(Posted this in multiple forums prior)
Recently, Github user nkht has reported success in removing the entire Intel ME firmware from his/her Asus Rampage IV Extreme motherboard. Apparently, the Intel ME Watchdog is not active in some/all of the existing X79 PCH and hence the system does not turn off every 30 minutes as expected. I then attempted this on my Asus Rampage IV Gene motherboard and also obtained similar results.
The findings can be found on the following links:
https://github.com/corna/me_cleaner/issues/278
https://github.com/nkht/me_removal
Basically, the entire “ME region” in the BIOS image has been cleared by replacing the region with “FF” using a Hex Editor/UEFITool. Additionally, the MEI controller initialization can be halted by flipping a bit in the MEPlatformPEI module found in the BIOS Region.
Systems with potentially broken Watchdog timers:
LGA2011-0, LGA2011-1, LGA1356: Motherboards using the X79/C600 series chipset
Untested systems:
LGA1366: Motherboards using the X58/5000 series chipset
LGA1567: Motherboards using the 7500 chipsets
LGA2011-3: Motherboards using the X99/C612 chipset
Likely incompatible systems:
Any system running Skylake or newer CPUs, as their ME mechanism have changed substantially
Most mainstream LGA115X platforms and mobile platforms, especially for those using iGPU
All systems with Intel Boot Guard enabled by the manufacturer
Potential downsides of removing Intel ME completely
1) If your PCH has an active watchdog timer, your system will turn off after 30 minutes, or stop booting altogether and you will need to re-flash your backup BIOS.
2) Any and all Intel ME/AMT features will no longer be available after applying this modification.
3) Possible instability or broken features after modding. For example, the LAN port may not function after a cold boot and requires re-initialization or a reboot. POST timings might also increase.
To test this yourself
If you would like to attempt this modification yourself, you may proceed to the links above to understand the findings, and/or simply just change your entire ME region to FF using HxD/UEFITool without changing the size of the region, and flash the image/ME region onto your motherboard. A CH341a flasher would be recommended for backup in case the BIOS flash fails, especially since the Intel ME region which is often write-protected. It will also be a good idea to backup your current BIOS containing your motherboard UUID, Serial Number and MAC address using tools such as FTK8/FTK9, or dumping via the SPI flasher. For Asus motherboards with USB Flashback, you may rename the modified .CAP file to ERALL.CAP and flash using a USB Drive. Do keep in mind to add your motherboard UUID, Serial Number and MAC address to ERALL.CAP using FD44, otherwise those information may be permanently lost.
Conclusion
It seems like some Intel chipsets (more likely those with ME 6.x to 10.x) could be shipped with deactivated ME watchdog timers. In this case, it is possible to remove the Intel ME firmware entirely on those systems/platforms. However, the exact chipsets which do not have the active timer are still relatively unknown.
didnt understand your point?
is this happened with intel specter patched?
dont know how you receive watchdog violation
On systems with watchdog, if you properly disable ME (via FITc) then it doesn’t reset every 30 minutes either
You also forgot to mention, without ME FW, usually fan control is broken (fan at full speed always) and sometimes overclock/memory controls do not work properly either.
@XGen Win7 is better than Win8 

@XGen - I hate Win8-10  both seem slower to me than Win7, and much less reporting back to MS and big brother with Win7
both seem slower to me than Win7, and much less reporting back to MS and big brother with Win7 
@weareanomalous - see above, Xgen has a question, thanks!
This modification is contingent upon the status of the Intel ME Watchdog timer, and is not related to DPC watchdog (Windows 8/10). Spectre is still patched as the (updated) microcode is not removed from the BIOS image. Without an active watchdog timer, a blank ME image can be used without 30 minute shutoffs. Of course, I’m not encountering DPC_WATCHDOG_VIOLATION BSODs on Windows 10 either.
I still experience proper fan control (I guess the Asus EC is controlling it?), and I did overclock the processor by 0.1GHz to x40 on all cores, and RAM to 1600MT/s without problems (I could go higher, but I prefer not to overvolt, and x41 multiplier is unstable even on single core). Corna, the owner of the ME_Cleaner repo also mentioned that the fan control is usually not controlled by Intel ME especially on no-so-old systems.
Currently, running MEInfo on my system results in the following error:
Error 9460: Unknown or unsupported hardware platform
This FITc is quite interesting. I tried to read and understand the help file to no avail though. Is it capable of doing the same thing as ME_Cleaner (/s flag) by setting the HAP bit, or disable the ME by putting it into manufacturing mode?
Yes, it may be controlled by EC, same for memory/OC control options too (That’s less of an issue usually, but some boards can take this hit with corrupt ME FW).
Usually it’s mainly full speed fan issue I see. Yes, you can set HAP Bit to disable ME via FITc, I’m not sure about what manufacturing mode does, you’d have to ask Plutomaniac about that one.
