Finally getting an x250. I’m used to big clunky laptops so hoping it will be nice. Unfortunately this laptop has the down sides to most newer computers; limited expansion, intel ME and iffy construction.
While I wait for shipping, figured I would check out the bios situation. I found somebody’s full flash dump so I can see what I am getting: https://www.sendspace.com/file/4zb7zh
Not much on this laptop but I found a reddit tutorial to at least kill the screen white-list since I have a 1080p screen inbound: https://www.reddit.com/r/thinkpad/commen…reen_whitelist/
When I open the rom in UEFI tool, I can’t find the GUIDs or module names to match the X1C files: https://www.dropbox.com/sh/d2zqqte6pedpq…RAojAM1Nra?dl=0
I also read there is an advanced menu but cannot find any tutorials on how to modify the bios to enable it. Just people posting dumps and someone doing it for them… that’s no fun. Anyone have any more info?
As a bonus, me_cleaner does work with this bios and it will remove modules. It is probably safer to use the soft disable so you don’t lose things like ethernet. That’s the route I will be taking.
update: I found the GUIDs in volume image section… search in UEFI tool is broken.
@NSAfarm - Sorry, read along until you mentioned X1C files, what is that about and what/why are you linking something there?
Search in UEFITool works fine, at least in version 25/26 and 51-55 NE Alpha, I use those all day long, searching with all of them (Hex, GUID and text search, works fine, in all those versions)
Please link me to the latest stock BIOS for this system, from Lenovo, the download page not the direct link. Then I will check BIOS for you and let you know about unlocking, if it’s easy, if it’s hard, how to do etc.
Don’t disable ME On a laptop, often this = fan at high speed always, can mess up CPU functions (multi, voltages, XMP) and mess up memory speed/timings sometimes too.
It’s up to you though, it’s your system. Yes, I would not use ME_Cleaner, do it properly via Intel FITc and disable the HAP Bit (reserved)
Me cleaner does the hap bit. I have a similar Intel SFF system I already did this to. Removing modules = no ethernet/temp monitoring while setting the bit just disabled it. I should set the flash unlocked too but no idea how that will play with intel secureboot, etc. That part is easy to experiment on as long as I can do it in-circuit this time and not just removing the chip.
bios: https://pcsupport.lenovo.com/us/en/produ…nloads/ds102288
Btw, those modules are used to cancel the LCD screen whitelist because I am upgrading the screen. I had the choice of buying X230 with the ability to use coreboot or X250 with cheap 1080P ![]()
Also… I found insyde EZE which would ungray and change the logo which is some other stuff I like to do to my machines but none of the bios open with it. Neither the bin, nor the FL1 and FL2 from the stock bios. Phoenixtool does break it out so maybe I could just hex-splice a logo inside. Can you recommend other tools?
Got the laptop… I installed the screen and the only thing I notice is that the brightness goes up to full when booting up. Supposedly I its not adjustable in windows but linux is taking care of it. I have all AMT features on, this thing came from a corporate environment.
When I get set up I will try to read the chip powered from wake on lan since some guy on reddit bricked his with the raspi 3.3v. Are the dumps even rebuild-able cross machine? Is there a point to posting it? I have an old revision of the bios but unfortunately boot guard is enabled ![]()
Yes, but ideal way to do the HAP Bit edit is via Intel FITc program, if that is all you want to do. When you mention “SecureBoot” do you mean just that, or “BIOS Guard”?
If secureboot, editing BIOS or FD means nothing, if you mean boot guard is properly enabled on this system, then you can’t edit any parts of the BIOS shown in cyan/red with UEFITool NE Alpha version as those would be covered by Boot Guard.
To check if that is enabled, you need ME FW working so you can do MEInfoWin.exe -verbose
Check the end of that report, if you see Measured or Verified enabeld on the left/FPF side, then it’s enabled and nothing you can do to disable that except replace the PCH.
If enabled, above mentioned things apply to what you can/can’t edit or bricked BIOS
Still, X1C files tell me nothing, I haven’t downloaded that package yet though (can’t download from dropbox today) But to remove a whitelist in BIOS you do not need other files, unless someone pre-edited extracted modules from the exact BIOS version you are using now.
