Hi everyone,
I own a Crucial SSD which supports self-encryption, but needs a BIOS interface to enter the password upon boot. My laptop has it, but my desktop mainboard (MSI Z78 Mpower Max) lacks the ATA security extension. But there is help in form of a PCI expansion ROM: ATA Security eXtension BIOS. As far as I understood it this ROM will replace the original ROM used for PXE booting. I have two network cards as onboard devices: a Atheros LAN adapter and a Intel Centrino WiFi adapter. I already played around with the UBU-toolkit and got some success as it detects both (executed “ubu.bat”) and can read the BIOS file from MSI (UEFItool GUI). The last remaining task is the integration of the ATA expansion ROM into the BIOS. I know a non-UEFI tutorial, but I can’t figure out how to do this with an UEFI BIOS. Can anyone help with some advice and things to look for?
@ Nova:
Welcome at Win-RAID Forum!
Although I have never done such BIOS modification, I suspect, that it may work with an AMI UEFI BIOS by using a rather similar procedure as described within the guide you have linked:
Open the mainboard BIOS with the AMI Aptio UEFI MMTool according to >this< guide. Then search for the "CSMCORE" file and replace the related PCI ROM modules, which are all there. After having checked "Link present" within the "For Option Rom" area, you will see the VendorID and DeviceID of the PCI ROM modules, which are within your BIOS.
Regards
Fernando
To make it short: it works, thank you! As soon as I will get my new SSD I can report if the whole chain works, but the ATA expansion has been successfully flashed and gets called on boot correctly.
Congratulations and thanks for your feedback.
That would be fine, because other visitors of this Forum may benefit from your success.
Got my new SSD (Crucial MX100 512GB) yesterday. I can confirm that everything works almost perfect. There are only two cavecats: You have to run every protected disk in IDE instead of AHCI mode. I have two controllers (6x Intel standard + 2x ASmedia), so I connected it to the ASmedia one and set it to IDE while the Intel controller and attached disks remains in AHCI mode. Second, I had to use my laptop (Asus UX32VD) to set the passwords, the extension BIOS was unable to set one (but it can unlock, which is all I want). From the point of BIOS modding it all worked as you suggested. You first have to configure the extension BIOS as mentioned in my tutorial link and then fuse it into the mainboard BIOS through the AMI Aptio UEFI MMTool as you pointed out in your tutorial. Flashing from the BIOS itself (called “M-Flash”) didn’t work (even with the official BIOS update), so you have to use a bootable USB stick with the AMI flash tool on it. I just downloaded the USB package from MSI, dropped in my modified BIOS file and everything went totally smooth.
Still quite a bunch of work, but after Snowden you can’t be paranoid enough^^. My other drives are all Truecrypt protected, they auto-mount on boot with a batch file and a random long passwords saved on the SSD, which is now secured (although this file is additionally protected by the Win7 file encryption and therefore ultimately by my long Windows logon password, just in case…). Normal hard drives are only taking a performance hit of 10-20%, that’s ok for me, but SSD performance would have been down by about 40-70%, this was not acceptable. Luckily this problem has been solved by new SSDs which encrypt themselves with specialised onboard controllers (called “self encrypting devices” → SEDs), but this requires expensive software (OPAL 2.0 compatible) or the good old ATA password to work.
@ Nova:
Thanks for your feedback after having configured your new 512 GB Crucial MX100 SSD.
It is fine, that everything worked flawlessly.
There is a brandnew SSD tool named "Crucial Storage Executive" available, which may help you to encrypt your new SSD. Please look >here<.
Sadly the tool can only erase the disk. For OPAL compliant encryption you need a small pre-boot OS which is written to a special memory range of the SSD. This OS will be booted before unlock and will ask for the password. It can be freely programmed, so you can implement network connections and advanced management features. Therefore almost all products are targeted at business customers, which drives the prices up. The ATA password is the only free option at the moment.
Can confirm it works fine with ASUS P8H77-M Pro (AMI BIOS) now have ATA Security eXtension, after some trouble with flashing bios it works now. Now it is possible to use a self-encrypted SSD (like Samsung Evo/Pro 840/850) and unlock it with ATA-Password.
How to:
1. (not necessarily) update your BIOS/UEFI to newest version with ASUS tools. Test if everything is working after update.
