I successfully managed to remove ME backdoor using me_cleaner using this command:
To clean the ME and set the MeAltDisable bit: me_cleaner.py -O cleaned_bios.bin -S dumped_bios.bin. No more ME problems and vulnerabilities.
@ RamGuy:
Yes when it comes to ASUS, they tend to tie the BIOS version with the CSME firmware on some motherboards, causing issues when updating manually. I suppose the board rebooted before updating the CSME firmware, that’s how it’s usually done.
@ nikoZ:
What backdoor? That’s your own personal belief, not a fact. No matter what, me_cleaner reports must be posted at Issue 3.
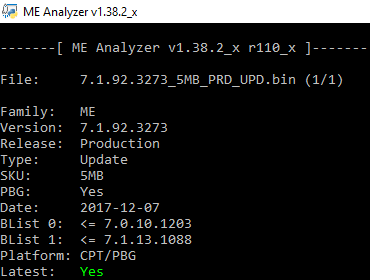
Intel ME 7 5MB Firmware v7.1.92.3273
There are same with other ASUS Mobo since RAMPAGE V Extreme era. I think ASUS may locked there product for ME Firmware, Gigabit Firmware etc. So we cannot manual flash ME Firmware, Gigabit Firmware like older mobo era anymore.
Not only Firmware locked , after talking with ASUS Technicians support they said. There are no BIOS copy feature anymore.
In other words, after pass 3 Years warranty period, If your BIOS 1 bricked or corrupted from any case. There are only RMA channal to fixed the mobos, Ofcause we must pay all shipping , part replacement, labour charge,etc. Otherwise we must selling the mobo before ending of warranty.
After read your respons “ these update seem…without any issue”. I ‘ve many hopeful for ASUS product again.
Updated OP with:
Intel MEI v11.7.0.1058 for Corporate systems Drivers & Software
I have ASUS X99-A II motherboard and ASUS offers on download page package of Intel Management Engine Interface, v11.0.0.1172, 76MB. As plutomaniac suggested, I’m going to manually install INF files from Seaction A1 of this thread, v11.7.0.1045.
I noticed that inside this ASUS package there is some hotfix for IMEI - it’s some “Kernel-Mode Driver Framework 1.11” (KB 2685811) and it “needs” to be installed when using Windows 7.
I am using Windows 7 and my question is: if I am going to use only INF manual installer from section A1 should I still install this hotfix / KB 2685811 first?
KB 2685811: https://support.microsoft.com/en-us/help…ndows-vista–wi
Make sure you have the latest Windows updates installed. Then pick the latest driver from this thread.
@plutomaniac : What I found is that KB2685811 is not installed by default and should be manually installed when it’s needed.
I know that KB2685811 is required for “full IME setup” (with software & system services).
I do not know if KB2685811 is required for just IME INF driver (without any additional software or system services - just like in Section A1) - and this is the driver I want to install.
That’s why I asked this question as I do not want to install KB2685811 if I do not need it.
EDIT: On this youtube video IME setup shows an error/failure during “Intel Management Engine Components” installation caused by no KB2685811 installed (this error is visible around 00:50 video time).
I did manual installation of IME INF driver only from A1 section of this thread and it installed without any errors on Windows 7 without KB2685811.
My question remains: do I still need to install KB2685811 just for this IME driver to function properly or not?
Maybe this KB2685811 is only required by IME’s software and/or system services which I do not have installed?
I have a question.
What is the right way to update bios on GIGABYTE motherboard from version that has 9.0 ME to another with 9.1 ME.
Can I use Q-Flash or only FPT ?
Hi, I’m trying to downgrade Intel ME and I’m not capable. I currently have version 11.8.50.3425 LP and I’m trying to downgrade to version 11.0.0.1205 LP which is what I had previously.
I have tried with the following tools: afuWIN, flash programming tool, FWUpdate and in all I get an error:
Flash Programming tool:
Error 368: Failed to disable write protection for this BIOS space.
FWUpdate:
Error 8705: Firmware update not initiated due to versión miscmatch
AfuWin:
Error: BIOS does not support AFU.