Otherwise you extract the module yourself in BIOS and apply bypass edit.
So, whitelist BIOS for screen not needed, good. the brightness may be adjusted in hidden BIOS options or vBIOS/GOP modules of the BIOS itself.
BIOS from one system to another would be fine, but you will loose serial/LAN MAC ID etc (well you will gain that systems info instead 
If bootguard is enabled and done properly at chipset, nothing you can do, except edits to BIOS areas that are not covered by boot guard (cyan/red in UEFITool NE Alpha)
Boot guard key in BIOS would be same across all these same model, actual key that may vary is stored in the FPF of chipset.
I checked, much of the BIOS is OK to edit even with boot guard enabled and properly setup. This especially applies to stuff we normally would modify for a BIOS mod, update microcodes, unlock menus etc.
Sorry, I am not familiar with editing Phoenix to enable BIOS menus etc, so I can’t help with this one in that area
That’s good to know. I will check for red stuff and look up phoenix menus. Everything said it was insyde, even phoenixtool and then I saw phoenix when I updated to the newest version. It is all properly enabled as I used the tool from coreboot. The ME functions and remote functions stay active even when I turned it off in the bios. It will definitely need that hap set.
--------------------------
Got some new info, hopefully it will work. I found a patch for wifi whitelist and advanced menu for T450s… It patches 2 modules. SystemFormBrowserCore and LenovoWmaPolicyDxe. Luckily it came with a before/after bios.
Looking at X250 SystemFormBrowser it is a bit different in other parts, however it is exactly the same where the file was patched. I will check the WMA module next but I believe it is related to wifi only so probably no need.
0x428 -0x437 (module, body only)
T450s Mod
77 8B 1D 82 6D 24 96 4E 8E 10 34 67 D5 6A B1 BA
T450s Original
04 32 0B 48 3C C2 E1 4A BB 16 A7 3F AD DA 47 5F
X250 Original
04 32 0B 48 3C C2 E1 4A BB 16 A7 3F AD DA 47 5F
As you can see the values are the same so I should be able to hex edit my own module and get the advanced menu. I will dump full modules as well as the WMA and make sure no signatures/checksums were altered as well.
ETA: No checksum/signatures were patched. WMA policy has patches that jump around. I will look in IDA to see if they are changed instructions.
--------------------------------
So some good news and some bad news.
Removing flash protection works, hap bit works and ME gets stuck in initializing forever. Editing any modules = no boot and 5 beeps. Cross flashing bios from another person = brick, even if you flash back your old bios and verify.
-----
Unbricked by pulling the CMOS battery and letting it sit! But I’m back to square 1 on modding besides the low hanging fruit. Even stranger, after pulling the CMOS battery, only the time was lost, not a single other setting.
FullModules.zip.txt (80.2 KB)
It could be a mix of Phoenix/Insyde, not sure, just not something I can play with. Maybe if you gave me a dump would make it easier, but can’t be sure.
Possibly that would mean same edit, but who knows! You don’t know what that code bit is actually doing, nor what the edit does differently.
Get UEFITool NE Alpha and check what I mentioned, only certain areas can be edited or instant brick due to boot guard. You can check to see if that’s enabled at the chipset burned in level or not via >> MEInfoWin.exe -verbose
And then check the end of the report, if you see Measured or Verified enabled on the left/FPF side, then nothing you can do except don’t edit anything covered by boot guard colors (red or cyan) in UEFITool NE Alpha.
If you do not see either of those enabled at the left/FPF side, but only BIOS side, then it can be easily disabled in the ME FW before you disable that.
To run that report, you will need ME FW enabled of course.
I did look with the new UEFI tool and I edited modules that were only white. Those guys on reddit had success except it seems now security beeps = no boot at all.
Uploaded my dump to http://ge.tt/8rIVcqy2 and http://s000.tinyupload.com/index.php?fil…688023902899933
They has success recently, I mean on the BIOS you are using now, or on older BIOS? Give me the reddit link, maybe I can see something interesting or useful.
Enable ME FW, and check what I mentioned above >> MEInfowin.exe -verbose
That way we at least know what we are dealing with here.
Your mod BIOS = beeps/brick could just be bad mod?
