@100PIER
You wrote "I have tried SpecuCheckTool on an antique (2005) AMD K8 Sempron 3000+ W7 SP1 32 bit platform" and then you showed log on Intel system. Anyway nothing suspicious in the log.
@mbk1969
In fact I have (among some others) 2 antiques PCs: one W7 SP1 32bit (2005 AMD K8 mono core 64bit CPU) and one other W10 RS3 64bit (2008 Intel Dual Core CPU).
Post#25, #35 was for AMD cpu machine, Post#40 was for Intel cpu machine.
To summarize:
with the oldest platform (2005) the tools does not work or does report errors. Is it due to a monocore architecture ?
Do you think that any PCs on the planet based on a mono core CPU 64bits (AMD or Intel) are not at all concerned by the Meltdown/Spectre ? (and this should explain why the Tools does not work or display a error) ?
In post #40 I was wondering why your Tool does offer the "Enable mitigation Through Registry" Option button active and when clicking ON and then Reboot I observe no changed diagnostic for a new run of your tool ?
Is it normal ?
Meltdown and Spectre is not about cores. They are about "prefetcher" which tries to predict next portion of code/data to be executed and fetches it to CPU cache memory. Problem with RAM is its low speed comparing to CPU. To boost performance CPU manufacturers invented cache memory which stands between CPU logical units and RAM. When any program is executed portion of code and data are preloaded from RAM to cache (and then logical units execute code with data from cache). Modern CPUs has this "prefetcher" quite smart and flexible, and each generation has something new in it, and AMD with Intel made different implementations of this "prefetcher". Namely this thing in CPU is target of Spectre/Meltdown attacks.
Enabling/disabling mitigation through registry only works on systems where OS received patch with support, and with hardware received microcode with support.
@mbk1969
Many thanks, it is clear that even very old CPUs are also concerned by Spectre…
Yes, it is was I thought: Enabling/disabling mitigation through registry does only work where OS received patch with support, and with hardware received microcode with support.
In my test on the antique PC the OS is patched but obviously I have not updated the microcode (it does not exist yet or will never be available…).
So, why do you offer, for this PC, the 2 buttons active (not greyed) ?
For me the 2 buttons should be ‘inactive’ because one of the two conditions to do “on/off” the mitigation is to have a correct µCode applied (if I understand well).
I wrote that tool only to offer alternative to a guys who had troubles with PowerShell version from MS. In Russian we say about such fast development - "made on the knee" (I spent 1 hour on first version). Buttons were added afterwards as a bonus. Since there is no harm in enabling/disabling mitigations I did no pay attention to such nuances. Also since I am aware of these two mitigations` details I assumed that most of users will be too.
Also most of programmers are lazy.
@mbk1969
Many thanks again for your very nice tool and your time to reply. My question was only to ‘understand’ and your tool is perfect for me ‘as is’.
