@mbk1969
Thanks for the reply about PCID feature. It is clear.
On my antique AMD W7 platform .NET v4.7, v3.5, v3.0, v2.0 does coexist at the moment. Even .NET v4.7.1 update is properly installed. So, it is OK for .NET components.
However PS2 is installed. So I have to upgrade PS2 → PS3 → PS5. (may be i can found the different PS versions somewhere on MS site ?)
Then may be "Win7-KB319566-x66.zip" (WMF v5.1) will be installable and then may be Ashampoo Tool be working…
@100PIER
According to this page
https://docs.microsoft.com/en-us/powersh…=powershell-5.1
"The installation package for PowerShell comes inside a WMF installer. The version of the WMF installer matches the version of PowerShell; there’s no stand alone installer for Windows PowerShell."
See section “Upgrading existing Windows PowerShell” (links are there)
Thanks,
I have succeed finally, with MS Tech support help, to get WMF v5.1 and PS v5.1 working on W7 SP1 32 bit (safe mode was a necessity to install , and also forget BSOD).
However, Ashampoo tool does not work:
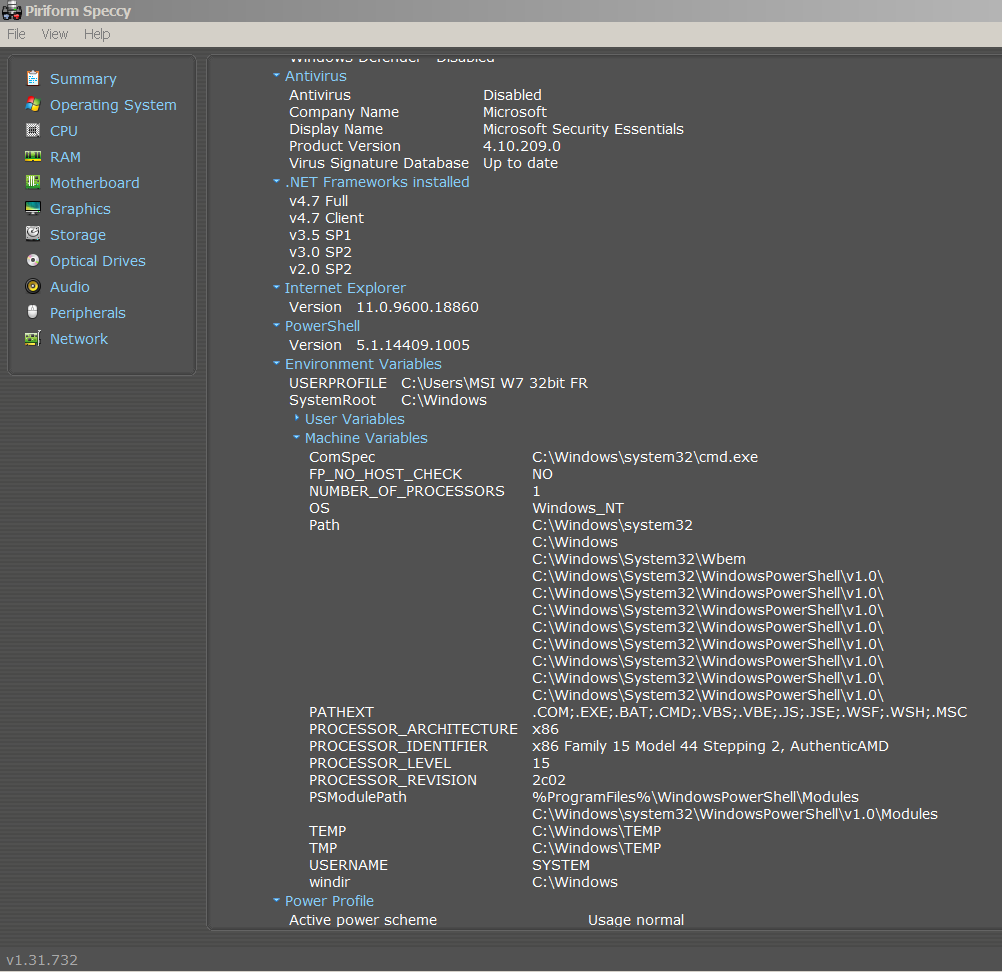
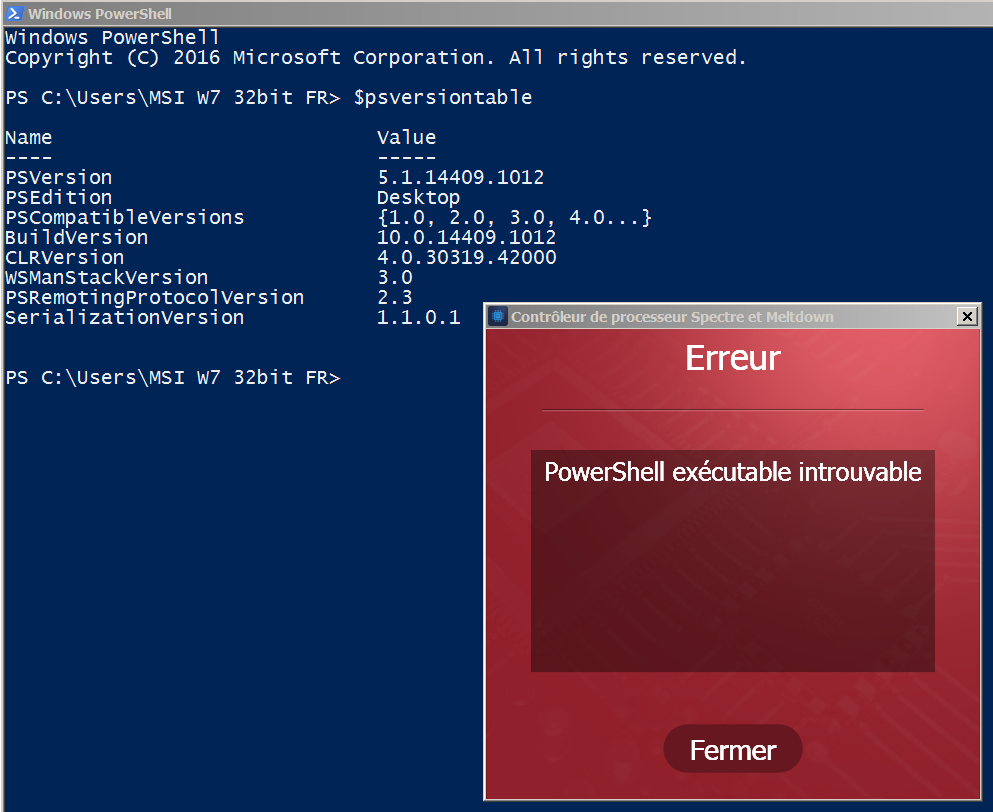
@100PIER