I found your mod bytes here in discussion - FYI
https://www.bios-mods.com/forum/archive/…ad-16101-9.html
Looks like you probably need to use the correct variables for your BIOS not those exact ones, for whatever menu you want to replace (before) with the correct menu you want (advanced etc) since the before there is different than yours.
I would read forward and backward in that thread, it may help. See also - https://www.bios-mods.com/forum/archive/…read-27352.html
I thought it could be bad mod but every time I change anything I get 5 beeps and no post. I even did it replace as body in UEFI tool so that the header checksums don’t change and still it gives 5 beeps and no boot. I set the security chip to disable and cleared it. Its like they run a check on the whole image and I don’t see public information on any thinkpad x250 modification. I’m going to look for a way to extract the IFR and make sure that is the right menu being replaced but it doesn’t look hopeful.
It may be a bad mod since I can’t find “77 8B 1D 82 6D 24 96 4E 8E 10 34 67 D5 6A B1 BA” hex in bios but no idea if it will boot with the good mod either. None of that should cause a problem until I go into the bios and open the actual menu.
---------------
I did some searching. I found File_DXE_driver_CFEF94C4-4167-466A-8893-8779459DFA86_PlatformHiiAdvancedDxe and it matches the hex. So this mod should work. I think there is more than one place where the original replaced hex string is but I doubt it has to be changed there too if this mod worked on T450. It opens up with universal IFR extractor and is quite the impressive menu. I think the problem lies with whatever security lenovo has implemented to stop bios tampering. I was stupid to upgrade to the latest bios as I could have probably done these mods no problem.
I could make a single byte or two change as a test edit, then you see if that also gets brick/5 beeps? Here is the setup module IFR, and yes you have the correct module - http://s000.tinyupload.com/index.php?fil…637834611067246
"It matches in hex" << What matches what?? I mean, what are you comparing there, to what? That is the module that controls the BIOS menu, IFR above
Here, please test, brick/5 beep or not? Only four bytes edited here. If this boots, let me know, I can do ahead and update microcodes for you too if you want, while I’m looking at this.
http://s000.tinyupload.com/index.php?fil…927362106776252
Also, you still have yet to show me MEInfoWin -verbose report. Would be nice to know if that is enabled or not. ME FW is set to >> Boot Guard Profile 4 - FVE << Which = VB (verified Boot), Immediate Shutdown on violation
I guess from this we can surmise Verified Boot will be enabled and burned to the FPF at chipset, but not Measured Boot, I see it’s disabled on the ME FW side but still could be enabled by itself at chipset level. VB is for sure, probably on both ends
Here, this PDF may help you too - http://s000.tinyupload.com/index.php?fil…495734374194576
On the 5 beeps, maybe RSA signed BIOS, see link at post #2 - Insyde H2O bios unlocking/flashing
That hack works by replacing the pointer from one menu page to another. It matches as in I find both pointer addresses in the right spots just like on the working T450 bios.
I haven’t run ME info because I don’t run windows. I used intelmetool and pretty much everything was enabled. I can try booting it off a flash drive but I will have to flash original bios with ME enabled. No settings are available that I didn’t turn off before pulling the dump at least just using the bios side. Me was unprovisioned and set disabled.
I tried your bios and got the 5 beeps but I had boot. I also tried the guide with modded modules and didn’t get 5 beeps but just a few lights flash and it doesn’t boot. There is another volume I can’t place in uefitool and only one key.
volume:
BTW, here is ME info
https://pastebin.com/62L2U09L
and verbose:
https://pastebin.com/y3UTbK0L
-----
I can confirm that modifying the key at all produces no boot/no beeps. Maybe that is in the bootguard protected section or everything has to be resigned?
Yes, I figured that out about the patch method, when I linked you to that info and two pages the other day.
You can do the MEINFO thing from DOS then, or UEFI Shell too I think, maybe even Linux files in there I can’t remember for your version. Check the ME System tools package for your version and you should find other than Windows files for that, but you do have to have working ME FW in there to do the report.
I see you got it, thanks. As suspected, Verified boot is burned into the chipset FPF, so nothing you can do in the BIOS regions covered by Boot Guard unless chipset is replaced.
