but what I am trying to get answered is, if it is enough to just use InSpectre for Spectre and Meltdown fixes or if I need to mess with Intel Microcode in addition to InSpectre.
True, sorry I worded it kind of strange.
Also in your previous post you said:
Would that mean that I could just revert back to some early/beta BIOS and I would be good? Because on the one hand I want to have the latest BIOS running, on the other hand I don’t want those Microcodes coming with latest BIOS putting a performance hit on my system with their Spectre/Meltdown fixes.
100% depends on platform.
For Sandy/Ivy - in most cases* you are fine with just InSpectre Disable options (+ deleting file with patched uCode that Windows update injects).
For Haswell and later :
If BIOS you are using is from 2017 or earlier - it’s the same as Sandy/Ivy.
Only in case where you have MB that has BIOS from 2018 and later, OR a *moded BIOS with uCode updates inside - you have to worry about downgrading it’s version.
What is CPU model here, that would help a lot (at least for me, because I don’t look at official BIOS, only actual uCode in this regards + CPUID)
I say that because many BIOS “Could be” updated with ucode to prevent the spectre/meltdown issues, or downgrade uCode to "perform maybe better than if you had latest uCode
Latest BIOS can be used, and still old uCodes placed back in if desired. As mentioned above though, if latest BIOS is 2017 or possibly 2018, then may not even have Spectre/Meltdown uCodes in it anyway so no BIOS mod needed to downgrade uCodes.
Mine has LGA 1155 with Q77 Chipset, so therefore Ivy I guess according to: https://en.wikipedia.org/wiki/LGA_1155
and: https://ark.intel.com/content/www/us/en/…ss-chipset.html
I do have this BIOS though from 18. July 2018: https://www.dell.com/support/home/us/en/…e=optiplex-7010
It has been modded to include NVMe Module. I did no modding regarding Microcodes.
I already told you my CPU model @Lost_N_BIOS ![]()
Well my current BIOS is from 18. July 2018: https://www.dell.com/support/home/us/en/…e=optiplex-7010
You helped me modding it, do you remember ![]()
Here is the download link you gave me: http://s000.tinyupload.com/index.php?fil…141853363214057 from this thread: Dell Optiplex 3020 BIOS flashing (4)
EDIT: According to this reddit (I know I know) it should be enough to just run InSpectre and disable it. If your microcodes are updated by Windows and the microcodes in the BIOS are older than the microcodes that came with Windows, then the microcodes from Windows will be loaded on OS level. Now if you run an old OS (like 1709), which I am planning to do, then those microcodes can’t/won’t interact with the OS: https://www.reddit.com/r/intel/comments/…e_updates_from/
Question still remains if you guys think otherwise and downgrading microcodes on BIOS is still a good idea. If so I would appreciate any help regarding modding the BIOS from above link. Or if you need a full BIOS dump (the 12mb that covers the 4mb and 8mb chip) and not only the 6144kb dump then please let me know and I can share it with you.
Sorry, I did look back when I asked, and in first post, but missed your CPU model mentioned in post #5 
If you let windows replace microcode it will be latest, and your BIOS already contains spectre/meltdown bugfix microcoes (not the latest ones, but still has the earlier fixes in there)
I personally suggest running the latest microcode and ME FW, you will not notice any performance losses anyway, most in the performance hit early microcodes could only be noticed by benchmarks not actual computer usage.
However, if you want to downgrade microcodes we can, you need >> cpu306A9_plat12_ver0000001C_2015-02-26_PRD_2F737D45.bin & you have to stop windows from loading it’s own.
All this, has nothing to do with InSpectre, I am talking BIOS level edit and whatever you do with windows microcode file only.
Haha no problem man ![]() I guess you found the CPUID by googling for "my CPU Model + CPUID"?
I guess you found the CPUID by googling for "my CPU Model + CPUID"?
May I ask how you found the microcode revision? Did you have to open the NVMe BIOS.bin in UEFITool to find it?
