My pain, that I have great compatibility trouble between HP EliteDesk 800 G5 SFF and HPE Tesla T4 GPU, bought for study bioinformatics and AI technologies in medicine.
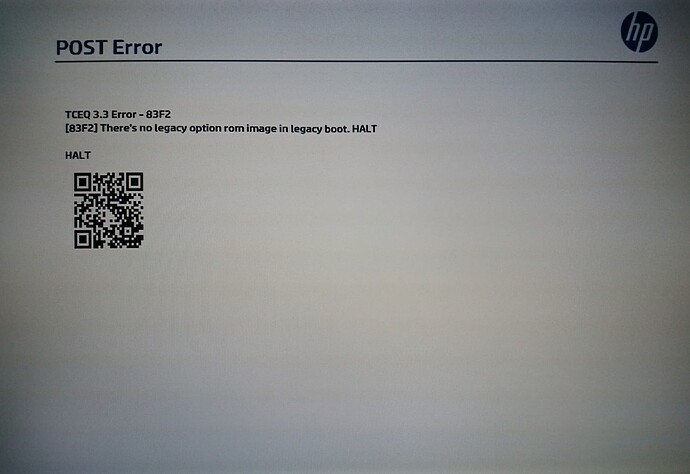
Every boot I have black screen, system hang, 3 long beeps, 3 short beeps and BIOS setup inaccessibility, prolonged noisy boot, although Win10x64 works well with Tesla T4 in every application and in Device manager.
But black screen on every boot + system halt - they prevent me from proper installing Red Hat Linux v9 with proper Tesla T4 GPU kernel mods injection during Linux installation.
I wrote to official HP support, but they are silent, as shown:
Absolutely the same configuration (Intel Core i9 + chipset Q370 + embedded Intel UHD 630 + Tesla T4) works perfectly into industrial PC Nuvo-7166gc (I plan to buy modded water cooling or 3D-printed blower).
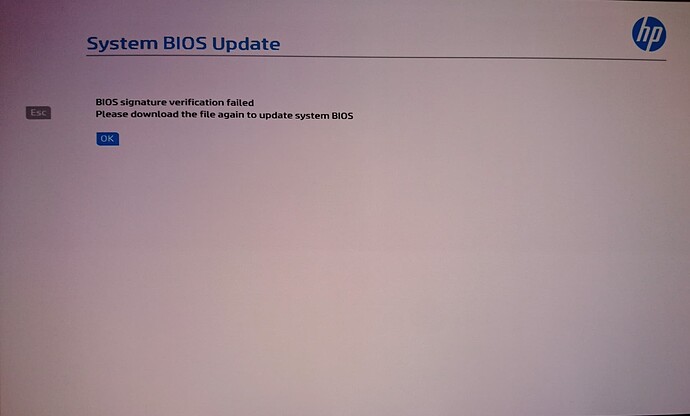
I upgraded vBIOS of TeslaT4 with new UEFI GOP driver (nvflash64), but without effect (Tesla T4 became more stable in power management, less panic, less hot).
The boot issues were the same.
Thus, in order to solve compatibility issues I dream of job to be done:
-
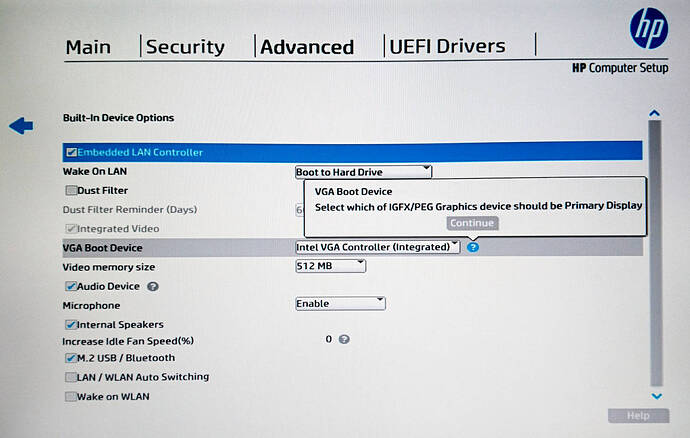
Unhide in “Advanced settings” menu with submenus “Primary Video Boot Device” and “Primary Graphics Device” (they are not seen in IFRExtractor, only by listing and viewing).
GraphicsConfiguration → PE32 image section, GUID: DE35F257-36BF-4F71-8270-51CF5378B86C
Section_PE32_image_HpSetup_0147_IFR
0x10BAF4 Advanced (0x28B)
0x10BECB Var Store: 0x11[2] (HP_GraphicsConfiguration) {24 2F CE 9E 3B FB BA 4A 33 49 B4 9D B4 D6 7D 89 23 51 11 00 02 00 48 50 5F 47 72 61 70 68 69 63 73 43 6F 6E 66 69 67 75 72 61 74 69 6F 6E 00}
0x10DE52 Form: Built-In Device Options, Form ID: 0x6 {01 86 06 00 91 02}
0x10DE58 Subtitle: Built-In Device Options {02 87 91 02 00 00 00}
0x10DF44 Checkbox: Integrated Video 32-bit Support, Variable: 0x0 {06 8E 02 00 BD 00 87 00 02 8F 00 00 00 00}
0x10DF52 End {29 02} -
Inject fresh VBT(228?)+GOP driver (1091?) into stock HP BIOS.
-
Inject fresh OROM vBIOS (1065?) in order to support embedded Intel UHD 630 + embedded GPU GT2 for error-free boot of VMs and remote desktop support (i.e. check PyMol rendering on my workstation).
The latest HP EliteDesk 800 G5 SFF Bios is v02.18.00 and it includes very very old UEFI drivers:
EC/SIO F/W 8.9.20
Cypress PD FW (CCG5C) 4.4.0
Cypress PD FW (CCG5) 6.8.0
Intel Legacy VBIOS 9.2.1020 (19/03/04)
Intel GOP EFI Driver 9.0.1085 (19/02/21)
GbE Version 0.54 (I219LM)
PXE option ROM 0.1.14
PXE UEFI Driver 0.0.23
And here is the stock HP BIOS v2.18 for modding:
https://ftp.hp.com/pub/softpaq/sp148001-148500/sp148214.exe
As HP BIOSes are partially encrypted - I don’t risk to brick my system, although I had just prepared recovery USB with HP_TOOLS with recent BIOS.
I need a thorough Guru’s help, to mod my desktop BIOS ![]()
![]()
br>
Edit by Fernando: Thread title shortened