So, with my BIOS edit, you get 5 beeps, but it boots? What does that mean, can you get to DOS or BIOS after that? If yes, what does the 5 beeps then mean? I thought that meant No and it was bricked
Sorry, I don’t understand what you are asking about when you say >> another volume I can’t place in uefitool and only one key. << And those images
Your first image looks like TPM key/stuff, should only affect TPM related things.
The 5 beeps is TPM failed the signature. But your patch works enough to get into bios and dos/etc. When I try to change an entire module even not in red I get 5 beeps and no video/post, just shut down.
The encryption guide you linked has 1 volume (per uefitool) that is signed. In my bios the bootguard enforced volumes + TPM and the not enforced ones are all signed with the same key. There is no other key by itself like he had. So if I edit it I get immediate shutdown, no beeps.
I guess its possible to test this further by replacing the microcode and seeing if it will boot to bios with or without beeps. Phoenix guide that was linked is for much older bios without this stuff. PBE does not open these images.
Why is TPM invoked here, are you using TPM? Can you remove the TPM device, or disable it in BIOS? So my edit is OK then, if you can boot to DOS or enter BIOS. Maybe your edit is breaking the BIOS, since mine does not do that but yours does?
Immediate shutdown would happen no matter what with anything in the boot guard covered area, that is unrelated to the RSA signed thing I linked above.
I can update microcodes for you if you want, or you got it?
* Edit - for your perusal, someone just linked me to these also, for bypassing RSA checks (not boot guard) - these are from @CodeRush from this forum - Just done reading, second link there seems to be the new/current method, easily digestible too (Thanks CodeRush!)
[REQUEST] Unlocking “Advanced Menu” BIOS -Notebook HP model_15-bw032wm(AMD processor)
TPM I set to off before the dump, I hate TPM but really turning it off seems impossible. Just like ME is "off" but runs until you set the HAP bit. I know you say the RSA check is different but if you look at the dump and the guide you will see what I mean about there being only one key and it signs the TPM too. In that guide only 1 volume image is signed
Here is what is really signed:
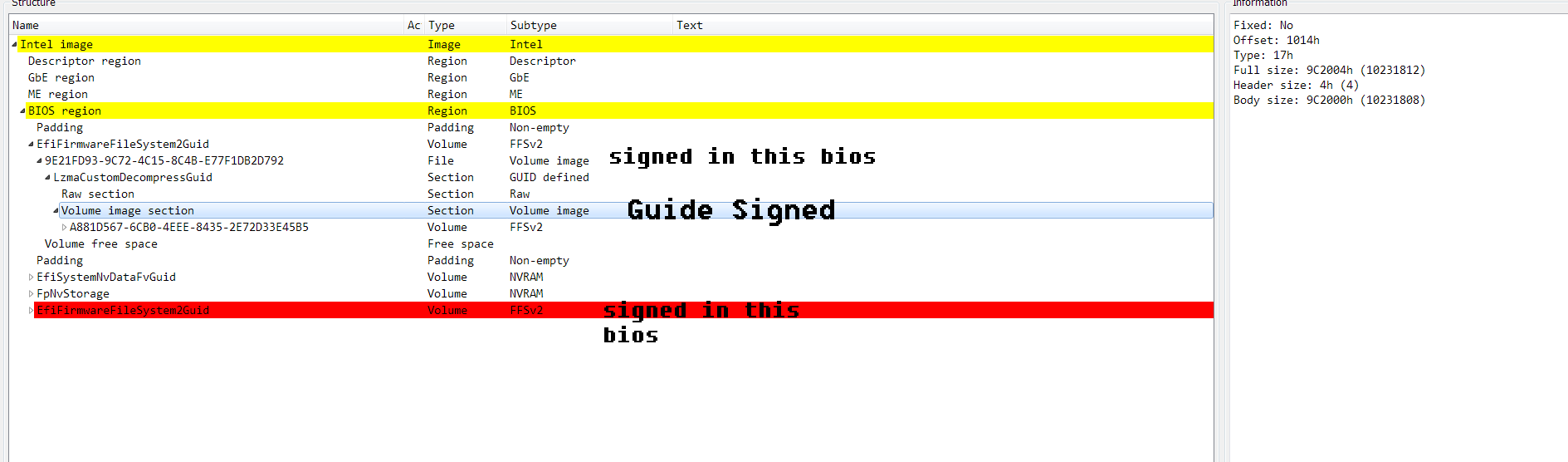
And both use same key… because only one key in the file besides bootguard key.