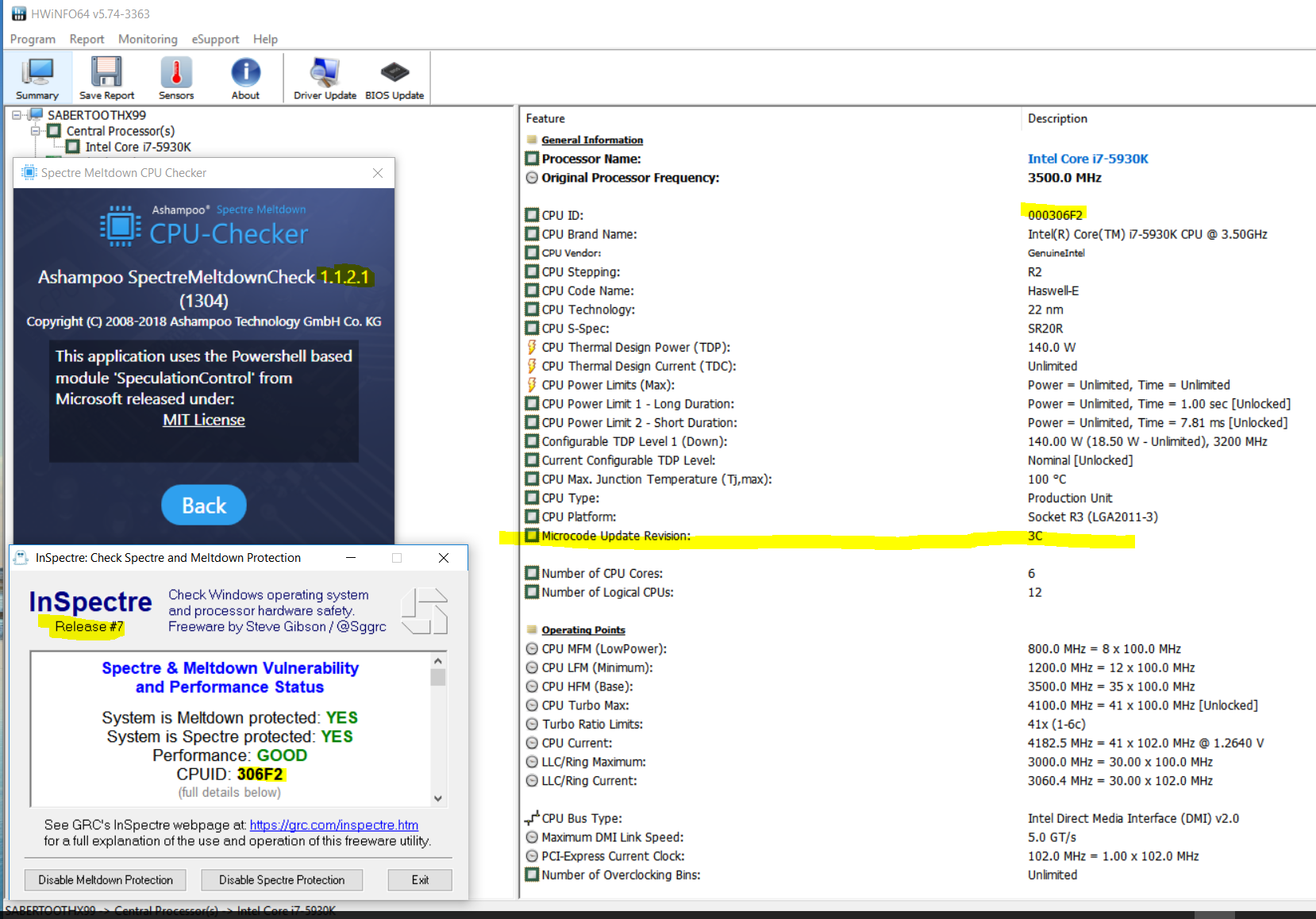
FYI: Here is GRC-InSpectre Release#5 run on a x99 PC “fully mitigate”:
[[File:InSpectre_5_W10_X99_Haswell-E_µC_3B_20jan18.PNG|none|auto]]
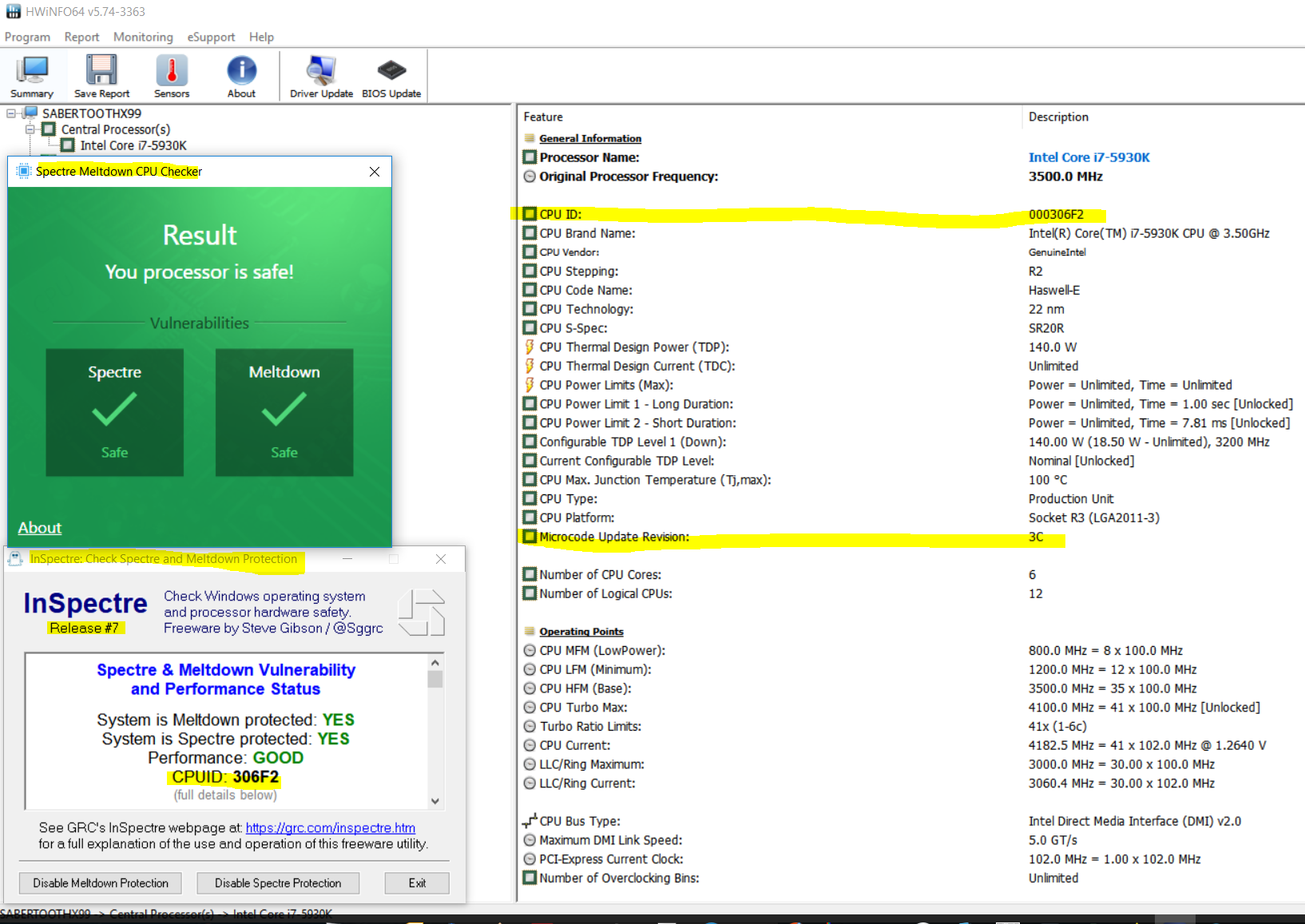
@mbk1969 , thanks used your tool.
@100PIER , also used the cpumcupdate2.1 and install.bat using the latest Linux Processor Microcode Data File which told me “No CPU’s needed update” in event viewer log, so used the uninstall.bat. (was not very surprising since no new microcode for IVB).
@N607
@mbk1969
Thanks for the info about cpumcupdate tool. I"ll do tests to learn about it.
