Hello, I have the ability to flash through the programmer - but for this I need a bios mod
The program from the archive fails to generate a “MOD.bin” file for your G5 KF?
I did not start start.bat because the archive contains a 3000 series of video cards (because I don’t know much, I was afraid to start it), I pulled out the commands from start.bat only to create a dump. Once I mistakenly overwrote the BIOS from another laptop by inattention and then flashed the original BIOS in a friendly service on the programmer. Mod.bin received in the evening I’ll try to flash it on the programmer. Thanks for the help.
This goes along with how Gigabyte named one series of the G5 laptops.
I understand, I just have a more recent laptop with 4060 video, it is also G5 but 2023
Hi there. I have my G7 KE 12 gen (12500H) and 3060 laptop. And i want to unlock my bios. Is it possible? I have FB05 March 2023 BIOS.
Hi and sorry. Unlock is not possible.
Hello, do you have for the g5 kd-52US123SO, to unlock the bios, im in fb05 version.
Thank you
@Sweet_Kitten Hello, I have the Gigabyte G5 KC i5 10500H and RTX3060 Laptop, but with FB08 BIOS version, can I use the files you share earlier for unlock de the BIOS or you need my BIOS backup?
Thanks for your attention.
Try the following.
If doesn’t work, a BIOS backup wil be needed.
@Sweet_Kitten
Everything works perfectly and now are a LOT of options available in the BIOS.
I really want to thank you for the work you have done.
hello. I have a Gigabyte G5 KD laptop. Is there a way to unlock the bios of this laptop?
Hello. The way is the same as for G5 KC.
Could you help me have the advanced bios options?
Hi @Sweet_Kitten , ![]()
I have a Clevo NP70PNJ. Seem to be a NP5x_NP6x_NP7xPNK_PNH_PNJ series.
For the NP70PNJ, it features an Intel i7 12700H + RTX 3050, which is equivalent to a Gigabyte G7 GE based on the same Clevo platform and BIOS.
So, we’re dealing with Intel’s 12th generation.
.
![]() However, based on what I see in your script:
However, based on what I see in your script:
if (:NP) then { echo looks like device 12-th Gen CPU, which BIOS can not be modified all the way through automatically }
.
![]() And especially based on these posts:
And especially based on these posts:
Post #311
Hello, I’m sorry to resurrect an old post, I wanted to know if it’s possible to use this Mod for G5 KE 12500h rtx 3060. I tried to use it but it says “You ought to flash the Mod manually by some SPI prog. tool”. All good? Thanks in advance.
Post #312
That’s right, for new Gigabyte laptops with 12 gen CPU, the script is only capable of generating a “MOD.bin” file.
Gigabyte G5 is a Clevo barebone device. And they don’t allow to install customized BIOS anymore. I think that some register of PCH (platform controller hub) blocks operations with SPI if the CPU is NOT in SMM state. There’s no solution to this yet unless you’re willing to help.
Post #330
Sorry, BIOS chip memory is not writable for these: G5 KF, G5 MF, G5 GE, G5 KE, G5 ME.
It seems like modifying the BIOS for Intel 12th generation is a dead end.
.
![]()
![]() In the case of Intel 12th gen, creating a backup of the current BIOS isn’t a problem: fptw… -d 𝗕𝗜𝗢𝗦.bin
In the case of Intel 12th gen, creating a backup of the current BIOS isn’t a problem: fptw… -d 𝗕𝗜𝗢𝗦.bin
![]()
![]() Patching in *.txt format is a bit tricky, but it’s doable with HxD since similar patterns often recur: UEFIPatch… 𝗜𝗡.bin 𝘕𝘗.𝘵𝘹𝘵 -o 𝗠𝗢𝗗.bin But let be honest, I don’t kown where to start…
Patching in *.txt format is a bit tricky, but it’s doable with HxD since similar patterns often recur: UEFIPatch… 𝗜𝗡.bin 𝘕𝘗.𝘵𝘹𝘵 -o 𝗠𝗢𝗗.bin But let be honest, I don’t kown where to start…
![]()
![]() However, I stumbled upon this while trying to flash a modified BIOS for microcodes: Microcode Update of Insyde UEFI BIOSes. It seems that the major issue is writing the modified BIOS: fptw… -f 𝗠𝗢𝗗.bin -bios in the case of the 12th generation CPUs?