2. Now make a backup of your BIOS/UEFI by using the read option of ASUS flash-tool, AFUDOS or AFUWIN. If you download BIOS-file from ASUS website, it is not complete, because some device-specific data (serial number, mac address, …) are not in this file. But if you read BIOS from your Mainboard, it contains this important device-specific data. If you flash with original ASUS flash-tool, the device-specific data are inserted automatically. If you flash with afudos, afuwin or external programmer, you have to insert your device-specific data manually with FB44Editor tool. ASUS cap-files size is 8194 KB, because the first 2048 Bytes (2KB) is a capsule header, these 2048 Bytes will be automatically removed and not flashed to BIOS if you flash with original ASUS flash-tool. I dont know why this header is needed, for some security checks and other stuff. If you read BIOS with AFUDOS/AFUWIN or external programmer it will be 8192 KB, without capsule header. Original ASUS flash-tools will not accept files without capsule header to write it to BIOS, you will get an error “security check failed”.
After you have successfully made a backup of your BIOS, please save it on several varios places like usb-pen or sd-card.
3. Now download ATASX (http://www.fitzenreiter.de/ata/ata_eng.htm), you need the file ATASX.ROM and BROMCFG.EXE. Readme is included. For configurating ATASX you also need Vendor ID and Device ID from your onboard network card. Most mainboard do have Realtek network cards onboard. Vendor ID for Realtek is allways 10EC and Device ID varies, you can see it in Windows Device Manager → Network Devices → Realtek → Details → Hardware ID’s. In my case Device ID is 8168. Typ is allways 020000. Bromcfg only works in DOS, so you will need the free tool DOSBOX, in DOSBOX you can mount your ATASX directory to virtual drive c: with "mount c d:\path_to_my_atasx_directory", with command “c:” you then swith to your virtual drive c: and with “dir” you can list your directory and start bromcfg with “bromcfg.exe” command. After you did followed all steps in bromcfg, you will get a atasx.rom file ready for your mainboard.
4. Now you have to insert atasx.rom into your backuped mainboard BIOS file (8192 KB).
Use this tutorial from Fernando, search for the “CSMCORE” file and replace the PCI opROM which has Vendor ID 10EC (only if you have Realtek network card, otherwise Vendor ID is not 10EC) with your atasx.rom file.
→ [Guide] Manual AMI UEFI BIOS Modding
Your network card will still working, you only replace the Boot from Network option. Save now the BIOS as modified.rom or modified.bin (8192 KB).
(!) With tool FD44Edit (https://github.com/LongSoft/FD44Editor/releases) you can check if your device-specific data is contained in your modified.bin file (serial number, mac, …). If not, you can open your original BIOS backup file, then click to save to image file and select your modified.bin file. Your device specific data will be transfered from original backup to your modified BIOS.
5. Now you have to flash this modified.rom file in your mainboard BIOS-chip.
→ [Guide] How to flash a modded ASUS or ASRock AMI UEFI BIOS
But because of security checks it was not possible for me to flash it internal with AFUDOS/AFUWIN/ASUS EZ Flash 2. So a external programmer is needed to flash a Winbond 25Q64 chip. Chip is in a sockel, so it can easy be removed from mainboard and placed back again. The cheapest external USB programmer CH341A costs 3 USD (Ebay, Amazon).
6. After you have succefully flashed your modified BIOS, you should enter BIOS Setup and enable Network Boot Option. And for SATA enable IDE, not AHCI (!) because ATASX only support IDE-Mode. The next time you boot your computer, ATASX screen should be displayed and if you press CTRL+S you will enter ATASX settings.
