Yep, could the reason be that I’m running on windows 11? Anyways I tried changing it with compatibility modus but that failed too.
Edit: second screenshot tells me that ‘‘the system can’t find the path’’.
Cant be.
But now at least I know the version of Intel Management Engine. This will help avoid the error: "the system can’t find the path". Run "READ.BAT" file from the archive attached.
14.0.36.1158.zip (2.04 MB)
That’s odd. Let me check if there is any other tool available to dump the BIOS
Update: I will try your way
Good. And now the BIOS that I see does not have PFAT format and I can modify it. But the question is how to flash it back to SPI flash memory as there is error 167.
I think I have a solution, but the process may seem difficult for you:
You should use the RU.EFI shell to allow writing BIOS to SPI flash.
BIOS Lock VarOffset - 0x17
Flash Protection Range Registers VarOffset - 0x6DD
Change 01 to 00
You will find this variable in a store named "PchSetup".
Here’s a useful example of using the program.
EDIT: I think it’ll take a while for you to figure out how the shell app works, so I’m going to sleep now.
Thank you for providing the needed assistance. It will indeed take time to understand how it works and I will read the guide carefully. Since I don’t want to brick anything I will also look for making a back-up. I will return back on this topic asap ![]()
Update: This shell is amazing! I kind off understand the basic of it, but I’m curious what or how I should interpret this data:
“Flash Protection Range Registers VarOffset - 0x6DD”
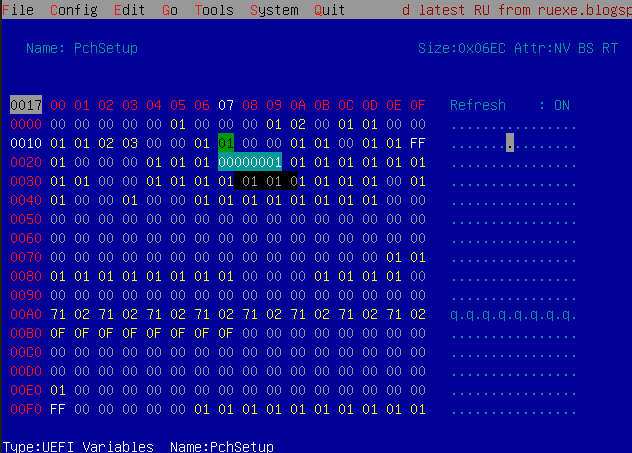
I attached the screenshot of page PchSetup. As I understood I need to change the variables from 01 to 00. I found 0x17 but can’t find 0x6DD. I think 0x6DD is already on 00.
As a sidenote: changing 0x17 to 00 doesn’t keep the settings saved. I tried several times, but it reverts back to 01 after rebooting.
Try scrolling down the page.
Do not reboot immediatelly but save the changes by pressing Ctrl+W.
Silly me… I found the variable.
I saved by pressing Ctrl +W got the message that it is OK, but when I restart it reboots again and sets the value back to 01.
Oh, this is too bad. It looks like Lenovo added a system to prevent unauthorized changing of variables. There is nothing to be done about this without hardware BIOS flashing tools. Since disabling the protection mechanism involves modifying BIOS, it creates a circle. Last time I’ve seen this on HP device and only on it, but the tendency is expanding.
So close yet so far ![]() let me see if I can revert back to an older bios version
let me see if I can revert back to an older bios version
Couldn’t revert back to the old BIOS. I found this topic [TOOL] Lenovo (H20) Bios Unlocker and Locker. Don’t know if this could work out. —> NO.
Other than that I guess I’m out of options.
Since I’m still learning any feedback is always welcome!
Another update. After hours of searching the forums I came to the conclusion that I indeed only have the option left to use an SPI programmer as @Sweet_Kitten suggested.
With only four days of knowledge I find the risk of bricking using an SPI programmer too high. The amount of people bricked their BIOS (chip) with several warnings included is most likely due to lack of knowledge.
Overclocking memory speeds and tweaking some other settings is for me not worth the risk (at this moment) and I encourage everyone to think twice before taking next steps.
So that means I firstly will take more time to learn about modding. That said, I especially would like to thank @Sweet_Kitten for the effort!
Hello KewellH. Did a search for Legion T7 XMP BIOS unlock and found this forum and thread.
Like you, I’m trying to figure out a way to unlock the advanced BIOS for T7-34IMZ5. It seems you got stumped at trying to revert back to old BIOS? I have previous versions of BIOS dating back to last June 2021 and have messed around with reverting back to different BIOS versions. In order to revert back to previous BIOS versions, you have to go into the BIOS and disable "Secure Roll Back Prevention" and set it to "NO". Hope this helps in some way.
Oh, this is too bad. It looks like Lenovo added a system to prevent unauthorized changing of variables. There is nothing to be done about this without hardware BIOS flashing tools. Since disabling the protection mechanism involves modifying BIOS, it creates a circle. Last time I’ve seen this on HP device and only on it, but the tendency is expanding.
Sweet Kitten, thanks for help and work you have done thus far.
Can the BIOS/UEFI "Secure Boot" setting be the variable or culprit?
---------
What is Secure Boot?
Secure Boot is one feature of the latest Unified Extensible Firmware Interface (UEFI) 2.3.1 specification (Errata C). The feature defines an entirely new interface between operating system and firmware/BIOS.
When enabled and fully configured, Secure Boot helps a computer resist attacks and infection from malware. Secure Boot detects tampering with boot loaders, key operating system files, and unauthorized option ROMs by validating their digital signatures. Detections are blocked from running before they can attack or infect the system.
How does Secure Boot work?
Secure Boot works like a security gate. Code with valid credentials gets through the gate and executes. However, Secure Boot blocks at the gate and rejects a code that has bad credentials, or no credential.
Hi,
Can you maybe extract they key combo used to acces that part of the bios?Or do they use a dongle of somekind? There is a way to boot a bios from usb, but that was very limited ( see my post on biosmod). I’m still leaning these things, sorry if make no sense ![]() gr
gr
Hi @KewellH , would you be so kind yo upload a BIOS dump for your T7-34IMZ5 again, please. It seems that this file is deleted. Thank you very much!!!
@Sweet_Kitten Hello, after browsing and learning from this post and others, I attempted to dump my BIOS and modify it using ru.efi, but ultimately I failed and would like to seek your help.
Basic Information:
My PC is a Legion Ren9000k 34IAZ, which is essentially the same series as the Legion T7-34IMZ5 from the post above, just sold in different regions.
The BIOS version is O5HKT2DA. You can see that the BIOS versions for the 34IAZ and T7-34IAZ7 are the same from the following two webpages:
- Legion T7-34IAZ7:
Legion T7-34IAZ7 BIOS Update - Legion Ren9000k 34IAZ:
Legion Ren9000k 34IAZ BIOS Update
This BIOS version already has some advanced menus enabled, such as the option to enable XMP. The BIOS update history is described in the second link.
My Needs: I have enabled XMP in the BIOS, and it works fine, but I also want to use XTU/Throttlestop for undervolting and overclocking. I can overclock, but I cannot undervolt due to the undervolt protection. So, I want to disable the undervolt protection.
What I Have Done:
Here is the BIOS I dumped.
Initially, I tried using SREP, but neither of the configuration files from the following two links worked:
Using UEFITool, I found that the “Undervolt Protection” option is hidden by the following logic:
Suppress If: {0A 82}
Variable 0x285C equals 0x0 {12 86 5C 28 00 00}
Variable 0x1293 equals 0x0 {12 06 93 12 00 00}
Or {16 02}
End {29 02}
Setting: UnderVolt Protection, Variable: 0x381 {05 91 CB 1D CC 1D EF 0E 02 00 81 03 10 10 00 01 00}
Option: Disabled, Value: 0x0 {09 07 04 00 00 00 00}
Option: Enabled, Value: 0x1 {09 07 03 00 30 00 01}
Through RU.EFI, I attempted to modify the CPUSetUp entry 0x381 to 0, but I received the error 0x00000008, indicating EFI_WRITE_PROTECTED.
I also had another idea to modify the “Suppress” condition to display the “Undervolt Protection” option:
Suppress If 0x285C = FF OR 0x1293 = FF
But I didn’t have any advanced guidance on how to do this.
Then I returned to SREP, tried to understand how it works, and with guidance from GPT, I learned how to create a CFG file. I replaced the "Suppress If" starting instruction with NOP, but still no effect:
Op Loaded
Setup
Op Patch
Pattern
0A 82 12 86 5C 28 00 00 12 06 93 12 00 00 16 02 29 02
00 00 12 86 5C 28 00 00 12 06 93 12 00 00 16 02 29 02
Op End
Op LoadFromFV
SetupUtilityApp
Op Exec
Based on previous SREP usage experiences, when the process runs successfully, it forces entry into the BIOS interface. According to my understanding and reviewing the SREP log files, it seems I couldn’t find the SetupUtilityApp.
Even after reviewing each part of the BIOS with UEFITool, I didn’t have enough knowledge or capability to identify the BIOS startup program for this version.
So, I basically failed completely.
It’s fine. You’ve tried your best. 3 years back I failed too.
Sadly, I haven’t made any progress on this request since then. Nothing has changed except me being now able to communicate in english better. A solution to the request is still yet to be found.
Here are the main showstoppers If you are trying to access more advanced part of the bios, or change variables without rewriting the memory chip completely.
- Specific nvram stores are protected.
- intel flash tool is locked by software policy.
- The runtime patcher is not effective for AMI (even if you find the startup program).
This is not the single case I supervised where bios is so secure. I tried plenty of things before ending up with feeling that everything was useless.
IMO, all that’s left is to do device disassembly and write memory chip directly.
If bios is boot guard protected, your options are limited to changing setup defaults.
Thank you very much for your suggestion! In that case, I’ll buy a non-disassembly programmer to give it a try. It’s very cheap, and I hope I won’t end up damaging my motherboard, haha!