@pustekuchencake :
I have answered your questions >here<.
If you don’t want to use any real Intel MEI driver, you can install just the NULL_HECISystem.inf text file instead. This will avoid a yellow bang within the Device Manager.
Hello
While wanting to update the MEI drivers, I realized that in the device manager, I had “Other devices”, related to the Management Engine Interface that I did not have before, I don’t know why that is appeared
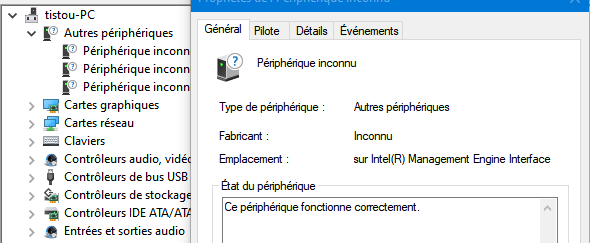
Looking at the IDs (SWC \ PROVIDER_INTEL_COMPONENT_ICLSCLIENT), it would correspond to an "Intel Trusted Connect Service Client" driver (iclsClient.inf) I believe
Anyone have an idea ?
Thanks
@Fernando Thanks
I found more recent drivers (1.58.48.0 of 2019) but I don’t understand why I have these peripherals now
When I install these drivers, I have a new service that appears in Windows services
Perhaps a novelty of the latest X299 bios (Rampage VI Extreme)
If you have an idea
Obviously yes.
I had these additional devices from the day i updated my PRIME Z370-A BIOS to 2401.
The only entry in the changelog is "Supported Intel® Optane™ Memory H10 device"
Hi guys,
Please help me! :S
My log…
i7-10510U
Copyright (C) 2005 - 2019, Intel Corporation. All rights reserved.
Intel(R) ME code versions:
BIOS Version N.1.00
MEBx Version 0.0.0.0000
GbE Version Unknown
Descriptor Version 1.0
Vendor ID 8086
FW Version 14.0.10.1204 LP Consumer
LMS Version 1927.14.0.1305
MEI Driver Version 1931.14.0.1323
PMC FW Version 140.1.1.1004
PCHC FW Version 14.0.0.7001
PCH Information
PCH Version 0
PCH Device ID 284
PCH Step Data A0
PCH SKU Type Production PRQ Revenue
PCH Replacement Counter 0
PCH Replacement State Disabled
PCH Unlocked State Disabled
FW Capabilities 0x31119240
Protect Audio Video Path - PRESENT/ENABLED
Intel(R) Dynamic Application Loader - PRESENT/ENABLED
Intel(R) Platform Trust Technology - PRESENT/ENABLED
Persistent RTC and Memory - PRESENT/ENABLED
Capability Licensing Service State Enabled
Crypto HW Support Enabled
End of Manufacturing Enable No
FWUpdLcl Enabled
Firmware Update OEM ID 00000000-0000-0000-0000-000000000000
Integrated Sensor Hub Initial Power State Disabled
Intel(R) PTT State Enabled
Intel(R) PTT initial power-up state Enabled
OEM Tag 0x00
PAVP State Yes
Post Manufacturing NVAR Config Yes
TLS State Disabled
FW Type Production
Last ME reset reason Global system reset
BIOS Config Lock Enabled
Host Read Access to ME Enabled
Host Write Access to ME Enabled
Host Read Access to EC Enabled
Host Write Access to EC Enabled
SPI Flash ID 1 EF4018
SPI Flash ID 2 Not Available
BIOS boot State Pre Boot
M3 Autotest Disabled
EPID Group ID 0x355D
Keybox Not Provisioned
RPMC Replay Protection Unsupported
RPMC Replay Protection Bind Counter 0
RPMC Replay Protection Bind Status Pre-bind
RPMC Replay Protection Rebind Unsupported
RPMC Replay Protection Max Rebind 1
Storage Device Type SPI
Minimum Allowed Anti Rollback SVN 1
Image Anti Rollback SVN 2
Trusted Computing Base SVN 1
Re-key needed False
HW Binding Enabled
FPF UEP ME FW
*In Use
— — -----
ACM SVN Not set 0x00 0x00
BSMM SVN Not set 0x00 0x00
EK Revoke State Not set Not Revoked Not Revoked
Error Enforcement Policy 0 Not set Disabled Disabled
Error Enforcement Policy 1 Not set Disabled Disabled
Intel(R) PTT Not set Enabled Enabled
