Intel CSME 11.8 Consumer PCH-LP Firmware v11.8.50.3425
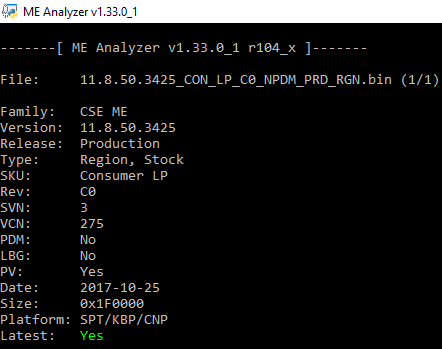
Intel CSME 11.8 Corporate PCH-LP Firmware v11.8.50.3425
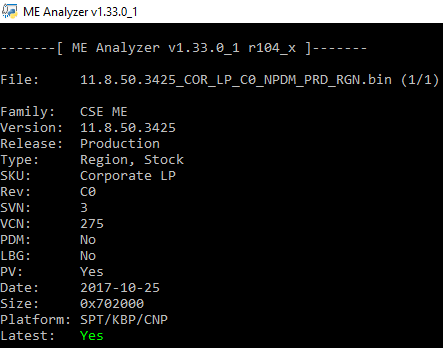
Intel CSME System Tools v11 r3
Intel CSME 11.8 Consumer PCH-LP Firmware v11.8.50.3425

Intel CSME 11.8 Corporate PCH-LP Firmware v11.8.50.3425

Intel CSME System Tools v11 r3
@ p82:
Thank you very much for the clean/stock (RGN) firmware. We only had the dirty (EXTR) before. Thank you for using ME Analyzer as well. 
Intel ME 8 1.5MB Firmware v8.1.70.1590 (EXTR → RGN)
Hey Plutomaniac,
can I update v8.1.70.1590 EXTR to v8.1.70.1590 RGN, via FWUpdate?
Will it be safe to do it?
Thanks in advance
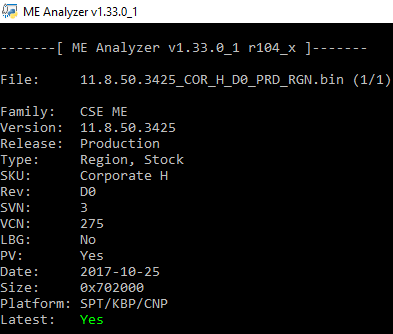
Intel CSME 11.8 Corporate PCH-H Firmware v11.8.50.3425 (CVE-2017-9765, CVE-2017-13077, CVE-2017-13078, CVE-2017-13080, CVE-2017-5705, CVE-2017-5708, CVE-2017-5711, CVE-2017-5712, CVE-2017-5729)
after the chipset replaces the hard drive does not deteck if this is problematic about the biosn firmware … thanks for everything
Intel CSME 11.8 Consumer PCH-H Firmware v11.8.50.3425 (CVE-2017-9765, CVE-2017-13077, CVE-2017-13078, CVE-2017-13080, CVE-2017-5705, CVE-2017-5708, CVE-2017-5711, CVE-2017-5712, CVE-2017-5729)
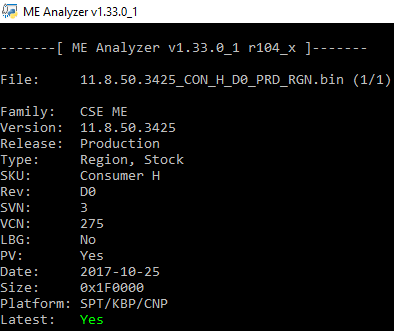
Changelog v11.8.50.3425
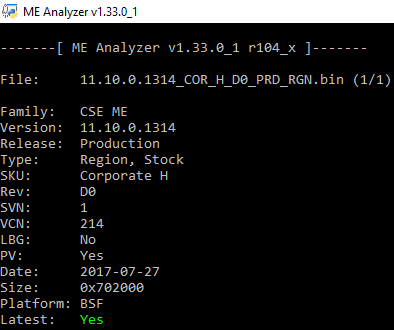
hello,
1. Did I understand it right? ME consists of DATA and CODE sections and if there are bug in DATA(which was configured by manufacturer) updating or reflashing current version using FWUpadate and ME downloaded from first page doesn’t affect DATA section?
