@ igorsk
[Discussion] UBU Tool related Questions, Reports and Suggestions (191)
My LGA771+LGA775 microcodes colection is almost finalized.
//edit: 16th April 2017. LGA771-775 colection update
//edit2: 3rd February 2018, updated
All credit goes to plutomaniac.But I’m still looking for latest 10676h, 10677h and 1067Ah microcodes for platforms 0, 2, 4, 6.
Intel Microcode List ver0.4a
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
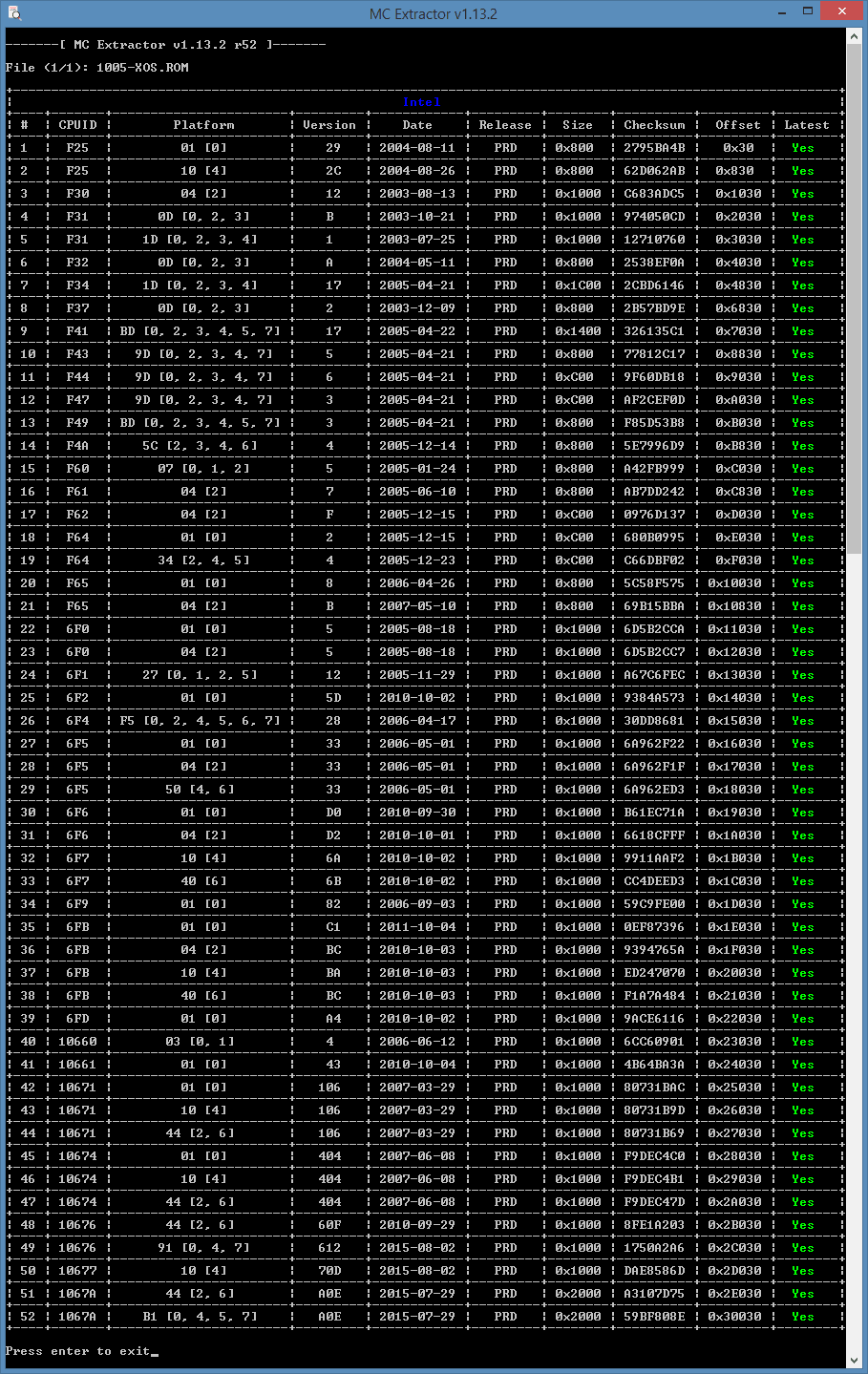
ntelmicrocodelist.exe 1005-XOS.ROM
Intel Microcode List ver0.4a
CPUID=F25 Rev=29 2004/08/11 CRC=2795BA4B Off=30 Size=800 Plat=0
CPUID=F25 Rev=2C 2004/08/26 CRC=62D062AB Off=830 Size=800 Plat=4
CPUID=F30 Rev=12 2003/08/13 CRC=C683ADC5 Off=1030 Size=1000 Plat=2
CPUID=F31 Rev=0B 2003/10/21 CRC=974050CD Off=2030 Size=1000 Plat=0,2,3
CPUID=F31 Rev=01 2003/07/25 CRC=12710760 Off=3030 Size=1000 Plat=0,2,3,4
CPUID=F32 Rev=0A 2004/05/11 CRC=2538EF0A Off=4030 Size=800 Plat=0,2,3
CPUID=F34 Rev=17 2005/04/21 CRC=2CBD6146 Off=4830 Size=1C00 Plat=0,2,3,4
CPUID=F37 Rev=02 2003/12/09 CRC=2B57BD9E Off=6830 Size=800 Plat=0,2,3
CPUID=F41 Rev=17 2005/04/22 CRC=326135C1 Off=7030 Size=1400 Plat=0,2,3,4,5,7
CPUID=F43 Rev=05 2005/04/21 CRC=77812C17 Off=8830 Size=800 Plat=0,2,3,4,7
CPUID=F44 Rev=06 2005/04/21 CRC=9F60DB18 Off=9030 Size=C00 Plat=0,2,3,4,7
CPUID=F47 Rev=03 2005/04/21 CRC=AF2CEF0D Off=A030 Size=C00 Plat=0,2,3,4,7
CPUID=F49 Rev=03 2005/04/21 CRC=F85D53B8 Off=B030 Size=800 Plat=0,2,3,4,5,7
CPUID=F4A Rev=04 2005/12/14 CRC=5E7996D9 Off=B830 Size=800 Plat=2,3,4,6
CPUID=F60 Rev=05 2005/01/24 CRC=A42FB999 Off=C030 Size=800 Plat=0,1,2
CPUID=F61 Rev=07 2005/06/10 CRC=AB7DD242 Off=C830 Size=800 Plat=2
CPUID=F62 Rev=0F 2005/12/15 CRC=0976D137 Off=D030 Size=C00 Plat=2
CPUID=F64 Rev=02 2005/12/15 CRC=680B0995 Off=E030 Size=C00 Plat=0
CPUID=F64 Rev=04 2005/12/23 CRC=C66DBF02 Off=F030 Size=C00 Plat=2,4,5
CPUID=F65 Rev=08 2006/04/26 CRC=5C58F575 Off=10030 Size=800 Plat=0
CPUID=F65 Rev=0B 2007/05/10 CRC=69B15BBA Off=10830 Size=800 Plat=2
CPUID=6F0 Rev=05 2005/08/18 CRC=6D5B2CCA Off=11030 Size=1000 Plat=0
CPUID=6F0 Rev=05 2005/08/18 CRC=6D5B2CC7 Off=12030 Size=1000 Plat=2
CPUID=6F1 Rev=12 2005/11/29 CRC=A67C6FEC Off=13030 Size=1000 Plat=0,1,2,5
CPUID=6F2 Rev=5D 2010/10/02 CRC=9384A573 Off=14030 Size=1000 Plat=0
CPUID=6F4 Rev=28 2006/04/17 CRC=30DD8681 Off=15030 Size=1000 Plat=0,2,4,5,6,7
CPUID=6F5 Rev=33 2006/05/01 CRC=6A962F22 Off=16030 Size=1000 Plat=0
CPUID=6F5 Rev=33 2006/05/01 CRC=6A962F1F Off=17030 Size=1000 Plat=2
CPUID=6F5 Rev=33 2006/05/01 CRC=6A962ED3 Off=18030 Size=1000 Plat=4,6
CPUID=6F6 Rev=D0 2010/09/30 CRC=B61EC71A Off=19030 Size=1000 Plat=0
CPUID=6F6 Rev=D2 2010/10/01 CRC=6618CFFF Off=1A030 Size=1000 Plat=2
CPUID=6F7 Rev=6A 2010/10/02 CRC=9911AAF2 Off=1B030 Size=1000 Plat=4
CPUID=6F7 Rev=6B 2010/10/02 CRC=CC4DEED3 Off=1C030 Size=1000 Plat=6
CPUID=6F9 Rev=82 2006/09/03 CRC=59C9FE00 Off=1D030 Size=1000 Plat=0
CPUID=6FB Rev=C1 2011/10/04 CRC=0EF87396 Off=1E030 Size=1000 Plat=0
CPUID=6FB Rev=BC 2010/10/03 CRC=9394765A Off=1F030 Size=1000 Plat=2
CPUID=6FB Rev=BA 2010/10/03 CRC=ED247070 Off=20030 Size=1000 Plat=4
CPUID=6FB Rev=BC 2010/10/03 CRC=F1A7A484 Off=21030 Size=1000 Plat=6