KM SVN Not set 0x00 0x00
OEM ID Not set 0x00 0x00
OEM KM Present Not set Disabled Disabled
OEM Platform ID Not set 0x00 0x00
OEM Secure Boot Policy Not set 0x00 0x00
CPU Debugging Not set Enabled Enabled
BSP Initialization Not set Enabled Enabled
Protect BIOS Environment Not set Disabled Disabled
Measured Boot Not set Disabled Disabled
Verified Boot Not set Disabled Disabled
Key Manifest ID Not set 0x00 0x00
Force Boot Guard ACM Not set Disabled Disabled
PTT Lockout Override Counter Not set 0x00 0x00
Persistent PRTC Backup Power Not set Enabled Enabled
RPMC Rebinding Not set Disabled Disabled
RPMC Support Not set Disabled Disabled
SOC Config Lock State Not set Disabled Disabled
SPI Boot Source Not set Enabled Enabled
Txt Supported Not set Disabled Disabled
OEM Public Key Hash FPF Not set
OEM Public Key Hash UEP 8DE52279F2CEE6DAABB2E364843E6B726273A4EC269650BFD63B8EA7F0FB376F
OEM Public Key Hash ME FW 8DE52279F2CEE6DAABB2E364843E6B726273A4EC269650BFD63B8EA7F0FB376F
PS C:\FW\Info> cd…
PS C:\FW> cd .\Fw<br />PS C:\FW\Fw> dir
Directory: C:\FW\Fw
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 21.01.2020 20:48 3006464 14.0.11.1205_CON_LP_X_PRD_EXTR.bin
-a---- 21.01.2020 20:48 560616 FWUpdLcl64.exe
PS C:\FW\Fw> .\FWUpdLcl64.exe -f .\14.0.11.1205_CON_LP_X_PRD_EXTR.bin
Intel (R) Firmware Update Utility Version: 14.0.11.1205
Copyright (C) 2005 - 2019, Intel Corporation. All rights reserved.
Checking firmware parameters…
Warning: Do not exit the process or power off the machine before the firmware update process ends.
Sending the update image to FW for verification: [ COMPLETE ]
Do not Interrupt
Error 433: PMC partition is not in the Update Image.
PS C:\FW\Fw>
EDIT by Fernando: To save space I have put the MEInfo results into a “spoiler”.
@tecnics :
Since our Intel ME expert plutomaniac is currently very busy outside the Forum, you may have to wait for a reply several days or weeks.
I am sorry about that.
@tecnics I think plutomaniac answered already. You might want to read the first post.
“The PMC firmware can only be updated after being merged with a CSME 12-14 firmware via Flash Image Tool.”
…
"Starting from CSME 12, Intel FWUpdate tool does not work with bare RGN or EXTR CSE firmware as it requires that they are first combined/stitched with the equivalent Power Management Controller (PMC) firmware, which is updated alongside the main CSE firmware."
In addition: Here’s someone with an error 434 (ME 12) who seems to have solved the problem as described in the first post…
@plutomaniac :
Intel has released an updated version of the v13 platform Intel ME Firmware for IceLake CPU mobile systems. It is v13.0.20.1310 (Consumer LP variant, 1.5M) dated 01/21/2020.
You can get from >this< Station-Drivers site.
Update dated 02/01/2020:
Meanwhile Intel has released the Intel CSME Firmware v13.0.21.1319.
Dear fellows,
I cannot clean CSME Region on a Lenovo T490 notebook, I get this error when I try to load xml file that I previously saved. Do I need newer FIT Tools? I tried with r19 and r20, the same error happens.
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
LOG file
===============================================================================
Intel (R) Flash Image Tool. Version: 12.0.40.1434
Copyright (c) 2013 - 2019, Intel Corporation. All rights reserved.