2. If I just reflash BIOS file with the same ME version, is there are way to recognize was the ME region reflashed too or stayed untouched(mby some counter or date of update)?
Test ME FW 11.8.50.3425
MB MSI z270
BIOS Version 1.30
MEBx Version 0.0.0.0000
GbE Version Unknown
Vendor ID 8086
PCH Version 0
FW Version 11.8.50.3425 H
Security Version (SVN) 3
LMS Version Not Available
MEI Driver Version 11.7.0.1045
Wireless Hardware Version Not Available
Wireless Driver Version Not Available
FW Capabilities 0x31111140
Intel(R) Capability Licensing Service - PRESENT/ENABLED
Protect Audio Video Path - PRESENT/ENABLED
Intel(R) Dynamic Application Loader - PRESENT/ENABLED
Intel(R) Platform Trust Technology - PRESENT/DISABLED
Re-key needed False
TLS Disabled
Last ME reset reason Global system reset
Local FWUpdate Enabled
BIOS Config Lock Enabled
GbE Config Lock Enabled
Host Read Access to ME Enabled
Host Write Access to ME Enabled
Host Read Access to EC Enabled
Host Write Access to EC Enabled
SPI Flash ID 1 EF4018
SPI Flash ID 2 Unknown
BIOS boot State Post Boot
OEM ID 00000000-0000-0000-0000-000000000000
Capability Licensing Service Enabled
OEM Tag 0x00000000
Slot 1 Board Manufacturer 0x00000000
Slot 2 System Assembler 0x00000000
Slot 3 Reserved 0x00000000
M3 Autotest Disabled
C-link Status Disabled
Independent Firmware Recovery Disabled
EPID Group ID 0xFD6
LSPCON Ports None
5K Ports None
OEM Public Key Hash FPF Not set
OEM Public Key Hash ME 0000000000000000000000000000000000000000000000000000000000000000
ACM SVN FPF 0x0
KM SVN FPF 0x0
BSMM SVN FPF 0x0
GuC Encryption Key FPF Not set
GuC Encryption Key ME 0000000000000000000000000000000000000000000000000000000000000000
FPF ME
--- --
Force Boot Guard ACM Not set Disabled
Protect BIOS Environment Not set Disabled
CPU Debugging Not set Disabled
BSP Initialization Not set Enabled
Measured Boot Not set Disabled
Verified Boot Not set Disabled
Key Manifest ID Not set 0x0
Enforcement Policy Not set 0x0
PTT Not set Enabled
EK Revoke State Not Revoked
PTT RTC Clear Detection FPF Not set
FW Status Register1: 0x90000255
FW Status Register2: 0x02F60506
FW Status Register3: 0x00000020
FW Status Register4: 0x00084000
FW Status Register5: 0x00000000
FW Status Register6: 0x00000002
CurrentState: Normal
ManufacturingMode: Enabled
FlashPartition: Valid
OperationalState: CM0 with UMA
InitComplete: Complete
BUPLoadState: Success
ErrorCode: No Error
ModeOfOperation: Normal
SPI Flash Log: Not Present
Phase: ROM/Preboot
ICC: Valid OEM data, ICC programmed
ME File System Corrupted: No
PhaseStatus: AFTER_SRAM_INIT
FPF and ME Config Status: Not committed
BIOS Version 1010
MEBx Version 0.0.0.0000
GbE Version 0.2
Vendor ID 8086
PCH Version 0
FW Version 11.8.50.3425 H
Security Version (SVN) 3
LMS Version Not Available
MEI Driver Version 11.7.0.1045
Wireless Hardware Version Not Available
Wireless Driver Version Not Available
FW Capabilities 0x31111540
Intel(R) Capability Licensing Service - PRESENT/ENABLED
Protect Audio Video Path - PRESENT/ENABLED
Intel(R) Dynamic Application Loader - PRESENT/ENABLED
Intel(R) Platform Trust Technology - PRESENT/DISABLED
Re-key needed False
TLS Disabled
Last ME reset reason Firmware reset
Local FWUpdate Enabled
BIOS Config Lock Enabled
GbE Config Lock Enabled
Host Read Access to ME Enabled
Host Write Access to ME Enabled
Host Read Access to EC Disabled
Host Write Access to EC Enabled
SPI Flash ID 1 EF4018
SPI Flash ID 2 Unknown
BIOS boot State Post Boot
OEM ID 00000000-0000-0000-0000-000000000000
Capability Licensing Service Enabled
OEM Tag 0x00000000
Slot 1 Board Manufacturer 0x00000000
Slot 2 System Assembler 0x00000000
Slot 3 Reserved 0x00000000
M3 Autotest Disabled
C-link Status Disabled
Independent Firmware Recovery Disabled
EPID Group ID 0xFD2
LSPCON Ports None
5K Ports None
OEM Public Key Hash FPF 0000000000000000000000000000000000000000000000000000000000000000
OEM Public Key Hash ME 0000000000000000000000000000000000000000000000000000000000000000
ACM SVN FPF 0x0
KM SVN FPF 0x0
BSMM SVN FPF 0x0
GuC Encryption Key FPF 0000000000000000000000000000000000000000000000000000000000000000
GuC Encryption Key ME 0000000000000000000000000000000000000000000000000000000000000000
FPF ME
--- --
Force Boot Guard ACM Disabled Disabled
Protect BIOS Environment Disabled Disabled
CPU Debugging Enabled Enabled
BSP Initialization Enabled Enabled
Measured Boot Disabled Disabled
Verified Boot Disabled Disabled
Key Manifest ID 0x0 0x0
Enforcement Policy 0x0 0x0
PTT Enabled Enabled
PTT Lockout Override Counter 0x0
EK Revoke State Not Revoked
PTT RTC Clear Detection FPF 0x0
FW Status Register1: 0x90000245
FW Status Register2: 0x06F60546
FW Status Register3: 0x00000020
FW Status Register4: 0x00084004
FW Status Register5: 0x00000000
FW Status Register6: 0x40000000
CurrentState: Normal
ManufacturingMode: Disabled
FlashPartition: Valid
OperationalState: CM0 with UMA
InitComplete: Complete
BUPLoadState: Success
ErrorCode: No Error
ModeOfOperation: Normal
SPI Flash Log: Present
Phase: ROM/Preboot
ICC: Valid OEM data, ICC programmed
ME File System Corrupted: Yes
PhaseStatus: AFTER_SRAM_INIT
FPF and ME Config Status: Match
Intel MEI Driver v11.7.0.1045 (Windows 8 & Windows 10) INF for manual installation
Thanks to Microsoft for the update and khanmein for letting me know. 
@ vickygameboy:
I doubt your problem is CSME-related. Have you run MEInfo and MEManuf tools to verify that everything works properly, as explained at the first post? If these seem ok, I suggest you apply the latest Dell BIOS or wait for the inevitable update which should come soon which officially includes ME 11.8.
@ Octopuss & Atem90:
You both have not understood the difference between RGN/EXTR/UPD and the difference between Flash Programming Tool and FWUpdate. Read the first post carefully.
@ kenzo2:
I can neither understand your English nor your situation. A lot more info and better explanation is required.
@ andr84:
1. Exactly, you’ve understood correctly.
2. That greatly depends on the way the OEM has decided to release BIOS and/or ME updates.
@ Gus.Ghanem & jjxaker:
Thank you for your reports guys! Everything looks fine (still don’t know what “Re-Key” is).
@ jjxaker:
Your other ASUS Z170 board still does not properly accept CSME firmware updates I assume (MFS corrupted), right?