CPUID=6FD Rev=A4 2010/10/02 CRC=9ACE6116 Off=22030 Size=1000 Plat=0
CPUID=10660 Rev=04 2006/06/12 CRC=6CC60901 Off=23030 Size=1000 Plat=0,1
CPUID=10661 Rev=43 2010/10/04 CRC=4B64BA3A Off=24030 Size=1000 Plat=0
CPUID=10671 Rev=106 2007/03/29 CRC=80731BAC Off=25030 Size=1000 Plat=0
CPUID=10671 Rev=106 2007/03/29 CRC=80731B9D Off=26030 Size=1000 Plat=4
CPUID=10671 Rev=106 2007/03/29 CRC=80731B69 Off=27030 Size=1000 Plat=2,6
CPUID=10674 Rev=404 2007/06/08 CRC=F9DEC4C0 Off=28030 Size=1000 Plat=0
CPUID=10674 Rev=404 2007/06/08 CRC=F9DEC4B1 Off=29030 Size=1000 Plat=4
CPUID=10674 Rev=404 2007/06/08 CRC=F9DEC47D Off=2A030 Size=1000 Plat=2,6
CPUID=10676 Rev=60F 2010/09/29 CRC=8FE1A203 Off=2B030 Size=1000 Plat=2,6
CPUID=10676 Rev=612 2015/08/02 CRC=1750A2A6 Off=2C030 Size=1000 Plat=0,4,7
CPUID=10677 Rev=70D 2015/08/02 CRC=DAE8586D Off=2D030 Size=1000 Plat=4
CPUID=1067A Rev=A0E 2015/07/29 CRC=A3107D75 Off=2E030 Size=2000 Plat=2,6
CPUID=1067A Rev=A0E 2015/07/29 CRC=59BF808E Off=30030 Size=2000 Plat=0,4,5,7
MC Extractor v1.13.2 r52
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
-------[ MC Extractor v1.13.2 r52 ]-------
File (1/1): 1005-XOS.ROM
+------------------------------------------------------------------------------------------------------------+
| Intel |
+----+-------+-----------------------+---------+------------+---------+--------+----------+---------+--------+
| # | CPUID | Platform | Version | Date | Release | Size | Checksum | Offset | Latest |
+----+-------+-----------------------+---------+------------+---------+--------+----------+---------+--------+
| 1 | F25 | 01 [0] | 29 | 2004-08-11 | PRD | 0x800 | 2795BA4B | 0x30 | Yes |
+----+-------+-----------------------+---------+------------+---------+--------+----------+---------+--------+
| 2 | F25 | 10 [4] | 2C | 2004-08-26 | PRD | 0x800 | 62D062AB | 0x830 | Yes |
+----+-------+-----------------------+---------+------------+---------+--------+----------+---------+--------+
| 3 | F30 | 04 [2] | 12 | 2003-08-13 | PRD | 0x1000 | C683ADC5 | 0x1030 | Yes |
+----+-------+-----------------------+---------+------------+---------+--------+----------+---------+--------+
| 4 | F31 | 0D [0, 2, 3] | B | 2003-10-21 | PRD | 0x1000 | 974050CD | 0x2030 | Yes |
+----+-------+-----------------------+---------+------------+---------+--------+----------+---------+--------+
| 5 | F31 | 1D [0, 2, 3, 4] | 1 | 2003-07-25 | PRD | 0x1000 | 12710760 | 0x3030 | Yes |
+----+-------+-----------------------+---------+------------+---------+--------+----------+---------+--------+
| 6 | F32 | 0D [0, 2, 3] | A | 2004-05-11 | PRD | 0x800 | 2538EF0A | 0x4030 | Yes |
+----+-------+-----------------------+---------+------------+---------+--------+----------+---------+--------+
| 7 | F34 | 1D [0, 2, 3, 4] | 17 | 2005-04-21 | PRD | 0x1C00 | 2CBD6146 | 0x4830 | Yes |
+----+-------+-----------------------+---------+------------+---------+--------+----------+---------+--------+
| 8 | F37 | 0D [0, 2, 3] | 2 | 2003-12-09 | PRD | 0x800 | 2B57BD9E | 0x6830 | Yes |
+----+-------+-----------------------+---------+------------+---------+--------+----------+---------+--------+