Do you need CPUID + CPU Model + Microcode revision to find the "old" microcode? Or why do you need it?
I will do a fresh install of Windows 10 1709 on my NVMe and optimize it and disable all Windows Updates off. But if you want you can explain me your method to turn off Windows Updates. ![]()
Sure let’s try it! Maybe we can do it like last time when we modded the BIOS for NVMe and you point me to the correct guide/tutorial that I need? Maybe you can explain the steps to me?
Can we use the modded NVMe BIOS file you created for me (http://s000.tinyupload.com/index.php?fil…141853363214057) as starting file or do we need a fresh full 12mb BIOS dump this time with FPTw. If we need a full 12mb dump is there a different command for that?
Edit: @Lost_N_BIOS can the flashing part be done with service_mode + FPTw again? Or will it be locked regardless of service_mode?
@Lost_N_BIOS - Is this where I need to grab cpu306A9_plat12_ver0000001C_2015.bin? Link: [OFFER] Intel CPU Microcode Archives
@Koven - Yes, CPUID found for your CPU model at CPU-world.com
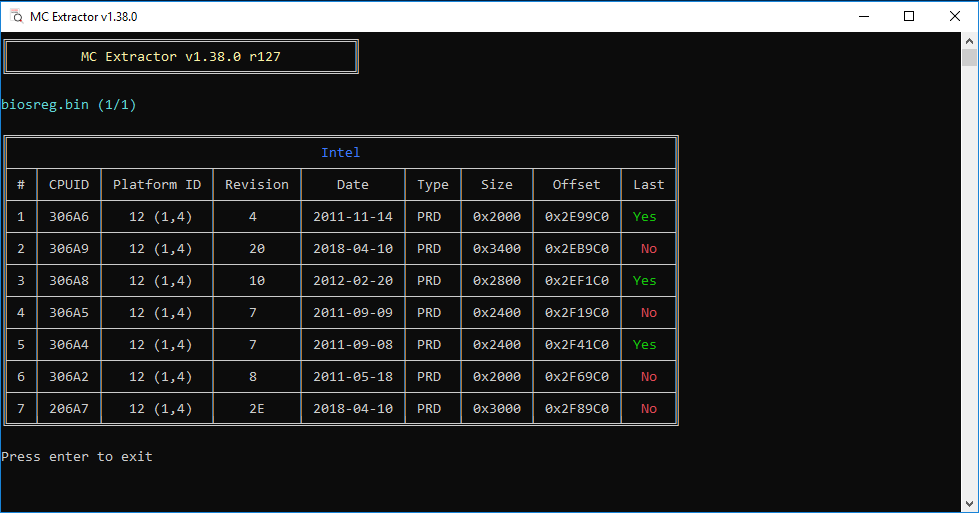
Current microcode version in BIOS is found by dropping BIOS file on MC Extractor - https://github.com/platomav/MCExtractor
To find the old microcode, I’ll simply go to our pre-spectre microcode repo and get the one there for your CPUID
Windows updates is fine, you can’t disable windows updates anyway can you? What you need to do is delete the microcode file windows uses, and check often to make sure it’s not added back again (or check often current in-use microcode with AIDA64 or HWINFO64)
Here’s how to delete the windows microcode file - Intel, AMD, VIA & Freescale CPU Microcode Repositories Discussion (19)
Yes, I would use the mod BIOS I already made for you, and just edit that. Yes, flash with service mode jumper on and FPT. And yes, that page you linked is the repo I meant.
Microcode edit can be done with MMTool 4.5, or UEFITool 25 and hex editor, sorry I’ve not written any guide for this, but we do have some already here for UEFITool editing
However, it’s outdated and does not apply directly to your BIOS type -[GUIDE] AMI INTEL CPU Microcode Update Guide
MMTool is much easier, but no guide here about it. Basically, open BIOS in MMTool 4.50.0.23 go to “CPU Patch” tab and delete the one one for your CPUID, and insert new one, then save file with new name (and rename extension to .bin once done)
^^ MMTool 4.50 does not show all microcodes, and does not do the edit correctly (removes a bunch of others), so do not use this. 5.07 shows them all, but you can’t edit, same for 5.024/25 too.