Have you tried my tool on Win7 32bit? If it works then you can leave Ashampoo`s one. After all I just took source from original MS script, from MS developers themselves.
@mbk1969
1) Yes are the test results with your Tool under W7 SP1 32bits PowerShell v5, WMF v5.1, .NET Framework v4.7.1 running on a legacy antique MSI-AMD platform:
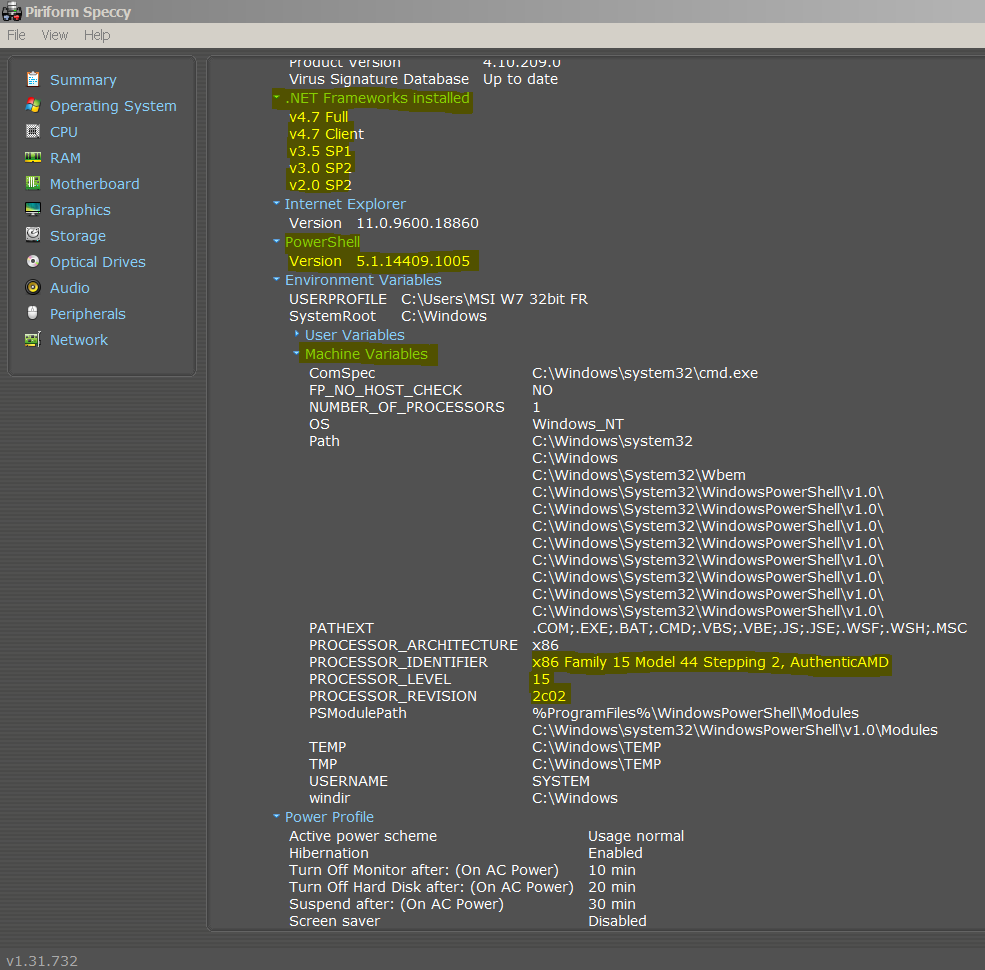
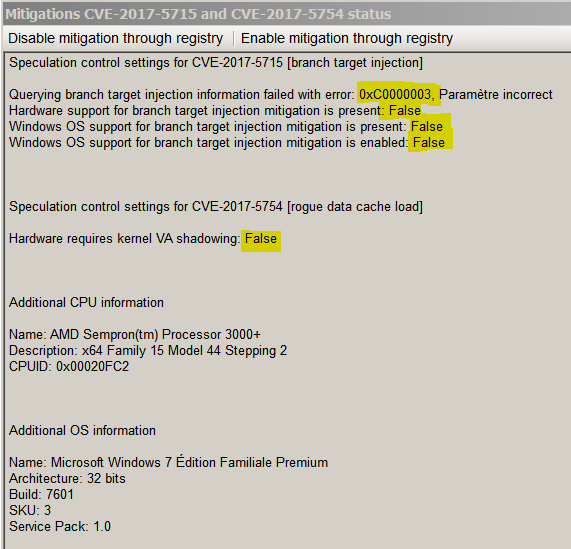
What do you think about ?
2) The purpose of your tool and Ashampoo tool is the same: does detect Spectre/Meltdown vulnerabilities of the PC.
Frankly, my preference is your tool because I don’t understand why for the same purpose your tool does not need one internet connection and Ashampoo Tool does need one. Is it for spying/logging the results ?
What is your opinion ?
All is as expected: patch is not installed (hence error 0xC0000003), and test for Meltdown is not performed due to detected AMD processor (assuming that only Intel ones are vulnerable).
If their utility internally utilizes PowerShell script from Microsoft then internet connection is needed to download that script (and install it at next step). Namely requirements for this tool point to that possibility of utilizing PowerShell script.
@mbk1969
Thanks for your comments.
1) Here is the link to the Complete List (Rev 4.0) of CPUS (Intel, AMD, ARM, Apple) concerned by the bug Meltdown/Spectre:
Complete List of CPUS concerned by Meltdown/Spectre
AMD is also concerned by the Spectre exploit 2:
AMD Spectre
2) Ashampoo Support does confirm a bug, a new release will delivered soon after fixing it.
The internet connection does seeem needed due to a MS “piece of software” only available by internet:
[u]the application needs an internet connection because the newest routines from Microsoft are needed, which are only available online. The problem in your case might be that there is a blank space in the path for either your user name or the temp folder. Our developers are working on a fix for this bug which should be solved soon. There will be a new version of the CPU Checker available after this problem has been solved.[/u]
Thats on the paper. But Microsoft script doesnt output info about Meltdown mitigation status if it discovers AMD processor.
The provided CPU List link does confirm AMD CPUs are not vulnerable to Meltdown bug.