| 9 | F41 | BD [0, 2, 3, 4, 5, 7] | 17 | 2005-04-22 | PRD | 0x1400 | 326135C1 | 0x7030 | Yes |
+----+-------+-----------------------+---------+------------+---------+--------+----------+---------+--------+
| 10 | F43 | 9D [0, 2, 3, 4, 7] | 5 | 2005-04-21 | PRD | 0x800 | 77812C17 | 0x8830 | Yes |
+----+-------+-----------------------+---------+------------+---------+--------+----------+---------+--------+
| 11 | F44 | 9D [0, 2, 3, 4, 7] | 6 | 2005-04-21 | PRD | 0xC00 | 9F60DB18 | 0x9030 | Yes |
+----+-------+-----------------------+---------+------------+---------+--------+----------+---------+--------+
| 12 | F47 | 9D [0, 2, 3, 4, 7] | 3 | 2005-04-21 | PRD | 0xC00 | AF2CEF0D | 0xA030 | Yes |
+----+-------+-----------------------+---------+------------+---------+--------+----------+---------+--------+
| 13 | F49 | BD [0, 2, 3, 4, 5, 7] | 3 | 2005-04-21 | PRD | 0x800 | F85D53B8 | 0xB030 | Yes |
+----+-------+-----------------------+---------+------------+---------+--------+----------+---------+--------+
| 14 | F4A | 5C [2, 3, 4, 6] | 4 | 2005-12-14 | PRD | 0x800 | 5E7996D9 | 0xB830 | Yes |
+----+-------+-----------------------+---------+------------+---------+--------+----------+---------+--------+
| 15 | F60 | 07 [0, 1, 2] | 5 | 2005-01-24 | PRD | 0x800 | A42FB999 | 0xC030 | Yes |
+----+-------+-----------------------+---------+------------+---------+--------+----------+---------+--------+
| 16 | F61 | 04 [2] | 7 | 2005-06-10 | PRD | 0x800 | AB7DD242 | 0xC830 | Yes |
+----+-------+-----------------------+---------+------------+---------+--------+----------+---------+--------+
| 17 | F62 | 04 [2] | F | 2005-12-15 | PRD | 0xC00 | 0976D137 | 0xD030 | Yes |
+----+-------+-----------------------+---------+------------+---------+--------+----------+---------+--------+
| 18 | F64 | 01 [0] | 2 | 2005-12-15 | PRD | 0xC00 | 680B0995 | 0xE030 | Yes |
+----+-------+-----------------------+---------+------------+---------+--------+----------+---------+--------+
| 19 | F64 | 34 [2, 4, 5] | 4 | 2005-12-23 | PRD | 0xC00 | C66DBF02 | 0xF030 | Yes |
+----+-------+-----------------------+---------+------------+---------+--------+----------+---------+--------+
| 20 | F65 | 01 [0] | 8 | 2006-04-26 | PRD | 0x800 | 5C58F575 | 0x10030 | Yes |
+----+-------+-----------------------+---------+------------+---------+--------+----------+---------+--------+
| 21 | F65 | 04 [2] | B | 2007-05-10 | PRD | 0x800 | 69B15BBA | 0x10830 | Yes |
+----+-------+-----------------------+---------+------------+---------+--------+----------+---------+--------+
| 22 | 6F0 | 01 [0] | 5 | 2005-08-18 | PRD | 0x1000 | 6D5B2CCA | 0x11030 | Yes |
+----+-------+-----------------------+---------+------------+---------+--------+----------+---------+--------+
| 23 | 6F0 | 04 [2] | 5 | 2005-08-18 | PRD | 0x1000 | 6D5B2CC7 | 0x12030 | Yes |
+----+-------+-----------------------+---------+------------+---------+--------+----------+---------+--------+
| 24 | 6F1 | 27 [0, 1, 2, 5] | 12 | 2005-11-29 | PRD | 0x1000 | A67C6FEC | 0x13030 | Yes |
+----+-------+-----------------------+---------+------------+---------+--------+----------+---------+--------+
| 25 | 6F2 | 01 [0] | 5D | 2010-10-02 | PRD | 0x1000 | 9384A573 | 0x14030 | Yes |
