Yes you are right. But I haven’t tried to fix it yet. With a previous test BIOS image file, I was just trying to find its source. The error has changed, you see?
Try this one: test~2.bin
Yes, I can see that!!! I’ll run the tests now.
No start… Motherboard turns on, but no initialization
There is something wrong with this dump, the BIOS seems to be broken
For some reason, the BIOS rejects changes in the setup modules. I can’t figure out why it behaves like this. Or maybe it rejects any changes to itself? Was the computer still able to boot into the operating system after writing the first two binaries?
I think It had been able to.
It’s a complicated situation… So, you understand more than I do on this issue, what do we do next? What should I do?
Are you saying that this BIOS is tamper-proof and cannot be disabled? And all our efforts are in vain?
Heck, I just need it to output an image through the video card and not through the built-in video… I didn’t think it would be that hard…
I’m not sure on anything about this BIOS at the moment.
Too difficult for me.
I want to do something. Please write a good backup to motherboard and boot to Windows. After that, run “START” batch file from this archive and follow the on-screen instructions. Let’s try to use the new utility solution.
I did everything like you said! I used the downloaded files to create a bootable USB. And was able to run it on my board. Here is a picture.
Well, you did everything right. But for some reason it did not work. Gotta find out why.
@AARCH64_EL3, what is meant in this case? What is write protected?
Any idea what to do next? If so, I’m ready for the challenge!
We can check if this BIOS is tamper-proof by editing something very unsignificant. BIOS version text, for example. 1.02.000 to 1.02.001.
Shall I share the modified BIOS for you to check? What do you think?
From that point it will be clearer what to do next.
I’ll do anything! Just tell me what I need to do and I’ll do it. I have no ideas except yours.
Great! Thank you. I’m off to work now, I’ll check after work and report back…
I’m here! I wrote down the dump file “Test_3”… result - error again and the same as first time: <null_string>[0x002F]. It turns out that there is protection against changes, if I understood the meaning of our experiment correctly.
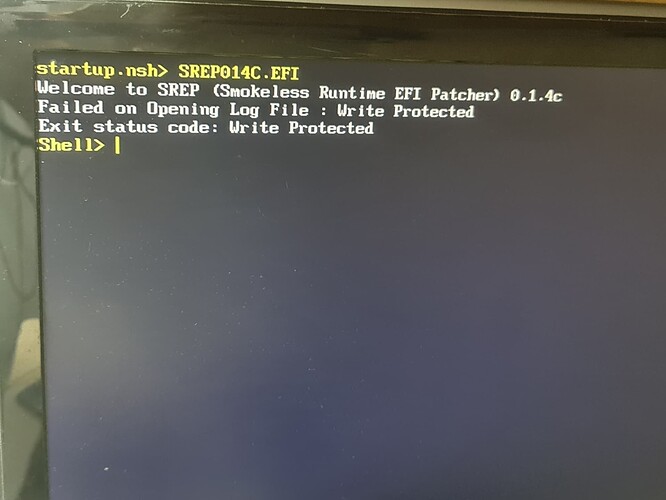
The usb/efi partition, it failed to create the log file in the efi partion
you can use the version before 0.1.4c, that will write the patcg log to console instead of on a file (but will reset due when whatchdog expire, this was fixed on 0.1.4c, if needed I can release 0.1.4d, with a switch to decide on how ouput the log, console or file)
Sadly, can’t figure out what to do with the BIOS internal protection. I know I said that it is possible to unlock, but it was more about the fact that I have an understanding how to work with UEFI. Your request would have been successful long ago if not for this tamper-proof function.
I suggest to rely on other, not so radical methods as BIOS flashing.
I did what you recommended.
@Aleksandr85, the download link has been updated. Would you like to try it out?