Excellent! This is very helpful. Thank you @Sweet_Kitten!
So there is indeed a HP_BBUpdate module, GUID: 94F994D5-4F3D-4FA6-BDA1-D398C3B0BB8 and also a HP_BBUpdate_Loader, GUID: 5C0203AC-5118-4952-9AAE-614AAE683FD4 in the BIOS I have.
For the record, my BIOS is a 08A13, version F.15, although the system board ID is 08A14: no mistake here, the BIOS image seems to be common for both versions. Just adding this for completeness, as it’ll eventually come up later anyway.
Prior HP BIOS Mod
Findings
I found some details regarding a prior mod involving HP_BBUpdate, close to the HP 15-ec series but not quite the same. It’s for a HP Pavilion 15-bc404ur (4EL78EA), an 8th Gen Intel / nVidia device from 2019 with an AMI BIOS as well. Even more similar then, so far so good.
On another forum, cerg2010 (credit where credit’s due) posted a mod against BIOS version F.21 (2018-11-14) for this device.
The stock BIOS image was included in update SP92665 from HP. A user on that forum preserved an earlier version of that download, which is a completely different executable but the BIOS images stored inside them are identical, so never mind. Two other images are included in the update, for 084ED and 084F7 as well, but the mod is for system board ID 084F8.
Besides the signature verification check removal (which is what I’m most interested in), the mod also unhides the setup menus, removes the PRRs and Wi-Fi whitelist, enables BCLK overclocking, and disables signature check for BIOS recovery mode flash (will execute any EFI file named HpBiosUpdate.efi or HpBiosMgmt.efi). So the scope of changes is quite vast. Kudos to the modder!
To that effect, there are changes in two modules as well as to the ME region. The changed modules are:
-
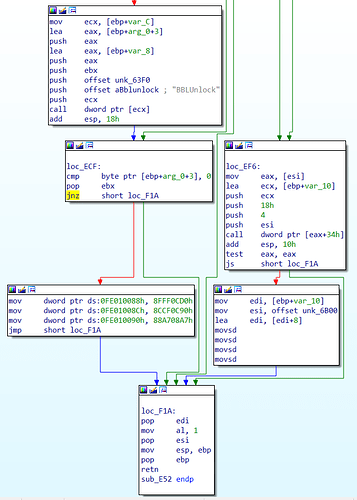
Pre-EFI Initialization (PEI) module HP_BBUpdate GUID: 94F994D5-4F3D-4FA6-BDA1-D398C3B0BB8F, which appears twice in the 084F8 image, so it has to be replaced twice. In my 08A13 BIOS I only have it once.
-
Driver Execution Environment (DXE) module AMITSE GUID: B1DA0ADF-4F77-4070-A88E-BFFE1C60529A.
Note / Reminder: the proper way to extract these modules for comparison with UEFI Tool is to right-click and Extract body… of the PE32 Image Section under LzmaCustomDecompressGuid. It’s easy to get that wrong.
Interestingly, there were 7 further BIOS updates for this device. The latest one is F.33 (2022-08-16), as part of SP141996. While AMITSE has changed significantly between the versions, the HP_BBUpdate module remains the same in both F.21 and F.33, which means that part of the mod could be reused for the newest version. Unfortunately, the HP_BBUpdate binary is completely different in the 08A13 BIOS I’m trying to mod (that’d make it just too easy).
Conclusions
-
Since AMITSE is just the setup utility, no matter what is there would not prevent a modified BIOS from booting. While I also want to unhide menus (in fact it’s the very reason why I’m attempting the mod), it’s outside the scope of the question here and can be ignored for now.
-
There is no mention of any mods to HP_BBUpdate_Loader and since it’s also present in the 084F8 image, it can be concluded that it doesn’t have to be modified.
-
The reason why there are two versions of HP_BBUpdate in the 084F8 image is because there seem to be two exact copies of the same EFI firmware filesystem there, both with the same Volume GUID: 61C0F511-A691-4F54-974F-B9A42172CE53. In HP_BBUpdate itself, there are mentions of “1st” and “2nd” boot blocks, $HP1stBB and $HP2ndBB, etc., which I think refers to this as well. By comparison, in the 08A13 there is only one Volume GUID 61C0F511-A691-4F54-974F-B9A42172CE53, which falls in the BootGuard-marked area. HP_BBUpdate is outside it, on a Volume GUID: 14E428FA-1A12-4875-B637-8B3CC87FDF07. Essentially, the image layout is significantly different.
-
The ME region is completely different in the mod compared to the stock F.21. At first glance, it’s difficult to say what exactly is going on there. Running them through @platomavfan’s ME Analyzer, it seems these are actually two separate versions: 12.0.10.1127 in the stock BIOS vs 12.0.0.1069 in the mod. Thus, the mod is a downgrade. Looking at the earlier BIOS releases: F.17 (SP8813), F.18 (SP88779), and F.19 (SP91738), it turns out all three have the same ME version as the mod. And thus the difference between the stock ME region from these earlier versions and the mod is just down to 5,688 bytes out of the 3,141,632 bytes total size, so approx. 2%. Much easier to investigate further if need be.
I’m sharing all the relevant files so there is no need to redo the same work if anyone else wants to look into it: 110.44 MB folder on MEGA
The file names are hopefully self-explanatory.