Anyways, I thought maybe my patch is bad but the screen whitelist patch was reported successful by other X250/T450 users on reddit with much less bios editing experience, some got the TPM beeps but that’s it. You have more experience than me so if you don’t mind update the microcode and then I can do the same and I’ll compare the 2 files to make sure my process isn’t wrong.
I’ll then test and see if it boots or not. I’ll try coderush’s guide as well when I get done with work and see where that takes me.
I finally got the module open in ida and in my patch the code makes sense:
2
3
4
5
6
7
8
9
10
11
12
13
else
{
v5 = 0i64;
v1 = 0;
while ( 1 )
{
result = dword_140(&MenuPTr_380[2 * v1], 0i64, &v5);
v2 = result < 0;
if ( !result )
break;
if ( ++v1 >= 4 )
goto LABEL_9;
}
asm:
.text:0000000000001BF8 lea rax, MenuPTr_380
.text:0000000000001BFF mov ecx, ebx
.text:0000000000001C01 lea r8, [rsp+58h+arg_0]
.text:0000000000001C06 shl rcx, 4
.text:0000000000001C0A xor edx, edx
.text:0000000000001C0C add rcx, rax
.text:0000000000001C0F mov rax, cs:qword_11358
.text:0000000000001C16 call qword ptr [rax+140h]
.text:0000000000001C1C test rax, rax
.text:0000000000001C1F jz short loc_1C2B
.text:0000000000001C21 inc ebx
.text:0000000000001C23 cmp ebx, 4
.text:0000000000001C26 jb short loc_1BF8
.text:0000000000001C28
Address of 1 page is changed in that table, so date+time page is replaced with "advanced".
---
ETA: This is the source of the patch as it was done: https://translate.googleusercontent.com/...UquJd1GGODsBhng
Also cannot find any extra key like he had in his tutorial. Lenovo did not use that method. But results seem the same. Replace module and get no boot.
---
I did more testing:
1. Non protected modules from another x250 with different bios version = beeps and no boot/screen (just like patching)
2. Editing Volume_NVRAM_EfiSystemNvDataFvGuid.vol, no beeps and all good. I changed the logo and I notice the microcode lives in there.
3. Someone elses NVRAM file, trips bootguard
4. Removing non-secure modules doesn't work either.
I looked in the file posted and I see more than 4 byes changed? What did you change in that and did it rebuild?
Sorry, I can’t understand any of what you posted?? And, when you said Date+Time replaced with Advanced, I was really lost, have no clue what you are talking about, if that’s referring to a BIOS menu mod, sounds like it’s all wrong.
On your # items
1. You can’t mix and match modules from one BIOS version to another, sounds like you did, so no boot expected there.
3. If you edit NVRAM and all OK, but insert some other NVRAM see #1 above.
4. Lost me again, too non-specific
If you want me to update microcodes, link me to the exact file you want edited and I will update.
I only changed 4 bytes in the BIOS I sent you, when I mentioned that, so however you are comparing is the issue probably. BIOS modules are compressed, so when you change some bytes, it looks like way more than your actual changes, especially once you insert the module and recompile the BIOS.