So, this edit must be done with UEFITool 51-55 for extract and version 25 for insert. In this BIOS all microcodes must begin at a multiple of 800h (so 0h, 800h, 1000h, 1800h, 2000h, and so on), if previous ends before a 800h multiple fill with FF till the next 800h multiple
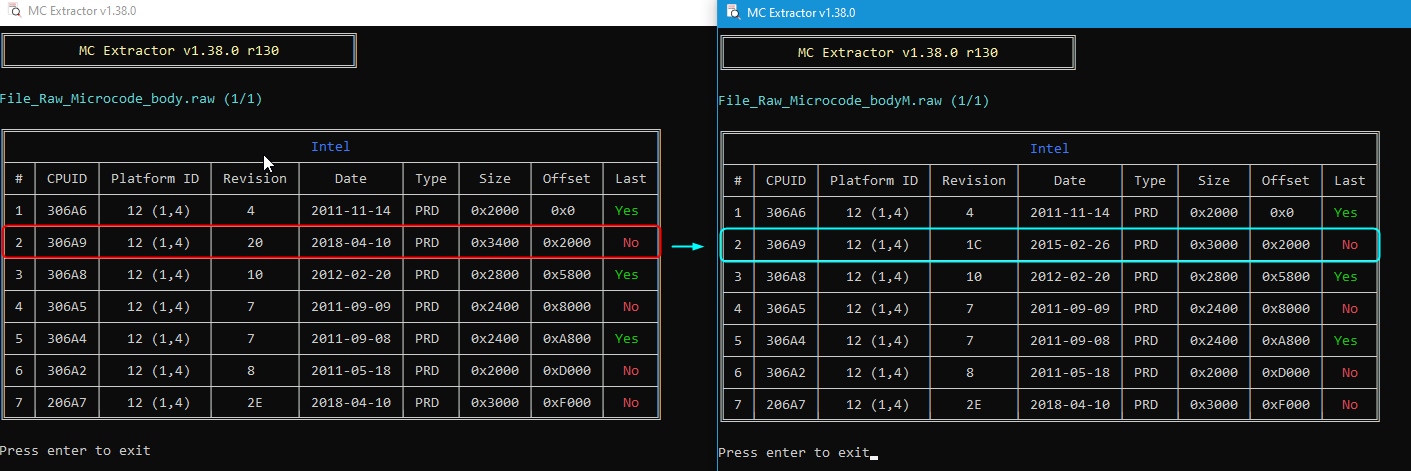
Since the one you want to edit in is smaller than original you can FF the entire original 306A9 space of the extracted microcode body 2000h-5800h and then paste in the 1C version at 2000h (make sure you past over, not insert, so all alignments are kept and file size is not increasing)
Once done drop new mod BIOS on MC Extractor to confirm your new microcode is in there replacing the old, and no errors shown in MC Extractor.
In MC Extractor, you’re mod microcode body should look like this once done, vs stock one. Notice the offsets all remain same, and the size of the one we edited is now different
Then flash like before, making sure you use the -bios flag >> FPTw.exe -bios -f nvmeucode.bin
I have BIOS done for you if you want, but didn’t upload since it sounded like you wanted to try doing yourself 
@Lost_N_BIOS my FIT tab is greyed out. I am not sure if has always been like that… The only thing that changed is that I installed my OS again. I believe it worked a few days ago… It doesn’t matter if I use the bios file from the NVMe edit last time or if I dump a new one or if I use the full 12MB one… All have FIT tab greyed out…
Does your FIT tab work with my BIOS?
Is it a good idea to not only update CPUID 306A9 to the most up-to-date pre-spectre microcode, but also all the others that say "No"?