1/23/2020 - 9:19:58 afternoon
===============================================================================
Using vsccommn.bin with timestamp 20:10:49 05/01/2019 GMT
Command Line: C:\Users\xxx\Desktop\WIN32\fit.exe
Log file written to fit.log
Loading C:\Users\xxx\Desktop\T490.bin
Decomposed PCH Strap Length: 0x45
FIT version used to build the image: 12.0.23.1311
Writing map file C:\Users\xxx\Desktop\WIN32\T490\T490.map
Saving XML ...
XML file written to C:\Users\xxx\Desktop\WIN32\Untitled.xml
===============================================================================
Intel (R) Flash Image Tool. Version: 12.0.40.1434
Copyright (c) 2013 - 2019, Intel Corporation. All rights reserved.
1/23/2020 - 9:21:10 afternoon
===============================================================================
Using vsccommn.bin with timestamp 20:10:49 05/01/2019 GMT
Command Line: C:\Users\xxx\Desktop\WIN32\fit.exe
Log file written to fit.log
Loading C:\Users\xxx\Desktop\WIN32\Untitled.xml
Loading XML file: C:\Users\xxx\Desktop\WIN32\Untitled.xml
Error 249: [Ifwi Actions] General error. Unable to get OEM Public Key Hash.
Error 9: Failed to decompose Image.
Unable to open file: C:\Users\xxx\Desktop\WIN32\Untitled.xml. Reverting to default configuration.
Loading defaults.
Error 235: [Ifwi Actions] Failed to load input file. Failed to get manifest version for PMC Binary File: C:\Users\xxx\Desktop\WIN32\ME Sub Partition\Decomp\PMCP.bin
Error 235: [Ifwi Actions] Failed to load input file. Failed to validate manifest version
Error 1: Initialize Error Error Initializing Fit.
FIT failed to load default configuration and cannot recover.
CSME image downloaded from Lenovo Website
EDIT by Fernando: FIT code put into a "spoiler" to save space
11.8.71.3630 consumer H seems to be working on h110 from msi. What intel me should i install 11.7.0.1057 ?
Dear all,
Want to fix CSME security bugs for a Dell E6520. Latest available BIOS version A22 is installed. CSME Firmware version is now 7.1.91.3272 (still vulnerable regarding Intel SA00086).
You have listed a newer Version: "Intel ME 7 5MB Firmware v7.1.92.3273"
Can I install it hassle-free via Windows or do I need a SPI Flash programmer device? Is it very risky to brick it or to get an unstable system (shutdown after 30min or other “Features”)?
Here are some Infos from MEInfo tool:
For 6/X79/C600-series systems which run ME 5MB v7
Intel(R) MEInfo Version: 7.1.50.1166
Copyright(C) 2005 - 2011, Intel Corporation. All rights reserved.
Intel(R) Manageability and Security Application code versions:
BIOS Version: A22
MEBx Version: 7.0.0.63
Gbe Version: 1.3
VendorID: 8086
PCH Version: 4
FW Version: 7.1.91.3272
UNS Version: Not Available
LMS Version: Not Available
MEI Driver Version: 11.0.0.1157
Wireless Hardware Version: 2.1.225
Wireless Driver Version: 15.16.0.2
FW Capabilities: 234249317
Intel(R) Active Management Technology - PRESENT/ENABLED
Intel(R) Anti-Theft Technology - PRESENT/ENABLED
Intel(R) Capability Licensing Service - PRESENT/ENABLED
Protect Audio Video Path - PRESENT/ENABLED
Intel(R) Dynamic Application Loader - PRESENT/ENABLED
Intel(R) AMT State: Enabled
CPU Upgrade State: Upgrade Capable
Cryptography Support: Enabled
Last ME reset reason: Global system reset
Local FWUpdate: Enabled
BIOS and GbE Config Lock: Enabled
Host Read Access to ME: Disabled
Host Write Access to ME: Disabled
SPI Flash ID #1: EF4017
SPI Flash ID VSCC #1: 20052005
SPI Flash ID #2: EF4015
SPI Flash ID VSCC #2: 20052005
SPI Flash BIOS VSCC: 20052005
BIOS boot State: Post Boot
OEM Id: 00000000-0000-0000-0000-000000000000
Link Status: Link down
System UUID: 4c4c4544-0034-3610-8048-b7c04f574d31
MAC Address: 5c-26-0a-68-32-d6
IPv4 Address: 0.0.0.0
Wireless MAC Address: a0-88-b4-6e-55-40
Wireless IPv4 Address: 0.0.0.0
IPv6 Enablement: Disabled
Wireless IPv6 Enablement: Disabled
Privacy Level: Default
Configuration state: Not started
Provisioning Mode: PKI
Capability Licensing Service: Enabled
Capability Licensing Service Status: Permit info not available
OEM Tag: 0x00000000
Thank you!
