I got an OptiPlex 7010 with “ME DISABLED 3”.
Can anyone unlock my image?
https://drive.google.com/open?id=1v2vq7r…Dzy-HpTIXkYAzbI
@show - What is "ME Disabled 3" Is this some error, if yes, show image.
this label.

Hahaaaaa! Well, that says it all in big font even! 
Do you have flash programmer? if not, check the board over for two pin jumper areas, that say Service, ME, FD, or FDO… Do you see any of those?
I don’t have flash programmer.
There is “SERVICE MODE” pin on my board.
@show - How did you dump 12MB file without programmer, with FPT?
Great you have service mode jumper, download this Intel ME System Tools V8 R3 package if you do not have it already, it’s in section "C"
Intel Management Engine: Drivers, Firmware & System Tools
Put a jumper on Service mode, and then inside System Tools package find Flash Programming Tool folder, inside it you will find windows folder. Select that windows folder, hold shift and press right click, then choose open command window here.
Then flash the file using command below
FPTw.exe -me -f fixmereg.bin
Then this command
FPTw.exe -greset
http://s000.tinyupload.com/index.php?fil…413823168523209
Then after reboot, shut down again and remove service mode jumper. If there is error running the -greset command above, run that again now with jumper removed.
If there is any errors, especially “Size” errors, stop, let me know and I will send you full image file instead.
It’s better to flash regions when that is all you are fixing, but with split BIOS I’m not sure what FPT does, so stop if any error, do not force or continue.
@Lost_N_BIOS
I got a dump file by using fptw64.exe.
(Sorry, I didn’t know this is called the flash programmer.)
Anyway I applied fixmereg.bin given by you,
and Intel AMT is available on my PC now!
Thank you!
@show - when I mention flash programmer (Not flash programming tools folder, as in Intel FPT), I mean hardware flash programmer like CH341A
Glad you were able to find and use Intel FPT, and it’s good to hear the ME region posted above fixed the BIOS/AMT for you, thanks for reporting back!
I see that someone else has been able to get AMT access on a Optiplex 7010 that was set as ME 6 Lockout from Dell. We get our systems from a company that refurbishes PCs and get a mix of variations, usually ME 1 or ME 3 from Dell, but I have at least one that is ME 6. I’ve been able to get the ones that were… I forget what exactly, Intel Management something, updated to full AMT access with KVM, along with the ones that were ME 3 Disabled updated to AMT access. But the one machine that I came across so far (I still have a lot more computers to go through before I know how many more) that is locked out and flashing the ME doesn’t enable AMT access. I’m not certain which file it was that they flashed to get it working, though I did see that they lost the serial number and other such information from the flash.
It’s been a long time since I’ve done any BIOS hacking (side note: hot flashing BIOS chips was a fun exercise back in the day) and it seems a lot more sophisticated these days. I read the thread on instructions, but I’m still not certain on what I need to pull, or if I just need to modify something in that other file that someone flashed so that the system doesn’t wipe it’s own info in regards to serial number, MAC, and whatnot. While for this machine, since we have a lifetime parts warranty, I could just call them up and say the motherboard needs replaced and hopefully get one that isn’t locked out, we also got ~60 PCs from a local business that also are set to lockout and I can’t get those motherboards replaced. (They’re actually a larger motherboard as they aren’t the ultra small form factor PCs.)
If you need an image from either one of the working machines or one of the lockout machines, or want to give me a heads up on what I need to do myself to get it to work, just let me know. Thank you.
I grabbed an SPI from a PC with a working AMT that’s been updated to the latest BIOS and ME firmware. Went to grab an SPI from the version that is disabled and noticed something interesting. I tried on several, but each one would fail on the Intel ME Firmware update on the first attempt. A second attempt would appear to work correctly and will then show the latest version being installed when running the BIOS update again. However, ME Analyzer shows that the ME was not updated. I then flashed the modified ME from A21 that I used successfully on other AMT disabled PCs on one of the machines and it did update the ME to that version, but when running the A29 update again, it still does not update the ME.
So it appears that I can’t do a straight apples to apples comparison on the SPI images of the lockout and working files, but hopefully it is close enough.
Here are the files I grabbed if anyone else would like to take a look while I try and find some time to dive into them.