About IDE vs AHCI mode performance for SSD:
→ http://archive.benchmarkreviews.com/inde…=1&limitstart=3
No perfomance loss in writing data to SSD, some few perfomance loss in reading data from SSD. But if you do not operate a server and every nanosecond is important, you will not notice any perfomance collapce. This is a bridging solution. In few years you can buy then a new mainboard with fast M.2 and not SATA, but buy not again ASUS mainboard. They have very bad support. I asked for 3 months about implementation of ATA-Password to their BIOS, first they told me to wait some weeks, then they not even answer anymore to emails. ASROCK belongs to ASUS, but they support is the best i ever seen. Not only ATA-Password, they have implemented other things for my needs in their BIOS. Allways 24-48h after my email, ASROCK support send me a modified BIOS. Only one time they did not what i asked for, ATA-Password is set on ASrock only in High-Mode not in Maximum-Mode. In High-Mode somebody with Master-Password can descript the SDD, and a Master-Password could be set automatically by Mainboard, who knows. In Maximum-Mode even with Master-Password nobody can descript it, only with User-Password, which is set by User. So i have to put my SSD first time to my notebook to set the ATA-Password, because notebook set password to Maximum-Mode.
Modified BIOS v1505 with build-in ATASX for ASUS P8H77M-Pro is attached (8192 KB) to this posting. Do not flash it before you have not put your SN, MAC, UUID inside this modified BIOS with tool FD44Editor.exe
FD44Editor_0.9.2_win.zip (4.31 MB)
p8h77-m-pro-asus-1505_body_atasx.zip.001.zip (1.48 MB)
Another problem:
If connect a new SSD and want to set ATA-password, its not possible, because mainboard does “ata security freeze” at boot. This is ok, it is preventing that somebody (virus) can set a random password after boot. But because of this, you can not set a ATA-Password in ATASX, as drive is “ata security frozen” by mainboard.
Experiment I (tested, does not work):
So i placed my SSD first in my Thinkpad notebook and set a user-ata-password in BIOS.
But problem: it seems Thinkpad notebook does not use ASCII for password. It uses scancodes. So if you type a password “mysuperpassword” - then password is not “mysuperpassword” (!)
If you connect this drive to another computer than Thinkpad and type “mysuperpassword” you will get an error “wrong password”. The same error if try to unlock with ASUS P8H77M-Pro with ATASX. ATASX recognizes SSD and tells it is locked with USER-Password in Maximum-Mode and is promt for password input, but if i type “mysuperpassword” i get error “wrong password”. If i place SSD back to Thinkpad and type “mysuperpassord” then it works.
So there is a problem to SET a ata-password, because of “ata security freeze” by Asus Bios.
I found a tool to unlock drive with Lenovo/IBM Thinkpad ata-password (so you could set another ASCII password), but because it does only work with Linux, i could not test it yet:
→ https://github.com/jethrogb/lenovo-password
→ https://jbeekman.nl/blog/2015/03/lenovo-…d-hdd-password/
Experiment II (tested, does work):
I have entered now a User-Password in a ASrock Mainboard (ASrock support will send modified BIOS with ATA-Security enabled if you ask them). And ASrock uses ASCII for password, no damn scancode like Lenovo/IBM Thinkpad. Then went to ATASX setup menu on ASUS P8H77-M (ssd status: high, locked, not frozen) and it was possible to unlock the drive with my User-Password (status: high, unlocked, not frozen). In ATASX i did set User-Password again, but in Maximum-Mode (status: maximum, unlocked, not frozen), because ASrock mainboards set User-Password to High-Mode only. Maximum-Mode is more secure, as nobody can decrypt the drive, even with a known Master-Password. In High-Mode somebody who knows the default Master-Password, can unlock drive and dont need your secret User-Password.
So Problem is: somebody who doesnt have a second computer which is capable to set a ATA-Password, will not be able to use ATASX, as its not possible to set ATA-Password with ATASX first time, because mainboard freezes all security commands of the SSD. If password is already set to SSD, than no problem to change it with ATASX.
But maybe you can use Linux or DOS Live-Boot-CD/USB-Pen to set password, too. So a second computer is not needed.
How to:
1. switch off pc, disconnect SATA cable from SSD
2. swich on pc and boot a Linux Live-CD/USB-Pen or DOS Live-CD/USB-Pen.
3. now connect SATA cable to SSD again (so drive should be not frozen now, because usually ata-security-freeze is made at bios boot-process)
4. in Linux use “hdparm” tool and in DOS use “atapwd” Tool to set ATA-Password.
Maybe you can also try a SATA/USB adapter with Linux Live-CD, as USB-drives should stay security-unfrozen.
Links:
linux live-cd: → http://www.knoppix.org/
hdparm options: → http://man7.org/linux/man-pages/man8/hdp…20Feature%20Set
atapwd boot-cd: → http://www.ultimatebootcd.com/
Experiment III (tested, does work):
1. Download Gparted Linux Live CD ISO or USB version → http://gparted.org/livecd.php
2. In mainboard BIOS set SATA to ACHI-Mode, after this set SATA-Port at which your SSD is connected to “Hot-Plug”-Mode. In IDE-Mode the “Hot-Plug”-Mode is not possible, and mainboard disables all SATA-Ports at which no device is connected at boot process. So if you disconnect SSD before booting to prevent it to be security-frozen, SATA-Port will be disabled and if you connect SSD again after boot, the SSD will not be recognized by OS (Windows, Linux). Only if “Hot-Plug” is enabled in BIOS, then SATA-Ports without connected devices will not be disabled and will be still available after boot.
3. Switch off PC, disconnect SATA cable from SSD
4. Swich on PC and boot from Linux Live-CD or USB-Pen
5. As soon as you see Gparted boot-menu, connect SATA cable to SSD again (so drive should be not security-frozen now, because usually ata-security-freeze is only made at bios boot-process). Now let Gparted load and start, if you will asked something while loading, read it and just push ENTER/RETURN button on your keyboard.
6. In Gparted Linux-Desktop, double-click on “Terminal” programm (like CMD in Windows) to start it. You need to know which device-path your SSD does have, in Gparted-Window itself, you can see which device-path belongs to your SSD (e. g. /dev/sda or /dev/sdb)
7. In Terminal-Window type this and then press ENTER button on keyboard:
sudo hdparm --security-mode m --security-set-pass MYPASSWORD /dev/sda
If everything is ok, you should see this message:
/dev/sda
Issuing SECURITY_SET_PASS command, password=“MYPASSWORD”, user=user, mode=max
8. Now go to mainboard BIOS and set SATA Mode back from AHCI to IDE, so ATASX can see your drive. Finished!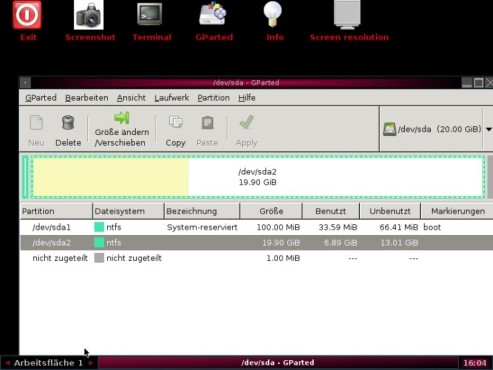
Experiment IV (tested, does work):
1. Like Experiment III above, but with USB-SATA enclosure/adapter.
2. Place your SSD in a ‘SATA to USB adapter’ and boot PC from ‘Gparted Linux Live’ CD-ISO or USB pen → http://gparted.org/livecd.php
3. In Terminal-Window you type this and then press ENTER button:
sudo hdparm --security-mode m --security-set-pass MYPASSWORD /dev/sda
If everything is ok, you should see this message:
/dev/sda
Issuing SECURITY_SET_PASS command, password=“MYPASSWORD”, user=user, mode=max
hi!
better method than usign ata password is Opal on Self Enrypting Drives.
there is new free software to unlock this mechanis. I tried it and is working good
[Tool] sedutil - Self encrypting drive software to handle TCG OPAL 2.0-compliant Self-Encrypting Drives
Does it works with every OS like: Linux, Windows, MacOS, … ?
There are two version of command utility for Linux and Windows. And you have to have opal compatible drive. Im testing it on my Samsung 850 Pro and it works very good. Only cons right now is you cannot hibernate or suspend system as this is not supported right now.
Some off topic:
I am searching for a Windows tool to send ATA-Security commands.
I need to unlock and lock USB-Drive (sata-drive in usb-enclosure).
In Linux there is no problem to unlock/lock USB-Drive with command “hdparm”.
But i can not find any tool for Windows. Here is some code for this, if we have programmer here, maybe somebody can try this?
http://stackoverflow.com/questions/31960…0xf2-in-windows
http://stackoverflow.com/questions/50709…vice-in-windows
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
166
167
168
169
170
171
172
173
174
175
176
177
178
179
180
181
182
183
184
185
186
187
188
189
190
191
192
193
194
195
196
197
198
199
200
201
202
203
204
205
206
207
208
209
210
211
212
213
214
215
216
217
218
219
220
221
222
223
224
225
226
227
228
229
230
231
232
233
234
235
236
237
238
239
240
241
242
243
244
245
246
247
248
249
250
251
252
253
254
255
256
257
258
259
260
261
262
263
264
265
266
267
268
269
270
271
272
273
274
275
276
277
278
279
280
281
282
283
284
285
286
287
288
289
290
291
292
293
294
295
296
297
298
299
300
301
302
303
304
305
306
307
308
309
310
311
312
313
314
315
316
317
318
319
320
321
322
323
324
325
326
327
328
329
330
331
332
333
334
335
336
337
338
339
340
341
342
343
344
345
346
347
348
349
350
351
352
353
354
355
356
357
358
359
360
361
362
363
364
365
366
367
368
369
370
371
372
373
374
375
376
377
// Sending ATA commands directly to device in Windows?
// http://stackoverflow.com/questions/5070987/sending-ata-commands-directly-to-device-in-windows
#include <Windows.h>
#include <ntddscsi.h> // for ATA_PASS_THROUGH_EX
#include <iostream>
// I have copied the struct declaration from
// "IDENTIFY_DEVICE_DATA structure" http://msdn.microsoft.com/en-us/library/windows/hardware/ff559006(v=vs.85).aspx
// I think it is better to include the suitable header (MSDN says the header is Ata.h and suggests to include Irb.h)
typedef struct _IDENTIFY_DEVICE_DATA {
struct {
USHORT Reserved1 :1;
USHORT Retired3 :1;
USHORT ResponseIncomplete :1;
USHORT Retired2 :3;
USHORT FixedDevice :1;
USHORT RemovableMedia :1;
USHORT Retired1 :7;
USHORT DeviceType :1;
} GeneralConfiguration;
USHORT NumCylinders;
USHORT ReservedWord2;
USHORT NumHeads;
USHORT Retired1[2];
USHORT NumSectorsPerTrack;
USHORT VendorUnique1[3];
UCHAR SerialNumber[20];
USHORT Retired2[2];
USHORT Obsolete1;
UCHAR FirmwareRevision[8];
UCHAR ModelNumber[40];
UCHAR MaximumBlockTransfer;
UCHAR VendorUnique2;
USHORT ReservedWord48;
struct {
UCHAR ReservedByte49;
UCHAR DmaSupported :1;
UCHAR LbaSupported :1;
UCHAR IordyDisable :1;
UCHAR IordySupported :1;
UCHAR Reserved1 :1;
UCHAR StandybyTimerSupport :1;
UCHAR Reserved2 :2;
USHORT ReservedWord50;
} Capabilities;
USHORT ObsoleteWords51[2];
USHORT TranslationFieldsValid :3;
USHORT Reserved3 :13;
USHORT NumberOfCurrentCylinders;
USHORT NumberOfCurrentHeads;
USHORT CurrentSectorsPerTrack;
ULONG CurrentSectorCapacity;
UCHAR CurrentMultiSectorSetting;
UCHAR MultiSectorSettingValid :1;
UCHAR ReservedByte59 :7;
ULONG UserAddressableSectors;
USHORT ObsoleteWord62;
USHORT MultiWordDMASupport :8;
USHORT MultiWordDMAActive :8;
