@MLS.22 , I appreciate your offer, but this BIOS isn’t on the same Clevo platform or CPU generation.
However, it’s interesting to disassemble it for inspiration in modding.
@Sweet_Kitten : NP70PNJ . But can refered as ★NP5x_6x_7xPNK_J_H or ★NPxx**PN_KHJ or ★NPxxPNK_J_H or ★NPxxPNKJH or ★SCHENKER MEDIA 17 (M22) (ID: SME17M22) or ★Gigabyte G7 GE …
Nonetheless, I was too focused on how to unlock/mod my BIOS when the question doesn’t apply.
Indeed, on the 12th generation Intel processors, especially the H-series CPUs, undervolting is physically impossible. It’s a hardware modification in the microprocessor’s construction.
Case closed. End of story.
Long explanation
In fact, this 12th generation processor model has an ‘Undervolt Protection’ that can only be (and very difficultly) unlocked on CPUs type K / X. ![]()
For the 12th H-series family, it’s simply hardware-locked. ![]()
I contacted ![]() Intel to express my frustration
Intel to express my frustration ![]() with their increasing tendency to lock down their systems. They responded that it’s a security measure
with their increasing tendency to lock down their systems. They responded that it’s a security measure ![]() due to the Plundervolt vulnerability
due to the Plundervolt vulnerability ![]() , and also because most end-users tend to brick
, and also because most end-users tend to brick ![]() their hardware when undervolting.
their hardware when undervolting.
If a hardware has overheating issues ![]() , it’s not Intel’s fault, but rather the manufacturers putting a 12500H or 12700H into a 2cm-thick laptop; it’s a design flaw, and undervolting isn’t meant to compensate for the manufacturers’ design flaws they said.
, it’s not Intel’s fault, but rather the manufacturers putting a 12500H or 12700H into a 2cm-thick laptop; it’s a design flaw, and undervolting isn’t meant to compensate for the manufacturers’ design flaws they said.
![]() A notable point found on Reddit: if Intel allows it in the HK’s type, what’s the difference in terms of vulnerability with an H or P? It’s seem to be the perfect excuse to force you to go for an HX processor
A notable point found on Reddit: if Intel allows it in the HK’s type, what’s the difference in terms of vulnerability with an H or P? It’s seem to be the perfect excuse to force you to go for an HX processor ![]()
In short, the locking is hardware-based for the 12th-gen H version, regardless of the PC brand.
So, @Sweet_Kitten or @lfb6 can rightfully and logically close every kind of request about modding 12th not K/X ![]()
.
So, regarding the BIOS for my Clevo NP70PNJ - 12700H - RTX 3050, I’ll have to settle with Intel ME updates (to address the vulnerabilities detected by Intel CSME Detection Tool) and microcode updates (to address CPU vulnerabilities).
For Intel ME, I found how to do it as seen here
For the microcodes, @lfb6 guided me step by step here (Kudo to him ![]() ), and I have a BIOS with up-to-date microcodes (
), and I have a BIOS with up-to-date microcodes ( ![]() 1 [5,23 Mo] ) that seems good.
1 [5,23 Mo] ) that seems good.
But, still, due to the 12th-gen locking issues, it’s not as simple as flashing with a simple FTPW64.exe -d MODDED_BIOS.BIN -bios
However, I might have a solution:
My Clevo’s original BIOS ( ![]() 2 [27,5 Mo] ) is provided in three versions,
2 [27,5 Mo] ) is provided in three versions, NPx0PNx.12 , NPx0PNx12.efi , and NPx0PNx12.exe .
By dissecting the NPx0PNx12.exe , I can see that it uses H2OFFT-Wx64.exe to flash an isflash.bin containing the original BIOS (NPx0PNx.12) and it platform.ini.
NPx0PNx12.exe ➜ ( ![]() 3 [6,74 Mo] )
3 [6,74 Mo] )
NPx0PNx12.exe extracted (with H2OFFT-Wx64.exe and original isflash.bin) ➜ ( ![]() 4 [7,28 Mo] )
4 [7,28 Mo] )
My concern now is that I’ve created an isflash.bin with a modified BIOS and updated microcodes inside ( ![]() 5 [6,83 Mo] ). I can run
5 [6,83 Mo] ). I can run H2OFFT-Wx64.exe, which finds and accepts my modified BIOS isflash.bin.
But I’m afraid to click “OK” ![]()
Even though the microcodes are outside the BootGard area, I fear there might be another security mechanism, like a hash/salt/signature for the entire BIOS, and that in the next boot, those Intel folks might block everything before even loading the BIOS (because a different hash/salt/signature that would block/stop boot that I haven’t yet found)
I think I must use the official TOOL folder ![]() (
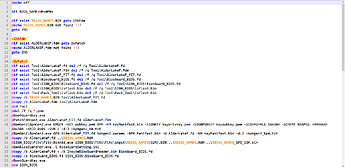
(![]() 6 [54,4 Mo] ) inside the original BIOS to packed something with complex signature like this
6 [54,4 Mo] ) inside the original BIOS to packed something with complex signature like this ![]() :
: