Download Link: https://dl.dropboxusercontent.com/u/7372…d5p_f8n_mod.zip
The brief How-tos are for AWARD BIOSes and mainly specific to this mod,
but i hope others will also find it useful in other scenarios.
Note that this mod is intact in most if not all aspects possible and thus
things I wasn’t sure about are not forced to get managed and are not included at all.
The mod is behaving as it should (I’m running this on my live system) and this way you can (should) flash it
with the BIOS built-in QFlash, but of course first make sure your current one is backed up (see later).
Module Modifications
RAID750.BIN 3.0.1540.59 → 3.2.1540.15
UI750.BIN 3.0.1540.59 → 3.2.1540.15
ahci.BIN 3.0.B.0(3.0.A) → 3.1.2.0
JMB59.BIN 1.06.59 → 1.07.28
RTEGPXE.BIN 2.37(only PXE) → 2.54(PXE+RPL)
Original Layout
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
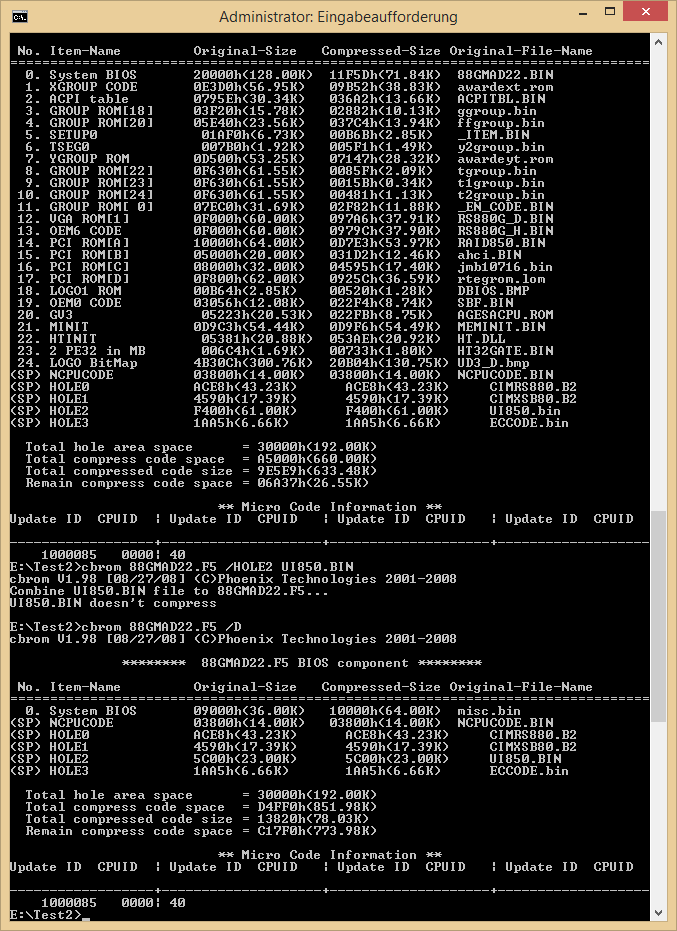
CBROM32_198.EXE V1.98 [08/27/08] (C)Phoenix Technologies 2001-2008
******** M79XTUD5.F8n_Orig BIOS component ********
No. Item-Name Original-Size Compressed-Size Original-File-Name
================================================================================
0. System BIOS 20000h(128.00K)12CC4h(75.19K)m79xtud5.BIN
1. XGROUP CODE 0F1C0h(60.44K)0A2BDh(40.68K)awardext.rom
2. ACPI table 06E1Eh(27.53K)0324Fh(12.58K)ACPITBL.BIN
3. GROUP ROM[18] 04970h(18.36K)03098h(12.15K)ggroup.bin
4. GROUP ROM[20] 05BD0h(22.95K)035F6h(13.49K)ffgroup.bin
5. SETUP0 018A0h(6.16K)00A75h(2.61K)_ITEM.BIN
6. TSEG0 00490h(1.14K)00398h(0.90K)y2group.bin
7. YGROUP ROM 0B680h(45.63K)058F7h(22.24K)awardeyt.rom
8. GROUP ROM[22] 0F630h(61.55K)0083Eh(2.06K)tgroup.bin
9. GROUP ROM[23] 0F630h(61.55K)0015Bh(0.34K)t1group.bin
10. GROUP ROM[24] 0F630h(61.55K)0015Ch(0.34K)t2group.bin
11. GROUP ROM[ 0] 08470h(33.11K)0313Eh(12.31K)_EN_CODE.BIN
12. PCI ROM[A] 0F400h(61.00K)097D9h(37.96K)RAID750.BIN
13. PCI ROM[B] 05200h(20.50K)03382h(12.88K)ahci.BIN
14. OEM3 CODE 0C000h(48.00K)0704Ch(28.07K)ahci.DLL
15. PCI ROM[C] 07A00h(30.50K)04479h(17.12K)JMB59.BIN
16. PCI ROM[D] 0C800h(50.00K)0711Eh(28.28K)RTEGPXE.LOM
17. OEM0 CODE 034F6h(13.24K)0265Bh(9.59K)SBF.BIN
18. GV3 05223h(20.53K)022FBh(8.75K)AGESACPU.ROM
19. MINIT 0DE53h(55.58K)0DE7Bh(55.62K)MEMINIT.BIN
20. HTINIT 05381h(20.88K)053AEh(20.92K)HT.DLL
21. 2 PE32 in MB 006BDh(1.68K)006ECh(1.73K)HT32GATE.BIN
22. OEM1 CODE 0A400h(41.00K)0A428h(41.04K)09561117.BIN
23. LOGO BitMap 4B30Ch(300.76K)0E56Fh(57.36K)FXT_UD5P.BMP
(SP) NCPUCODE 03800h(14.00K)03800h(14.00K)NCPUCODE.BIN
(SP) HOLE0 4D38h(19.30K) 4D38h(19.30K)CIMRD790.B2
(SP) HOLE1 2FE8h(11.98K) 2FE8h(11.98K)CIMSB700.B2
(SP) HOLE2 DC00h(55.00K) DC00h(55.00K)UI750.BIN
(SP) HOLE3 E8Dh(3.64K) E8Dh(3.64K)ECCODE7.BIN
Total hole area space = 30000h(192.00K)
Total compress code space = A4000h(656.00K)