USHORT AdvancedPIOModes :8;
USHORT ReservedByte64 :8;
USHORT MinimumMWXferCycleTime;
USHORT RecommendedMWXferCycleTime;
USHORT MinimumPIOCycleTime;
USHORT MinimumPIOCycleTimeIORDY;
USHORT ReservedWords69[6];
USHORT QueueDepth :5;
USHORT ReservedWord75 :11;
USHORT ReservedWords76[4];
USHORT MajorRevision;
USHORT MinorRevision;
struct {
USHORT SmartCommands :1;
USHORT SecurityMode :1;
USHORT RemovableMediaFeature :1;
USHORT PowerManagement :1;
USHORT Reserved1 :1;
USHORT WriteCache :1;
USHORT LookAhead :1;
USHORT ReleaseInterrupt :1;
USHORT ServiceInterrupt :1;
USHORT DeviceReset :1;
USHORT HostProtectedArea :1;
USHORT Obsolete1 :1;
USHORT WriteBuffer :1;
USHORT ReadBuffer :1;
USHORT Nop :1;
USHORT Obsolete2 :1;
USHORT DownloadMicrocode :1;
USHORT DmaQueued :1;
USHORT Cfa :1;
USHORT AdvancedPm :1;
USHORT Msn :1;
USHORT PowerUpInStandby :1;
USHORT ManualPowerUp :1;
USHORT Reserved2 :1;
USHORT SetMax :1;
USHORT Acoustics :1;
USHORT BigLba :1;
USHORT DeviceConfigOverlay :1;
USHORT FlushCache :1;
USHORT FlushCacheExt :1;
USHORT Resrved3 :2;
USHORT SmartErrorLog :1;
USHORT SmartSelfTest :1;
USHORT MediaSerialNumber :1;
USHORT MediaCardPassThrough :1;
USHORT StreamingFeature :1;
USHORT GpLogging :1;
USHORT WriteFua :1;
USHORT WriteQueuedFua :1;
USHORT WWN64Bit :1;
USHORT URGReadStream :1;
USHORT URGWriteStream :1;
USHORT ReservedForTechReport :2;
USHORT IdleWithUnloadFeature :1;
USHORT Reserved4 :2;
} CommandSetSupport;
struct {
USHORT SmartCommands :1;
USHORT SecurityMode :1;
USHORT RemovableMediaFeature :1;
USHORT PowerManagement :1;
USHORT Reserved1 :1;
USHORT WriteCache :1;
USHORT LookAhead :1;
USHORT ReleaseInterrupt :1;
USHORT ServiceInterrupt :1;
USHORT DeviceReset :1;
USHORT HostProtectedArea :1;
USHORT Obsolete1 :1;
USHORT WriteBuffer :1;
USHORT ReadBuffer :1;
USHORT Nop :1;
USHORT Obsolete2 :1;
USHORT DownloadMicrocode :1;
USHORT DmaQueued :1;
USHORT Cfa :1;
USHORT AdvancedPm :1;
USHORT Msn :1;
USHORT PowerUpInStandby :1;
USHORT ManualPowerUp :1;
USHORT Reserved2 :1;
USHORT SetMax :1;
USHORT Acoustics :1;
USHORT BigLba :1;
USHORT DeviceConfigOverlay :1;
USHORT FlushCache :1;
USHORT FlushCacheExt :1;
USHORT Resrved3 :2;
USHORT SmartErrorLog :1;
USHORT SmartSelfTest :1;
USHORT MediaSerialNumber :1;
USHORT MediaCardPassThrough :1;
USHORT StreamingFeature :1;
USHORT GpLogging :1;
USHORT WriteFua :1;
USHORT WriteQueuedFua :1;
USHORT WWN64Bit :1;
USHORT URGReadStream :1;
USHORT URGWriteStream :1;
USHORT ReservedForTechReport :2;
USHORT IdleWithUnloadFeature :1;
USHORT Reserved4 :2;
} CommandSetActive;
USHORT UltraDMASupport :8;
USHORT UltraDMAActive :8;
USHORT ReservedWord89[4];
USHORT HardwareResetResult;
USHORT CurrentAcousticValue :8;
USHORT RecommendedAcousticValue :8;
USHORT ReservedWord95[5];
ULONG Max48BitLBA[2];
USHORT StreamingTransferTime;
USHORT ReservedWord105;
struct {