A29_* are the files from the PC with the working AMT.
DA29_* are the files from the PC with Dell shipping it in AMT lockout mode.
MA29_* are the files from the PC where I applied the modified ME that enables AMT on machines where it was disabled but doesn’t seem to have an effect on lockout machines other than actually updating the ME firmware.
Probably only needed the SPI files since flashing just the ME doesn’t seem to get these working.
While I do intend to try and get this figured out on my own, I don’t mind if someone with a bit more experience with doing this figures it out before me and offers up the needed files. (Preferably with an explanation of how it was done so that 1, it is a learning experience and I can possibly know how to do this for other models in the future and 2, I don’t screw up the instructions right now when trying to do it myself and screw up the whole PC. lol)
EDIT >
Files were grabbed using these commands:
FPT -d a29_me.bin -me
FPT -d a29_spi.bin
A29_ME.zip (2.64 MB)
A29_SPI.zip (5.92 MB)
DA29_ME.zip (2.57 MB)
DA29_SPI.zip (5.85 MB)
MA29_ME.zip (2.5 MB)
MA29_SPI.zip (5.78 MB)
The ME LOCKOUT 6 restriction is found at the Flash Descriptor > PCH Strap 10 > “Reserved” field which is not really “reserved”. The proper name for this field is “AltMEDisable” and it must be set to false for the ME to not be disabled at boot. So adjust that and make sure to enable all the AMT features at Flash Image Tool while you’re following [Guide] Clean Dumped Intel Engine (CS)ME/(CS)TXE Regions with Data Initialization.
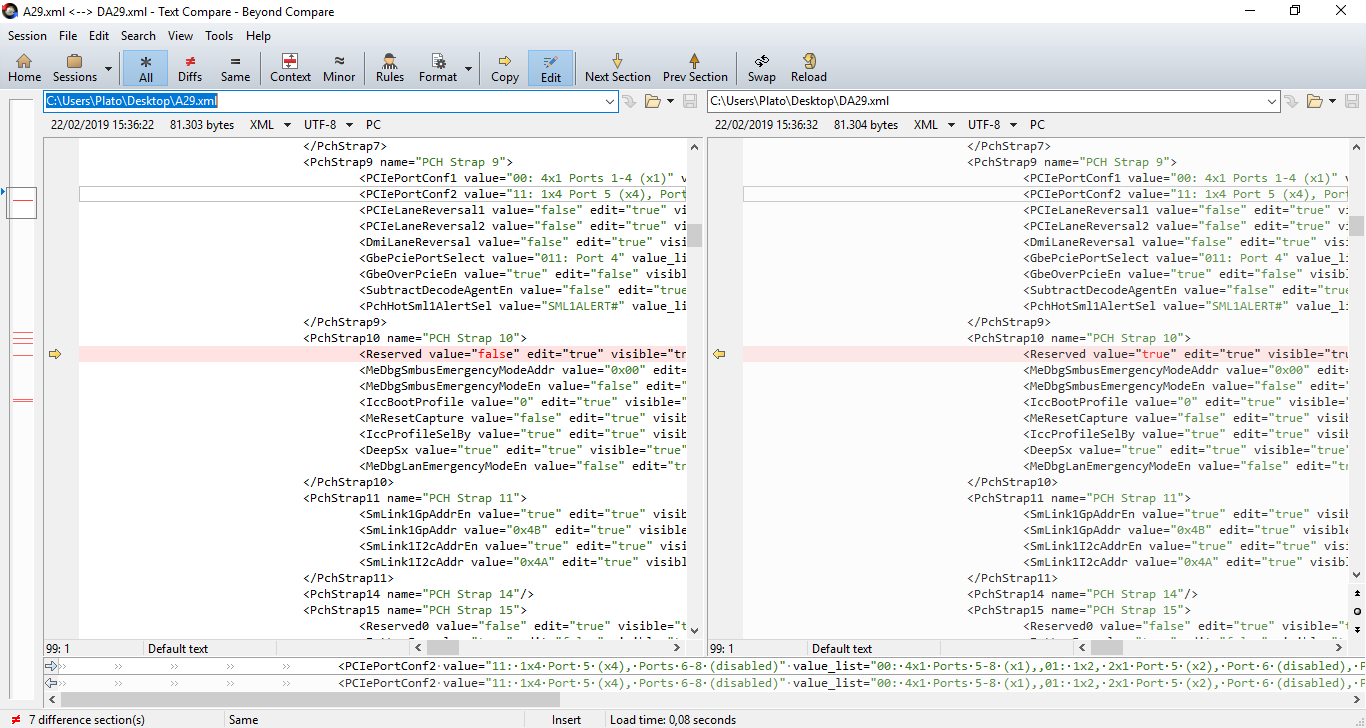
I haven’t even had a chance to sit down and look at the files yet, but with that bit of info, I think I might be able to do that this afternoon after lunch.
