thank you chino, for this small guide. was finally able to get around the encapsulated gigabyte bios, flash a modded version and get ReBar to work on my turing card c:
@chinobino Hello, ive been trying to update my bios to bypass an Oemid mismatch using the modded version, both .85 and .87. After entering the command the system will not reboot through the dos, and after a manual reboot the new software will not boot. Im on a B450M DS3H, any idea if im using the correct version of the modded efiflash?
@cj30a Hi and welcome to the Win-RAID forum.
Changes to the more recent B450 BIOS may have caused EIFFlash to no longer work.
You may need to try using Flashrom:
Sorry if this is a stupid question…
I’m currently struggling to flash a Gigabyte motherboard and I keep getting the explanation that the BIOS files (.Fxx) that can be downloaded from the official website are a ‘special’ format not ‘raw’ and don’t try to flash it with any tool other than the official gigabyte efiflash.
Am I understanding correctly that this is not exactly true and I can use the FPT tool to flash it?
Most current bios are .Fxx, anyway they are CAPsulated/rom.
They are recognized by Q-Flash and by GigaByte Win based apps.
Hi, without knowing what your motherboard is I can’t say for sure.
If you have an Intel chipset then you can use the corresponding version of Intel FPT to flash the BIOS.
WARNING: If you have an Intel Gigabit Ethernet Adapter you will need to use the -savemac command or you can overwrite/erase your MAC address.
Hey @chinobino, I want to flash both bios roms (m_bios and b_bios).
My mobo is Gigabyte Z370XP SLI. The current version of the main bios (m_bios) and backup (b_bios) is F15 (the latest).
I was playing arround with Secure Boot in the main bios and at some point it stopped booting. The mobo switched to backup bios (I can tell because the version was F4, while the main bios version is F15). I decided to flash F4 to F15 using QFlash. It went well. Then I tweaked the bios (b_bios) so that it uses my regular settings (XMP, basic CPU OC) and I also enabled Secure Boot. Everything worked, but the next day when I turned on the PC it booted into the main bios (I can tell becase there were custom BIOS profiles under “Load Profiles”).
The main bios works fine with my regular settings and it boots with no issue, however I am afraid now about the backup bios, because I applied my regular settings to it + enabled Secure Boot and this is the problem. If something happens to my main bios again and the mobo tries to boot into the backup bios, there is a chance that it won’t boot (because the backup bios doesn’t use factory/optimized default setting, but instead uses my configuration).
That’s why I want to flash b_bios, so that it resets and uses factory default settings.
I can flash the main bios with QFlash (from within the UEFI) with no issue, but there is no option to flash both bios roms at the same time (I know there can be a checkbox saying “Also Update Backup BIOS”, but there is no such thing in my case, so QFlash doesn’t touch the backup bios).
One way to flash the b_bios is to force the mobo to boot in the backup bios (but I didn’t manage to do this explicitly, like holding power and reset buttons for 10 secs) and run QFlash. And I am afraid it wouldn’t boot in b_bios, because for some reason it switched back to m_bios (and now it always boots m_bios).
I have tried EFIFlash tool running from FreeDOS, but it says “BIOS is protected by SecureFlash”. When I reboot, nothing happens and the tool just starts over. The main bios was on the optimized defaults.
I don’t know how the DualBios thing works in detail. Perhaps it automatically resets CMOS of the backup bios (which basically resets to the optimized defaults)? If so, then I don’t even need to flash the backup bios and the mobo will do the job when something happens with the main bios.
What am I doing wrong? How to flash both bios roms with EFIFlash? Thanks in advance!
Hi @pripishchik and welcome to the Win-RAID forum.
Correct. If QFlash sees the the same BIOS version on the b_bios chip it won’t give the option to flash the backup.
I have tried this also with a Z370 and it does not work, I suspect it only works with gigabyte motherboards that were made before Z370.
Now that you have updated to F15 you cannot use EFIFlash to flash any BIOS due to SecureFlash now being enabled.
Your own testing has proven that BIOS settings are stored separately for each BIOS chip, so your current settings could cause POST failure if the settings saved are incompatible/incorrect.
The most likely issue would actually be with your CPU OC or RAM, if an unstable XMP profile was set.
