For those of us with older motherboards that have long since fallen out of manufacturer support - will the microcode updates meant to address the Meltdown/Spectre vulnerabilities be made available through UBU?
Only SoniX, the “maker” of the UBU tool may know the answer. So it would be better to ask this question within the “UBU Discussion” thread.
Furthermore you should consider, that the UBU tool is not able at all to update BIOS modules of non-UEFI BIOSes.
Will do - thanks. Fortunately it’s not quite that old, UEFI - but not updated by ASUS since 2014.
If Intel will publish updated CPU microcode for your CPU then it will be possible to use UBU because only thing to do will be to find/extract so called section file for the CPU. After extraction you can paste section file to certain UBU subfolder and it will show it in menu.
Also you can apply CPU microcode update with the help of VMware driver - here is page with instructions
http://forum.notebookreview.com/threads/…windows.787152/
Here is page with latest at the moment microcodes
https://downloadcenter.intel.com/downloa…e-Data-File?v=t
If Intel will publish new ones with patch for that security threats most probably this page will redirect you to the page with newest ones.
In the link below plutomaniac gave the microcode 23 whitch have the partially fix for spectre. (20-11-2017 microcode)
-[Discussion] UBU Tool related Questions, Reports and Suggestions (221)
I download it and i added to UBU tool 1.69.6 from sonix’s to recognise it.
IF sonix and the other UBU tool helpers have no problem i uploaded it here without the MMtool.
If anyone have a problem please delete or edit my post.
THIS IS SONIX’S tool and i didnt change anything except i added the microcode in the 1150 slot folder and i added one line in the 1150 slot script. —>(if /I %ec%==23 (set mc2=1150\cpu000306C3_plat32_ver00000023_date20-11-2017.bin) && exit /b)
-http://www.uploadmb.com/dw.php?id=1515173524
SOS:
The microcode haswell from intel 23 gives whea errors even at stock. Please wait a better microcode.
UPDATE 12/01/2018 (dd/mm/yyyy)
Withdrawn CPU Microcode Updates: Intel provides to Lenovo the CPU microcode updates required to address Variant 2, which Lenovo then incorporates into BIOS/UEFI firmware. Intel recently notified Lenovo of quality issues in two of these microcode updates, and concerns about one more. These are marked in the product tables with “Earlier update X withdrawn by Intel” and a footnote reference to one of the following:
1 – (Kaby Lake U/Y, U23e, H/S/X) Symptom: Intermittent system hang during system sleep (S3) cycling. If you have already applied the firmware update and experience hangs during sleep/wake, please flash back to the previous BIOS/UEFI level, or disable sleep (S3) mode on your system; and then apply the improved update when it becomes available. If you have not already applied the update, please wait until the improved firmware level is available.
2 – (Broadwell E) Symptom: Intermittent blue screen during system restart. If you have already applied the update, Intel suggests continuing to use the firmware level until an improved one is available. If you have not applied the update, please wait until the improved firmware level is available.
3 – (Broadwell E, H, U/Y; Haswell standard, Core Extreme, ULT) Symptom: Intel has received reports of unexpected page faults, which they are currently investigating. Out of an abundance of caution, Intel requested Lenovo to stop distributing this firmware.
-https://support.lenovo.com/gr/el/solutions/len-18282
@boombastik :
Hello boombastik and thanks a lot for info and link of “adapted” UBU Tool! 
