Introduction:
I recently bought a “CHUWI Herobox Mini PC Intel Celeron J4125 Quad Core 8GB RAM 256G SSD” but it has a bios with a known problem. And because of this The Wake On Lan feature is not working.
I contacted the manufacturer but they do not have a bios update available (yet, but I don’t expect anything soon).
That’s when I started my quest to fix this problem.
I’m currently at day 5 of my quest, I’m almost at the point of giving up and I decided I need some help.
Problem “18 - Error: Secure Flash Rom Verify fail.”:
I’m not able to flash any modified bios to the board.
If I use the “AFUWINGUIx64” tool I get the following error “18 - Error: Secure Flash Rom Verify fail.”
I also tried the non GUI version “AFUWINGUIx64”
And tried flashing from the Uefi shell.
Every time I get the same “secure flash” error.
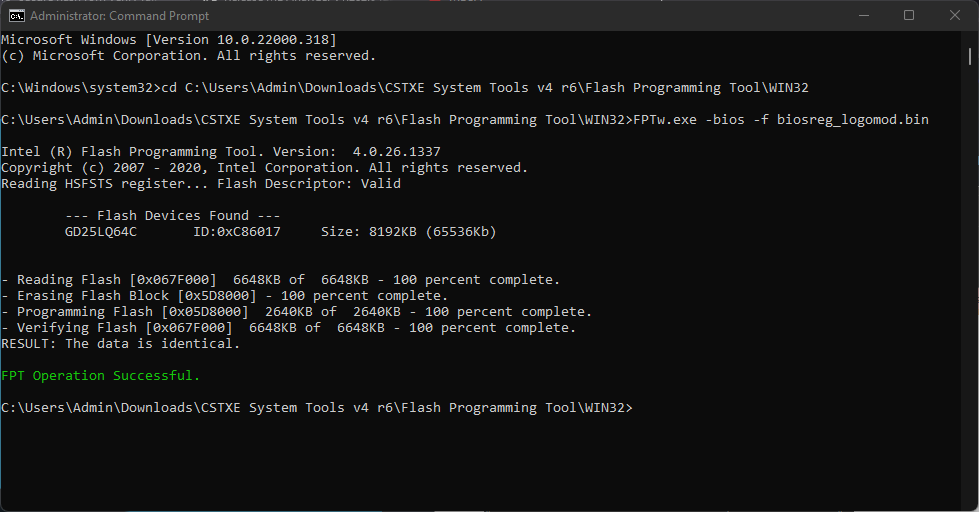
I managed to flash a modded bios using a SPI flash programmer, but this bios did not work.
BIOS mod:
Created a lot of modded bios versions I thought I was doing something wrong and corrupting the binary thus preventing it from flashing. I now assume this is most likely not the case and something else is preventing the modified Bios from running (Intel Management Engine?). To verify this I’m trying to flash a simple mod were I replaced only the Splash logo. (instead of the bios with unlocked features and updated lan drivers)
Changed the splash logo to a custom one using the “MMTool 5.2.0.25” , “UEFITool 0.28”, “AMI ChangeLogo Tool v5.0.0.2”
Things I tried:
#1 Flashing using the AMI AFU for Aptio V tools
As described above, tried all of the tools without success.
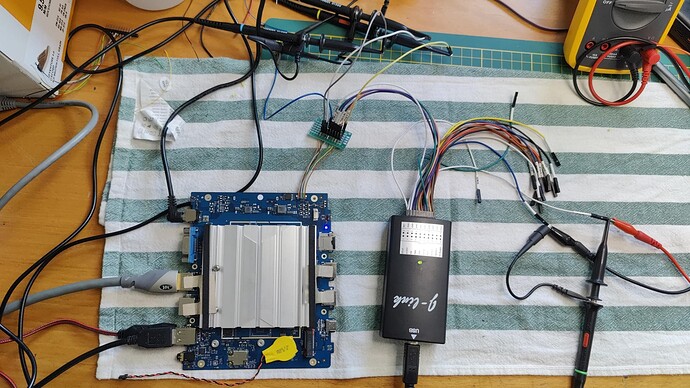
#2 Flashing the modded bios using a SPI flash programmer.
