Hi Guys,
i messed up with my Dell Optiplex SFF 5060.
Whats happend? I found the device in the e-waste at our company. A short test showed that is still working. My tought: Perfekt for HomeServer, but Yellow Label 3 - ME Disabled. (i want to use Intel AMT for remote on / off etc.)
Long times ago i modfied an olden Optiplex 790 or so. In my thoughts this wasn’t to difficult.
But this device has a Intel Q370 with Intel I3 CPU. So i had to the CSME Packages.
As my source of inspiration i use the (Intel (Converged Security) Management Engine: Drivers, Firmware and Tools (2-15)) Website. Very good to read, all information available, a big ‘thank you’ for the author.
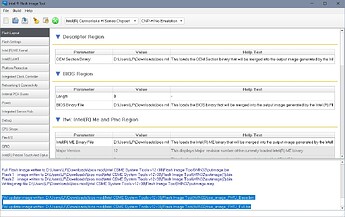
First of all i took a Dump of the SPI via fptw63.exe -d spi.bin. Just to be sure…
In the next steps i followed the instructions from the " How to use FWUpdate Tool at CSME v12: Chapter. Everything worked smoothly. But i wasn’t able to active MEBx at all. After that i updated the Dell Bios with the last recent version without any success.
I played with the service jumper. No chance to get MEBx working.
Then i found a thread here in the board relating to an other Dell Workstation. The User dumped the SPI, loaded in into FIT, changed some Parameters, rebuld the Image and then push it with fptw64.exe -desc and fptw64.exe -me back to the SPI.
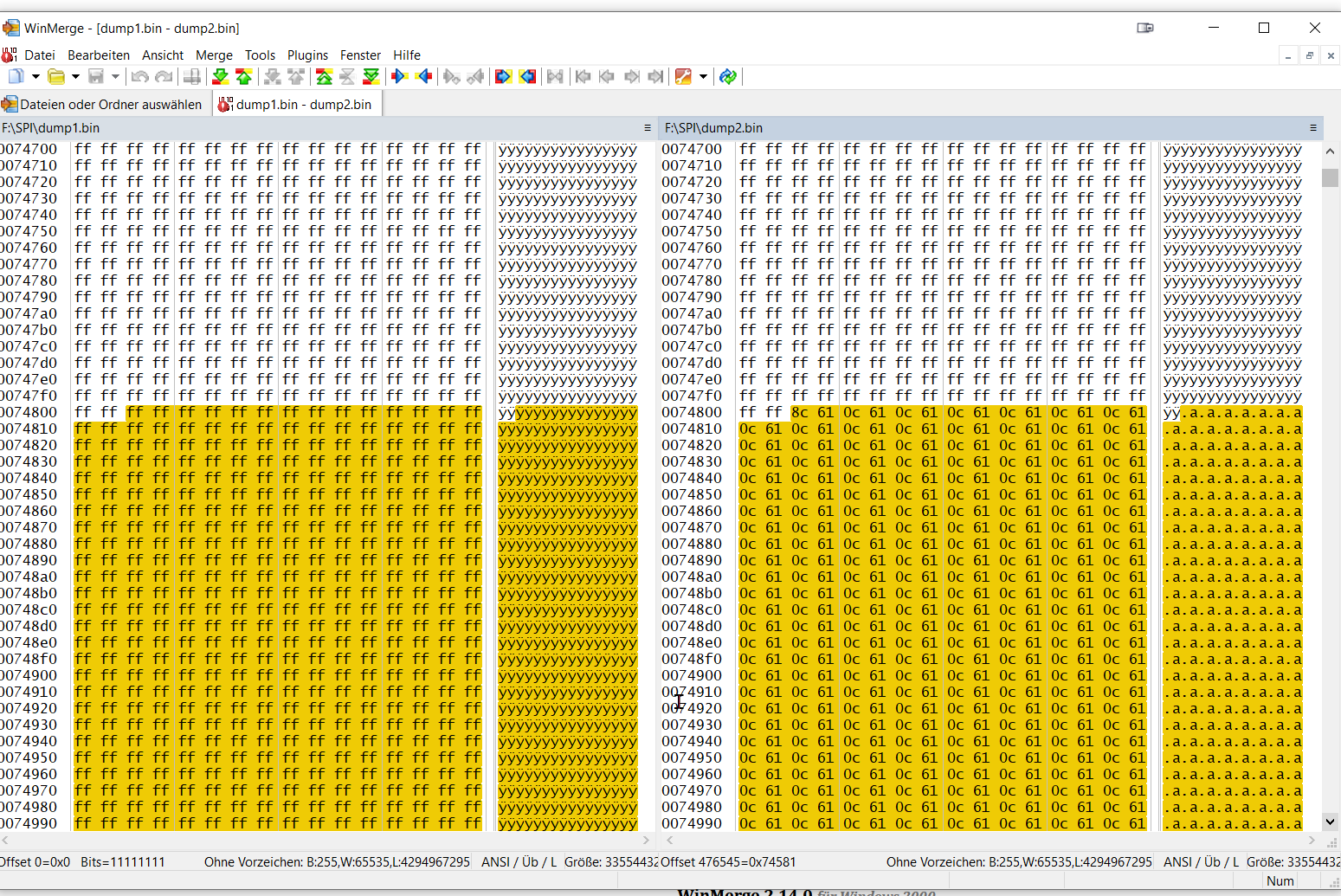
I did the same and dumb as i am, i ignored the warning about filesize within SPI and the Binary i had created before.
So now the PC makes nothing. Only 2x yellow / 1x yellow Error Code. In my eyes i overwrote the SPI with nonsense, so i have to reflash it.
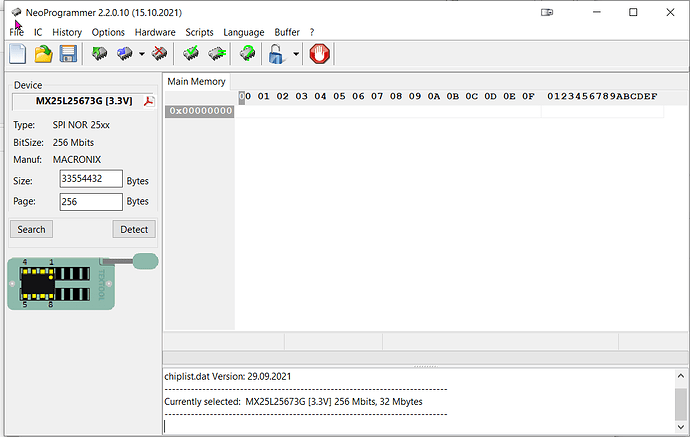
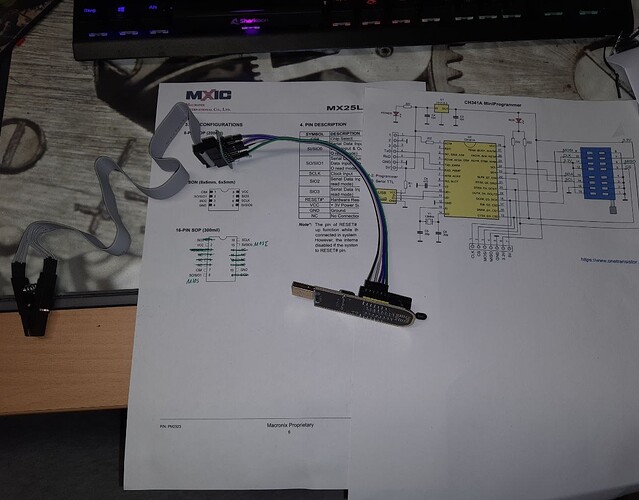
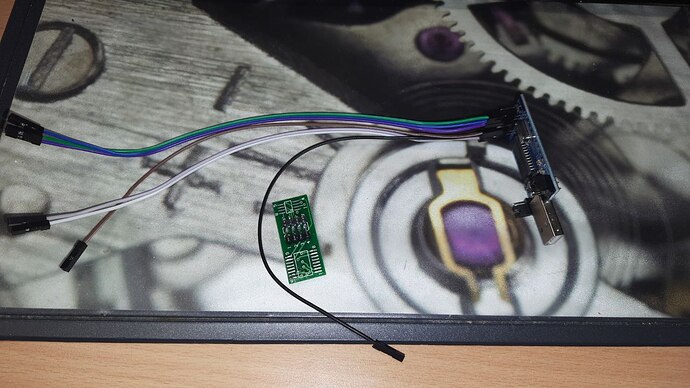
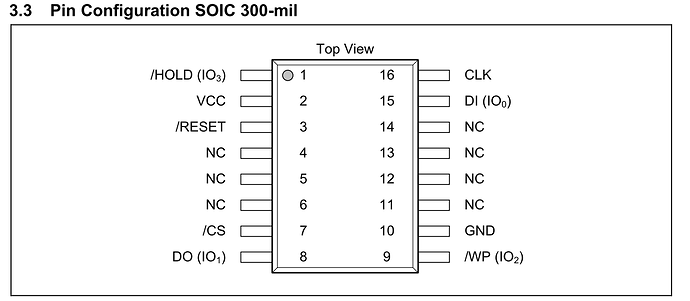
This device uses a MX25L25673GMT SPI Chip (https://www.macronix.com/Lists/Datasheet/Attachments/8761/MX25L25673G,%203V,%20256Mb,%20v1.7.pdf with an 16-PIN SOP Layout
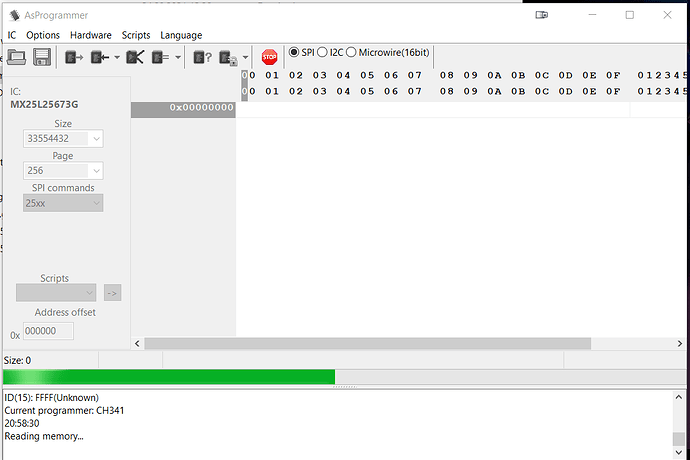
First Question to you → Can i restore the SPI with the existings Dumps i made ?
spi.bin - Google Drive => First Dump without any Dell Bios Updates
╔═══════════════════════════════════════════╗
║ ME Analyzer v1.283.3 r319 ║
╚═══════════════════════════════════════════╝
╔═════════════════════════════════════════════╗
║ spi.bin (1/1) ║
╟─────────────────────────────┬───────────────╢
║ Family │ CSE ME ║
╟─────────────────────────────┼───────────────╢
║ Version │ 12.0.6.1120 ║
╟─────────────────────────────┼───────────────╢
║ Release │ Production ║
╟─────────────────────────────┼───────────────╢
║ Type │ Extracted ║
╟─────────────────────────────┼───────────────╢
║ SKU │ Corporate H ║
╟─────────────────────────────┼───────────────╢
║ Chipset │ CNP/CMP-H B,A ║
╟─────────────────────────────┼───────────────╢
║ TCB Security Version Number │ 1 ║
╟─────────────────────────────┼───────────────╢
║ ARB Security Version Number │ 4 ║
╟─────────────────────────────┼───────────────╢
║ Version Control Number │ 10 ║
╟─────────────────────────────┼───────────────╢
║ Production Ready │ Yes ║
╟─────────────────────────────┼───────────────╢
║ OEM Configuration │ No ║
╟─────────────────────────────┼───────────────╢
║ FWUpdate Support │ Impossible ║
╟─────────────────────────────┼───────────────╢
║ Date │ 2018-07-11 ║
╟─────────────────────────────┼───────────────╢
║ File System State │ Initialized ║
╟─────────────────────────────┼───────────────╢
║ Size │ 0x77C000 ║
╟─────────────────────────────┼───────────────╢
║ Flash Image Tool │ 12.0.0.1069 ║
╚═════════════════════════════╧═══════════════╝
╔═════════════════════════════════════════════╗
║ Power Management Controller ║
╟─────────────────────────────┬───────────────╢
║ Family │ PMC ║
╟─────────────────────────────┼───────────────╢
║ Version │ 300.2.11.1015 ║
╟─────────────────────────────┼───────────────╢
║ Release │ Production ║
╟─────────────────────────────┼───────────────╢
║ Type │ Independent ║
╟─────────────────────────────┼───────────────╢
║ Chipset SKU │ H ║
╟─────────────────────────────┼───────────────╢
║ Chipset Stepping │ B ║
╟─────────────────────────────┼───────────────╢
║ TCB Security Version Number │ 3 ║
╟─────────────────────────────┼───────────────╢
║ ARB Security Version Number │ 3 ║
╟─────────────────────────────┼───────────────╢
║ Version Control Number │ 0 ║
╟─────────────────────────────┼───────────────╢
║ Production Ready │ No ║
╟─────────────────────────────┼───────────────╢
║ Date │ 2018-07-20 ║
╟─────────────────────────────┼───────────────╢
║ Size │ 0x14000 ║
╟─────────────────────────────┼───────────────╢
║ Chipset Support │ CNP ║
╚═════════════════════════════╧═══════════════╝
Warning: Outdated Database (r319 --> r320)!
Download the latest from https://github.com/platomav/MEAnalyzer/
Press enter to exit
MEInfo from the system before crash
C:\CSME\MEInfo\WIN64>MEInfoWin64.exe
Intel (R) MEInfo Version: 12.0.90.2077
Copyright (C) 2005 - 2022, Intel Corporation. All rights reserved.
General FW Information
Platform Type Desktop
FW Type Production
Last ME Reset Reason Unknown
BIOS boot State Post Boot
Slot 1 Board Manufacturer 0x00001028
Slot 2 System Assembler 0x00000000
Slot 3 Reserved 0x00000000
Capability Licensing Service Enabled
Local FWUpdate Enabled
OEM ID 68853622-EED3-4E83-8A86-6CDE315F6B78
Integrated Sensor Hub Initial Power State Disabled
Intel(R) PTT Supported Yes
Intel(R) PTT initial power-up state Disabled
OEM Tag 0x00
TLS Disabled
Intel(R) ME code versions:
BIOS Version 1.2.22
MEBx Version 12.0.0.0010
Vendor ID 8086
FW Version 12.0.6.1120 H Corporate
LMS Version Not Available
MEI Driver Version 2229.3.2.0
Wireless Hardware Version Not Available
Wireless Driver Version Not Available
IUPs Information
PMC FW Version 300.2.11.1015
LOCL FW Version 12.0.6.1120
WCOD FW Version 12.0.6.1120
PCH Information
PCH Version 0
PCH Device ID A306
PCH Step Data A0
PCH SKU Type Production PRQ Revenue
PCH Replacement State Disabled
PCH Replacement Counter 0
PCH Unlocked State Disabled
Flash Information
SPI Flash ID 1 Not Available
SPI Flash ID 2 Not Available
Host Read Access to ME Not Available
Host Write Access to ME Not Available
Host Read Access to EC Not Available
Host Write Access to EC Not Available
FW Capabilities 0x31119140
Protect Audio Video Path - PRESENT/ENABLED
Intel(R) Dynamic Application Loader - PRESENT/ENABLED
Intel(R) Platform Trust Technology - PRESENT/DISABLED
Persistent RTC and Memory - PRESENT/ENABLED
End Of Manufacturing
Post Manufacturing NVAR Config Enabled No
HW Binding Enabled
End of Manufacturing Enable Yes
Intel(R) Active Management Technology -
Intel(R) AMT State Disabled
M3 Autotest Enabled
Localized Language English
C-link Status Enabled
AMT Global State Enabled
Privacy/Security Level Default
Intel(R) Protected Audio Video Path
Keybox Not Provisioned
Attestation KeyBox Not Available
EPID Group ID 0x28C1
Re-key needed False
PAVP Supported Yes
Security Version Numbers
Minimum Allowed Anti Rollback SVN 1
Image Anti Rollback SVN 4
Trusted Computing Base SVN 0
FW Supported FPFs
FPF UEP ME FW
*In Use
--- --- -----
Enforcement Policy 0x03 0x03 0x03
EK Revoke State Not Revoked Not Revoked Not Revoked
PTT Enabled Enabled Enabled
OEM ID 0x00 0x00 0x00
OEM Key Manifest Present Not Present Not Present Not Present
OEM Platform ID 0x00 0x00 0x00
OEM Secure Boot Policy 0x3F9 0x3F9 0x3F9
CPU Debugging Enabled Enabled Enabled
BSP Initialization Enabled Enabled Enabled
Protect BIOS Environment Enabled Enabled Enabled
Measured Boot Enabled Enabled Enabled
Verified Boot Enabled Enabled Enabled
Key Manifest ID 0x0F 0x0F 0x0F
Persistent PRTC Backup Power Enabled Enabled Enabled
RPMB Migration Done Disabled Disabled Disabled
SOC Config Lock Done Not Done Done
SPI Boot Source Enabled Enabled Enabled
TXT Supported Disabled Disabled Disabled
ACM SVN FPF 0x02
BSMM SVN FPF 0x00
KM SVN FPF 0x00
OEM Public Key Hash FPF 69602F34CC9D121ECB7785F4F5CA4153ADC35633FF13A76B914FB2FE2835F691
OEM Public Key Hash UEP 69602F34CC9D121ECB7785F4F5CA4153ADC35633FF13A76B914FB2FE2835F691
OEM Public Key Hash ME FW 69602F34CC9D121ECB7785F4F5CA4153ADC35633FF13A76B914FB2FE2835F691
PTT Lockout Override Counter FPF 0x00
C:\CSME\MEInfo\WIN64>
Found a thread about SPI Flashing this chip → https://winraid.level1techs.com/t/problems-flashing-mx25l25673g/34664
Here the Image i flashed via fptw64.exe which makes my device unusable
https://drive.google.com/file/d/1KDY58MmHOiT3_s0tUkfTl2l658CPb5H_/view?usp=sharing
Here the last dump from spi (made with fptw64 -d) (recent BIOS Update from Dell, maybe older ME FW) (used as base image for FIT)
https://drive.google.com/file/d/1tKO4IVKQkb4BvL0S2MY5Ghhtumqro1u7/view?usp=sharing
After FIT i replaced ME Sub Region with this file ‘12.0.92.2145_COR_H_BA_PRD_EXTR-Y_3AC88DBF.bin’