Just to make sure my thought process is correct, to get this to work, I would first have to flash the Flash Descriptor (I remember seeing it in an earlier post around page 3 at default view settings to fix an issue with the drivers for 3G modem) then flash the ME?
Thank you so much for your help.
I can see that you have full SPI chip dumps (FD + ME + BIOS) so it’s easy. Follow [Guide] Clean Dumped Intel Engine (CS)ME/(CS)TXE Regions with Data Initialization on that system’s dump and while you’re adjusting things at Flash Image Tool, remember to set “Reserved” to “false” and to enable the AMT capabilities at the equivalent menu. Then re-flash the entire 12MB outimage.bin back.
I took what should have been my cleaned SPI image and flashed it to several PCs. It seemed to be a success as I was now able to get into AMT. However, when the computer lab was being used the next morning, it appears that somehow, the MAC addresses (and I believe serial numbers, possibly other settings) were all now being reported identically. This, needless to say, caused a lot of issues in that computer lab. Luckily, it had been the end of the day and I had only got to about 10 of the machines. As a temporary fix, once I figured out what the problem was, I used the registry to have Windows use the old MAC address (I luckily had those from an earlier network scan) for each of the machines while Windows is loaded. Attached is the file I used, if anyone can figure out how to make it not set the serial number/MAC/etc, I’d appreciate it. If you can also tell me how to purposefully make it set a specific serial number/MAC, I can create a handful of versions to reset the affected machines back to having their original MAC and serial numbers.
(It is probably something simple that I screwed up somewhere when following the instructions. In the meantime, would it be possible to just flash the ME from this file with the fptw -rewrite -me command and use the fpt -rewrite -desc command to flash the description instead of flashing the whole file? Or is it something in those bits that is re-writing the serial/MAC?)
A29_AMT.zip (5.77 MB)
This is not ME, but BIOS related. You should only re-flash the ME region of the SPI chip, not the whole thing. Each BIOS holds its own serial numbers, MAC address and other info. By re-flashing the whole SPI image into each system, you made firmware duplicates. Do you have SPI backups from these systems by any chance? If you do, you can replace the unlocked ME region only and flash them back as they were. Otherwise, you’ll have to edit each SPI/BIOS image and manually fix the MAC address with a hex editor. I don’t know where it is but if you know the current one, it should be easily detectable within the SPI image. @Lost_N_BIOS has done that multiple times to help other similar cases.
@gorgarath - Yes, I can help you fix this if you have all the MAC addresses for each machine. First I need one full SPI image and the correct MAC ID for that machine, preferably pull this from a machine that you have not reflashed already.
If serial number and UUID matters too, then I need those from the machine dump mentioned above as well. Then I can tell you how to fix all the messed up ones.
MAC, usually, will be a much easier thing for you to fix on all machines, but if serial/UUID is also needed to be fixed, this will be more difficult on your end and you may need me to do for all systems
For the rest of the machines, and any other time, if you are only fixing the ME use this command >> FPTw.exe -me -f me.bin
Do that with the extracted, corrected ME region as source file at the end of the command
The most important thing is getting the MAC address corrected so that the machines won’t be fighting each other on the network. I figured it had to be a BIOS thing and looked for a bit more info, but my google-fu was failing me and I wasn’t finding anything useful. Getting the serial fixed as well would be nice, but I’m not sure I have those anywhere other than the sticker on the chassis, assuming the motherboard matches the chassis. And the fact that it’s no guarantee with these refurbs that the motherboard matches, I’m not overly concerned.