Secure Boot only effects your OS loading so you should be able to enter BIOS to disable it should you need to.
There are two ways to flash the b_bios.
- Use a hardware programmer with a SOP-8 clip to flash the b_bios chip directly.
Note: As you have an Intel Gigabit adapter I would suggest inserting your MAC address into the GbE region of the stock F15 BIOS so that the hardware programmer does not erase your MAC address. You can do this easily using CoffeeTime v0.99
You need to make sure that you verify the b_bios chip after flashing to ensure that it was flashed successfully (e.g. check the checksum of the file you flash against a dump of the b_bios chip after flashing to ensure they are the same).
- The second option is more complex but is done using software:
a) Downgrade m_bios to F14 using Intel FPT_v11.8.x.zip
NOTE: As you have an Intel Gigabit adapter I would suggest inserting your MAC address into the GbE region of the stock F15 BIOS so that Intel FPT does not erase your MAC address. You can do this easily using CoffeeTime v0.99
b) Use modified EFIFlash to flash F14 to both m_bios and b_bios from DOS or UEFI bootable USB stick ensuring to use the /DB (DualBIOS) switch to update both main & backup BIOS chips.
c) Use QFlash to upgrade to F15 again and tick “Also Update Backup BIOS”
wow, thanks for the detailed response, appreciate that, but now I am wondering if there is a need to reset b_bios (by flashing it), if the mobo can automatically reset the settings (if there is a problematic XMP profile or CPU OC)? is the following true?
if your main BIOS (m_bios) ever fails and the board switches to backup BIOS (b_bios), Gigabyte’s firmware will try to boot it as-is, but if the current b_bios settings prevent a successful POST, it will automatically fall back to “Optimized Defaults” for that chip after a few failed boot attempts.
@pripishchik Yes, I don’t think you really have to worry about the b_bios.
If the m_bios is somehow corrupted and the motherboard attempts to boot from the b_bios three times (iirc) and fails, it will attempt to boot with optimized defaults.
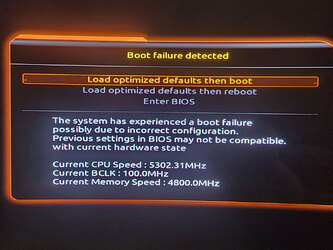
I think there is a screen that usually tells you that looks similar to this:
I have read all threads about flashing modded bios on locked motherboard here. I have successfuly modded and flashed such files several times on Intel H110 (bios chip in socket), Z270 (bios chip with spi pins) with FPT and with externall programmer. I was always starting from backup with external programmer.
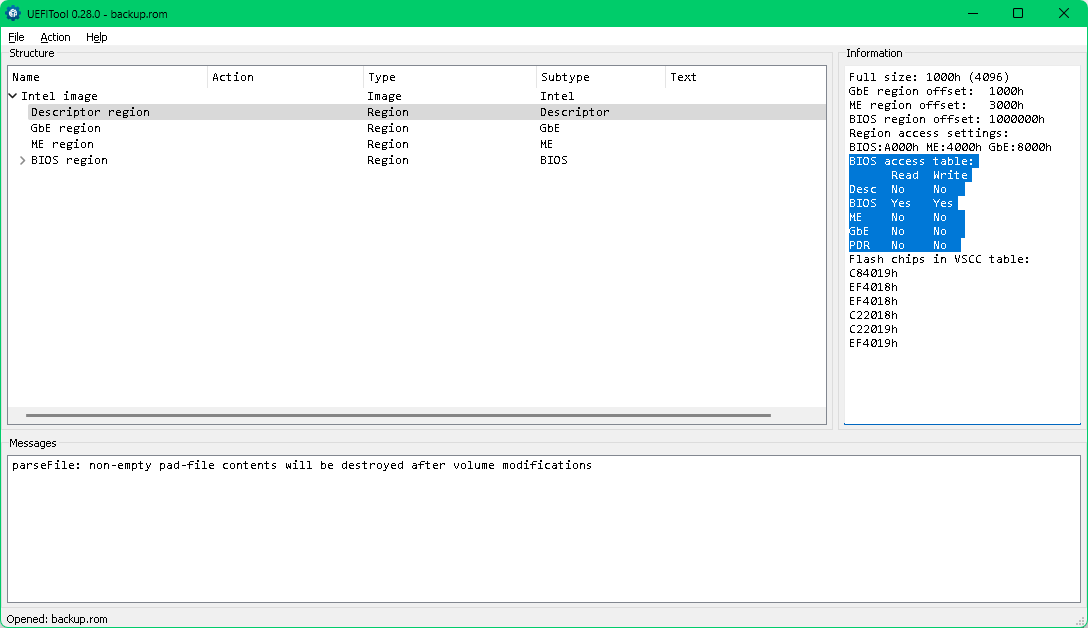
Now since Gigabyte has moved to capsulated bios and rollback to non-capsulated bios is not possible with Efiflash (even modded) and Q-flash, I have bunch of questions about Q-flash+ feature. It is present on my Gigabyte Z590I Aorus Ultra and bios chip looks like BGA with no spi connector for external programmer. I have some ideas on how to do full dump and flash modded bios then.