Just to let you know that there is no need to install WMF v5.1 and using Ashampoo v1.1. Besides, there are some talks on the net that this tool is blocking and preventing the update patch from Microsoft to be installed in Windows. But that is not yet confirmed.
Bettter to use one of those two tools that provide more details anyway:
SpecuCheck This tool must be executed with CMD or PowerShell
Or…
The Microsoft tool script via PowerShell, here are the commands to run:
1- Set-ExecutionPolicy -ExecutionPolicy REMOTESIGNED (answer “Yes”)
2- Install-Module SpeculationControl (Answer “yes” for all questions)
3- Import-Module SpeculationControl
4- Get-SpeculationControlSettings
5- (Optional) Set-ExecutionPolicy -ExecutionPolicy RESTRICTED (This set back the default policy. It is not recommended to run this command on a server because REMOTESIGNED is the default on a windows server)
Details on the output of this tool can be found here.
@Phoenix48
@mbk1969
Thanks for this 4th Spectre/Meltdown diagnostic Tool.
Does this tool diagnose the same things, for instance on a Haswell-E X99 W10 platform ?
[[File:SPECUCHECK_on_X99_Haswell-E.PNG|none|auto]] [[File:SPECTRE_TOOLS_W10_X99_Haswell-E_µC_3B_17jan18.PNG|none|auto]]
@100PIER
I am not sure but i don’t think their ways to test it are the same completely.
What i mean is i am fairly sure that they all test the same basics at the minimum. But what is more than the basics seems to not be tested by all the tools. And certainly not as well explained in details by all of them neither.
Your GRC tool (that i wasn’t aware of) is probably the most comprehensive of them all in terms of vulgarisation for everyone to understand and the only one that gives control to disable the protection in Windows. It is worth noting that you can click “show tech details” in the upper left of the tool for those who wants more details.
The Microsoft tool seems to give us many details but when you decipher them you realise that it is only telling us (in a very elaborate way) this simple thing: If the protection is there or not and, if not, because of what.
As for the SpecuCheck tool, it seems to go deeper in some ways but it may be harder then others to comprehend. One exemple of a clue that it may go deeper is in the last update that state:
"Show a green “no” if user global pages are enabled – this is a work-around if INVPCID is not enabled, so users should see “all green” in the best state."
That tells us that there is at least one work-around in windows that can be tested too beyond the basics.
And i won’t even talk about Ashampoo with its WMF5.1 installation just to get a simple “yes-or-no-without-explanations”…
As for your Haswell-E X99 question, yes, each tool test everything that it was coded to test no matter the system and will work on any platform. Obvioulsy, for a vulnerable CPU, the answer a test give may obvioulsy be different for each platform (Only W10 has a patch available for now). But each tool may have been coded to test different things when it goes beyond the basics. And for sure, they don’t have the same ways of explaining it.
I must also point out that only a different platform can easily produce different answers to a test between different systems with the same CPU. Because there is only 3 things that can affect this issue:
1- The CPU itself (It is affected since the manufacture or not, and if yes, the only way to change that answer is to buy a new CPU)
2- The CPU microcode of a CPU affected by #1 (the Microcode itself is changed by a patched one in the BIOS or the BIOS itself is changed by a new one that include a patched microcode)
3- The platform is patched or not (Windows 10, 7, 8, etc)
When more and more patched CPU microcode will become available, that answer will more and more become different too between users of the same CPU because some will install the patched microcode and others won’t do it or won’t even be aware that they should do it.
I must point out in that last statement that there is a HUGE amount of people out there that are aware that those flaws got out in the open but they almost all think that because their PC is older than a few years then they are not affected. They don’t even make a reseach to verify it so sure they are of this. I can even say that for myself. I have an Intel i7-980X that is already old in the PC world and it is affected too. I was a long time thinking that i was not affected because of the age of it. And one day, i decided to test it just for the fun of it… And i learned i was wrong…
@100PIER
Be aware that inSpectre tool is compiled as 32-bit process. My tool at first was compiled as 32-bit too (haven`t noticed that at first), and it was discovered that on some 64-bit Windows installations my 32-bit tool gives results different from PowerShell one. Which is strange because they are the same source code only in different languages. After I changed compilation to 64-bit that strange behaviour is gone.
So this InSpectre tool can show same behaviour.
As for your question, all tools have to call one specific Win API function to check the state of both mitigations. They differ in way of displaying the results.