Total compressed code size = 840F5h(528.24K)
Remain compress code space = 1FF2Bh(127.79K)
** Micro Code Information **
Update ID CPUID | Update ID CPUID | Update ID CPUID | Update ID CPUID
------------------+--------------------+--------------------+-------------------
1000085 00001040|
Mod Layout
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
CBROM32_198.EXE V1.98 [08/27/08] (C)Phoenix Technologies 2001-2008
******** M79XTUD5.F8n_RAID3.2.1540.15_AHCI3.1.2.0_JMB36X1.07.28_RTPXERPL2.54_NCPUCODE_ITEM.BIN BIOS component ********
No. Item-Name Original-Size Compressed-Size Original-File-Name
================================================================================
0. System BIOS 20000h(128.00K)12CC4h(75.19K)m79xtud5.BIN
1. XGROUP CODE 0F1C0h(60.44K)0A2BDh(40.68K)awardext.rom
2. ACPI table 06E1Eh(27.53K)0324Fh(12.58K)ACPITBL.BIN
3. GROUP ROM[18] 04970h(18.36K)03098h(12.15K)ggroup.bin
4. GROUP ROM[20] 05BD0h(22.95K)035F6h(13.49K)ffgroup.bin
5. SETUP0 018A0h(6.16K)00A75h(2.61K)_ITEM.BIN
6. TSEG0 00490h(1.14K)00398h(0.90K)y2group.bin
7. YGROUP ROM 0B680h(45.63K)058F7h(22.24K)awardeyt.rom
8. GROUP ROM[22] 0F630h(61.55K)0083Eh(2.06K)tgroup.bin
9. GROUP ROM[23] 0F630h(61.55K)0015Bh(0.34K)t1group.bin
10. GROUP ROM[24] 0F630h(61.55K)0015Ch(0.34K)t2group.bin
11. GROUP ROM[ 0] 08470h(33.11K)0313Eh(12.31K)_EN_CODE.BIN
12. PCI ROM[A] 0E800h(58.00K)0C4B2h(49.17K)RAID750.BIN
13. PCI ROM[B] 06600h(25.50K)03A38h(14.55K)ahci.BIN
14. OEM3 CODE 0C000h(48.00K)0704Ch(28.07K)ahci.DLL
15. PCI ROM[C] 08000h(32.00K)046B3h(17.67K)JMB36X.BIN
16. PCI ROM[E] 07A00h(30.50K)03B55h(14.83K)DUMMY.DUM
17. OEM0 CODE 034F6h(13.24K)0265Bh(9.59K)SBF.BIN
18. GV3 05223h(20.53K)022FBh(8.75K)AGESACPU.ROM
19. MINIT 0DE53h(55.58K)0DE7Bh(55.62K)MEMINIT.BIN
20. HTINIT 05381h(20.88K)053AEh(20.92K)HT.DLL
21. 2 PE32 in MB 006BDh(1.68K)006ECh(1.73K)HT32GATE.BIN
22. OEM1 CODE 0A400h(41.00K)0A428h(41.04K)09561117.BIN
23. LOGO BitMap 4B30Ch(300.76K)0E56Fh(57.36K)FXT_UD5P.BMP
24. PCI ROM[D] 10000h(64.00K)095A6h(37.41K)RTEGPXE.LOM
(SP) NCPUCODE 03800h(14.00K)03800h(14.00K)NCPUCODE.BIN
(SP) HOLE0 4D38h(19.30K) 4D38h(19.30K)CIMRD790.B2
(SP) HOLE1 2FE8h(11.98K) 2FE8h(11.98K)CIMSB700.B2
(SP) HOLE2 E000h(56.00K) E000h(56.00K)UI750.BIN
(SP) HOLE3 E8Dh(3.64K) E8Dh(3.64K)ECCODE7.BIN
Total hole area space = 30000h(192.00K)
Total compress code space = A4000h(656.00K)
Total compressed code size = 8D69Bh(565.65K)
Remain compress code space = 16985h(90.38K)
** Micro Code Information **
Update ID CPUID | Update ID CPUID | Update ID CPUID | Update ID CPUID
------------------+--------------------+--------------------+-------------------
1000085 00001040|
Notes about Modules:
AGESA module is unchanged (3.7.1.0), as the Motherboard already supports all possible AM3 CPUs.