I’ve modded latest BIOS released by ASRock for my Z97 OC Formula adding latest CPU MC Rev. 23 and now with latest cumulative patch released 03 january (KB4056892 - OS Build 16299.192) my system seems OK:
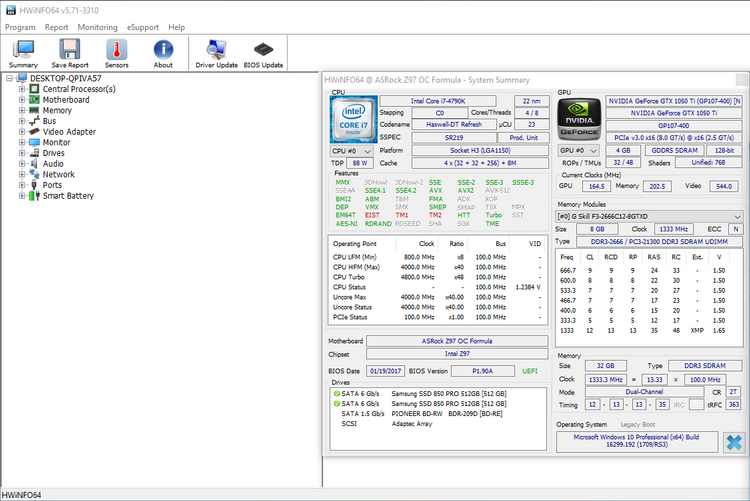

Cheers,
KK
EDIT by Fernando: Fully quoted post replaced by directly addressing and inserted too big picture devided and attached by using the Forum software (to save space, pictures can be enlarged by clicking onto them)
First of all the windows patch two attacks.
1)Rogue data cache load.
This patched software and are ok to go.
If your cpu is haswell and newer the windows activates also PCID perfomance optimization and the perfomance hit is smaller. This requires INVPCID (invalidate PCID) that is supported only from Haswell and up.
2)Branch target injection.
This need software and firmware update to work as intented.
The OS already patched this but to work ok you need and a microcode update.With microcode if u have lower cpu from skylake u will have bigger perfomance impact, because intel has optimized speculation with skylake and after.
Intel has released all these microcodes for this until now:
sig 0x000306c3, pf_mask 0x32, 2017-11-20, rev 0x0023, size 23552
sig 0x000306d4, pf_mask 0xc0, 2017-11-17, rev 0x0028, size 18432
sig 0x000306f2, pf_mask 0x6f, 2017-11-17, rev 0x003b, size 33792
sig 0x00040651, pf_mask 0x72, 2017-11-20, rev 0x0021, size 22528
sig 0x000406e3, pf_mask 0xc0, 2017-11-16, rev 0x00c2, size 99328
sig 0x000406f1, pf_mask 0xef, 2017-11-18, rev 0xb000025, size 27648
sig 0x00050654, pf_mask 0xb7, 2017-11-21, rev 0x200003a, size 27648
sig 0x000506c9, pf_mask 0x03, 2017-11-22, rev 0x002e, size 16384
sig 0x000806e9, pf_mask 0xc0, 2017-12-03, rev 0x007c, size 98304
sig 0x000906e9, pf_mask 0x2a, 2017-12-03, rev 0x007c, size 98304
The first one is for haswell and i tested it in two asrock z97 anniverssary motherboards and work ok. I put it in Sonix’s UBU tool if anyone want to try it.I have only tested it in asrock z97 motherboards with haswell refresh cpus. Also killkernel tried it in his asrock formula motherboard and it worked.
GeneO an intel overclocker found from tests that microcode 23 is slower from microcode 22, but i think if someone dont overclock it is the same.
-http://www.overclock.net/t/1645289/haswe…ity-differences
Thnks killkernel for testing and GeneO for his perfomance overview.
If you want to see if your hardware is patched from 2 attacks you can see more there:
-https://www.tenforums.com/windows-10-new…rabilities.html
@boombastik :
Since you obviously agreed to 100PIER’s proposal to create this new Subforum, I have moved your post about the CPU Microcode Update by using a customized UBU tool into it and gave this thread a hopefully meaningful title. You can change the title at every time yourself by editing the start post.
If you should not agree to the movement, please let me know it.
@killkernel :
I hope, that you agree as well.
Thnks Fernado. This customized UBU tool has the Haswell Microcode 23 nothing more or less.
Unfortunately no microcode update will fix that fiasco… only a software fix… and AMD isn’t in the clear either.