+----+-------+-----------------------+---------+------------+---------+--------+----------+---------+--------+
| 26 | 6F4 | F5 [0, 2, 4, 5, 6, 7] | 28 | 2006-04-17 | PRD | 0x1000 | 30DD8681 | 0x15030 | Yes |
+----+-------+-----------------------+---------+------------+---------+--------+----------+---------+--------+
| 27 | 6F5 | 01 [0] | 33 | 2006-05-01 | PRD | 0x1000 | 6A962F22 | 0x16030 | Yes |
+----+-------+-----------------------+---------+------------+---------+--------+----------+---------+--------+
| 28 | 6F5 | 04 [2] | 33 | 2006-05-01 | PRD | 0x1000 | 6A962F1F | 0x17030 | Yes |
+----+-------+-----------------------+---------+------------+---------+--------+----------+---------+--------+
| 29 | 6F5 | 50 [4, 6] | 33 | 2006-05-01 | PRD | 0x1000 | 6A962ED3 | 0x18030 | Yes |
+----+-------+-----------------------+---------+------------+---------+--------+----------+---------+--------+
| 30 | 6F6 | 01 [0] | D0 | 2010-09-30 | PRD | 0x1000 | B61EC71A | 0x19030 | Yes |
+----+-------+-----------------------+---------+------------+---------+--------+----------+---------+--------+
| 31 | 6F6 | 04 [2] | D2 | 2010-10-01 | PRD | 0x1000 | 6618CFFF | 0x1A030 | Yes |
+----+-------+-----------------------+---------+------------+---------+--------+----------+---------+--------+
| 32 | 6F7 | 10 [4] | 6A | 2010-10-02 | PRD | 0x1000 | 9911AAF2 | 0x1B030 | Yes |
+----+-------+-----------------------+---------+------------+---------+--------+----------+---------+--------+
| 33 | 6F7 | 40 [6] | 6B | 2010-10-02 | PRD | 0x1000 | CC4DEED3 | 0x1C030 | Yes |
+----+-------+-----------------------+---------+------------+---------+--------+----------+---------+--------+
| 34 | 6F9 | 01 [0] | 82 | 2006-09-03 | PRD | 0x1000 | 59C9FE00 | 0x1D030 | Yes |
+----+-------+-----------------------+---------+------------+---------+--------+----------+---------+--------+
| 35 | 6FB | 01 [0] | C1 | 2011-10-04 | PRD | 0x1000 | 0EF87396 | 0x1E030 | Yes |
+----+-------+-----------------------+---------+------------+---------+--------+----------+---------+--------+
| 36 | 6FB | 04 [2] | BC | 2010-10-03 | PRD | 0x1000 | 9394765A | 0x1F030 | Yes |
+----+-------+-----------------------+---------+------------+---------+--------+----------+---------+--------+
| 37 | 6FB | 10 [4] | BA | 2010-10-03 | PRD | 0x1000 | ED247070 | 0x20030 | Yes |
+----+-------+-----------------------+---------+------------+---------+--------+----------+---------+--------+
| 38 | 6FB | 40 [6] | BC | 2010-10-03 | PRD | 0x1000 | F1A7A484 | 0x21030 | Yes |
+----+-------+-----------------------+---------+------------+---------+--------+----------+---------+--------+
| 39 | 6FD | 01 [0] | A4 | 2010-10-02 | PRD | 0x1000 | 9ACE6116 | 0x22030 | Yes |
+----+-------+-----------------------+---------+------------+---------+--------+----------+---------+--------+
| 40 | 10660 | 03 [0, 1] | 4 | 2006-06-12 | PRD | 0x1000 | 6CC60901 | 0x23030 | Yes |
+----+-------+-----------------------+---------+------------+---------+--------+----------+---------+--------+
| 41 | 10661 | 01 [0] | 43 | 2010-10-04 | PRD | 0x1000 | 4B64BA3A | 0x24030 | Yes |
+----+-------+-----------------------+---------+------------+---------+--------+----------+---------+--------+
| 42 | 10671 | 01 [0] | 106 | 2007-03-29 | PRD | 0x1000 | 80731BAC | 0x25030 | Yes |
+----+-------+-----------------------+---------+------------+---------+--------+----------+---------+--------+
| 43 | 10671 | 10 [4] | 106 | 2007-03-29 | PRD | 0x1000 | 80731B9D | 0x26030 | Yes |
+----+-------+-----------------------+---------+------------+---------+--------+----------+---------+--------+
| 44 | 10671 | 44 [2, 6] | 106 | 2007-03-29 | PRD | 0x1000 | 80731B69 | 0x27030 | Yes |
+----+-------+-----------------------+---------+------------+---------+--------+----------+---------+--------+
| 45 | 10674 | 01 [0] | 404 | 2007-06-08 | PRD | 0x1000 | F9DEC4C0 | 0x28030 | Yes |
+----+-------+-----------------------+---------+------------+---------+--------+----------+---------+--------+
| 46 | 10674 | 10 [4] | 404 | 2007-06-08 | PRD | 0x1000 | F9DEC4B1 | 0x29030 | Yes |
+----+-------+-----------------------+---------+------------+---------+--------+----------+---------+--------+
| 47 | 10674 | 44 [2, 6] | 404 | 2007-06-08 | PRD | 0x1000 | F9DEC47D | 0x2A030 | Yes |
+----+-------+-----------------------+---------+------------+---------+--------+----------+---------+--------+
| 48 | 10676 | 44 [2, 6] | 60F | 2010-09-29 | PRD | 0x1000 | 8FE1A203 | 0x2B030 | Yes |
+----+-------+-----------------------+---------+------------+---------+--------+----------+---------+--------+
| 49 | 10676 | 91 [0, 4, 7] | 612 | 2015-08-02 | PRD | 0x1000 | 1750A2A6 | 0x2C030 | Yes |
+----+-------+-----------------------+---------+------------+---------+--------+----------+---------+--------+
| 50 | 10677 | 10 [4] | 70D | 2015-08-02 | PRD | 0x1000 | DAE8586D | 0x2D030 | Yes |
+----+-------+-----------------------+---------+------------+---------+--------+----------+---------+--------+
| 51 | 1067A | 44 [2, 6] | A0E | 2015-07-29 | PRD | 0x2000 | A3107D75 | 0x2E030 | Yes |
+----+-------+-----------------------+---------+------------+---------+--------+----------+---------+--------+
| 52 | 1067A | B1 [0, 4, 5, 7] | A0E | 2015-07-29 | PRD | 0x2000 | 59BF808E | 0x30030 | Yes |
+----+-------+-----------------------+---------+------------+---------+--------+----------+---------+--------+
2018-02-03 complete LGA771-775 NetBurst-C2Q 45 nm.zip (677 KB)
For anyone interested in the Intel Microcode “Extra” undocumented Header, I’ve written a detailed wiki page about it here:
Intel Microcode Extra Undocumented Header
Any useful comments, suggestions, improvements etc are always welcome.
cpu000406E3_platC0_ver000000B2 date01-02-2017
To me, it looks like the analysis for the 5th dword is partially incorrect.
Please reread Ben Hawkes’ paper, he mentions the 64th bit on his observation number 5. This would be bit 0 of the field right after the "magic" field that is always 0xa1, i.e. the field that has a constant 0x00020001 value in every microcode update seen in public updates and BIOSes thus far. This also makes a lot more sense when you read the full text in Ben’s paper, where he says the bit was initially "1" and things got strange when it was changed to "0", i.e. the dword was being changed from 0x00020001 to 0x00020000.