To set that with FITc, go to ME Kernal and then at bottom setting “Reserved” set to Yes
Apparently the manufacturing mode is simply setting the HDA_SDO pin on a (usually server) motherboard to high. Initially I had doubts regarding the FIT because I suspected there may be a software version of ‘setting the pin’, which doesn’t seem to be the case since FIT toggles the HAP bit instead.
There also seems to be a firmware version of the HDA_SDO pin: https://github.com/corna/me_cleaner/issues/214
FIT is definitely an interesting tool nevertheless.![]()
I don’t know too much about ME FW, plutomaniac would be able to answer you or give you more info on the manufacturing mode when he sees this thread
Regarding Manufacturing Mode, read these:
http://blog.ptsecurity.com/2018/10/intel…de-macbook.html
https://twitter.com/platomaniac/status/1047460521723793413
[Guide] Clean Dumped Intel Engine (CS)ME/(CS)TXE Regions with Data Initialization (4)
plutomaniac - Thank you! Reading your comments at Twitter leads me to a question 
So, if system has FPF burned fuses, but OEM/User Mnf mode not closed, I see we can check if Mnf mode enabled with MEINfo -fwsts, but how to see if it’s closed or not?
If it’s not closed, and FPF fuses burned, can BootGuard be disabled by user to then flash in mod BIOS, and if yes what is proper way to do that in this situation where Mnf mode is not closed but FPF burned in?
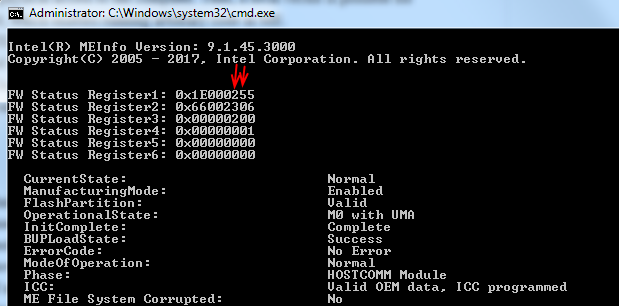
Further absorption has occurred [rgin] - Reading your first link, I think it means we can check here, if I see 25 then it’s closed correct?
Thanks 
You can use MEInfo to see if Manufacturing Mode is enabled or not. It reads FW Status Register 1 and displays the value for easy reading. More info on this can be found at the first link by the PTSecurity guys. Burned fuses means that the "OEM" Manufacturing Mode is over so an "enabled" Mnf after that is the "User" one, per my naming. If you see uncommitted FPF and Mnf enabled then you can do whatever you want basically, like the OEM before it leaves the factory.
Thanks, I tried to figure that out about FW Status register one at your first link, but unsure if I understood correctly, so I added that image above in a later edit to ask/confirm
So if measured/verified boot enabled at FPF, then nothing else matters and there’s nothing you can do no matter what except replace PCH, correct?
No, only the 4th (starting from 0, thus 5th) bit of FWSTS1 in LE shows the Manufacturing Mode state. Example:
0x1E000245 = 0b00011110000000000000001001000101 (Disabled)
0x1E000255 = 0b00011110000000000000001001010101 (Enabled)
If FPF are set, they are permanent so yes, new uncommitted PCH.
Thanks, all so confusing still  I thought that would show Mnf closed or not, not that it showed Mnf mode enabled/disabled (since that is already easily visible with MEInfo)
I thought that would show Mnf closed or not, not that it showed Mnf mode enabled/disabled (since that is already easily visible with MEInfo)
I’ve been confused with ME since day one here, and our first conversation, I’m sure you remember too, I don’t think I’ll ever be able to keep it all straight 

What’s that mean >> ME FPF Fusing Patch Status: ME FPF Fusing patch NOT applicable
This is from system with Bootguard set (measured/verified boot enabled at FPF)
They are the same. The easily readable text that MEInfo shows comes from analyzing the FW Status Registers.
Some sort of FPF patch they released without public disclosure a little more than a year ago.
Ahh, so I don’t even need to check anything with MEInfo then, gotcha 
So that FPF Patch = nothing to do with what I’ve been asking about  Thanks
Thanks
plutomaniac, can you explane me, how can i protect my system on mobo MSI z97 if all keys (bootguard etc are FFFFFF)? Also my mobo has SA-00086 vulnerability and Manufacturing Mode is enabled. I want to shut down Manufacturing Mode but i need to config my OEM keys, bootguard etc. What to do at first?
BG requires OEM BIOS integration as well. Just close manufacturing mode via “fptw64 -closemnf”, if it’s open. Use FWUpdate tool to update the ME firmware to the latest possible.
I didn’t understand this “BG requires OEM BIOS integration as well”, can explain? I read that if a hacker knows the keys to the ME modules, then the system is considered not secure. If all my keys is empty i think this is vulnerability