@Phoenix48
My tool also have buttons for disabling/enabling the mitigations. You simply need to create/delete two registry values described in MS article - quite simple.
@Phoenix48
Thanks for your very interesting comment that I agree totally.
To illustrate the fact that old PCs are also concerned by the bugs I have run the 4 tools on my 10 years old PC (DELL Vostro 400, CPU Intel Core 2 Duo E6850 MicroCode "1C") running perfectly under W10 RS3 64bits.
[[File:InSPECTRE_W10_x64_Intel_Conroe_06FB_µCode_C1.PNG|none|auto]]
[[File:MtigationS_Tool_W10_x64_Intel_Conroe_06FB_µCode_C1.PNG|none|auto]]
Speculation control settings for CVE-2017-5715 [branch target injection]
Hardware support for branch target injection mitigation is present: False
Windows OS support for branch target injection mitigation is present: True
Windows OS support for branch target injection mitigation is enabled: False
Windows OS support for branch target injection mitigation is disabled by system policy: False
Windows OS support for branch target injection mitigation is disabled by absence of hardware support: True
Speculation control settings for CVE-2017-5754 [rogue data cache load]
Hardware requires kernel VA shadowing: True
Windows OS support for kernel VA shadow is present: True
Windows OS support for kernel VA shadow is enabled: True
Windows OS support for PCID performance optimization is enabled: False [not required for security]
Additional CPU information
Name: Intel(R) Core™2 Duo CPU E6850 @ 3.00GHz
Description: Intel64 Family 6 Model 15 Stepping 11
CPUID: 0x000006FB
Additional OS information
Name: Microsoft Windows 10 Famille
Architecture: 64 bits
Build: 16299
SKU: 101
Service Pack: 0.0
[[File:SpectreMeltdownTool_W10_x64_Intel_Conroe_06FB_µCode_C1.PNG|none|auto]]
[[File:SPECUCHECK_W10_x64_Intel_Conroe_06FB_µCode_C1.PNG|none|auto]]
I have tried SpecuCheckTool on an antique (2005) AMD K8 Sempron 3000+ W7 SP1 32 bit platform under PowerShell v5.0 (administrator) interface. It does not work and does immediatly state:
"Your system eitheir does not have the appropriate patch, or it may not support the information class required"
Does it mean that all old CPUs (Intel, AMD) with one core are not concerned by the SPECTRE bug ?
I have read on the net that all AMD CPUs (old and recents) are not concerned by the MELTDOWN bug.
Do we have to modify the title of this sub forum: How to confirm the Microcode Revision for your CPU has the most secure SPECTRE patches
Hows it going 100PIER. I started a thread just for this, your answer is getting there. A list of codes with notations like the old OROM chart here. We updated the OROM, sent in the information like which motherboard, etc so this way people coming here have a central area to review and then determine if they want to update or wait. Same thing here and it sounds like just as you mentioned. I think this is where we are headed.
@100PIER
If you will run my tool on your antique rig and paste output here we can decipher it together.
@mbk1969
Here is the Spectre/Meltdown diagnostic tests set results done on a 10 years Dell PC running W10 RS3 x64 (Intel Dual Core CPU):
This PC does seem Spectre vulnerable and the unique solution does seem to update to a new µCode if available one day ? and how to update it ?
I don’t think one day Dell will provide a new BIOS release ! The last one was done on June 2008 !!
[[File:GRC_InSPECTRE_W10_x64_Intel_Conroe_06FB_µCode_C1_20jan18.PNG|none|auto]] [[File:SpectreMeltdownTool_W10_x64_Intel_Conroe_06FB_µCode_C1_20jan18.PNG|none|auto]]
Here are Specucheck and Mitigations Tools result:
[[File:SPECUCHECK_W10_x64_Intel_Conroe_06FB_µCode_C1_20jan18.PNG]][[File:MitigationS_Tool_W10_x64_Intel_Conroe_06FB_µCode_C1_20jan18.PNG|none|auto]]
I have also tested your Option “Enable Mitigation through Registry” and started again your Tool and Specucheck Tool. I do observe no change to the tests results:
[[File:MitigationS_Tool_W10_x64_Intel_Conroe_06FB_µCode_C1_afterEnableMitigationRegistry_20jan18.PNG]] [[File:SPECUCHECK_W10_x64_Intel_Conroe_06FB_µCode_C1_afterEnableMitigationRegistry_20jan18.PNG|none|auto]]