Was wondering if the chances of falling victim to a Spectre like attack is less if your running OSX?
Thanks
Don’t patch your private systems for Spectre/Meltdown/etc. with those stupid microcode updates and please also disable the OS Integration. It just doesn’t make any sense for a system that sits under your desk:
- Spectre/Meltdown/etc is over 1 year old and there is still no real world PoC available that works out of the box. Just use an up-to-date browser and your safe.
- It cripples the performance
- There are so many Privilege escalations for Windows/macOS/Linux. So why should anyone waste time and use a highly sophisticated “bug” when you could steal the Information with less effort?
Wonder if there is any performance data for what ever microcode updates that are out there? I would down grade my system if I knew which ones were best…
There are enough benchmarks out there. just use the latest non Spectre ucode and you are good. normally every new ucode update makes the pc a Little bit slower this is why overclockers mostly tend to strip their BIOS from ucodes or use a specific version
Oh god 906EA please be better than D6 crap.
Doubt the 906EA will improve anything, it’s been half a year of reduced performance and wrong ring multis for my 8700K. Last one that was decent was B4 I think.
When I mod a Z390 BIOS for performance, I use the AE and BE microcodes.
These were the last not to produced reduced performance.
But honestly it only really matters in benchmarks etc. It really matters little in day to day use and the new microcodes usually have security patches etc. that for some are more important.
The reduced performance is also seen under Windows with some software that I use
With Cascade Lake-X, I am using old microcode, the latest ones are too bad
More for overclocking than direct performance at the same freq. Thing barely overclocks anymore, D6 made me downgrade from 4.8core/4.7cache to -100mhz on each with MORE voltage than it needed for faster with prior mcodes… yet to try with DE that testing starts tonight… id drop all this crap long ago and stick with like 84 or something that was GOOD, but stupid Microsoft likes to control your PC and blame security paranoia, so they end up shoving the current mcodes onto it anyway. (its MY system, let ME choose what to have or not to have)
I already flashed the DE and was not expecting any improvement, even if there is a possibility to improve the performance Intel will not do it, otherwise no one will buy newer CPUs.
Any how I didn’t notice any improvement or slower performance CPUID is cpu906E9.
Any release notes?
A reminder for you who use windows if didn’t apply the necessary mitigations mentioned in this link https://support.microsoft.com/en-us/help…vulnerabilities
In my case I have to enable mitigations for CVE-2018-3639 (Speculative Store Bypass) by adding these registry keys
2
reg add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\Memory Management" /v FeatureSettingsOverride /t REG_DWORD /d 8 /f
reg add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\Memory Management" /v FeatureSettingsOverrideMask /t REG_DWORD /d 3 /f
Here are my Speculation Control Settings:
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
PS C:\Windows\system32> Get-SpeculationControlSettings
For more information about the output below, please refer to https://support.microsoft.com/help/4074629
Speculation control settings for CVE-2017-5715 [branch target injection]
Hardware support for branch target injection mitigation is present: True
Windows OS support for branch target injection mitigation is present: True
Windows OS support for branch target injection mitigation is enabled: True
Speculation control settings for CVE-2017-5754 [rogue data cache load]
Hardware requires kernel VA shadowing: True
Windows OS support for kernel VA shadow is present: True
Windows OS support for kernel VA shadow is enabled: True
Windows OS support for PCID performance optimization is enabled: True [not required for security]
Speculation control settings for CVE-2018-3639 [speculative store bypass]
Hardware is vulnerable to speculative store bypass: True
Hardware support for speculative store bypass disable is present: True
Windows OS support for speculative store bypass disable is present: True
Windows OS support for speculative store bypass disable is enabled system-wide: True
Speculation control settings for CVE-2018-3620 [L1 terminal fault]
Hardware is vulnerable to L1 terminal fault: True
Windows OS support for L1 terminal fault mitigation is present: True
Windows OS support for L1 terminal fault mitigation is enabled: True
Speculation control settings for MDS [microarchitectural data sampling]
Windows OS support for MDS mitigation is present: True
Hardware is vulnerable to MDS: True
Windows OS support for MDS mitigation is enabled: True
BTIHardwarePresent : True
BTIWindowsSupportPresent : True
BTIWindowsSupportEnabled : True
BTIDisabledBySystemPolicy : False
BTIDisabledByNoHardwareSupport : False
BTIKernelRetpolineEnabled : False
BTIKernelImportOptimizationEnabled : True
KVAShadowRequired : True
KVAShadowWindowsSupportPresent : True
KVAShadowWindowsSupportEnabled : True
KVAShadowPcidEnabled : True
SSBDWindowsSupportPresent : True
SSBDHardwareVulnerable : True
SSBDHardwarePresent : True
SSBDWindowsSupportEnabledSystemWide : True
L1TFHardwareVulnerable : True
L1TFWindowsSupportPresent : True
L1TFWindowsSupportEnabled : True
L1TFInvalidPteBit : 45
L1DFlushSupported : True
MDSWindowsSupportPresent : True
MDSHardwareVulnerable : True
MDSWindowsSupportEnabled : True
In this case you can control the loaded Microcode, just rename the file mcupdate_GenuineIntel.dll to mcupdate_GenuineIntel_back.dll or anything else, and only the Bios Microcode you flashed will be loaded to the system.
Running sfc /scannow will restore the file
I take it back, somehow I have noticed that my Laptop is much faster with the new Microcode 0xDE, especially when browsing.