USHORT LogicalSectorsPerPhysicalSector :4;
USHORT Reserved0 :8;
USHORT LogicalSectorLongerThan256Words :1;
USHORT MultipleLogicalSectorsPerPhysicalSector :1;
USHORT Reserved1 :2;
} PhysicalLogicalSectorSize;
USHORT InterSeekDelay;
USHORT WorldWideName[4];
USHORT ReservedForWorldWideName128[4];
USHORT ReservedForTlcTechnicalReport;
USHORT WordsPerLogicalSector[2];
struct {
USHORT ReservedForDrqTechnicalReport :1;
USHORT WriteReadVerifySupported :1;
USHORT Reserved01 :11;
USHORT Reserved1 :2;
} CommandSetSupportExt;
struct {
USHORT ReservedForDrqTechnicalReport :1;
USHORT WriteReadVerifyEnabled :1;
USHORT Reserved01 :11;
USHORT Reserved1 :2;
} CommandSetActiveExt;
USHORT ReservedForExpandedSupportandActive[6];
USHORT MsnSupport :2;
USHORT ReservedWord1274 :14;
struct {
USHORT SecuritySupported :1;
USHORT SecurityEnabled :1;
USHORT SecurityLocked :1;
USHORT SecurityFrozen :1;
USHORT SecurityCountExpired :1;
USHORT EnhancedSecurityEraseSupported :1;
USHORT Reserved0 :2;
USHORT SecurityLevel :1;
USHORT Reserved1 :7;
} SecurityStatus;
USHORT ReservedWord129[31];
struct {
USHORT MaximumCurrentInMA2 :12;
USHORT CfaPowerMode1Disabled :1;
USHORT CfaPowerMode1Required :1;
USHORT Reserved0 :1;
USHORT Word160Supported :1;
} CfaPowerModel;
USHORT ReservedForCfaWord161[8];
struct {
USHORT SupportsTrim :1;
USHORT Reserved0 :15;
} DataSetManagementFeature;
USHORT ReservedForCfaWord170[6];
USHORT CurrentMediaSerialNumber[30];
USHORT ReservedWord206;
USHORT ReservedWord207[2];
struct {
USHORT AlignmentOfLogicalWithinPhysical :14;
USHORT Word209Supported :1;
USHORT Reserved0 :1;
} BlockAlignment;
USHORT WriteReadVerifySectorCountMode3Only[2];
USHORT WriteReadVerifySectorCountMode2Only[2];
struct {
USHORT NVCachePowerModeEnabled :1;
USHORT Reserved0 :3;
USHORT NVCacheFeatureSetEnabled :1;
USHORT Reserved1 :3;
USHORT NVCachePowerModeVersion :4;
USHORT NVCacheFeatureSetVersion :4;
} NVCacheCapabilities;
USHORT NVCacheSizeLSW;
USHORT NVCacheSizeMSW;
USHORT NominalMediaRotationRate;
USHORT ReservedWord218;
struct {
UCHAR NVCacheEstimatedTimeToSpinUpInSeconds;
UCHAR Reserved;
} NVCacheOptions;
USHORT ReservedWord220[35];
USHORT Signature :8;
USHORT CheckSum :8;
} IDENTIFY_DEVICE_DATA, *PIDENTIFY_DEVICE_DATA;
// Taken from smartmontools
// Copies n bytes (or n-1 if n is odd) from in to out, but swaps adjacents
// bytes.
static void swapbytes(char * out, const char * in, size_t n)
{
for (size_t i = 0; i < n; i += 2) {
out[i] = in[i+1];
out[i+1] = in[i];
}
}
// Taken from smartmontools
// Copies in to out, but removes leading and trailing whitespace.
static void trim(char * out, const char * in)
{
// Find the first non-space character (maybe none).
int first = -1;
int i;
for (i = 0; in[i]; i++)
if (!isspace((int)in[i])) {
first = i;
break;
}
if (first == -1) {
// There are no non-space characters.
out[0] = '\0';
return;
}
// Find the last non-space character.