However, I stumbled upon this while trying to flash a modified BIOS for microcodes: Microcode Update of Insyde UEFI BIOSes. It seems that the major issue is writing the modified BIOS: fptw… -f 𝗠𝗢𝗗.bin -bios in the case of the 12th generation CPUs?
.
Correct.
One guy today wrote that he was able to flash using fpt but ended up bricking his NP50RNx due to some mistake. Now I’m trying hard to get any details.
UPD: the guy lied.
I will attempt rather naively to flash a isflash.bin MOD version, which is, in fact, an original isflash.bin but with updated microcodes (plus fixes for checksums in headers/data and fixes sizes) using H2OFFT-Wx64.exe
Picture
Because unlike FPTWxxx.exe, H2OFFT-Wx64.exe appears to have more workarounds (IHISI + SMI) for flashing a modified isflash.bin
If I succeed in flashing the modified isflash.bin with H2OFFT-Wx64.exe, it means that it might be possible to do the same with a SetupUtilityApp that you patch because in both cases, we are outside of BootGuard
However, this implies that applying *.TXT patches with UEFIPatch.exe in batch mode might be dead ![]() . We would need to be done manually in hexadecimal
. We would need to be done manually in hexadecimal ![]() …
…
The thing is, I don’t know how everyone here knows which hexadecimal values to change to modify options in a BIOS for example… ![]()
It’s like you all read directly in binary files the way Neo reads the matrix! ![]()
![]()
![]() (★)
(★)
(★) EDIT : I think I find how you all find hexa vars to modify: LongSoft / IFRExtractor-RS
ifrextractor_v1.5.1_Windows.zip (409.1 KB)
hello can you do this
https://download.gigabyte.com/FileList/BIOS/nb-bios-aero15-vd-win10-win11-64bit-fb08-fe08-ec-f006.zip?v=9b2337c6a93f8ce68fe7703ab6676bfc
But what is this model? Can’t find by filename.
@MLS.22 , I appreciate your offer, but this BIOS isn’t on the same Clevo platform or CPU generation.
However, it’s interesting to disassemble it for inspiration in modding.
@Sweet_Kitten : NP70PNJ . But can refered as ★NP5x_6x_7xPNK_J_H or ★NPxx**PN_KHJ or ★NPxxPNK_J_H or ★NPxxPNKJH or ★SCHENKER MEDIA 17 (M22) (ID: SME17M22) or ★Gigabyte G7 GE …
Nonetheless, I was too focused on how to unlock/mod my BIOS when the question doesn’t apply.
Indeed, on the 12th generation Intel processors, especially the H-series CPUs, undervolting is physically impossible. It’s a hardware modification in the microprocessor’s construction.
Case closed. End of story.
Long explanation
In fact, this 12th generation processor model has an ‘Undervolt Protection’ that can only be (and very difficultly) unlocked on CPUs type K / X. ![]()
For the 12th H-series family, it’s simply hardware-locked. ![]()
I contacted ![]() Intel to express my frustration
Intel to express my frustration ![]() with their increasing tendency to lock down their systems. They responded that it’s a security measure
with their increasing tendency to lock down their systems. They responded that it’s a security measure ![]() due to the Plundervolt vulnerability
due to the Plundervolt vulnerability ![]() , and also because most end-users tend to brick
, and also because most end-users tend to brick ![]() their hardware when undervolting.
their hardware when undervolting.
If a hardware has overheating issues ![]() , it’s not Intel’s fault, but rather the manufacturers putting a 12500H or 12700H into a 2cm-thick laptop; it’s a design flaw, and undervolting isn’t meant to compensate for the manufacturers’ design flaws they said.
, it’s not Intel’s fault, but rather the manufacturers putting a 12500H or 12700H into a 2cm-thick laptop; it’s a design flaw, and undervolting isn’t meant to compensate for the manufacturers’ design flaws they said.
![]() A notable point found on Reddit: if Intel allows it in the HK’s type, what’s the difference in terms of vulnerability with an H or P? It’s seem to be the perfect excuse to force you to go for an HX processor
A notable point found on Reddit: if Intel allows it in the HK’s type, what’s the difference in terms of vulnerability with an H or P? It’s seem to be the perfect excuse to force you to go for an HX processor ![]()
In short, the locking is hardware-based for the 12th-gen H version, regardless of the PC brand.
So, @Sweet_Kitten or @lfb6 can rightfully and logically close every kind of request about modding 12th not K/X ![]()
.
So, regarding the BIOS for my Clevo NP70PNJ - 12700H - RTX 3050, I’ll have to settle with Intel ME updates (to address the vulnerabilities detected by Intel CSME Detection Tool) and microcode updates (to address CPU vulnerabilities).
For Intel ME, I found how to do it as seen here
For the microcodes, @lfb6 guided me step by step here (Kudo to him ![]() ), and I have a BIOS with up-to-date microcodes (
), and I have a BIOS with up-to-date microcodes ( ![]() 1 [5,23 Mo] ) that seems good.
1 [5,23 Mo] ) that seems good.
But, still, due to the 12th-gen locking issues, it’s not as simple as flashing with a simple FTPW64.exe -d MODDED_BIOS.BIN -bios
However, I might have a solution:
My Clevo’s original BIOS ( ![]() 2 [27,5 Mo] ) is provided in three versions,
2 [27,5 Mo] ) is provided in three versions, NPx0PNx.12 , NPx0PNx12.efi , and NPx0PNx12.exe .
By dissecting the NPx0PNx12.exe , I can see that it uses H2OFFT-Wx64.exe to flash an isflash.bin containing the original BIOS (NPx0PNx.12) and it platform.ini.
NPx0PNx12.exe ➜ ( ![]() 3 [6,74 Mo] )
3 [6,74 Mo] )
NPx0PNx12.exe extracted (with H2OFFT-Wx64.exe and original isflash.bin) ➜ ( ![]() 4 [7,28 Mo] )
4 [7,28 Mo] )
My concern now is that I’ve created an isflash.bin with a modified BIOS and updated microcodes inside ( ![]() 5 [6,83 Mo] ). I can run
5 [6,83 Mo] ). I can run H2OFFT-Wx64.exe, which finds and accepts my modified BIOS isflash.bin.
But I’m afraid to click “OK” ![]()
Even though the microcodes are outside the BootGard area, I fear there might be another security mechanism, like a hash/salt/signature for the entire BIOS, and that in the next boot, those Intel folks might block everything before even loading the BIOS (because a different hash/salt/signature that would block/stop boot that I haven’t yet found)
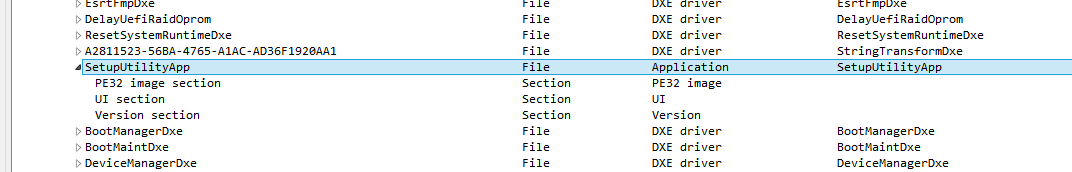
I think I must use the official TOOL folder ![]() (
(![]() 6 [54,4 Mo] ) inside the original BIOS to packed something with complex signature like this
6 [54,4 Mo] ) inside the original BIOS to packed something with complex signature like this ![]() :
: