Hello,
I have 2 old PCs Fujitsu Siemens Esprimo E5730 both with the same latest BIOS version but with different AMT version; I did not found on Fujitsu Siemens drivers/support site anything that can help me to upgrade AMT.
I try to upgrade the oldest AMT to latest version without success until now:
- AMT unprovisioned/provisioned
- TPM cleared - disable/enabled
- from DOS
- from win 8.1 x64
…
If anybody can provide some help.
thank you
MEInfo from win 8.1 x64
Latest AMT 5.2.70.1046:
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
Intel(R) MEInfo Version: 5.0.0.1167
PMXUtil: Error during PMX Call: sseidrvdll32e.dll!IDRVInstallDriver(): Failed to start loaded service err: 1275
Reading Fw Status Register....
PMXUtil: Error during PMX Call: sseidrvdll32e.dll!IDRVInstallDriver(): Failed to start loaded service err: 1275
...
PMXUtil: Error during PMX Call: sseidrvdll32e.dll!IDRVInit(): Failed VerAddVersion() call
FW Status Register: 0X00000000
BIOS Version: 6.00 R1.19.2824.A1
Intel(R) Standard Manageability code versions:
Flash: 5.2.70 Netstack: 5.2.70
Apps: 5.2.70 Intel(R) Standard Manageability: 5.2.70
FW Capabilities: 62
ASF2
Intel(R) AMT
Intel(R) Standard Manageability
Intel(R) QST
Intel(R) TPM
VendorID: 8086
Build Number: 1046
Manageability Mode: Intel(R) Standard Manageability
UNS Version: 5.0.5.1018
LMS Version: 5.2.0.1018
MEI Driver version: 5.2.0.1008
Link status: Link down
Cryptography fuse: Enabled
Flash protection: Enabled
Last ME reset reason: Global system reset
Configuration state: Completed
BIOS boot State: Post Boot
MAC Address: 00-19-39-4d-0d-a1
FWU Override Counter: Always
FWU Override Qualifier: Always
IP Address: 0.0.0.0
MEBx Version: 5.0.5.8
FT Version: 5.2
FT Build Number: 1046
Local FWUpdate: Enabled
Secure FWUpdate: Disabled
Remote Connectivity Service Capability: False
Configuration Mode: Small Business
TPM Vendor ID: INTC
TPM SPEC Version: 1.2.5.2
TPM FW Version: 5.2
TPM Firmware Build Number: 1046
TPM State: Operational
TPM Operational Mode: Enabled Owned Active
iTPM - FIPS 140-2: False
iTPM - Failed Attempts Threshold:61440
iTPM - Initial lockout period: 526
iTPM - Lockout multiplier: 4096
iTPM - Fade-out period: 0
iTPM - Physical presence life time lock flag: False
iTPM - Physical presence command enabled flag: True
iTPM - Physical presence HW enabled flag: False
TPM fuses (MCH/ICH/soft strap MCH/ soft strap ICH): Enabled
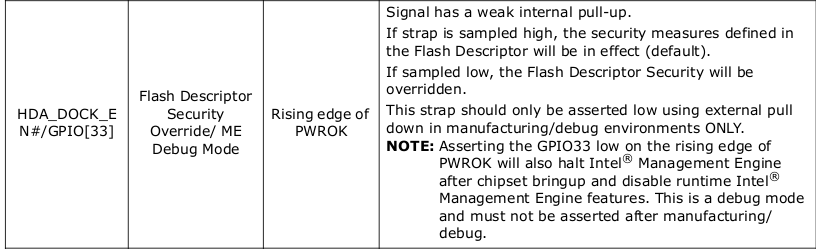
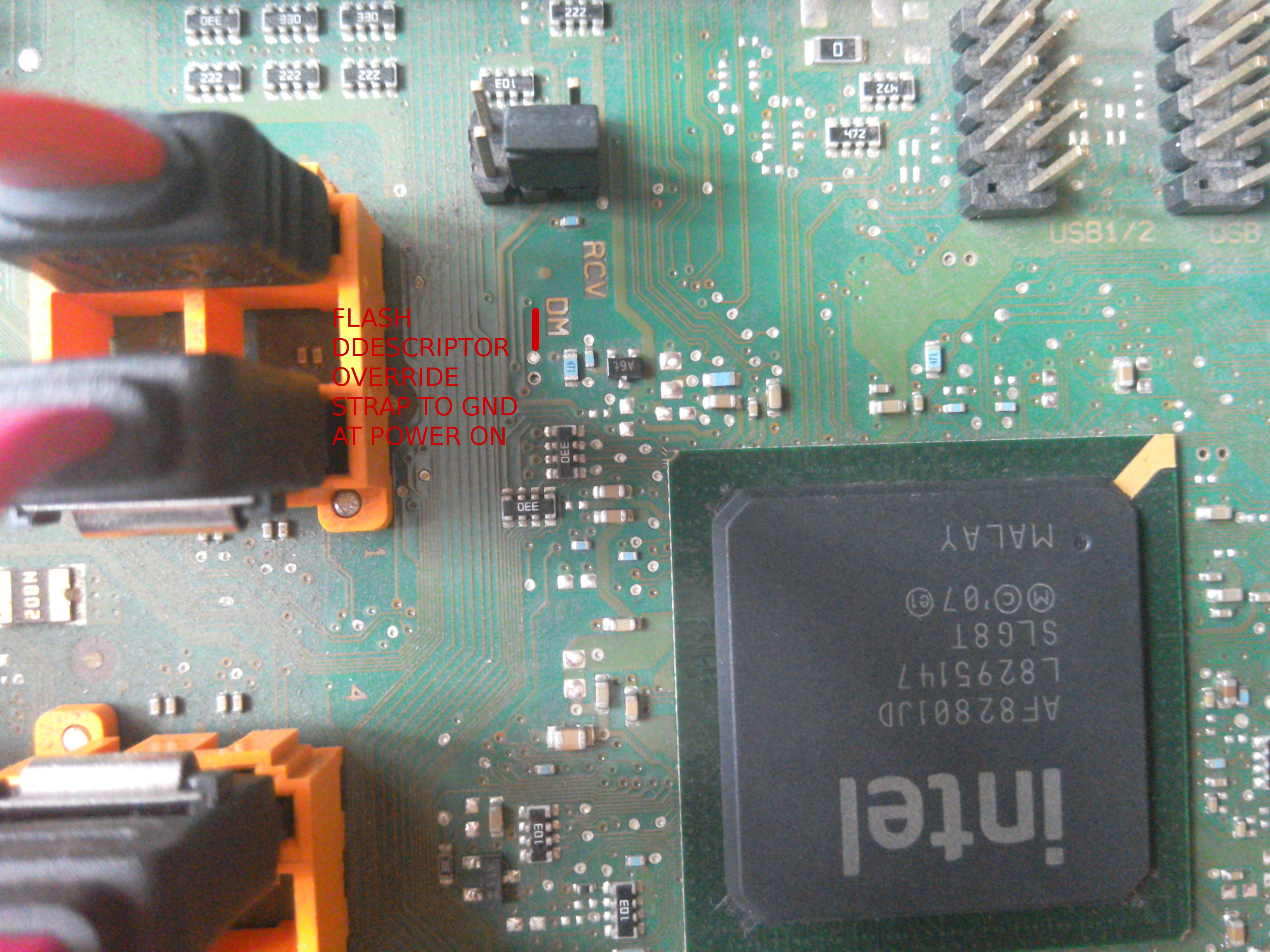
FW behavior on Flash Descriptor Override Pin-Strap: Halt
Oldest AMT 5.0.1.1111 the one I try to upgrade:
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
Intel(R) MEInfo Version: 5.0.0.1167
PMXUtil: Error during PMX Call: sseidrvdll32e.dll!IDRVInstallDriver(): Failed to start loaded service err: 1275
Reading Fw Status Register....
PMXUtil: Error during PMX Call: sseidrvdll32e.dll!IDRVInstallDriver(): Failed to start loaded service err: 1275
...
PMXUtil: Error during PMX Call: sseidrvdll32e.dll!IDRVInit(): Failed VerAddVersion() call
FW Status Register: 0X00000000
BIOS Version: 6.00 R1.19.2824.A1
Intel(R) Standard Manageability code versions:
Flash: 5.0.1 Netstack: 5.0.1
Apps: 5.0.1 Intel(R) Standard Manageability: 5.0.1
FW Capabilities: 62
ASF2
Intel(R) AMT
Intel(R) Standard Manageability
Intel(R) QST
Intel(R) TPM
VendorID: 8086
Build Number: 1111
Manageability Mode: Intel(R) Standard Manageability
UNS Version: 5.0.5.1018
LMS Version: 5.2.0.1018
MEI Driver version: 5.2.0.1008
Link status: Link down
Cryptography fuse: Enabled
Flash protection: Enabled
Last ME reset reason: Power up
Configuration state: Completed
BIOS boot State: Post Boot
MAC Address: 00-19-39-47-bb-dd
FWU Override Counter: Always
FWU Override Qualifier: Always
IP Address: 0.0.0.0
MEBx Version: 5.0.5.8
FT Version: 5.0
FT Build Number: 1111
Local FWUpdate: Enabled
Secure FWUpdate: Disabled
Remote Connectivity Service Capability: False
Configuration Mode: Small Business
TPM Vendor ID: INTC
TPM SPEC Version: 1.2.5.0
TPM FW Version: 5.0
TPM Firmware Build Number: 1111
TPM State: Operational
TPM Operational Mode: Enabled Owned Active
iTPM - FIPS 140-2: False
iTPM - Failed Attempts Threshold:61440
iTPM - Initial lockout period: 526
iTPM - Lockout multiplier: 4096
iTPM - Fade-out period: 0
iTPM - Physical presence life time lock flag: False
iTPM - Physical presence command enabled flag: True
iTPM - Physical presence HW enabled flag: False
TPM fuses (MCH/ICH/soft strap MCH/ soft strap ICH): Enabled
FW behavior on Flash Descriptor Override Pin-Strap: Halt
Try to Flash AMT from win8.1 without success:
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
FWUpdLcl.exe 5.2.70.1046.bin -generic -verbose
Firmware Update Utility Version 5.2.50.1042
Copyright (C) 2007-2011 , Intel Corporation. All Rights Reserved
Trying to connect to MEI driver.Connected to HECI driver, version: 5.2.0.1008
***** Flash Info ******
Version : 5.0.1.1111
Last Update Staus : 1
SKU : (2110)
: Intel (R) QST
: ASF2
: Intel (R) AMT
: Intel Standard Manageability
: Intel (R) TPM
EnabledUpdateInterfaces : 5
***** Image Info ******
Version : 5.2.70.1046
SKU : (2110)
: Intel (R) QST
: ASF2
: Intel (R) AMT
: Intel Standard Manageability
: Intel (R) TPM
Error (8721): Firmware update through TPM is enabled. Use -tpm switch
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
FWUpdLcl.exe 5.2.70.1046.bin -tpm -verbose
Firmware Update Utility Version 5.2.50.1042
Copyright (C) 2007-2011 , Intel Corporation. All Rights Reserved
Trying to connect to MEI driver.Connected to HECI driver, version: 5.2.0.1008
***** Flash Info ******
Version : 5.0.1.1111
Last Update Staus : 1
SKU : (2110)
: Intel (R) QST
: ASF2
: Intel (R) AMT
: Intel Standard Manageability
: Intel (R) TPM
EnabledUpdateInterfaces : 5
***** Image Info ******
Version : 5.2.70.1046
SKU : (2110)
: Intel (R) QST
: ASF2
: Intel (R) AMT
: Intel Standard Manageability
: Intel (R) TPM
Communication Mode: TPM
MEinfo from DOS:
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
Copyright(C) 2005-08 Intel(R) Corporation. All Rights Reserved.
Intel(R) MEInfo Version: 5.0.0.1167
Reading Fw Status Register....
FW Status Register: 0X3009065A
BIOS Version: 6.00 R1.19.2824.A1
Intel(R) Standard Manageability code versions:
Flash: 5.0.1 Netstack: 5.0.1
Apps: 5.0.1 Intel(R) Standard Manageability: 5.0.1
FW Capabilities: 62
ASF2
Intel(R) AMT
Intel(R) Standard Manageability
Intel(R) QST
Intel(R) TPM
VendorID: 8086
Build Number: 1111
Manageability Mode: Intel(R) Standard Manageability
Link status: Link down
Cryptography fuse: Enabled
Flash protection: Enabled
Last ME reset reason: Global system reset
Configuration state: Completed
BIOS boot State: Post Boot
MAC Address: 00-19-39-47-bb-dd
FWU Override Counter: Always
FWU Override Qualifier: Always
IP Address: 0.0.0.0
MEBx Version: 5.0.5.8
FT Version: 5.0
FT Build Number: 1111
Local FWUpdate: Enabled
Secure FWUpdate: Disabled
Remote Connectivity Service Capability: False
Configuration Mode: Small Business
TPM Vendor ID: INTC
TPM SPEC Version: 1.2.5.0
TPM FW Version: 5.0
TPM Firmware Build Number: 1111
TPM State: Operational
TPM Operational Mode: Enabled Owned Inactive
iTPM - FIPS 140-2: False
iTPM - Failed Attempts Threshold:10
iTPM - Initial lockout period: 240
iTPM - Lockout multiplier: 2
iTPM - Fade-out period: 3600
iTPM - Physical presence life time lock flag: False
iTPM - Physical presence command enabled flag: True
iTPM - Physical presence HW enabled flag: False
TPM fuses (MCH/ICH/soft strap MCH/ soft strap ICH): Enabled
FW behavior on Flash Descriptor Override Pin-Strap: Halt
Try to Flash AMT from DOS without success:
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
Firmware Update Utility Version 5.2.50.1042
Copyright (C) 2007-2011 , Intel Corporation. All Rights Reserved
Trying to connect to MEI driver.
***** Flash Info ******
Version : 5.0.1.1111
Last Update Staus : 1
SKU : (2110)
: Intel (R) QST
: ASF2
: Intel (R) AMT
: Intel Standard Manageability
: Intel (R) TPM
EnabledUpdateInterfaces : 5
***** Image Info ******
Version : 5.2.70.1046
SKU : (2110)
: Intel (R) QST
: ASF2
: Intel (R) AMT
: Intel Standard Manageability
: Intel (R) TPM
Communication Mode: TPM
FW image is uploading through TPM.
EDIT by Fernando: To save space I have put the codes into "spoilers" (can be opened by clicking onto them).