for (i = strlen(in)-1; i >= first && isspace((int)in[i]); i--)
;
int last = i;
strncpy(out, in+first, last-first+1);
out[last-first+1] = '\0';
}
// Taken from smartmontools
// Convenience function for formatting strings from ata_identify_device
void ata_format_id_string(char * out, const unsigned char * in, int n)
{
bool must_swap = true;
#ifdef __NetBSD__
/* NetBSD kernel delivers IDENTIFY data in host byte order (but all else is LE) */
// TODO: Handle NetBSD case in os_netbsd.cpp
if (isbigendian())
must_swap = !must_swap;
#endif
char tmp[65];
n = n > 64 ? 64 : n;
if (!must_swap)
strncpy(tmp, (const char *)in, n);
else
swapbytes(tmp, (const char *)in, n);
tmp[n] = '\0';
trim(out, tmp);
}
int main(int argc, char* argv[])
{
HANDLE handle = ::CreateFileA(
"\\\\.\\PhysicalDrive0",
GENERIC_READ | GENERIC_WRITE, //IOCTL_ATA_PASS_THROUGH requires read-write
FILE_SHARE_READ,
0, //no security attributes
OPEN_EXISTING,
0, //flags and attributes
0 //no template file
);
if ( handle == INVALID_HANDLE_VALUE ) {
std::cout << "Invalid handle\n";
}
// IDENTIFY command requires a 512 byte buffer for data:
const unsigned int IDENTIFY_buffer_size = 512;
const BYTE IDENTIFY_command_ID = 0xEC;
unsigned char Buffer[IDENTIFY_buffer_size + sizeof(ATA_PASS_THROUGH_EX)] = { 0 };
ATA_PASS_THROUGH_EX & PTE = *(ATA_PASS_THROUGH_EX *) Buffer;
PTE.Length = sizeof(PTE);
PTE.TimeOutValue = 10;
PTE.DataTransferLength = 512;
PTE.DataBufferOffset = sizeof(ATA_PASS_THROUGH_EX);
// Set up the IDE registers as specified in ATA spec.
IDEREGS * ir = (IDEREGS *) PTE.CurrentTaskFile;
ir->bCommandReg = IDENTIFY_command_ID;
ir->bSectorCountReg = 1;
// IDENTIFY is neither 48-bit nor DMA, it reads from the device:
PTE.AtaFlags = ATA_FLAGS_DATA_IN | ATA_FLAGS_DRDY_REQUIRED;
DWORD BR = 0;
BOOL b = ::DeviceIoControl(handle, IOCTL_ATA_PASS_THROUGH, &PTE, sizeof(Buffer), &PTE, sizeof(Buffer), &BR, 0);
if ( b == 0 ) {
std::cout << "Invalid call\n";
}
IDENTIFY_DEVICE_DATA * data = (IDENTIFY_DEVICE_DATA *) (Buffer + sizeof(ATA_PASS_THROUGH_EX));
// Nota Bene: I think some endianness control is needed
char model[40+1];
ata_format_id_string(model, data->ModelNumber, sizeof(model)-1);
char serial[20+1];
ata_format_id_string(serial, data->SerialNumber, sizeof(serial)-1);
char firmware[8+1];
ata_format_id_string(firmware, data->FirmwareRevision, sizeof(firmware)-1);
std::cout << "ModelNumber: " << model << "\n";
std::cout << "SerialNumber: " << serial << "\n";
std::cout << "FirmwareRevision: " << firmware << "\n";
return 0;
}
Hey guys, i realy need some help. This is all new to me but i work my way through it.
I try to add the ATA Security Extension to my Gigabyte GA-990X-Gaming-SLI UEFI Bios. 4MB Rom Size. Last Bios Version was F1.
I loaded the original F1 Bios with mmtool and extractet under CSMCORE the Intel Lan Modul (Link Present “on” and Vendor ID:8086 Device ID:1539) to see how big it was: 68kb
In Dosbox i configurated the ATA Security Extension via: “bromcfg atasx.rom /s68” after finishing the rest i have now a 68kb rom file with the right informations (Vendor ID:8086 Device ID:1539 Type: 020000).
Back in mmtool i go to CSMCORE → replace → browse my 68kb file → Link Present “on” and Vendor ID:8086 Device ID:1539 → replace → save image
Im sure im done but after flashing it,i dont get the modul to work. In the Bios i enable boot on lan / only ide (no ahci) / no full logo on boot show
But the screen goes just black and the mainboard just did a restart. Did i something wrong or did i just dont see something importend?
I would love to try the AHCI BIOS Security Extension but the documentation is almost not present and i have no Linux to configure the rom :((
Answers would be awesome (maybe a pm in German ?? :D)
edit: Its working now. I just did the whole process again and just flashed it and its working this time (changed the timer for cntrl+s to 20sec). Can someone help me to configure the AHCI Security Extension? I have no Linux and im not sure how i have to do it ![]()
That’s my point, guys. I need a tip for an actual energy saving intel-based mini-itx-Board for my new pc with fully enabled ATA-Security with integrated graphics capable of viewing Netflix 4K?