@Lost_N_BIOS If you look at my previous post, there is the full SPI. B8-CA-3A-89-DA-87 is the MAC in the file while 90-B1-1C-95-D9-E4 is one of the correct MAC addresses. 8N6MGX1 is the S/N that was installed and 69TLDX1 is the S/N that matches the corrected MAC I gave you. I’m not sure if I have anything that would have a record of the UUID or even where to find that on a machine. My best bet is probably if Spiceworks picked it up on a scan. Is having duplicate hardware UUIDs an issue? I’m not sure what all they would effect.
The reason I had flashed the full SPI is that I had misunderstood what pluto had meant when saying to just flash the full SPI back. He was referring to that machine specifically, not to the rest of the ones I had to fix the Flash Descriptor to enable AMT due to the “lockout” mode Dell uses. So, from now on, I’ll just use the -me and -desc with that file to fix the AMT issues.
On a side note, would using the BIOS recovery mode that these systems have work to fix the issue? I have a copy of the Dell BIOS file in renamed format to work, but haven’t had a chance to try it yet. I’m thinking it won’t do anything, but I’m not sure.
Thank you all so much.
@gorgarath - Serial might be on a sticker on the boards too. Serial is only really necessary if these are under warranty and you needed to file RMA, or if serial/UUID is tied to windows activation on these systems.
UUID can also effect other software activations besides windows activation, it may not matter on your current systems though, you’ll find out soon enough if anything else starts saying it’s not activated or giving you issues then you’ll know this needs fixed too.
Do you mean BIOS in post #134? If yes, incorrect MAC is in 30+ of places in NVRAM volumes, and this can’t easily be fixed on many machines, it should be ignored or change once corrected in the main location I think.
The main actual MAC can be corrected for each system using the following method. Open any BIOS in UEFITool, expand the “Intel Image” at top, go to the second entry inside “GbE” Right click GbE and extract as-is.
Open this file in hex editor. MAC address is in this file twice, once at very beginning 0h and again at 2000h. Once edited, flash back this file by itself using FPT >> FPTw.exe -gbe -f gbe.bin
Serial, is in padding file in middle of the BIOS region, this can be seen/extracted with UEFITool and edited with hex editor
Location x2 @ 14Fc and 84dd
Inside this same file is also a PPID number, probably also machine specific
To correct this, on each system, you would need to reflash the BIOS region only, with a corrected edited BIOS (Extract that padding file, edit via hex, replace and save BIOS image, use this as source in below command)
To dump BIOS region for edit >>> FPTw.exe -bios -d biosreg.bin
To flash edited BIOS region back >> FPTw.exe -bios -f modbiosreg.bin
However, for the above BIOS region flash to be possible you will need to make several other BIOS edits, so maybe not ideal for you or the situation, but I will explain them below in case you want to edit.
You can do one by one with programmer, without having to do this.
You need to first unlock the FD in these BIOS, rewrite each system with an unlocked FD BIOS image, this will be easiest way using programmer, so you don’t have to program a tiny region with programmer (unless you know how to do that easily)
Unlock FD by opening entire BIOS in hex editor, and then see second spoiler image in section “B” in this thread - [Guide] Unlock Intel Flash Descriptor Read/Write Access Permissions for SPI Servicing
Then you also need to edit “BIOS Lock” in the setup SubGUID Module, Setup module you can find via search, GUID, and this is the GUID - 899407D7-99FE-43D8-9A21-79EC328CAC21, expand that to find subGUID - 97E409E6-4CC1-11D9-81F6-000000000000
Extract as-is, edit per below, then replace as-is, for this MMTool must be used instead of UEFITool due to some issues UEFITool has with file handling. For MMTool, find “SetupPrep” and extract uncompressed, then edit as mentioned, then replace
Edit 58b16, change 00 to 30
Then edit 58b24 change 30 to 00
Then this BIOS with FD unlocked and BIOS lock disabled, program in with programmer, then you can use FPT commands above to reflash the BIOS regions to change serial # on each system. The FPT GbE commands to fix MAC do not require this edit, only the changes and flash for BIOS region.