- Does Q-flash+ flash modded files?
- Does Q-flash+ retain MAC address?
- How do I know if my backup file made by FPT contain full dump even if UefiTool shows only BIOS region is unlocked for read/write? DESC, ME, GBE and POR are locked for read/write. I mean FPT did not show any warnings and dump file is 32 MB as my bios chip.
- If MAC address in my dump is 888888888788 does it mean that FPT was not able to dump real -GBE region? Is it possible that first bits are blank MAC, and real MAC is stored in other place? I was trying to find proper MAC in both (full and gbe only) dumps with no success.
Thanks in advance for all advice.
Definitely the best way to protect yourself from an accidental brick ![]()
I couldn’t find any images of the BIOS chip but there are replacements for sale on ebay.
Are you sure that it is BGA? They are usually SOP-8 on Gigabyte boards.
I have read reports of people having success to flash modified BIOS to AMD chipsets with Q-flash plus, not sure about Intel chipsets.
You could test by modifying a stock Gigabyte BIOS (such as the MAC address in the GbE region from 88:88:88:88:87:88 to 88:88:88:88:88:88) and then try to flash it with Q-flash plus.
If it says the file is invalid then you will know straight away.
Yes, Q-flash plus should not be overwriting the Intel GbE region with the MAC address from a stock BIOS.
If you were able to make a full backup without any error message from FPT then the read locks are clearly not present/active.
The easiest way is to try to write the backup back to the BIOS chip with FPT. If you get an error then it will tell you that there are write locks present depending on the error number. Gigabyte motherboards usually do not have any locks.
I believe the MAC adress is stored locally on the adapter and cannot be overwritten
Maybe @lfb6 or @plutomaniac could chime in if the GbE region is even being used for Intel 2.5GbE (and 5GbE) adapters?
Microsoft Windows [Version 10.0.26100.1742]
(c) Microsoft Corporation. All rights reserved.
C:\Windows\System32>e:
E:>fptw64 -D backup.rom
Intel (R) Flash Programming Tool Version: 15.0.35.1951
Copyright (C) 2005 - 2021, Intel Corporation. All rights reserved.
Reading HSFSTS register… Flash Descriptor: Valid
--- Flash Devices Found ---
ID:0xC22019 Size: 32768KB (262144Kb)
- Reading Flash [0x2000000] 32768KB of 32768KB - 100 percent complete.
Writing flash contents to file “backup.rom”…
Memory Dump Complete
FPT Operation Successful.
E:>fptw64 -F backup.rom
Intel (R) Flash Programming Tool Version: 15.0.35.1951
Copyright (C) 2005 - 2021, Intel Corporation. All rights reserved.
Reading HSFSTS register… Flash Descriptor: Valid
--- Flash Devices Found ---
ID:0xC22019 Size: 32768KB (262144Kb)
Warning: Unable to detect if ME was disabled.
Do you wish to proceed with the flash write operation? <Y/N>: n
Error 239: User selected to cancel the operation.
FPT Operation Failed.
I have never seen “Warning: Unable to detect if ME was disabled. Do you wish to proceed with the flash write operation? <Y/N>:”
Is it safe to proceed?
