You gotta be kidding me … the option "Legacy port redirection" is the only one that I left disabled in MEBx facepalm. It was there!
// how nice of Intel for not allowing to enable "legacy port redirection" from the standard AMT web interface
By default port 5900 it is disabled because if used by AMT will disable access to sw that use that port.
have a look at some doc:
https://software.intel.com/sites/managea…bilityports.htm
https://software.intel.com/sites/managea…ithport5900.htm
https://software.intel.com/en-us/blogs/2…eshooting-tips/
http://www.thomas-krenn.com/en/wiki/Inte…ment_Technology
https://www.scivision.co/intel-amt-vpro-…nc-viewer-plus/
I just got MeshCommander 0.5.6 up and running. See attached :). I enabled those two boxes and now I’m a happy bunny. I didn’t find an option in MeshCommander to enable the legacy redirection ports (5900) for standard VNC clients - should there be one? t would allow me to connect more easily from my mac and linux boxes.
Many, many thanks to both of you!
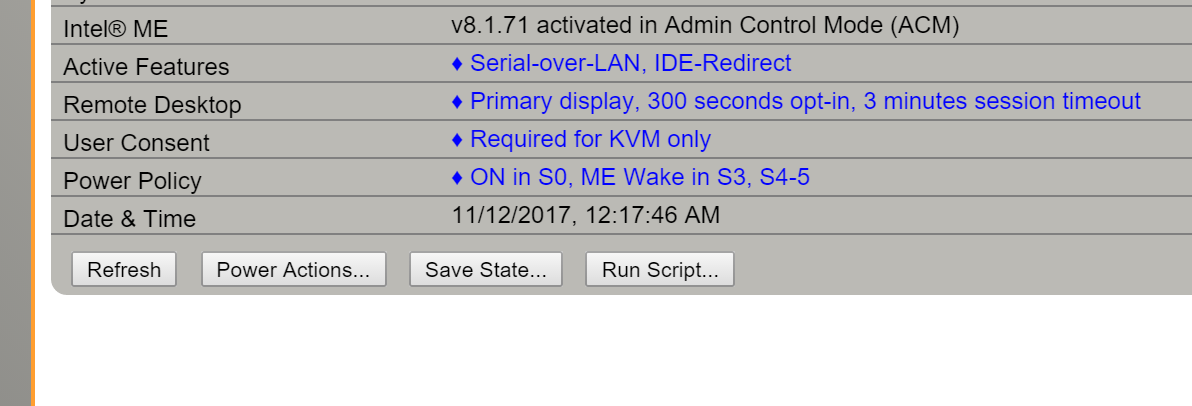
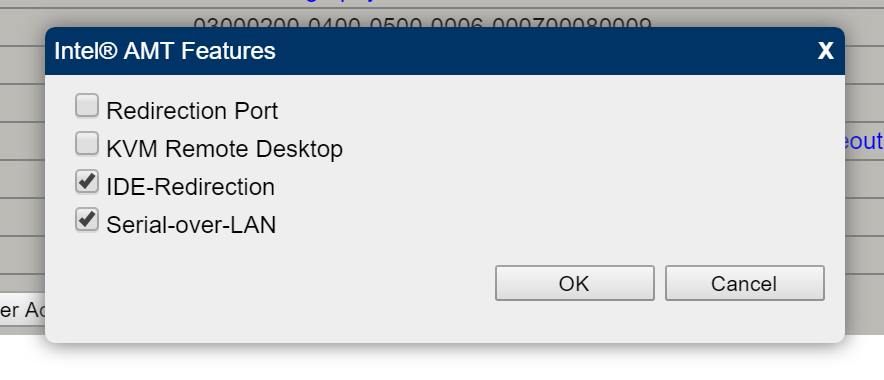
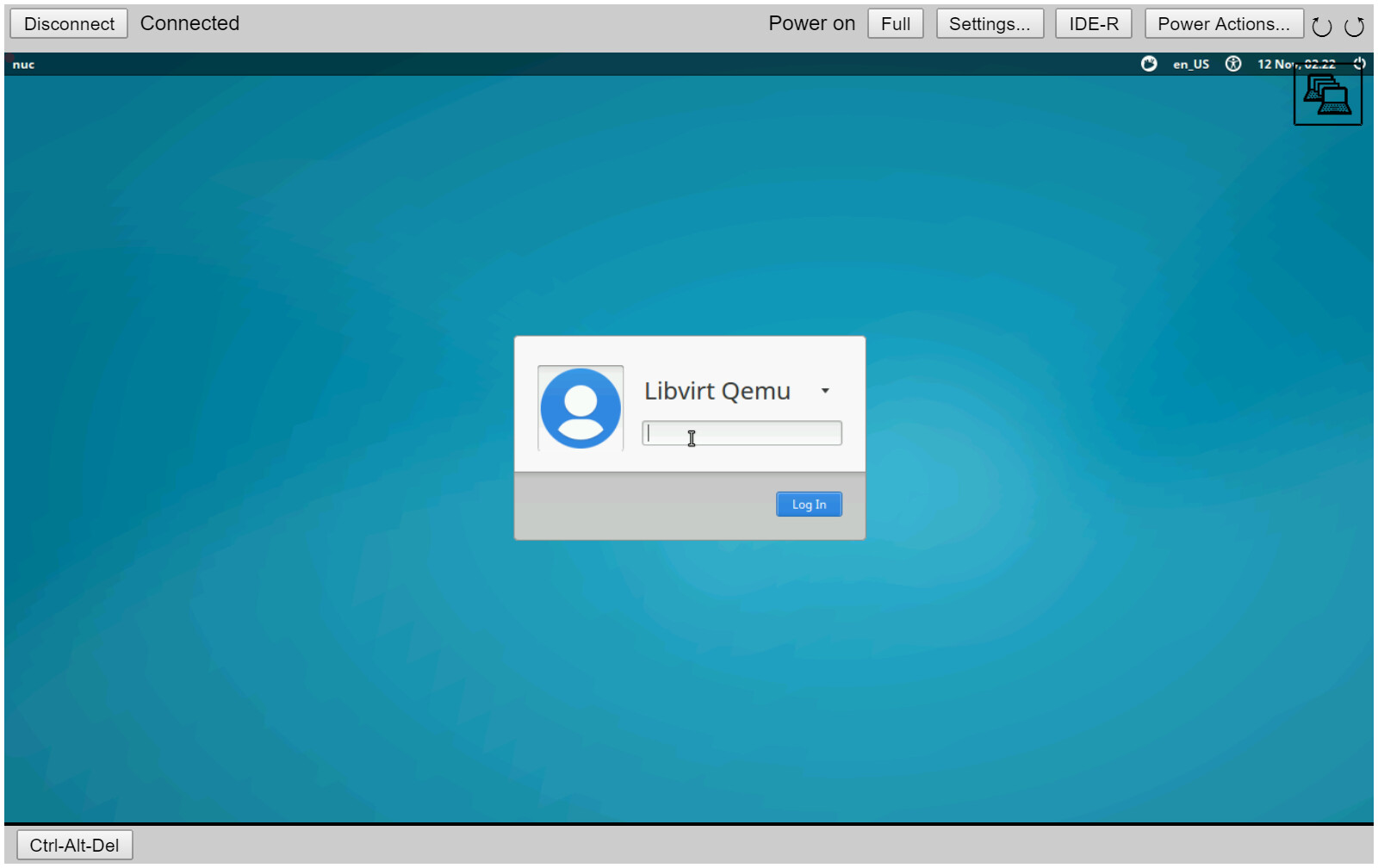
Mesh Commander seem to not have all legacy options.
I think you have to try Manageability Commander Tool or from Intel AMT Software Development SDK - KVM Console; unfortunately you will need a windows OS.
https://www.thomas-krenn.com/en/wiki/Int…ment_Technology
https://www.scivision.co/intel-amt-vpro-…nc-viewer-plus/
Is there any option to enable RAID, as I know it was also disabled by dell . Thanks.
Wow, I’ve read through this whole thread and tried all the of the posted mods and it still doesn’t seem to want to enable AMT on my dell Optiplex 7010 i5. My cover says ME LOCKOUT, not just ME disabled. Is it possible that there is no way to defeat this? I have attached the output from fptw64. Appreciate any help.
My dump is here: https://drive.google.com/open?id=1MzK48W…9VNjy3Fl_gnxs1s
@ Frankinator:
What CPU do you have? That dump already has AMT enabled, did you save it after flashing modded ME regions from previous users with the same system? If yes, do you have the original dump before any flashes? Also, do you use the motherboard jumper or a programmer?
@plutomaniac
Sorry for the lack of details! I have an i5 3470S. I did not take any dumps before attempting the flashes so what you’re seeing is, in fact, after my attempts. I followed instructions given to previous users who have the same model Dell. I’ve tried flashing from DOS with fpt and within windows with fptw64. I am using the jumper on the motherboard. I’m at Dell bios A25, though I’ve also tried downgrading to previous version to see if it helps. Also the same steps, flash with jumper, shutdown, put jumper back, issue -greset command… but nothing seems to work.