I edited 4 bytes at GUID CFEF94C4-4167-466A-8893-8779459DFA86 (PE32 body) Extract before and after you will see the four bytes I edited. Below is the before/after file if you are still not sure
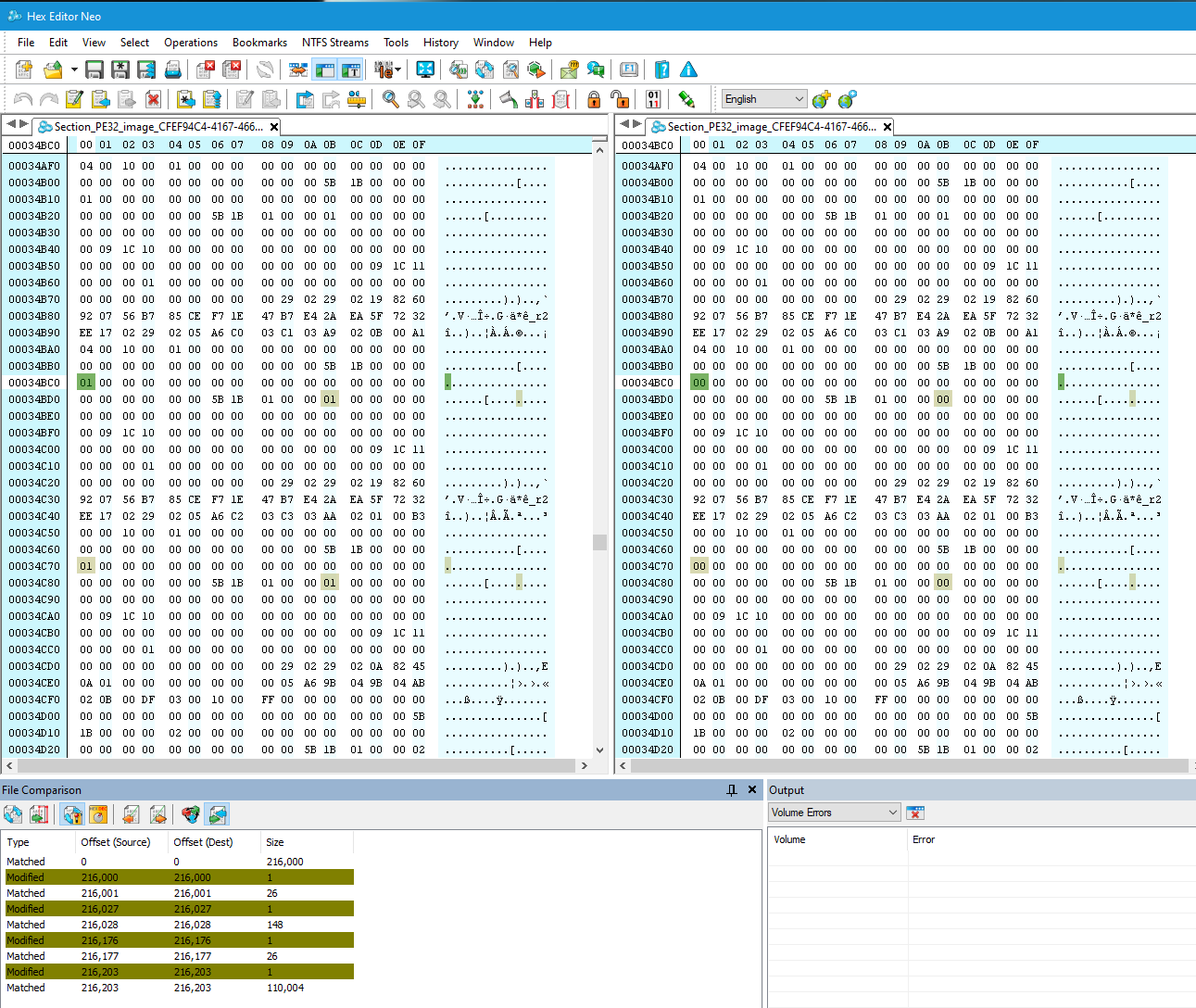
I changed default profile (x2) value for BIOS and SMI Lock - new.php?thread=5423&forum=16&reply=1&replyid=94902
Also, I don’t know assembly or coding like that, so I can’t look at code like you display and make any sense of it. I know it may seem like I maybe know a lot about that, but I really don’t
I know a little in IDA, how to bypass things in various ways, change jumps in various ways etc, and I can follow along and do an edit in assembly if there is given examples that match or at least resemble the code of file I’m looking into.
But to look at it like you presented it’s gibberish to me - I never use that view in IDA 
For #4 I removed MeInfo module which bios complains about since ME is disabled. Computer doesn’t boot same way as patching any other module.
#1 Other people have success and me previously using other versions/modules inside as single modules. I.e. changing the SATA module to raid, etc. Not in this version. Previously lots of success on reddit on T450, X250 and others. I took the entire volume of non protected modules so all should work together, this bios version ran on this machine previously.