Here is a screenshot of the 4 tests Spectre/Meltdown tools run on X99, CPU Haswell-E µCode=3B, W10 RS3 64bit:
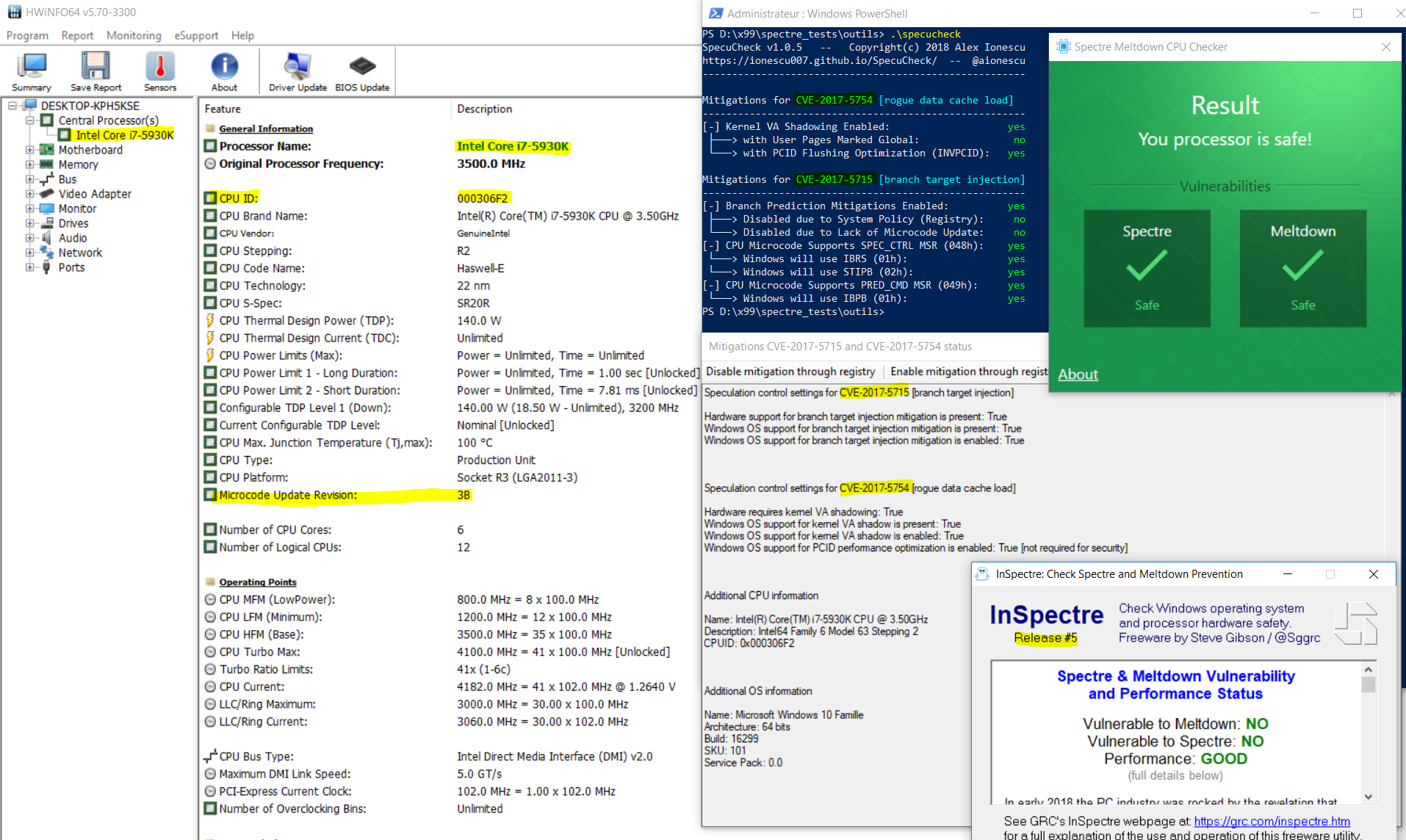
Specucheck Tool does suggest for CVE-2017-5754 mitigation apparently 2 differents options to get the "Kernel VA Shadowing Enabled" (yes case)).
I think I have used one (automatically ?, by default ?).
Who choose the option ? Is it W10 patch ?
What is the Option "with User pages marked Global" ?
@Fernando
I do recommend these tools to check the Spectre/Meltdown protection as well have the CPUID and µCode values used on a PC: