All currently known Intel, AMD and VIA CPU microcodes have been made available by plutomaniac (AKA platomav on Github) for the Win-RAID community!
Note that this thread will be updated from Plutomaniac’s Github when I have time, if you want to test the latest microcode and it isn’t here then you can still download the latest file(s) from Github.
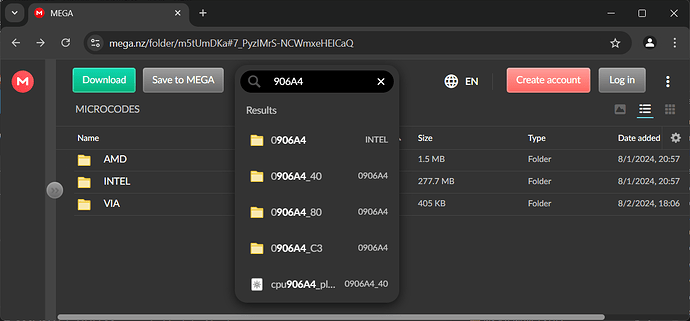
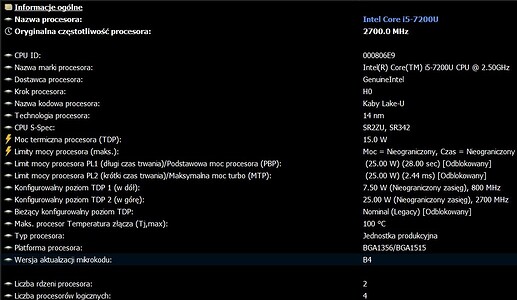
The Microcodes have been sorted into folders that are labeled by CPUID.
To find your specific CPU folder use the search box at the top of the Mega folder to enter your CPUID e.g.
Intel has subfolders for each Platform ID (i.e. 0906A4_40, 0906A4_80, 0906A4_C3), please make sure to use the same Platform ID for compatibility when swapping/updating microcodes in your BIOS.
In some cases you can use a higher Platform ID but this is not guaranteed!
WARNING: Replacing a working microcode + Platform ID with a non-compatible Platform ID can result in a POST (Power On Self Test) failure which may require BIOS recovery with a hardware programmer! Be careful!
Here is some helpful information taken directly from plutomaniac’s Github readme to help understand Platform ID on Intel systems:
- Platform (Intel only)
- Provides information about the supported sockets (LGA775, LGA1366 etc) or platform types (Desktop, Mobile etc) depending on CPU generation.
- Up to 8 supported Platforms, encoded in Little Endian binary form (bitfield).
- Examples: 0xC0 = 0b11000000 = 6,7 ; 0x03 = 0b00000011 = 0,1 ; 0x76 = 0b01110110 = 1,2,4,5,6.
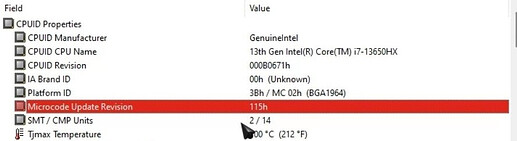
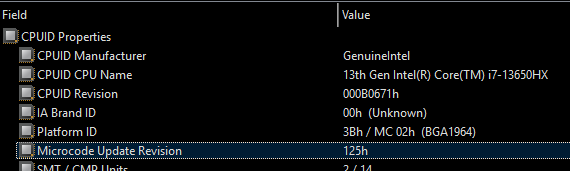
- When updating to another microcode, ensure that at least the same or more Platforms are supported. You can use MC Extractor to check each Intel microcode’s supported Platforms.
- Example: Changing from 0x5C (2,3,4,6) to 0x5D (0,2,3,4,6) is okay, due to the additionally included platform “0”.
- To not risk losing socket/platform support, avoid reducing the supported platforms.
- Example: Changing from 0x5C (2,3,4,6) to 0x58 (3,4,6) might not be okay due to the missing platform “2”.
- If you cannot find the exact CPUID & Platform combo at the repository, as the one you currently have, it might be because there is another microcode with the same CPUID but with more supported Platforms.
- Example: Microcodes with CPUID 0x906E9 & Platform 0x22 (1,5) were superseded by CPUID 0x906E9 & Platform 0x2A (1,3,5) in order to add LGA2066 socket/HEDT platform type support at KBL(-X).
- Null Platform (0x00) is implicitly the same as single Platform (0x01), since at least one platform must be supported.
- Example: At CPUID 0x633, Platform 0x00 = 0x01 = 0