@pustekuchencake :
AFAIK the “Intel SA00086_Windows Discovery Tools” are outdated. The currently latest Intel tool, which is able to check the vulnerability of the modern Intel ME Firmware, is named “Intel CSME Detection Tool”. The Windows variant can be downloaded from >this< Intel Download Center page.
@Fernando :
Thanks for this advice. However this Version doesn’t support most of the older CSME firmwares - only “for systems that include a 6th-10th Generation”. For older CSMEs you have to use the legacy Version (which obviously doesn’t include current security flaws) ![]() :
:
Intel® Converged Security and Management Engine (Intel® CSME) Detection Tool for Legacy Systems
The legacy Version also states that my System is still vulnerable to SA00086:
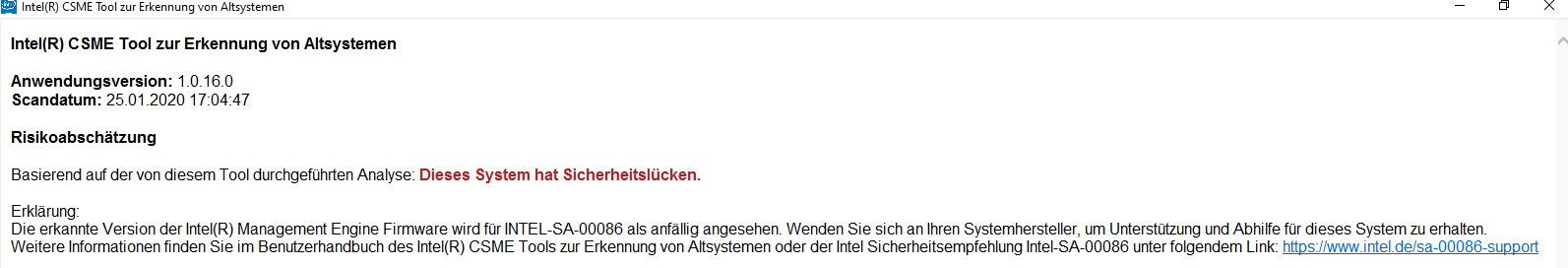
→ the Question remains: Is updating the Firmware normally hassle-free or is it a 50:50 process ![]()
@pustekuchencake :
Each BIOS/Firmware flashing procedure is a little bit risky, but if you pay attention and use a 100% matching Firmware and the latest available matching Intel (CS)ME System tool, the chances are much better than 50:50.
The update should be possible with Intel ME System Tools v7 r2 - (2018-09-08), see beginning of thread. In the folder FWUpdate you’ll find tools for DOS, Windows, Linux 32/64. I updated version 7, 8 , 9.0 and 9.1 several times without problems, but it’s flashing part of your bios chip and there’s always a risk. Check if your ME firmware is healthy with MEInfo/ MEManuf first (same package).
Since ME 7 is no longer supported for quite a while, there might be a lot of bugs you’ll never be able to fix:
"Note: Firmware versions of Intel® ME 3.x thru 10.x, Intel® TXE 1.x thru 2.x and Intel® Server Platform Services 1.x thru 2.X are no longer supported, thus were not assessed for the vulnerabilities/CVEs listed in this Technical Advisory. There is no new release planned for these versions." (Intel-sa-00213])
Intel® Product Security Center Advisories, latest for AMT 7 seems indeed to be SA-00086, latest for AMT 9 SA-000141. I’m pretty sure that ‘affected products’ beginning with 6th generation CPUs for later vulnerabilities doesn’t mean that 4th generation is safe, but that 4 th generation isn’t investigated…