For the patch, coderush actually wrote a guide on it exactly. https://translate.googleusercontent.com/…UquJd1GGODsBhng
Bios has 4 or 5 main pages. Info, Date/Time, Security, etc. As in the guide from coderush, you point one of those pages at advanced menu instead of what it was originally. Writing the code I’m just showing that I didn’t modify some random instruction and break the module. It still disassembles and decompiles correctly.
In Ida I always use decompiled code and assembly view and then I change instructions in hex edit.Then see again if they are correct in those 2 views. I’m not that great either but patched a few different styles of firmware before.
I’m beginning to think there is something checking integrity like in the other 2 coderush guides but I’m not smart enough to figure out what it is and afraid that its in the RSA signed section. I posted on bios mods, the dude took the bin and said it was complicated then never came back.
I assume if you remove ME region = no boot, sorry, not sure what MEInfo module is, never heard of that. If you want to disable ME FW set the reserved bit to Yes (HAP bit, you know)
I patched BIOS for you and it booted, so it’s not just not booting if you "patch any other module"
SATA module, if present as that, can be updated, RAID Can be updated etc, but you can’t swap one for the other, and you have to use ones compatible with your chipset and do the update properly.
Sorry, I still have no idea about the coding you have above. But yes, I get what you mean about swapping main menu 1 for the other. Sorry, I wish I knew more about Phoenix BIOS
I can update microcodes for you if you want, that should be OK since the other test edit I did for you was OK.
Good experiment would be to find a newer sata module and try to change it. I will have to do some research. I actually did swap sata module for raid module in my dell and old style phoenix bios.
This is what I removed and it didn’t boot, even though hap bit is disabled and the bios complains that it cannot load this module anymore.
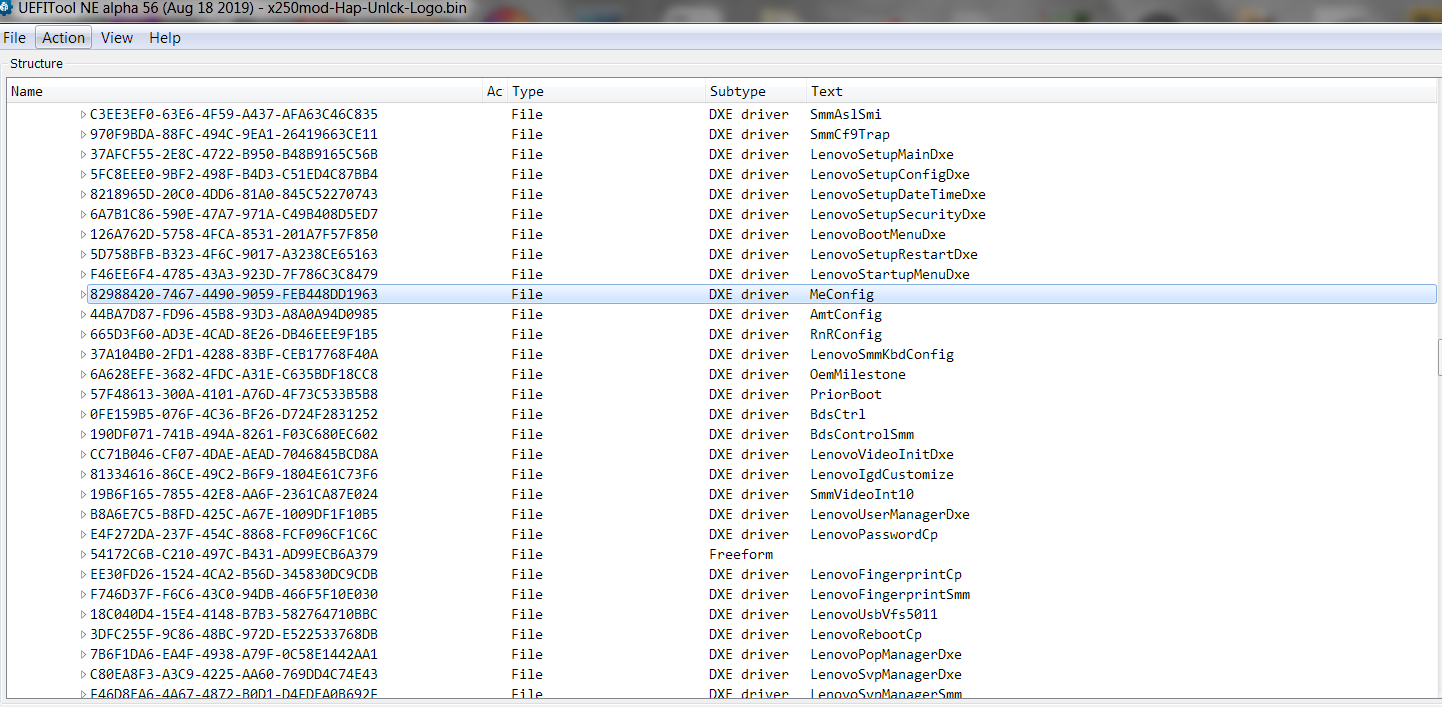
When you patch it was with UEFI tool, right? Just making sure that’s not the problem.