Latest firmware and ME driver successfully applied to Gigabyte GA-Z170MX-Gaming 5 (motherboard bios version F21):
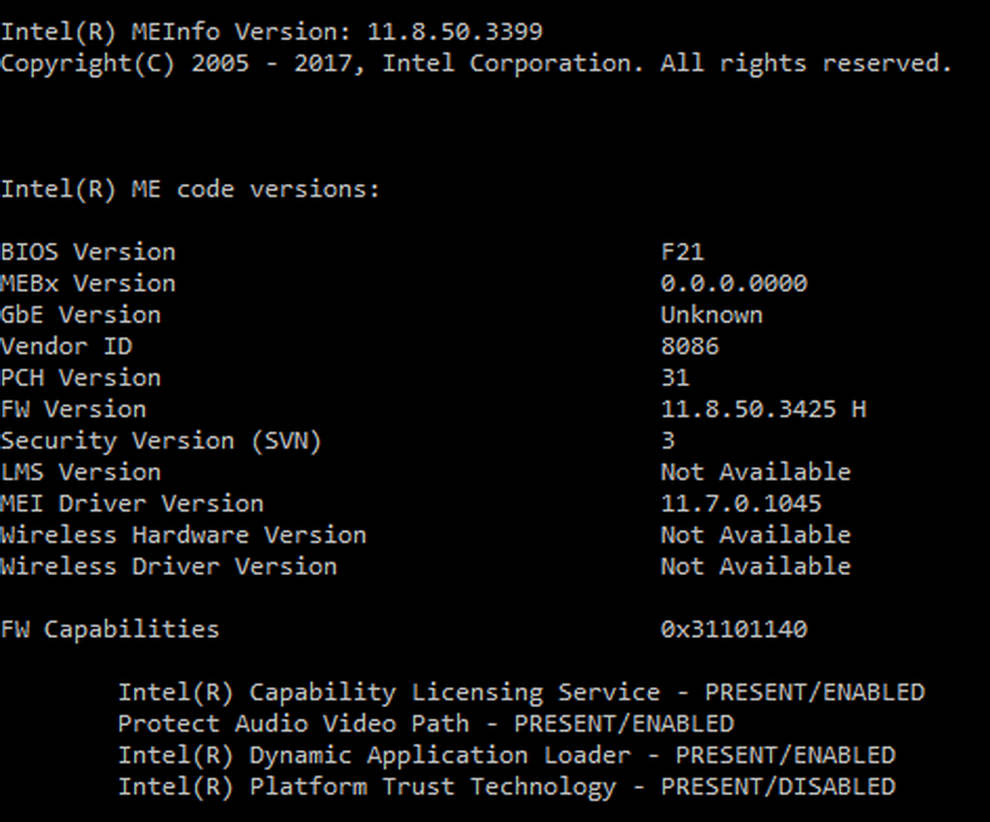
i could also confirm working ME 11.8.50.3425 on ASRock Z270 SuperCarrier:
https://www2.pic-upload.de/img/34264110/…1.8.50.3425.jpg
@ plutomaniac
Thank you,
1. so the only solution to reflash whole ME region(DATA + CODE)is to follow the ‘cleaning’ guide? I read the article with this guide, but don’t understand a bit what does ‘cleaning process’ exactly mean and what model specific settings it removes? Cleaning is only useful when the system is already built (branded desktop PC /dell,hp for example/ or any laptop) and if I purchased only motherboard there is nothing to ‘clean’ because it can be used in many different systems or it has ‘dirty’ ME also?
2. This final modified BIOS with ‘clean’ ME must be flashed via intel’s flash programming tool or can use manufacturer bios utility?
3. If I will flash modified BIOS with ‘clean’ ME , later is possible to flash original BIOS from manufacturer home page + update ME via FWUpdate?
Intel(R) MEInfo Version: 11.8.50.3399
Copyright(C) 2005 - 2017, Intel Corporation. All rights reserved.