To Do
-
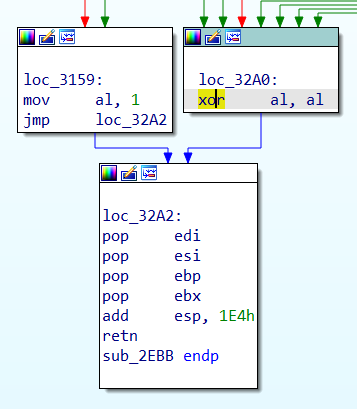
Disassemble and compare 084F8_HP_BBUpdate_F.21_F.33.efi and 084F8_HP_BBUpdate_F.21-Mod.efi to see what the patch is doing exactly: there are 3 different bytes as per 084F8_HP_BBUpdate_F.21-Mod-Diff.txt. Using these findings, reapply the same patch to 08A13_HP_BBUpdate_F.15.efi.
-
What about the ME region? In order to make a modified BIOS boot, are changes necessary to the ME region as well? Or is this part of the other mods only? The definite answer is in the 5,688 different bytes between 084F8_ME_F.17_F.18_F.19.rgn and 084F8_ME_F.21-Mod.rgn as per 084F8_ME_F.21-Mod-Diff.txt.
-
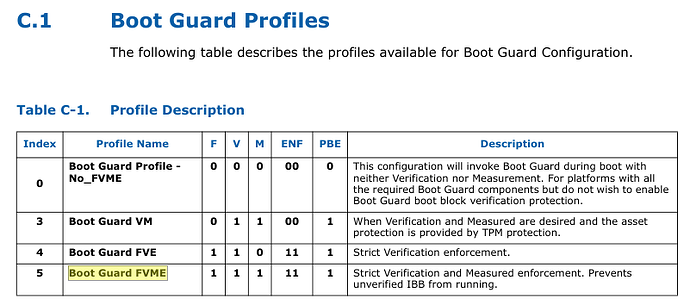
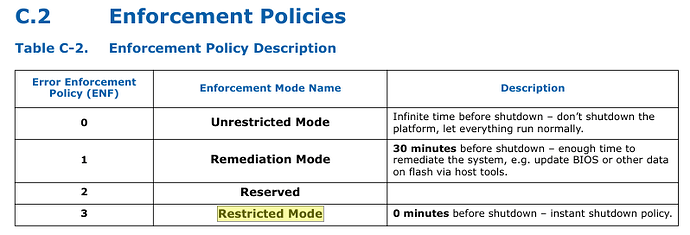
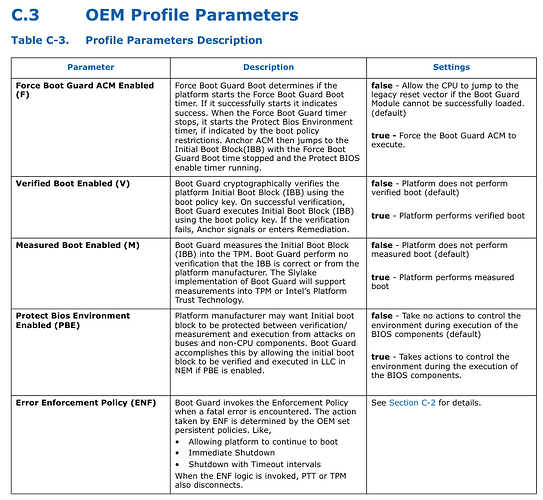
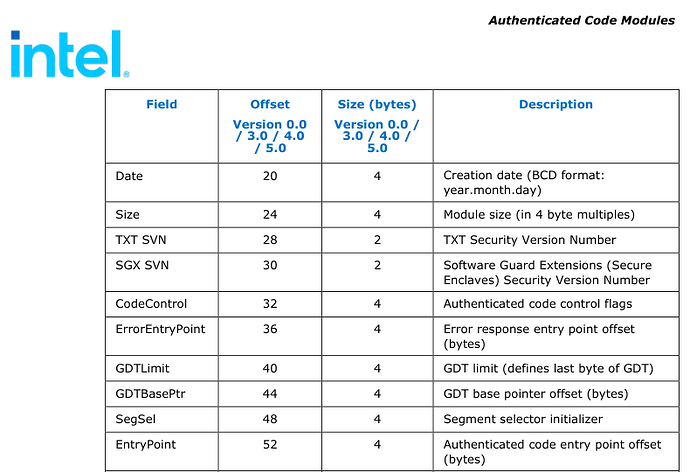
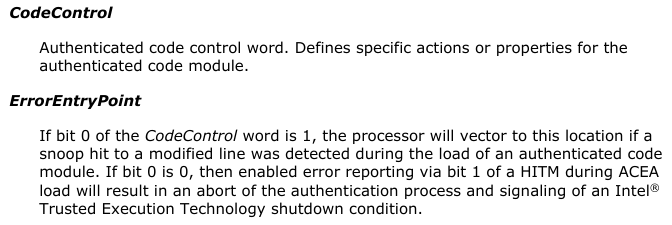
The BIOS I’m trying to mod has BootGuard enabled with both Measured and Verified boot. The Firmware Information Table (FIT) has entries for Startup ACM, BootGuard Key and also TXT Policy. None of this is present in the modded 084F8 8th Gen BIOS from 2018. Does this present an additional obstacle? The following seems to be a good BootGuard primer but the implications are unclear to me at this point: Bootguard - Trammell Hudson's Projects
-
And of course, is that the extent of it, or were there other possible surprises added by HP between the 8th and 12th Gen?
I’m not exactly there yet but it’s a start. If anyone wants to chip in, it’d be much appreciated. @Sweet_Kitten’s answer helped a lot, and I’m very grateful.