Add the information obtained through MEInfo:
BIOS Version Version 1.10
MEBx Version 11.0.0.0005
GbE Version 1.3
Vendor ID 8086
PCH Version 21
FW Version 11.8.50.3425 LP
Security Version (SVN) 3
LMS Version 11.7.0.1043
MEI Driver Version 11.7.0.1040
Wireless Hardware Version 2.1.77
Wireless Driver Version 18.21.0.2
How could I do the downgrade?
I have one more question in addition to my previous post. I used ME Analyzer and got this:
-------[ ME Analyzer v1.38.1 r109 ]-------
File: X99-A-II-ASUS-1701.CAP (1/1)
Family: ME
Version: 9.1.37.1002
Release: Production
Type: Region, Extracted
SKU: 1.5MB
SVN: 1
VCN: 12
PV: Yes
Date: 2015-11-07
FITC Ver: 9.1.10.1000
Size: 0x17D000
Platform: LPT/WPT
Latest: Yes
Is this the right firmware version to use Intel MEI Driver v11.7.0.1045 from A1 section of first post in this thread?
Hello, I am using Z170X-G3 Gigabyte and my FWUpdate is locked to Disabled. I have the latest bios from the manufacturer. however whatever I tried to do I could not patch Intel ME to fix the vulnerabilirty, I mailed them regarding this matter. I was wondering if there is any other way around to fix it? Thank you!
ASRock H97 Pro4 (P2.00) & Version 1709 (OS Build 16299.192)
Intel(R) Management Engine Interface v11.6.0.1026 (9/1/2016)
What should I do? Thanks.
http://i63.tinypic.com/24g0jlu.png
http://i68.tinypic.com/23u51dv.png
@Lex FYI, 11.7.0.1045 also the same. “This system is vulnerable” We need a new bios, but unfortunately my motherboard is EOL. I’ve emailed ASRock. 
Hello Everyone, just signed up.
I have an Asus UX305UA notebook (Skylake i7-6500U), after updating with official Asus ME firmware tool, MEinfo says (upon other things):
My question is:
If the update revoked the endorsement key, platform is unable re-key, how is it possible that a re-key is not needed ?
Did this update in some way hamper my ME/TPM functionality ?
Please note: before update MEInfo output was:
Unfortunately I couldn’t find info on the net, every other meinfo output I came accross was "Platform is re-key capable" "True".
If the EK in my TPM is revoked, and a new EK is not rolled in hardware, which EK is used to derive my bitlocker encryption key???
It sounds almost like a useless TPM <– hope to be wrong.
Any help really appreciated, thank you very much
EK Revoke State is mystery, I successfully re-keyed with latest Intel ME drivers (I have Platform re-key capable True though) but still FPF state remained Revoked so don’t think it FPF value can be reversed.
Also not really sure what Revoke state actually means, but Intel PTT TPM is still usable with this state without any issue so far.
Were you actually using TPM with bitlocker when you updated ME firmware? I was, so maybe FPF Revoke state is changed to Revoked when you actually use TPM (EK). Most people don’t use TPM so it stays Not revoked after Intel ME fw fix.
Just to be sure I cleared CMOS, cleared TPM, and encrypted whole drive from fresh. FPF Revoke state still remains Revoked though.
any idea what this new version actually does? I’m surprised there is new version released for ME 7 since 7.1.91.3272 was last and Intel stated ME 7 is already out-of-support. I guess it is not related to SA00086 because there is no mention in user guide about this version. *ME 6-10 only Corporate SKUs are vulnerable , fw fixes only for ME 8+ so basically Intel ME 6-7 are out of luck and left vulnerable ![]()
I suspended Bitlocker before updating (not disabled, suspended); now I disabled it and updated to 11.8.50.3426 (was 11.8.50.3399), still same output; maybe this EK is not related to tpm, or I’m missing something, don’t know.
Cleared TPM multiple times.
Hope someone with full knowledge can shed some light
TPM fully usable before and after
I think it may be related actually, because when you suspend bitlocker, bitlocker keys are still present in TPM.
So when you update ME with any key present in TPM (key is generated in EK chain) I think that’s where FPF EK gets to revoked state. Maybe if you’ve turned off bitlocker and cleared tpm, then there shouldn’t be any keys in EK chain and FPF would have stayed Not revoked.
That’s why most people don’t have FPF Revoke State Revoked, because most of the people don’t actually use Intel PTT TPM.
Just speculating.