Let’s continue the party! If you’ve read the two threads I just created you already know about that I’m trying to accomplish, but for those who didn’t I’d like to unlock the advanced section of the setup utility in my laptop, an Acer Aspire A515-57 with an Alder Lake-U processor.
There’s no rush, because I won’t be able to test anything until I get the hardware I need, I mean, I could probably do it now anyway creating some dodgy adapter; I’m crazy, but not that crazy haha.
So, scouring the forum and some others I came to the realization that for Insyde firmware, at least prior to Alder Lake, the interesting place to poke around is the body of the SetupUtility, a DXE driver it seems (still getting acquainted with the naming and overall flow of UEFI).
My system currently has version 1.15 of the firmware with the latest being 1.18, I extracted them all to check for changes and while in 1.16 that particular binary only changed the version string, 1.18 changed some other things; because I won’t update for now, I decided to stick to 1.15 and tinker with it (I’ll be uploading the relevant EFI file in case any of you wants to poke around).
The idea behind the creation of this thread is to get a general handle on how to proceed, perhaps some pointers to useful references, blog posts, etc. or even a generalized version on the workflow you modders usually do when it comes to these things.
I will be editing or amending the thread to add references to what I’ve been reading and what I find useful through the journey, and also what I stumble upon. For example, so far I learned that the basic structure of those files are PE64 (or a lite version of it?), and the machine instructions are those of the computer itself (so x86 for me).
Disassembling the file and making sense out of it is where the tricky part is, not only because it is assembly, but the whole thing seems convoluted to me. My initial exploration led me to:
- IDA (Pro?)
- Ghidra
- Radare2
The latter is terminal only, seems daunting to get into it to be honest, Ghidra is free and IDA has a free version that (maybe?) could work because it supports pe64, more on that later. Those are reverse engineering tools, or collection of tools capable of analizing the structure of a file and showing the assembly listing. They can also create some sort of C pseudocode, but without labeling that it is you get an obfuscated version of what’s going on in assembly (I’m talking from my knowledge level, maybe it’s just me that I’m thick).
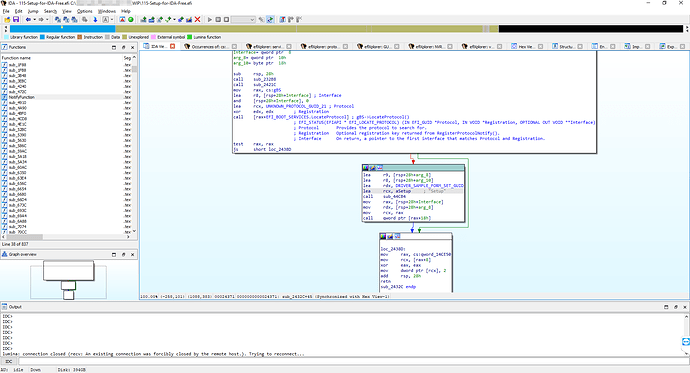
Anyway, those general applications can be extended through plugins, I don’t know if the seasoned modders use them, but I am trying my luck with IDA and I found the efiXplorer plugin most useful to at least try to get some common things tagged already. There are proprietary things added by those behind Insyde, but since they have to follow UEFI parts of it are standard. For Ghidra I found ghidra-firmware-utils that could be interesting, but when I tried opening Ghidra I was a bit overwhelmed (also in IDA, like damn… not my area by a long shot).
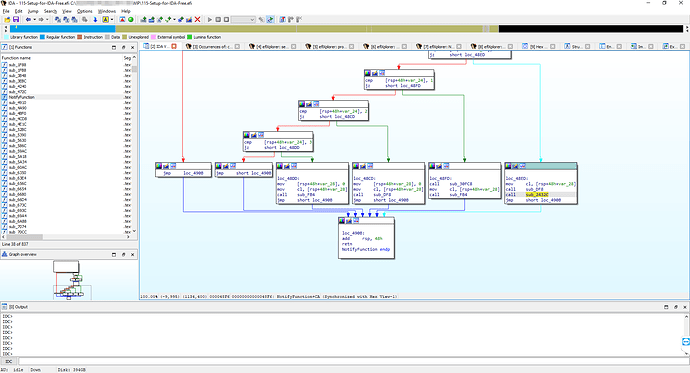
Traversing, or trying to traverse through it all I have found that from the NotifyFunction theres a subroutine that could be related to the SetupUtility itself, but I haven’t located that one yet:
And, of course, so far I know 0 about modding firmware or unlocking things. I’m guessing that at some point there will be one or several tests to assess whether the advanced UI is to be shown (JZ or JNZ) which would need to be reversed, but that’s about all I know.
With the whole thing about Intel locking undervoling, or overclocking areas, it may not be as simple, but hey, where’s the fun in that haha.
I noticed that the one of the 4 microcodes that ship with the firmware was updated in 1.18 too, but I guess it’s not as simple as downloading it (from the Linux distribution of it maybe) and replacing the file; that’s secondary though, it’s just that UEFITool reported there being microcode in the BIOS file.
And ME, which in this machine I don’t know to which extent it’s being used, but for that the easiest thing would probably be replacing the firmware images through FIT and rebuilding something flashable. I bet there are all kinds of hashes, and most likely also public keys and signatures… but let’s not get demoralized, little by little, hopefully something will come of it ![]()
That’s all for now! Thank you for reading through this, it is appreciated!
SetupUtility section image body (A515-57 v1.15).rar (284.3 KB)