Also why do we change CPUID 306A9 when on cpu-world it says that i7 3770 CPU has CPUID 306A4: http://www.cpu-world.com/CPUs/Core_i7/In…3770.html#cpuid
Maybe it would really be easier if you just send the download link ![]()
@Koven - Dell 7010 BIOS does not have FIT table, so you’re OK there
Yes, if you want, you can update all the others if you want. That makes the edit a bit different though, just follow the rules I mentioned above, and since you’re going ahead with all, you can go ahead and put your CPU’s microcode first if you want.
Yes, sorry, you are correct! Not sure why I showed changing 306A9, I guess my incorrect mention of it at previous post made me assume I said correct one there and I just carried on
306A4 already has latest microcode, and it is a pre-Spectre/meltdown one too (since 2011). I see why I said 306A9 now, because this pre-spectre thread had 306A9 as only one shown for IVY - [OFFER] Intel CPU Microcode Archives)
Your CPUID not there, because default/latest is already pre-spectre, the 3770K is 306A9 and has a Spectre/Meltdown update - you don’t need to do anything here for microcodes (Sorry I didn’t notice that sooner!)
So, do you just need NVME Mod BIOS, or you already did that yourself?
* Edit - @chinobino - I see some posts saying all quad IVY 306A9, why this one is 306A4 in CPU-world, or did it used to be 306A4 at launch, but now all IVY Quad load/use 306A9?
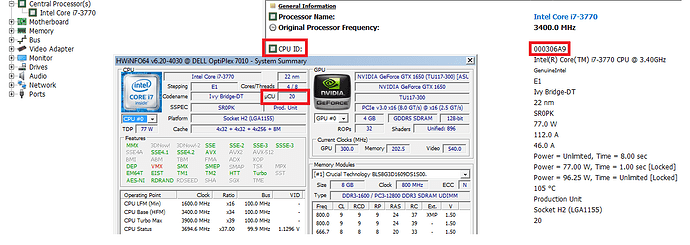
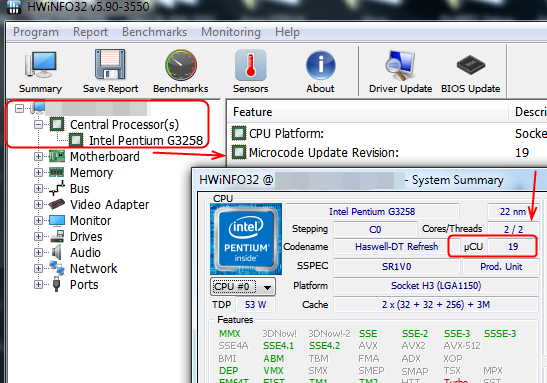
@Koven - load HWINFO64 , see image below, what do you see, 7 or 20?
@Lost_N_BIOS - Damn ok, but how do I find the microcodes in the BIOS region then? 
But even if 306A4 is the correct one for me and has no spectre/meltdown on it (because the microcode is from 2011 and the latest), do the other CPUID not influence Spectre/Meltdown then? For example 306A9, is from 2018 with spectre, does that not matter? Is it not needed to downgrade that one? Or what about 206A7, it is also from 2018, so probably has Spectre on it. Or is that not how it works?
We already did the NVMe flash ![]()
Here you go, looks like it 306A9 indeed:
Could you share the download link for my bios with Microcode mod? Just in case I give up editing my bios by myself hahaha
@Koven - MC Extractor will give you exact location by offset where the microcodes are located, then you can use “Action >> Go to Offset” in UEFITool or go directly to each in hex editor
https://github.com/platomav/MCExtractor
Or you can use search in UEFITool, by GUID, and this is the microcode module GUID - 17088572-377F-44EF-8F4E-B09FFF46A070
Only the in-use microcode for your CPU matters here, all others you can ignore. So, I was correct first time around then, your CPU is using 306A9 

Here is the mod BIOS I made for you previously (NVME mod one) with pre-spectre 306A9 microcode 1C from 2015
https://ufile.io/dc57xv6i