Thus, messing with the 5th dword ("maybe VCN" field) results in a normal failure per Ben’s testing – it is just a normal failure due to a bad signature.
All of these microcode updates have multiple "regions" inside – someone at intel has publicly stated that according to some of the SGX/microcode security papers. Let’s call the thing we send to the processor a MCU, to differentiate it from one of its "regions" that actually changes the processor’s microcode translation unit (let’s call that specific region, the "microcode patch").
That field might be the version of the "microcode patch" region, i.e. of the specific subset of the processor firmware that is used by its microcode translation unit. A MCU has been documented to also have runnable microcode and opcode regions that the processor executes when applying the update, for example. If you change one of these other regions, but not the "microcode patch", you would not have to update the microcode patch version field.
Ben Hawkes did not really test downgrades and that’s a test that can be easily engineered to show if this field can work as a downgrade barrier or not.
Yes you are right, it’s the 64th bit (thus MSB of the 3rd dword) and not byte as I saw. I’ll move the related comments from my 5th dword to the 3rd.
Indeed I suppose this can be easily tested but we would need someone with Linux and also a processor with a CPUID which has non-zero "VCN" and "SVN" fields at the microcode binaries.
What paper is this information found at?
To me it would make a lot more sense for the 5th and 18th dwords to be control numbers and not versions, especially since there is already such a thing, Update revision. The "downgrade" tests, if done, can exclude that possibility.
Page 16 of CHEN, AHN, "Security Analysis of x86 Processor Microcode", 2014-12-11. Search the article’s name in duckduckgo.
I assume you mean this sentence from the 2014 paper by Daming Chen:
I have already read that paper but not the source for that statement which seems to be "P6 Microcode Can Be Patched" by Linley Gwennap (09/1997). That very old paper does not seem to explicitly mention such a thing outside the Encryption section which is unrelated to these "regions" Chen mentioned and besides, these things may not have been valid for many years now due to the source paper being 20 years old and 10 years before Intel implemented the Extra header with Public Key encryption support. Also, as Chen mentions, such a thing cannot be verified without decrypting the binaries and Intel has no reason to explain their encrypted data structure, if there is any at this point.
Nonetheless, it seems very possible that such a "structure" (with 2 regions) exists. To me it would seem a lot more likely that dwords 8 (UpdateSize) and 17 (Unknown5) are related to these regions. The 8th is definitely the UpdateSize as demonstrated by Ben. The 17th can be many things as I explained.
One relatively recent Intel document (or patent, can’t recall) I read referred to the microcode patches as “unified patches”. They are not just updating the microcode sequencer unit anymore… Also, my theory is that not all of the undocumented header is meaningful to the processor itself, some fields are used by Intel internal tools or processes, or just documentation metadata.
The 8th dword (counting from 1 like you did) is the size of the oldest super-region, which was tested by Ben Hawkes. My best guess is that it contains everything the “classic” microcode updates contained, including whatever “regions” the P6 paper mentioned.
The 6th and 18th dwords have been used as auxiliary sizes, but not as consistently as the 8th dword.
Since Haswell, the 6th dword is the size of the entire update, all regions included. One would need to do a fault-injection analysis on the 6th dword on a recent processor to know if it is relevant to the processor’s microcode loader or not – it might know the size of the extra regions through other means: before Haswell several processors didn’t have the 6th dword as the entire update size, but very very likely had extra regions (and on those processors, the 6th dword looked like it was two 16-bit fields of unknown purpose).
The 18th dword does tell a history: it likely is used by Intel tools and not by the processor, at least before Skylake. Before Skylake, it can be zero, or it can be the same as the 8th dword, or, when slightly greater than the 8th dword, it will be the size of the microcode update including the noise padding and the extended signature table – not something the processor itself would care about.
I never paid any attention to the 17th dword, so I did not look for patterns related to it.
BTW, if you didn’t do it yet, look for Costan, V. and Devadas, S. “Intel SGX Explained”, MIT, 2016. It explains a lot of how Intel processor microcode works (because SGX is almost entirely done in ucode), and its references have several relevant patents which explain things further.
Exactly, I believe the same thing as well even if I didn’t mention it at the paper. I was thinking of that mostly at those (supposedly) SVN and VCN fields. Maybe they are used in a similar fashion as in Engine firmware to control invalid downgrades but even if the tests show that the loader does not care about those control numbers, it is very likely that they exist for "book-keeping" purposes, like "metadata" as you said. At the SGX Explained pdf I glimpsed at the term CPUSVN which does not seem related to microcode but shows that these VCN/SVN fields are used by Intel at other places besides Engine firmware.
Yes, these are all mentioned at the paper as well since they coincide with my observations too.
Ah that’s the paper I was looking for when I asked some posts back, since you had mentioned SGX. That "paper" is more like a book so I just read selectively by searching for "microcode". There is a small section for it but, as far as I can see, it does’t really say anything we don’t already know as these findings are based of the same two (major/known) papers that we’ve already read (Ben/2013 and Chen/2014).
Generally, the notion that certain fields of the undocumented Extra header may be used by internal Intel tools only, for metadata purposes or similar, and thus not by the CPU Loader seems very likely to me.
The SGX paper has quite an interesting information, which you can also get from the referred patent. One, is that CPUSVN components are 8-bit (thus, likely SVNs are 8-bit). The other is that the SGX CPUSVN is derived from concatenation or some other lossless transformation of the SVNs of everything related to the SGX environment (which obviously include microcode components, as well as ME components, among others). So, it might not be used by the microcode loader, and yet it might be used/exported by the microcode itself (in this case, SGX).
I just updated the paper based on our recent discussion, thank you for your contribution.
Yes I know. It’s the same at ME. I have mentioned at the VCN and SVN Extra header fields that only the 1st byte (= 8 bits) is used and the other three are reserved.
Interesting idea but if it’s used by the CPU after the MCU is successfully loaded, then it stands to reason that any such fields should be included at the encrypted data and not at a visible (but undocumented) header.
Yes I know. It’s the same at ME. I have mentioned at the VCN and SVN Extra header fields that only the 1st byte (= 8 bits) is used and the other three are reserved.
That means the field can handle up to 4 SVNs, and should be handled as such until further notice, IMHO. A SVN of zero is the same as no SVN for all intents and purposes (assuming it is unsigned, which is not necessarily a safe assumption, unless either the patents or ME provide clues about this), since it is the least possible security version number…
Interesting idea but if it’s used by the CPU after the MCU is successfully loaded, then it stands to reason that any such fields should be included at the encrypted data and not at a visible (but undocumented) header.
Well, yes. A related example: unless Intel is not being as through with this as typical, the processor microcode update process would have to be able to detect and fail due to incompatible processor flags masks, and that information was not present in any of the plaintext data sent to the processor before Skylake. Sure, it was in the documented header, but that header is irrelevant to the processor.
So, such information it is either part of the encrypted sections somehow (either as data, or as a pre-flight check implemented by update-provided opcode), or the hardwired HMAC secret has to be different on processors with incompatible processor flags mask (in which case the microcode update would fail on incompatible processors because the HMAC signature check would fail, even if the RSA keys are the same among all possible processor flags masks, including incompatible ones).
For SGX-related SVNs, which patents make it clear that are implemented as internal microcode-acessible-only registers, the update might have code that sets them from the plaintext header, or from some new parameter table region (encrypted), or even hardwired as ucode instructions inside the update (and thus also encrypted). Since the entire extra plaintext header is signed, fault-injection analysis is likely to be impossible, and there is no way to know unless someone at Intel discloses this information.
cpu00050671_plat78_ver000001AC date: 04-04-2017
Hello!
In readme stated:
C. Download MC Extractor MC Extractor is developed using Python 3.x and can work under Windows, Linux and macOS operating systems. Pre-built binaries are provided for Windows only with build/freeze instructions for all three OS found below.
But I don’t see any binaries. Tried to assemble it via provided manual, but it not finished successfully.
Can you please upload binaries somewhere and provide a link to get it? I’m not a python-programmer, so see no way how to fix that error ![]()
UPD: Successfuly built it with Python 3.5.3 version, 3.6.1 is not supported by current PyInstaller. Maybe that can be noted in readme.
Really, it’s so linux-way - to get a little program get a big developer suite, get a strange error, f**k with dependencies (oops, you need not a latest version, so get another big suite) - why not get just a binary if you need just a binary ? Open source is great, I like it - but if need to run program, not just learn code, precompiled binaries is what to download first.
Here is logs:
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
>pyinstaller --noupx --onefile MCE.py
111 INFO: PyInstaller: 3.2.1
111 INFO: Python: 3.6.1
112 INFO: Platform: Windows-7-6.1.7601-SP1
113 INFO: wrote e:\My downloads\BIOS\MCExtractor-master\MCExtractor-master\MCE.spec
115 INFO: UPX is not available.
116 INFO: Extending PYTHONPATH with paths
['e:\\My downloads\\BIOS\\MCExtractor-master\\MCExtractor-master',
'e:\\My downloads\\BIOS\\MCExtractor-master\\MCExtractor-master']
116 INFO: checking Analysis
117 INFO: Building Analysis because out00-Analysis.toc is non existent
117 INFO: Initializing module dependency graph...
119 INFO: Initializing module graph hooks...
121 INFO: Analyzing base_library.zip ...
Traceback (most recent call last):
File "D:\Soft\Python36\Scripts\pyinstaller-script.py", line 11, in <module>
load_entry_point('PyInstaller==3.2.1', 'console_scripts', 'pyinstaller')()
File "d:\soft\python36\lib\site-packages\PyInstaller\__main__.py", line 90, in run
run_build(pyi_config, spec_file, **vars(args))
File "d:\soft\python36\lib\site-packages\PyInstaller\__main__.py", line 46, in run_build
PyInstaller.building.build_main.main(pyi_config, spec_file, **kwargs)
File "d:\soft\python36\lib\site-packages\PyInstaller\building\build_main.py", line 788, in main
build(specfile, kw.get('distpath'), kw.get('workpath'), kw.get('clean_build'))
File "d:\soft\python36\lib\site-packages\PyInstaller\building\build_main.py", line 734, in build
exec(text, spec_namespace)
File "<string>", line 16, in <module>
File "d:\soft\python36\lib\site-packages\PyInstaller\building\build_main.py", line 212, in __init__
self.__postinit__()
File "d:\soft\python36\lib\site-packages\PyInstaller\building\datastruct.py", line 161, in __postinit__
self.assemble()
File "d:\soft\python36\lib\site-packages\PyInstaller\building\build_main.py", line 317, in assemble
excludes=self.excludes, user_hook_dirs=self.hookspath)
File "d:\soft\python36\lib\site-packages\PyInstaller\depend\analysis.py", line 560, in initialize_modgraph
graph.import_hook(m)
File "d:\soft\python36\lib\site-packages\PyInstaller\lib\modulegraph\modulegraph.py", line 1509, in import_hook
source_package, target_module_partname, level)
File "d:\soft\python36\lib\site-packages\PyInstaller\lib\modulegraph\modulegraph.py", line 1661, in _find_head_package
target_module_headname, target_package_name, source_package)
File "d:\soft\python36\lib\site-packages\PyInstaller\depend\analysis.py", line 209, in _safe_import_module
module_basename, module_name, parent_package)
File "d:\soft\python36\lib\site-packages\PyInstaller\lib\modulegraph\modulegraph.py", line 2077, in _safe_import_module
module_name, file_handle, pathname, metadata)
File "d:\soft\python36\lib\site-packages\PyInstaller\lib\modulegraph\modulegraph.py", line 2167, in _load_module
self._scan_code(m, co, co_ast)
File "d:\soft\python36\lib\site-packages\PyInstaller\lib\modulegraph\modulegraph.py", line 2585, in _scan_code
module, module_code_object, is_scanning_imports=False)
File "d:\soft\python36\lib\site-packages\PyInstaller\lib\modulegraph\modulegraph.py", line 2831, in _scan_bytecode
global_attr_name = get_operation_arg_name()
File "d:\soft\python36\lib\site-packages\PyInstaller\lib\modulegraph\modulegraph.py", line 2731, in get_operation_arg_name
return module_code_object.co_names[co_names_index]
IndexError: tuple index out of range
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
>build_exe MCE.py
Traceback (most recent call last):
File "D:\Soft\Python36\Scripts\build_exe-script.py", line 9, in <module>
load_entry_point('py2exe==0.9.2.2', 'console_scripts', 'build_exe')()
File "D:\Soft\Python36\lib\site-packages\py2exe\build_exe.py", line 141, in main
builder.analyze()
File "D:\Soft\Python36\lib\site-packages\py2exe\runtime.py", line 160, in analyze
self.mf.import_hook(modname)
File "D:\Soft\Python36\lib\site-packages\py2exe\mf3.py", line 120, in import_hook
module = self._gcd_import(name)
File "D:\Soft\Python36\lib\site-packages\py2exe\mf3.py", line 274, in _gcd_import
return self._find_and_load(name)
File "D:\Soft\Python36\lib\site-packages\py2exe\mf3.py", line 357, in _find_and_load
self._scan_code(module.__code__, module)
File "D:\Soft\Python36\lib\site-packages\py2exe\mf3.py", line 388, in _scan_code
for what, args in self._scan_opcodes(code):
File "D:\Soft\Python36\lib\site-packages\py2exe\mf3.py", line 417, in _scan_opcodes
yield "store", (names[oparg],)
IndexError: tuple index out of range
Binaries do exist, at Releases just like every Github project: https://github.com/platomav/MCExtractor/releases
The latest “develop” Github branch of PyInstaller works with Python 3.6.x just fine.
2
3
4
5
6
7
8
9
10
11
File: cpu00600F20_ver06000829_date20140523.bin
+----------------------------------------------------------------------------------------+
| AMD |
+---+----------+----------+------------+-------+----------+----------+--------+----------+
| # | CPUID | VERSION | DD-MM-YYYY | SIZE | CHKAMD | CHKMCE | OFFSET | STATUS |
+---+----------+----------+------------+-------+----------+----------+--------+----------+
| 1 | 00600F20 | 06000829 | 23-05-2014 | 0xA20 | 00000000 | C3C9070F | 0x00 | Outdated |
+---+----------+----------+------------+-------+----------+----------+--------+----------+
Note: Microcode #1 was not found at the database, please report it!
cpu00600F20_ver06000829_date20140523.zip (2.75 KB)
Can someone upload AMD ucodes old archive packages from amd64.org ?
Or maybe just this files:
cpu00000F00_ver02000008_date20070614.bin
cpu00000F48_ver00000046_date20040719.bin
cpu00200F31_ver02000057_date20080502.bin
plutomaniac, can you share complete binaries of ucodes listed in database ?