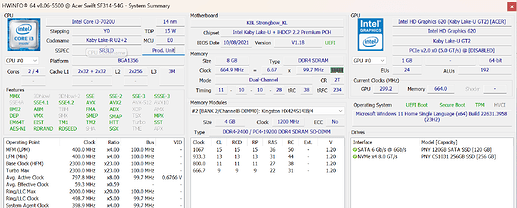
The device i’m currently working on is acer swift 3 sf314-54g (Insydeh2O). the hinge has already been reinforced with the back cover, i can’t open it again. otherwise, it will tear up the chassis.
I’m new to using a hex editor, and I doubt I’ve done it properly XD. Any advice and insights would be greatly appreciated.
Thanks in advance! ( ╹▽╹ )
MEInfo -verbose
Intel(R) MEInfo Version: 11.8.92.4189
Copyright(C) 2005 - 2020, Intel Corporation. All rights reserved.Windows OS Version : 10.0
FW Status Register1: 0xA0000245
FW Status Register2: 0x00F60506
FW Status Register3: 0x00000020
FW Status Register4: 0x00084004
FW Status Register5: 0x00000101
FW Status Register6: 0x40488B4ECurrentState: Normal
ManufacturingMode: Disabled
FlashPartition: Valid
OperationalState: CM0 with UMA
InitComplete: Complete
BUPLoadState: Success
ErrorCode: No Error
ModeOfOperation: Normal
SPI Flash Log: Present
FPF HW Source value: Not Applicable
ME FPF Fusing Patch Status: ME FPF Fusing patch NOT applicable
Phase: ROM/Preboot
ICC: Valid OEM data, ICC programmed
ME File System Corrupted: No
PhaseStatus: AFTER_SRAM_INIT
FPF and ME Config Status: Match
FW Capabilities value is 0x31111240
Feature enablement is 0x31111240
Platform type is 0x41130321
No Intel Wireless device was found
Intel(R) ME code versions:Table Type 85 ( 0x 55 ) found, size of 0 (0x 00 ) bytesBIOS Version V1.18
Table Type 85 ( 0x 55 ) found, size of 0 (0x 00 ) bytes
Table Type 0 ( 0x 00 ) found, size of 55 (0x 37 ) bytes
Table Type 1 ( 0x 01 ) found, size of 103 (0x 67 ) bytes
Table Type 2 ( 0x 02 ) found, size of 120 (0x 78 ) bytes
Table Type 3 ( 0x 03 ) found, size of 82 (0x 52 ) bytes
Table Type 4 ( 0x 04 ) found, size of 185 (0x B9 ) bytes
Table Type 7 ( 0x 07 ) found, size of 29 (0x 1D ) bytes
Table Type 10 ( 0x 0A ) found, size of 193 (0x C1 ) bytes
Table Type 11 ( 0x 0B ) found, size of 18 (0x 12 ) bytes
Table Type 12 ( 0x 0C ) found, size of 96 (0x 60 ) bytes
Table Type 14 ( 0x 0E ) found, size of 14 (0x 0E ) bytes
Table Type 16 ( 0x 10 ) found, size of 25 (0x 19 ) bytes
Table Type 17 ( 0x 11 ) found, size of 113 (0x 71 ) bytes
Table Type 19 ( 0x 13 ) found, size of 33 (0x 21 ) bytes
Table Type 20 ( 0x 14 ) found, size of 37 (0x 25 ) bytes
MEBx Version 0.0.0.0000
GbE Version Unknown
Vendor ID 8086
PCH Version 21
FW Version 11.8.97.4739 LP
Security Version (SVN) 3
LMS Version Not Available
MEI Driver Version 11.7.0.1057
Wireless Hardware Version 2.1.77
Wireless Driver Version 23.110.0.5FW Capabilities 0x31111240
Intel(R) Capability Licensing Service - PRESENT/ENABLED Protect Audio Video Path - PRESENT/ENABLED Intel(R) Dynamic Application Loader - PRESENT/ENABLED Service Advertisement & Discovery - NOT PRESENT Intel(R) NFC Capabilities - NOT PRESENT Intel(R) Platform Trust Technology - PRESENT/ENABLEDRe-key needed False
Platform is re-key capable True
TLS Disabled
Last ME reset reason Global system reset
Local FWUpdate Enabled
BIOS Config Lock Enabled
GbE Config Lock Enabled
Get flash master region access status…done
Host Read Access to ME Enabled
Host Write Access to ME Disabled