Of course, if you use programmer to fix BIOS region, you can do that for each system individually without having to unlock all this stuff, just dump the entire BIOS on each one by one and edit and reprogram, then next, and so on one at a time with their own files.
To avoid all this hassle on the remaining systems that you haven’t messed up in this manner, take a fixed ME BIOS image. Open in UEFITool, expand Intel Image, right click the ME and select extract As-Is and save as me.bin
Then use commands I gave in post #136 to reflash to each machine, but again for this, you will need to at least unlock FD on each system, so you can FPT flash the ME. Otherwise, dump each system’s BIOS with programmer, replace the ME region via UEFITool with the corrected ME region, then reprogram.
Do this one by one for each system you want to fix with the same ME
To make things easier on you, if you want, I can give you a FD unlocked, BIOS lock removed, generic BIOS image you can reflash to all the affected machines (affected ones only, rest of unaffected machines dump and edit ME properly one by one then reprogram).
This would be similar to what you did, would put in invalid serial and MAC etc, but would have the locks disabled, so you could then easily use FPT to reflash quickly on each instead of having to program each one individually.
Whatever sounds easier to you? If you’re reading this now, refresh page in 5 minutes or so and I will upload this BIOS for you, it will be BIOS from #134 edited.
Here is FD unlocked BIOS, with BIOS Lock disabled as well - http://s000.tinyupload.com/index.php?fil…219335065324801
@Lost_N_BIOS That … is a lot of information. lol
These are all refurbs and the serial isn’t really going to make much of a difference as I can get the serial number from the chassis or just supply a serial number from an unaffected machine. (We have a lifetime warranty on the parts from the company we buy our refurbs from and they do ask for serial, but most of the time I just grab one of the serial numbers at random instead of the actual serial on the machine.) Windows activation is all done via KMS with our Education license, so that won’t be an issue. It seems the worst case scenario will be I might need to re-run the device based activation for Office 365 on the affected machines if I don’t correct the serial and/or UUID.
Just to double check and make sure I have this right, I will need to make a hex edited gbe.bin for each of the affected machines with the corrected MAC address, correct?
If I just skip the serial and UUID, I think the majority of your post I can skip, though will probably come back to later just to give it a try. One thing that confuses me is the bit about needing to unlock the flash descriptor. Is that a software unlock that is different from using the jumper on the motherboard? I did not yet look at the linked post, but it sounds like it accomplishes the same task. (Assuming the linked method will actually make it so I don’t need to set the jumper on the motherboard to flash the FD/ME/etc?)
And just to clarify, to get the systems that have completely locked out AMT with the one setting in the FD, I can use my modified SPI file as-is, as long as I only flash the FD and ME? (ie FPT -rewrite -desc -f A29_AMT.bin followed by FPT -rewrite -ME -f A29_AMT.bin) And that should leave my serial numbers/MAC addresses/UUIDs alone?
I don’t know if it’s worth my time to correct the S/N for each of these machines, but I might give it a go for at least one of them just to do it and for the learning experience.
Thank you so much for all your help and instruction.
EDIT> I know there used to be a tool to erase the Serial number out of the BIOS on older Dells so that the correct one could be set so that the motherboard serial number could match the chassis. Not sure if there is a tool that works on these systems or not. Motherboards from Dell I believe just come with the serial number not set and prompt you for it on first boot. I don’t recall that from way-back-when when we bought new systems and had warranties from Dell, though I do recall the first boot prompting me for the code on the inside of the case for the AMT setting to have it enabled (1), disabled (3), locked out (6), etc. Sadly, at the time, I think I had hit 3 because I had no idea what it was talking about and that’s what the case had on it. I’ll find out when I get around to setting AMT up for that lab. Thankfully, Dell seems kind enough to provide that jumper on the motherboard so I can re-flash the ME without too much trouble. At least, I hope those old 780s or 790s or whatever they are have the jumper it it needs enabled. Else I’ll have to wait until they finally get replaced in another 2 or 3 years.
The jumper unlocks the FD so no need to do more on that front. You only need to flash the FD for the AltMEDisable bit and the ME for AMT enablement. Might be difficult to find some Dell OEM tool which replaces the info at NVRAM easily but do take a look at the BIOS Tools thread over at MDL.