The CPU is vPro capable, so is the chipset (Q77 - right?) and the modded ME firmware. The only remaining place is the BIOS which is were I assume Dell has placed the restriction. What you can try is replacing it with the stock one provided at their download site once the executable is unpacked. Note that you’ll loose some info such as Serial Number, Service Tag or similar. What you can do though, if you want to test it and verify that the restriction is there, is to backup your current BIOS (“fptw -bios -d bios.bin”) or better yet the entire SPI chip (“fptw -d spi.bin”) for safekeeping and then flash the stock one (“fptw -bios -f section_0_A.25.data”). I’ve attached the cleaned/updated/AMT-enabled ME firmware region, based on the dump you provided earlier, as well as the latest stock BIOS A25 from Dell. You can either flash specific regions with “fptw -me -f me_clean.bin” and “fptw -bios -f section_0_A.25.data” or dump (“fptw -d spi.bin”) and mod (UEFITool) your entire SPI image by “Replacing as is” the aforementioned regions and then flashing back (“fptw -f spi_mod.bin”).
7010.rar (5.64 MB)
Will try and follow up tomorrow! Thanks so much…
@plutomaniac
No dice! I backed up my image and flashed the stock bios. I lost serial/service tag junk, as you said. Then, still with the jumper on, I followed up with the me_clean.bin file and the -me option. I shutdown, removed the jumper and then issued fptw -greset. Still no AMT options to be found and no response to Ctrl+p. I scan all the bios options each time to see if anything has been added, and nothing is new. It is the Q77 express chipset. Is it possible this is disable permanently in hardware?
At this point we have to assume it is a hardware restriction, meaning motherboard design. Usually people see “ME Disable” and not “ME Lockout” tag. We have been successful in fixing the former every time. Maybe you can ask Dell to tell you what “ME Lockout” means exactly. For now, restore your backup BIOS to get back all system-specific info.
So I ended up tinkering too much on my computer and fried the bios. I just replaced the motherboard and this time I’m attaching the bios before doing any flashing. Could you please take a look?
spi.zip (5.84 MB)
Does the new motherboard also have a “ME Lockout” tag? If it does and the limitation is motherboard design based, nothing will change. Hopefully you picked a replacement motherboard with AMT enabled or at least with “ME Disable” tag (which has been verified to work, after the ME firmware mod, multiple times in the past). Anyway, here is the cleaned/updated/AMT-Enabled SPI image based on your previous attached dump.
spi_fix.rar (5.66 MB)
Actually, that designation was on the chassis not the motherboard. Alas, it appears to be something tied to the model of motherboard so I have to finally throw in the towel. Funny how there are TONS of articles about how hard it is to disable and kill ME but next to none on how to hack it back to life. Thanks for your help.
Can this ME Lockout message be related to Anti-theft being activated or maybe TPM problem ?
Not Anti-Theft related. Besides, I always disable it at those modded Engine regions. The limitation is certainly motherboard design based.
Hey people,
I wondered if anyone can help me here. I don’t want to hijack anyone’s thread, but I’m experiencing an issue which may have affected people here - or, someone here might be able to help me with.
I have a Dell Optilex 7010 SFF. It came with a sticker inside that states “ME DISABLED”. My goal is to enable ME so I can use the IP/KVM functionality. I have followed the instructions from earlier in the thread, which are as follows:
1. Flash BIOS to A25
2. Reboot
3. Reset BIOS to defaults
4. Reboot
5. Adjust BIOS settings to your liking
6. Shutdown
7. Set jumper to Service mode
8. Flash me_fix.bin via "fpt -rewrite -me -f me_fix.bin"
9. Shutdown
10. Set jumper back to normal mode
11. Perform ME reset via "fpt -greset"
12. Reboot
13. AMT should be operational
Unfortunately, although MEBx is now available in the boot options list, after logging in with the default password “admin”, I am immediately required to change this password. It doesn’t matter what password I attempt to change it to (I have looked up the complexity requirements), but it is rejected each time. I have attempted entering passwords that consist of upper case, lower case, numbers and symbols (such as ‘!’), but it will not accept the new password and I therefore cannot proceed with provisioning of AMT.
I have also reset the CMOS (using the appropriate jumper), but this did not help.
Any help would be much appreciated.
That difficulty shouldn’t be related to the firmware modifications. Here is a MEBx User Guide for you to see what is required when changing the password (chapter 3.3).
Thanks Plutomaniac, your posts here have been really helpful. There’s no way most of us would have been able to enable AMT/ME without your help. Sorry I didn’t reply before now, I’ve been pretty ill. Anyway, I’m not sure why it wasn’t accepting a new password, but after a full power off, the new password was accepted and all is now well.
Provided we’re all up & running, presumably we can just flash the latest BIOS/UEFI? This new version (A26) was released just three days ago:
http://www.dell.com/support/home/us/en/0…?driverId=848GW
Thanks again.