For Microcode updates see NCPUCODE changes below.
Modified the Decompressor to correctly manage Hole area for UI750.BIN.
DUMMY.DUM module is a fake PCI OROM what will never be invoked (VEN_5678:DEV_1234)
and is merely a pad for the remaining gap between newly updated and Sensitive modules.
The Realtek Boot ROM has RPL support too, but this ROM is designed so that RPL mode is separated
as an additional PCI OROM, so if you really want it, you have to redirect the initialization of the
OROM itself, or just go with the cut-off RPL parts without PXE.
Or even better, you can hook the switching to appear as an additional Setup submenu,
but RPL is probably unlikely to be needed at all, so this would be mostly a waste of time.
_ITEM.BIN Changes
SATA ESP option (for AHCI mode) is Enabled
BIOS Logo defaults always to Disabled
Onchip Ide Channel option is "Show only"
Onchip Ide Channel1 option is "Show only"
PATA Channel Mapping option is "Show only"
Notes about _ITEM.BIN:
These changes are only minor things. ESP (eSATA) is not tested to work and it makes not much sense at all, but hey.
Annoying BIOS Logo will be disabled when selected the "Load BIOS/Optimized Defaults" by default,
but of course it can be enabled/disabled any time later.
I was setting the IDE Channel options non-selectable (show only), because these settings could interfere
with certain AHCI/RAID/IDE setups (see >this AMD SB700/710/750 Register Reference Guide<), so I decided to leave them only as informational fields.
NCPUCODE.BIN Changes
Full List of CPU Microcode Patches:
Date:2008/05/01 CPUID:100F40 PatchID:01000085 -> Unchanged
Date:2010/02/17 CPUID:100FA0 PatchID:010000BF -> Date:2011/10/24 CPUID:100FA0 PatchID:010000DC
Date:2010/03/11 CPUID:100F41 PatchID:010000C6 -> Unchanged
Date:2010/03/11 CPUID:100F62 PatchID:010000C7 -> Unchanged
Date:2010/03/31 CPUID:100F43 PatchID:010000C8 -> Unchanged
Date:2010/03/31 CPUID:100F22 PatchID:010000C9 -> Unchanged
Date:2010/03/31 CPUID:100F20 PatchID:010000CA -> Unchanged
Notes about Microcode Patches:
The Microcode updates except for CPUID 100FA0 are currently all up to date (and probably will stay like this),
despite the fact that utils found around are not able to show some or most of these Patches.
"Newer" AM3 CPUs having CPUID 100FA0 (mostly Phenom II X6 CPUs) will be patched to the 010000DC Microcode,
what is anyway left outdated by Gigabyte at PatchID 010000BF in the original BIOS.
This Microcode update will fix Errata #438, #440 and #573 as per AMD documentation
"Revision Guide for AMD Family 10h Processors, order #41322" and is coming from Linux repositories.
Under Linux this will have no effect, because Linux will (should) patch the CPU to the newest (this) Microcodes,
however at the time of writing Windows 7 is only patching a few CPUs at boot time to some "critical" Microcodes:
2008/05/01 100F20(100F2A) - 01000084
2008/04/30 100F22(100F23) - 01000083
2008/03/06 200F31 - 02000032
This means that 100FA0 CPUs will be "left" at the patch level provided entirely by the BIOS
and thus with the old/original patch 010000BF they would be left vulnerable to the above mentioned 3 issues.
By the newest patch 010000DC here we say goodbye to these vulnerabilities.
Useful Key/Button Shortcuts
-In BIOS main screen CTRL+F1 brings up hidden menu(s). This is an AWARD specific combination.
In this case the hidden menu will show up only one item; the Spread Spectrum option for the SB.
This option can produce bugs in certain scenarios and i'm not sure if this BIOS has the workarounds for fixing it,
probably this is why it is hidden. Details about this can be found in AMD SB700/710/750 BIOS Developer's Guide.
-At boot time Alt+F12 brings up the screen to update the Backup BIOS to the image currently resides in Main BIOS.
-Reverting the Main BIOS to the Backup BIOS; switch off Computer, turn off Power supply/pull Power cable until
Mainboard LEDs are out, press+hold Power button, switch on Power/put back cable until switches off again
(after standard 4secs), Power off/cable out again, wait for LEDs, then Power back.
Push Power button and it should bring up a screen (after the main boot screen) telling,
it will revert the Main BIOS to the image currently in the Backup BIOS.
You can see some end-result photos dumped here: https://www.dropbox.com/sh/w6jte68kqdp3r...U7MzYC2/Results