This is MC:
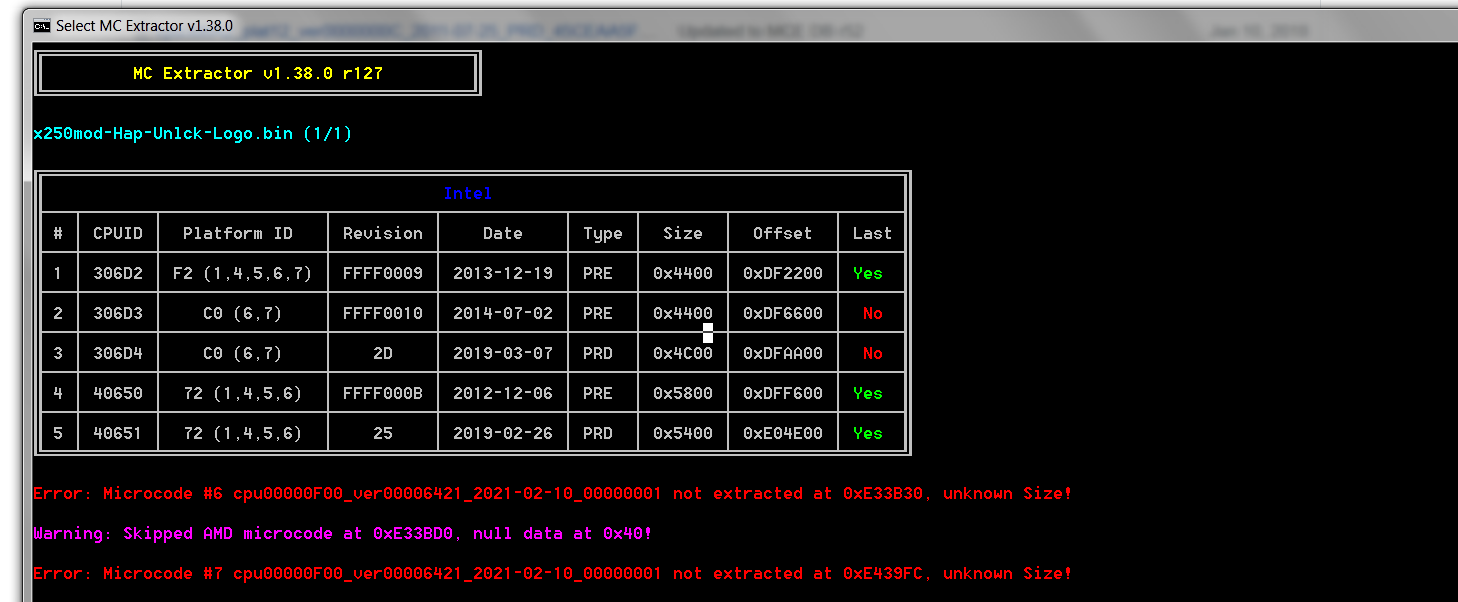
I found 1 update for D4 and its easy to change inside the NV.
Only replacement modules I see posted are intelgopdriver and maybe the ethernet. Gop driver listed is older or at least smaller but might be worth trying just to see if it can boot.