OK this one has updated EFI modules and NVMe 4 DXE added…so again, your choice.
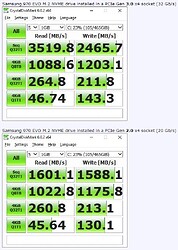
How do you think the performance of new technologies in NVME 1.4 and 2.0 depends on the PC platform and the connection method (PCI-E 2.0 x4 slot via the Z77 or PCI-E 3.0 x16 slot directly to the CPU)?
The maximum speed will certainly not change. But will the optimizations work with random access, and is it worth relying on the DRAM buffer?
Do the new disk controller technologies depend on hardware and BIOS, or are they fully provided by the OS driver?
I mean only those optimizations of new technologies that increase the speed in read/write modes, the speed of which does not rest on bandwidth, and which do not relate to cross-platform data transmission.
“How do you think the performance of new technologies in…”
Google is your “friend”…
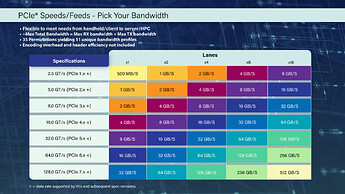
Now take your conclusions on simple PCIe bandwidth…
I’m sorry for another offtop, but I tried to find the answers on my own.
I have a question about the security of using modified firmware.
I understand that the risks of using modified firmware are entirely my responsibility. It would be pointless and unethical to shift this responsibility onto the enthusiasts who share their work. This is not a contract with obligations. Most of the risks can be eliminated only if you analyze each component and assemble the firmware yourself. But even official firmware can have security issues, and there have been cases of malware spreading through official channels due to the lengthy recall procedure.
I know there are several ways to analyze vulnerabilities hidden in UEFI firmware, but most of them involve the use of officially signed firmware and modules.
Is there a topic on this forum or another resource that summarizes these issues to avoid further discussion?
Is there any instructions on how to properly prepare the system for installing the modified firmware?
I am sure that the adaptation of the methods described below for the safe use of modified firmware deserves a proper reward (which of these is necessary, useless, dangerous/prohibited).
- Virustotal
- Get-SecureBootUEFI — shows the status of Secure Boot/DB/DBX/PK/KEK, quick Windows diagnostics. Microsoft documentation.
- fwupdmgr security — HSI assessment, firmware and security recommendations. The HSI specification.
- CHIPSEC — SPI protection check, UEFI analysis, firmware dump. GitHub.
- ESET UEFI Scanner — scans UEFI/ESP for known threats. ESET knowledge base.
- Kaspersky AV for UEFI — EFI-level protection and scanning. Product description.
- Analysis of unusual activity on the firewall is prohibited except for what is allowed.
Is it worth it before installing the modified firmware:
- Update the UEFI firmware from the manufacturer’s website.
- Update DBX/boot reviews MS guide.
- Clean or recreate ESP: delete unauthorized directories, reinstall the bootloader using standard OS tools.
- Reset NVRAM and restore Secure Boot keys: return platform keys (PK/KEK/DB), delete self-signed moks (if they should not be there).
- Disabling Compatibility Support Module