From what I’ve read so far on different mailing lists and articles, for some attack vectors a microcode update is even a prerequisite to be safe (but of course won’t fix it by itself, it needs further OS fixes and in some cases even new software). There is even hectic development in GCC and LLVM going on, Firefox and Chrome as well. The official statement from AMD implied that only one Spectre attack vector could be used (Bounds Check Bypass) which can be resolved by software / OS updates to be made available by system vendors and manufacturers. Hence I think they are far better off from this than Intel. Only a negligible performance impact is expected. Intel on the other hand is exposed on a wider front. And only new unreleased CPUs can solve it adequatly…
… which is not a concern for me as a home user, but I guess AMD will claim some market share in business and enterprise systems this year.
For more performance numbers, this report from the Red Hat Performance Engineering team describes their research into the performance impact of various microcode and kernel patch combinations in a server environment: https://access.redhat.com/articles/3307751
The microcode for haswell from INTEL have somthing faulty as all of us have internal erors.
MOre here:
-http://www.overclock.net/t/1645289/haswe…s#post_26534561
Please wait intel to respond.
In linux the microcode works ok, but wait for more test.
Thanks Fernando, you got a good thought and i agree with this decision. ![]()
Would you mind listing to steps you used to get from a microcode.dat file to something working in UBU? I’d like to do the same for my 3930k.
EDIT: I’ve gotten the microcode.dat file extracted. Now just to figure out which file is for my CPU and add it to UBU. (I think the ID is "000206D7", but I’m basing that purely off the microcode version reading as 710 in hwinfo64 and that being the only "710" that shows up in the version of UBU I used to update last time.
The file i used was already in .bin file ready for ubu.
I think I got past that part (extracted the microcode.dat and located the correct .bin file) - mind showing me how you added the file to UBU?
EDIT: I’m an idiot. UBU already has the option to select your own file.
With ubu u can select an external file .bin to load microcode, it is in the menu.
I know how to add it internally in ubu but because it is sonix’s tool maybe he dont want to tell. Sorry for that.
Just saw that as you posted it - thank you for that, I’m an idiot.
I extracted this microcode update for my i7 6700K (CPU-ID 506E3 - version C2) from the official UEFI bios update for PRIME-Z270-K-ASUS (version 1002) and successfully updated my Z170 Deluxe (version 3504) UEFI bios:
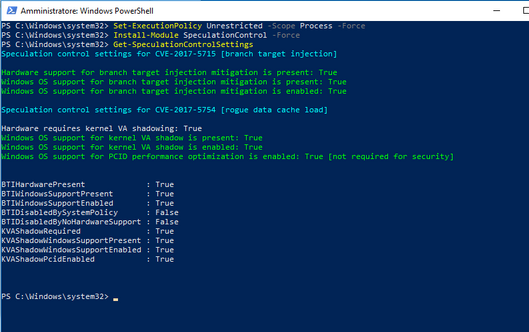
PS C:\WINDOWS\system32> Get-SpeculationControlSettings
Speculation control settings for CVE-2017-5715 [branch target injection]
Hardware support for branch target injection mitigation is present: True
Windows OS support for branch target injection mitigation is present: True
Windows OS support for branch target injection mitigation is enabled: True
Speculation control settings for CVE-2017-5754 [rogue data cache load]
Hardware requires kernel VA shadowing: True
Windows OS support for kernel VA shadow is present: True
Windows OS support for kernel VA shadow is enabled: True
Windows OS support for PCID optimization is enabled: True
BTIHardwarePresent : True
BTIWindowsSupportPresent : True
BTIWindowsSupportEnabled : True
BTIDisabledBySystemPolicy : False
BTIDisabledByNoHardwareSupport : False
KVAShadowRequired : True
KVAShadowWindowsSupportPresent : True
KVAShadowWindowsSupportEnabled : True
KVAShadowPcidEnabled : True