Intel(R) ME code versions:
BIOS Version 3504
MEBx Version 0.0.0.0000
GbE Version 0.7
Vendor ID 8086
PCH Version 31
FW Version 11.8.50.3425 H
Security Version (SVN) 3
LMS Version Not Available
MEI Driver Version 11.7.0.1040
Wireless Hardware Version Not Available
Wireless Driver Version Not Available
FW Capabilities 0x31111540
Intel(R) Capability Licensing Service - PRESENT/ENABLED
Protect Audio Video Path - PRESENT/ENABLED
Intel(R) Dynamic Application Loader - PRESENT/ENABLED
Intel(R) Platform Trust Technology - PRESENT/DISABLED
Re-key needed False
TLS Disabled
Last ME reset reason Firmware reset
Local FWUpdate Enabled
BIOS Config Lock Enabled
GbE Config Lock Enabled
Host Read Access to ME Enabled
Host Write Access to ME Disabled
Host Read Access to EC Disabled
Host Write Access to EC Disabled
SPI Flash ID 1 EF4018
SPI Flash ID 2 Unknown
BIOS boot State Post Boot
OEM ID 00000000-0000-0000-0000-000000000000
Capability Licensing Service Enabled
OEM Tag 0x00000000
Slot 1 Board Manufacturer 0x00000000
Slot 2 System Assembler 0x00000000
Slot 3 Reserved 0x00000000
M3 Autotest Disabled
C-link Status Disabled
Independent Firmware Recovery Disabled
EPID Group ID 0xF8A
LSPCON Ports None
5K Ports None
OEM Public Key Hash FPF 0000000000000000000000000000000000000000000000000000000000000000
OEM Public Key Hash ME 0000000000000000000000000000000000000000000000000000000000000000
ACM SVN FPF 0x0
KM SVN FPF 0x0
BSMM SVN FPF 0x0
GuC Encryption Key FPF 0000000000000000000000000000000000000000000000000000000000000000
GuC Encryption Key ME 0000000000000000000000000000000000000000000000000000000000000000
FPF ME
--- --
Force Boot Guard ACM Disabled Disabled
Protect BIOS Environment Disabled Disabled
CPU Debugging Enabled Enabled
BSP Initialization Enabled Enabled
Measured Boot Disabled Disabled
Verified Boot Disabled Disabled
Key Manifest ID 0x0 0x0
Enforcement Policy 0x0 0x0
PTT Enabled Enabled
PTT Lockout Override Counter 0x0
EK Revoke State Not Revoked
PTT RTC Clear Detection FPF 0x0
I do not have motherboards on the chipset Z170, only z270 ![]()
But yes, the problem with MFS remains on my boards MAXIMUS IX APEX, and the situation cannot be rectified…
Most likely the problem in the BIOS code, because even the firmware of the original BIOS via the programmer does not solve the problem. well at least at work is not affected…
I wonder if it’s possible to include "ManufacturingMode" for Asus boards?
Personally I would try the CleanUp Guide with the stock BIOS & ME firmware version (pick the same version from repo, if RGN). If that doesn’t solve the problem, then either the BIOS is buggy or there’s some sort of unique hardware/software issue (I assume MEInfo reports the same even under EFI or DOS environments).
What do you mean by that?
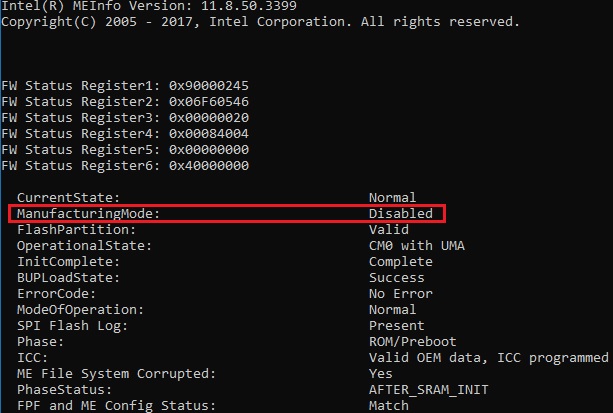
upd. the question is closed, I found where it turns on ![]()
Does not help…