Get EC region access status…done
Host Read Access to EC Disabled
Host Write Access to EC Disabled
Protected Range Register Base #0 0x6C0
Protected Range Register Limit #0 0x7FF
Protected Range Register Base #1 0x290
Protected Range Register Limit #1 0x5CF
Protected Range Register Base #2 0x0
Protected Range Register Limit #2 0x0
Protected Range Register Base #3 0x0
Protected Range Register Limit #3 0x0
Protected Range Register Base #4 0x0
Protected Range Register Limit #4 0x0
SPI Flash ID 1 C22017
SPI Flash ID 2 Unknown
BIOS boot State Post Boot
OEM ID 00000000-0000-0000-0000-000000000000
Capability Licensing Service Enabled
OEM Tag 0x00000000
Slot 1 Board Manufacturer 0x00000000
Slot 2 System Assembler 0x00000000
Slot 3 Reserved 0x00000000
M3 Autotest Disabled
C-link Status Disabled
Independent Firmware Recovery Disabled
EPID Group ID 0x2037Retrieving Variable “LSPCON Port Configuration”
LSPCON Ports NoneRetrieving Variable “eDP Port Configuration”
5K Ports None
OEM Public Key Hash FPF 5E74CE380DCA32BF2869A33E05EDBD4B365483B7061AA1604185E2AA04545A59Retrieving Variable “OEM Public Key Hash”
OEM Public Key Hash ME 5E74CE380DCA32BF2869A33E05EDBD4B365483B7061AA1604185E2AA04545A59
ACM SVN FPF 0x2
KM SVN FPF 0x2
BSMM SVN FPF 0x2
GuC Encryption Key FPF 0000000000000000000000000000000000000000000000000000000000000000Retrieving Variable “GuC Encryption Key”
GuC Encryption Key ME 0000000000000000000000000000000000000000000000000000000000000000FPF ME --- --Force Boot Guard ACM Disabled
Retrieving Variable “Force Boot Guard ACM Enabled”
Disabled
Protect BIOS Environment Enabled
Retrieving Variable “Protect BIOS Environment Enabled”
Enabled
CPU Debugging Disabled
Retrieving Variable “CPU Debugging”
Disabled
BSP Initialization Disabled
Retrieving Variable “BSP Initialization”
Disabled
Measured Boot Enabled
Retrieving Variable “Measured Boot Enabled”
Enabled
Verified Boot Enabled
Retrieving Variable “Verified Boot Enabled”
Enabled
Key Manifest ID 0x1
Retrieving Variable “Key Manifest ID”
0x1
Enforcement Policy 0x1
Retrieving Variable “Error Enforcement Policy”
0x1
PTT Enabled
Retrieving Variable “Intel(R) PTT Supported”
Enabled
PTT Lockout Override Counter 0x0
EK Revoke State Revoked
PTT RTC Clear Detection FPF 0x1
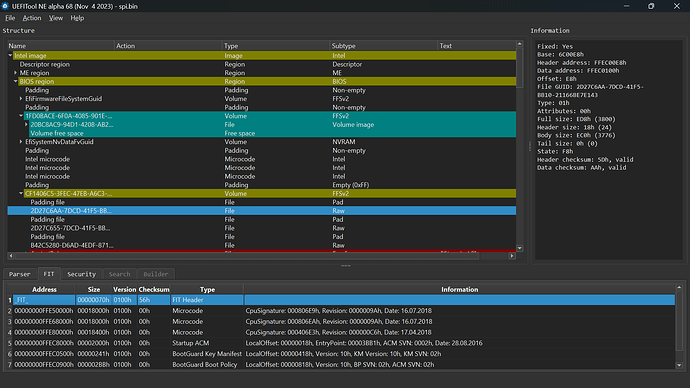
as far as i know about UEFITool NE colour mean:
- Yellow = ???, Cyan/Red = coverage by intel boot guard (?)
what should be concern:
- Verified and measured boot enabled at the PCH level = brick, no workaround to bypass this except by changing the PCH itself
- Microcode and FIT Table area is outside boot guard coverage = safe to perform modding (?)
what have i done:
- UEFITool 25 - 28 trigger checkProtectedRange in cyan area and break the FIT Table
- InsydeH2OEZE 100.00.03.11 trigger checkProtectedRange in cyan area, the FIT Table is not broken Replaced FIT file from the export module
- HxD load the dump bios, replaces the Microcode and fixing FIT Table, then save it. in Parser with UEFITool NE everything looks same as the dump file
Edit:
Both UEFITool and InsydeH2OEZE result in a brick, only the HxD method works.
Old:
Updated: