I have 2 Optiplex 7040 Micro which serve me as workers in a Proxmox cluster. Both came with AMT disabled, and I followed the procedure outline here imgurDOTcom/gallery/Mh9Jz to re-enable it with success, after which i updated the bios, and everything worked great. I bought a 3rd 7040 used system which was a bit customized (Owner and asset tag), removed them, and then (maybe stupidly?) updated the bios. Then i proceeded with AMT enablement, which went as usual, except for the fact after fptw64 -greset, the system would take a long while (more than 3 minutes) to shutdown the white LED. I removed the power, and the system booted, but the MEBx prompt was nowhere to be seen. Thinking i have maybe flashed the wrong (original?) .bin file, I re-dumped, and put it into FIT. I was greeted by a warning
and the AMT settings still being disabled. I re-enabled them and set the proper flash settings, but upon build it errors out with
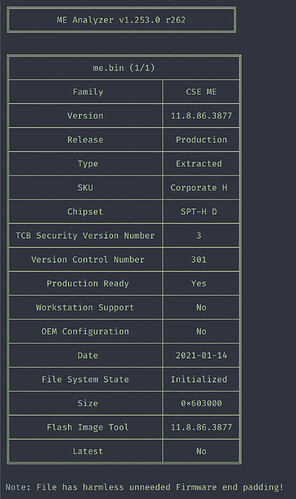
This was done using CSME System Tools v11 r42
I’ve referenced this thread wwwDOTwin-raidDOTcom/t3950f39-Optiplex-Intel-FIT-Build-Error.html and I seem to have access to an uncorrupted dump of me.bin. That said, I’m also looking at the xml that FIT is building, and am not sure where the problem lies. Does FIT even need to have a bin file to construct one, or is the XML itself enough?
At any rate, if worst comes to worst, could someone help me with fixing this? I’m looking at the Cleanup guide and it’s so big I don’t even know where to begin. I’m not really a windows/gui guy ![]()
I’m attaching my dumped me.bin, the generated XML and the outputs of meinfo --verbose and meanalyzer, hoping that @plutomaniac will see this and help me out ![]() I’m not really a windows guy, I work with Linux day-to-day and haven’t used in any great capacity since windows XP
I’m not really a windows guy, I work with Linux day-to-day and haven’t used in any great capacity since windows XP ![]()
Edit: I’ve dumped a me.bin from one of my working nodes, and got the exact same result. And I’m wondering - can I just flash me.bin from one of my amt-enabled machines to this new one? They are on the same bios and ME versions. Will this work?
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
166
167
168
169
170
171
172
173
174
175
176
177
178
179
180
181
182
183
C:\Users\movi\Downloads\CSME System Tools v11 r42\MEInfo\WIN64>MEInfoWin64.exe -verbose
Intel(R) MEInfo Version: 11.8.86.3909
Copyright(C) 2005 - 2020, Intel Corporation. All rights reserved.
Windows OS Version : 10.0
FW Status Register1: 0x94000245
FW Status Register2: 0x00F60506
FW Status Register3: 0x00000430
FW Status Register4: 0x00684000
FW Status Register5: 0x00001F01
FW Status Register6: 0x47C00BC9
CurrentState: Normal
ManufacturingMode: Disabled
FlashPartition: Valid
OperationalState: CM0 with UMA
InitComplete: Complete
BUPLoadState: Success
ErrorCode: No Error
ModeOfOperation: Normal
SPI Flash Log: Not Present
FPF HW Source value: Original FPF HW Fuse Bank
ME FPF Fusing Patch Status: ME FPF Fusing patch NOT required
Phase: ROM/Preboot
ICC: Valid OEM data, ICC programmed
ME File System Corrupted: No
PhaseStatus: AFTER_SRAM_INIT
FPF and ME Config Status: Match
FW Capabilities value is 0x31111140
Feature enablement is 0x11111140
Platform type is 0x42220422
No Intel Wireless device was found
Intel(R) ME code versions:
Table Type 85 ( 0x 55 ) found, size of 0 (0x 00 ) bytes
BIOS Version 1.20.2
Table Type 85 ( 0x 55 ) found, size of 0 (0x 00 ) bytes
Table Type 0 ( 0x 00 ) found, size of 53 (0x 35 ) bytes
Table Type 1 ( 0x 01 ) found, size of 74 (0x 4A ) bytes
Table Type 2 ( 0x 02 ) found, size of 62 (0x 3E ) bytes
Table Type 3 ( 0x 03 ) found, size of 52 (0x 34 ) bytes
Table Type 11 ( 0x 0B ) found, size of 78 (0x 4E ) bytes
Table Type 12 ( 0x 0C ) found, size of 29 (0x 1D ) bytes
Table Type 15 ( 0x 0F ) found, size of 37 (0x 25 ) bytes
Table Type 25 ( 0x 19 ) found, size of 11 (0x 0B ) bytes
Table Type 32 ( 0x 20 ) found, size of 22 (0x 16 ) bytes
Table Type 34 ( 0x 22 ) found, size of 19 (0x 13 ) bytes
Table Type 36 ( 0x 24 ) found, size of 18 (0x 12 ) bytes
Table Type 7 ( 0x 07 ) found, size of 29 (0x 1D ) bytes
Table Type 4 ( 0x 04 ) found, size of 120 (0x 78 ) bytes
Table Type 16 ( 0x 10 ) found, size of 25 (0x 19 ) bytes
Table Type 17 ( 0x 11 ) found, size of 99 (0x 63 ) bytes
Table Type 19 ( 0x 13 ) found, size of 33 (0x 21 ) bytes
Table Type 8 ( 0x 08 ) found, size of 35 (0x 23 ) bytes
Table Type 9 ( 0x 09 ) found, size of 24 (0x 18 ) bytes
Table Type 20 ( 0x 14 ) found, size of 37 (0x 25 ) bytes
Table Type 27 ( 0x 1B ) found, size of 24 (0x 18 ) bytes
Table Type 28 ( 0x 1C ) found, size of 41 (0x 29 ) bytes
Table Type 177 ( 0x B1 ) found, size of 14 (0x 0E ) bytes
Table Type 178 ( 0x B2 ) found, size of 126 (0x 7E ) bytes
Table Type 208 ( 0x D0 ) found, size of 35 (0x 23 ) bytes
Table Type 210 ( 0x D2 ) found, size of 14 (0x 0E ) bytes
Table Type 216 ( 0x D8 ) found, size of 31 (0x 1F ) bytes
Table Type 218 ( 0x DA ) found, size of 253 (0x FD ) bytes
Table Type 218 ( 0x DA ) found, size of 241 (0x F1 ) bytes
Table Type 218 ( 0x DA ) found, size of 43 (0x 2B ) bytes
Table Type 220 ( 0x DC ) found, size of 24 (0x 18 ) bytes
Table Type 221 ( 0x DD ) found, size of 21 (0x 15 ) bytes
Table Type 222 ( 0x DE ) found, size of 18 (0x 12 ) bytes
Table Type 130 ( 0x 82 ) found, size of 22 (0x 16 ) bytes
MEBx Version 11.0.0.0010
GbE Version 0.8
Vendor ID 8086
PCH Version 31
FW Version 11.8.86.3877 H
Security Version (SVN) 3
LMS Version 2130.1.16.4
MEI Driver Version 2120.100.0.1085
Wireless Hardware Version Not Available
Wireless Driver Version Not Available
FW Capabilities 0x31111140
Intel(R) Capability Licensing Service - PRESENT/ENABLED
Protect Audio Video Path - PRESENT/ENABLED
Intel(R) Dynamic Application Loader - PRESENT/ENABLED
Service Advertisement & Discovery - NOT PRESENT
Intel(R) NFC Capabilities - NOT PRESENT
Intel(R) Platform Trust Technology - PRESENT/DISABLED
Re-key needed False
Platform is re-key capable True
TLS Disabled
Last ME reset reason Global system reset
Local FWUpdate Enabled
BIOS Config Lock Enabled
GbE Config Lock Enabled
Get flash master region access status...done
Host Read Access to ME Disabled
Host Write Access to ME Disabled
Get EC region access status...done
Host Read Access to EC Disabled
Host Write Access to EC Disabled
Protected Range Register Base #0 0x0
Protected Range Register Limit #0 0x0
Protected Range Register Base #1 0x0
Protected Range Register Limit #1 0x0
Protected Range Register Base #2 0x0
Protected Range Register Limit #2 0x0
Protected Range Register Base #3 0x0
Protected Range Register Limit #3 0x0
Protected Range Register Base #4 0x0
Protected Range Register Limit #4 0x0
SPI Flash ID 1 20BA18
SPI Flash ID 2 Unknown
BIOS boot State Post Boot
OEM ID 68853622-eed3-4e83-8a86-6cde315f6b78
Capability Licensing Service Enabled
OEM Tag 0x00000000
Slot 1 Board Manufacturer 0x00001028
Slot 2 System Assembler 0x00000000
Slot 3 Reserved 0x00000000
M3 Autotest Enabled
C-link Status Enabled
Independent Firmware Recovery Disabled
EPID Group ID 0x1F9F
Retrieving Variable "LSPCON Port Configuration"
LSPCON Ports None
Retrieving Variable "eDP Port Configuration"
5K Ports None
OEM Public Key Hash FPF A53EF0C178D288B02E61FD71FC31874E89F041FE9332BA2A787A97F7146FB06C
Retrieving Variable "OEM Public Key Hash"
OEM Public Key Hash ME A53EF0C178D288B02E61FD71FC31874E89F041FE9332BA2A787A97F7146FB06C
ACM SVN FPF 0x2
KM SVN FPF 0x0
BSMM SVN FPF 0x0
GuC Encryption Key FPF 0000000000000000000000000000000000000000000000000000000000000000
Retrieving Variable "GuC Encryption Key"
GuC Encryption Key ME 0000000000000000000000000000000000000000000000000000000000000000
FPF ME
--- --
Force Boot Guard ACM Enabled
Retrieving Variable "Force Boot Guard ACM Enabled"
Enabled
Protect BIOS Environment Enabled
Retrieving Variable "Protect BIOS Environment Enabled"
Enabled
CPU Debugging Enabled
Retrieving Variable "CPU Debugging"
Enabled
BSP Initialization Enabled
Retrieving Variable "BSP Initialization"
Enabled
Measured Boot Enabled
Retrieving Variable "Measured Boot Enabled"
Enabled
Verified Boot Enabled
Retrieving Variable "Verified Boot Enabled"
Enabled
Key Manifest ID 0xF
Retrieving Variable "Key Manifest ID"
0xF
Enforcement Policy 0x3
Retrieving Variable "Error Enforcement Policy"
0x3
PTT Enabled
Retrieving Variable "Intel(R) PTT Supported"
Enabled
PTT Lockout Override Counter 0x0
EK Revoke State Not Revoked
PTT RTC Clear Detection FPF 0x0
me.bin.zip (3.65 MB)