I disassembled the mini PC and located the BIOS flash chip. “GD25LB64CVIG - GIGADEVICE”
Connected my Segger-Jlink clone to it and was able to read the flash memory, and also tested writing it back.
Everything seemed to work, but I was not able to get the modded bios functioning.
The bios shows up very shortly and gives the following error:
“flash update failed”
“flash image invalid or not found”
“system will reset in 5 seconds”
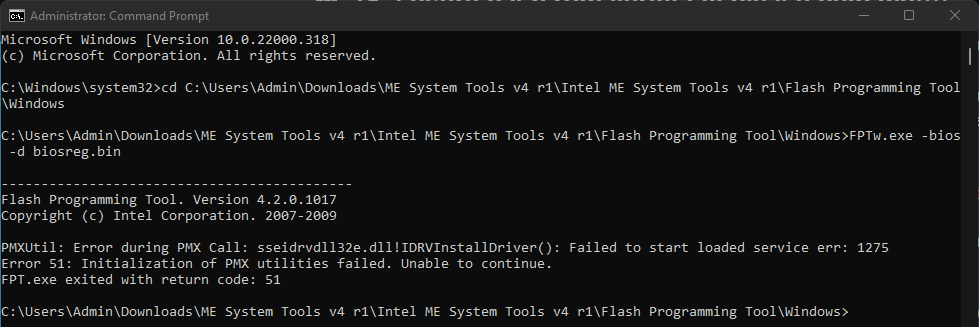
#3 Flash using the “FPTw.exe” tool
After reading this topic: 18- secure flash rom verify fail please help me!!!! - #4 by Lost_N_BIOS
I discovered I need to use the FPT tool for programming the bios so I check my “Intel ME Version” using the HWiNFO tool.
"
Intel Manageability Engine Features
Intel ME Version: 4.0, Build 1524, Hot Fix 32
Intel ME Recovery Image Version: 4.0, Build 1524, Hot Fix 32
Intel ME FITC Version: 4.0, Build 1337, Hot Fix 26
"
I have version 4 so I downloaded the “ME System Tools v4 r1.rar”
But running the FPTw.exe tool result in a error (currently I have Windows 11 Pro X64 running on the system):
In addition I tried other versions V15, V16, V2, V3 but none of them work.
#4 Disabling the Bios lock using ami setupwriter from efi shell
The bios lock variable offset is 0x161, but looking at the IRFE extract report this value was not set (bios unlocked by default).
Still tried disabling it using the ami setup writer from uefi shell, got the confirmation it was already turned off. Tried flashing a modified image afterwards but this failed.
#5 Tried signing the bios image file.
I’m able to add keys inside the bios so my thinking was if I sign the modded image using a self signed certificate and add this certificate to the bios it might work. The bios has the option: “Enroll Efi Image” “Allow the image to run in secure Boot mode. Enroll SHA256 Hash certificate of a PE image into Authorized Signature Database (db)”
But I’m not able to sign a BIN file. It is not supported by the microsoft signtool. So this was a dead end.
If someone know the correct way to do this please let me know (I’ve tried this to sign the image Self-signed certificates for testing code signing - Mustafa Mohamad)
#6 Hardware mod
I discovered a unpopulated connector footprint on the PCB near the BIOS flash chip most of the pins of this connector are connected to the SPI flash chip, however two of these pins are not connected to the flash chip or power/ground. I’m not sure for what purpose these are used. Maybe this is a way to disable the TPM or other method to disable Secure flash. I will try multiple logic levels on both pins if there is no other solution available to me, for now I do not want to apply voltages to pins I do not know the purpose of.
How to proceed?
I don’t know how to proceed anymore I believe I have tried everything and that’s why I have created this topic asking for help. Did I miss something or am I out of luck and is it really not possible to flash a modded bios to this system?
Files
Original.rom (original bios extracted using segger-jlink ans J-flash SPI software)
Spalshmod.rom (modified boot logo using AMI ChangeLogo Tool v5.0.0.2 tool)
https://drive.google.com/drive/folders/1KC63DRbYjjvLafZZMjK7k4QjJlj6TQiF?usp=sharing
Other info
System OS = windows 11 pro x64
Secure boot is turned off