I bet this new Microcode is still in beta, this is why it is so fast
The EA seems a bit faster and more stable, testing for hours now, I can say I notice a difference, maybe I am wrong, cause I don’t do benchmarks, but it looks faster and more stable so far.
but if you look back at #152 I enabled all the mitigations, cause Microsoft didn’t enable all of them.
Just to remind again,after the spectre and meltdown incidents in 2018, windows 10 has now safeguards in place in registry
Also Microsoft is releasing microcode updates regularly since then
Not to be least,almost all major manufacturers released either a Me firmware or bios update or even both after the incident (although most did not put them in product’s support page but in blogs/announcement pages,logic)
See Intel microcode updates for more information or Bleeping Computer report
InSpectre (Meltdown and Spectre vulnerability check tool,can enable/disable windows registry entries)
Intel CSME Version Detection Tool (The Intel Converged Security and Management Engine Version Detection Tool (Intel CSMEVDT) assists with detection of the security vulnerabilities described in recent Intel security advisories with installed management engine version in system))
Intel (Converged Security) Management Engine: Drivers, Firmware and Tools
All you need to do is clean install the latest windows 10build,and thats it.you dont need to go out hunting for these updates,windows will get them for you
Linux users also have a way to load them up at the start up
But for older cpu users,or older OS users there are two ways/methods,1-bios mod (better),2-vmware driver (tricky)
Using Windows 10 recommended.Even 10years+ old machines are capable of running Windows 10 without problems (WinMe-Xp era)
As mentioned above,it may be loaded onto the cpu at boot, by the bios, and replaced later in the boot stage by the OS as well
Microcode is akin to processor firmware.processors from Intel and AMD may need updates to their microcode to operate correctly.these updates fix bugs/errata that can cause anything from incorrect processing, to code and data corruption, system lockups, improvements (efficiency/speed)
As rule of thumb,keep your OS,apps,bios and drivers updated
the Microcode EA for my CPU could be by far the fastest I have ever test, now it is almost a day, very noticeable lower CPU usage when I compared to the tasks I did before, I really hope some one can test it and confirm
Little feedback, I was in a hurry so sorry for the bad feedback.
I did a quick benchmark using 3 Microcodes (84,DE and EA) and CPU-Z, I run twice ( only 0.1 difference) which means it was accurate, all the CVEs mitigations were enabled (in my case FeatureSettingsOverride=8 and FeatureSettingsOverrideMask = 3), same OS, just flashed the bios and run the benchmark immediately upon booting to Windows, no other apps were running.
The Microcode 84 I got 432 , When I run Get-SpeculationControlSettings some the CVEs mitigations were disabled (not supported by the CPU microcode), I forgot to copy the result cause I was in a hurry, I will not flash it again now.
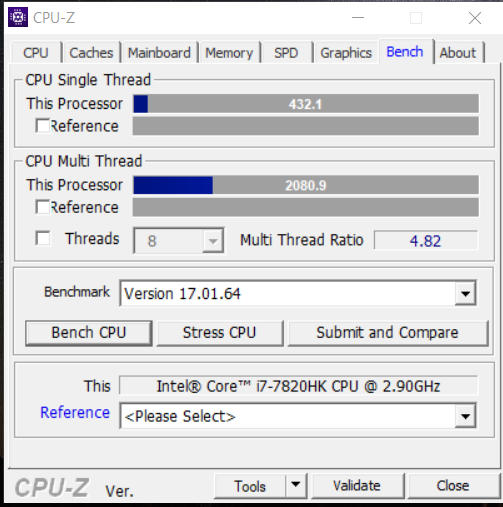
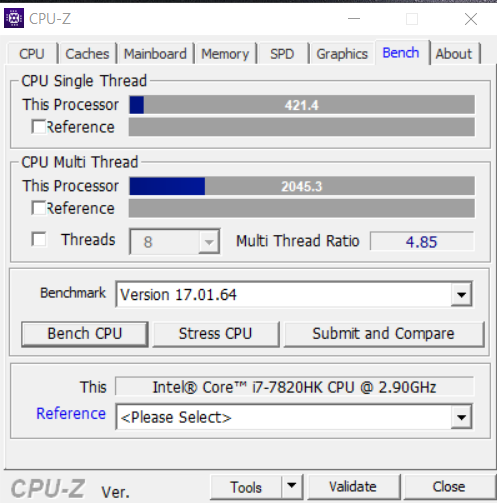
The Microcode DE I got 421 and all CVEs mitigations were enabled.
The Microcode EA I got 428 and all CVEs mitigations were enabled.
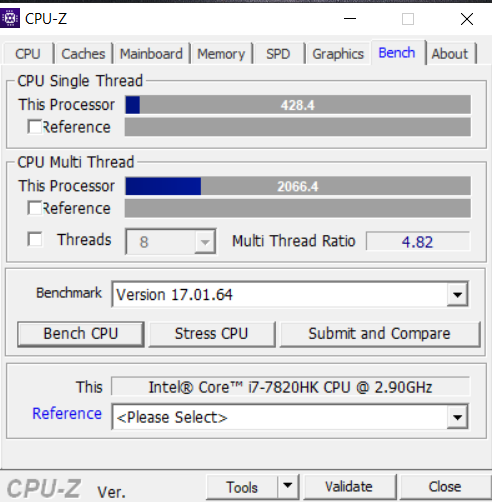
It is clear that the EA has better results than the DE and almost will catch the old 84 when some of the CVEs mitigations were disabled. Intel did something with the latest microcode, I hope they will keep it this fast.
I would prefer a slower CPU rather than the risk of being hacked. Not to mention the erratas in old microcode and the possibility of endless loops.