Did you run FPT from an elevated command prompt?
Is secure boot disabled?
Can you run MEInfoWin64.exe and MEManufWin64.exe from the CSME System Tools v15.0 r15 package on this page?
Yes, FPTw64 run from an elevated command. Please note I got the same output from FPT under Efi shell.
Yes, I only use my desktop with secure boot disabled.
Please find below outputs from MeInfo and MeManuf. Full output from FPT is also there, maybe it helps a little.
Microsoft Windows [Version 10.0.26100.1742]
(c) Microsoft Corporation. All rights reserved.
C:\Windows\System32>e:
E:>meinfowin64
Intel (R) ME Info Version: 15.0.41.2142
Copyright (C) 2005 - 2022, Intel Corporation. All rights reserved.
Platform Type Desktop
FW Image Type Production
Last ME Reset Reason Other
BIOS Boot State Post Boot
Boot Critical Code Redundancy Disabled
Current Boot Partition 1
Factory Defaults Recovery Status Enabled
Firmware Update OEM ID 00000000-0000-0000-0000-000000000000
TCSS FW partial update Disabled
Crypto HW Support Enabled
Intel(R) ISH Power State Disabled
OEM Tag 0x00
FW Update State Enabled
TLS State Enabled
CSME Measured Boot to TPM Disabled
BIOS Recovery State Disabled
Intel(R) ME Code Versions
BIOS Version F11b
GbE Version 0.4
MEI Driver Version 2102.100.0.1044
FW Version 15.0.52.2700 H Consumer
LMS Version 2316.5.1.12
IUPs Information
PMC FW Version 150.2.10.1020
SAMF FW Version 1.17.0.0000
PPHY FW Version 12.14.215.2015
PCHC FW Version 15.0.0.1021
PCH Information
PCH Name TGL
PCH Device ID 4385
PCH Revision ID B1
PCH SKU Type Production PRQ Revenue
PCH Replacement State Disabled
PCH Replaceable Counter 0
PCH Unlocked State Disabled
Transactional FW Information
Original image type Consumer
Current sku type Consumer
Flash Information
Storage Device Type SPI
SPI Flash ID 1 C22019
RPMC Unsupported
RPMC Bind Counter 0
RPMC Bind Status Pre-bind
RPMC Rebind Unsupported
RPMC Replay Protection Max Rebind 1
BIOS Read Access 0x000F
BIOS Write Access 0x000A
GBE Read Access 0x0009
GBE Write Access 0x0008
ME Read Access 0x000D
ME Write Access 0x0004
EC Read Access 0x0101
EC Write Access 0x0100
FW Capabilities 0x31319100
Intel(R) Protected Audio Video Path Present/Enabled
Intel(R) Dynamic Application Loader Present/Enabled
Intel(R) Platform Trust Technology Present/Enabled
Persistent RTC and Memory Present/Enabled
End Of Manufacturing
NVAR Configuration State Locked
EOM Settings Lock(Flash,Config) on 1st Boot
HW Binding State Enabled
Flash Protection Mode Protected
FPF Committed Yes
Intel(R) Protected Audio Video Path
Widevine provisioning state Not Provisioned
Attestation KeyBox Not Provisioned
PAVP State Yes
Security Version Numbers
Trusted Computing Base SVN 1
Anti Rollback SVNs
PMC 0 [minimum allowed: 0]
CSE 7 [minimum allowed: 0]
ROT KM 0 [minimum allowed: 0]
IDLM 0 [minimum allowed: 0]
OEM KM 0 [minimum allowed: 0]
HW Glitch Detection 0x08
TRC Polarity Rising Trans
TRC Mode Full-cycle polarity trans
TRC State Disabled
Intel(R) Platform Trust Technology
Intel(R) PTT initial power-up state Enabled
Intel(R) PTT State Enabled
SMx State Enabled
RSA1K Support Enabled
FW Supported FPFs FPF UEP
*In Use
— —
1st OEM Key Hash Revoked Disabled Disabled
1st OEM Key Hash size Enabled Enabled
1st OEM RSA Key size Enabled Enabled
2nd OEM Key Hash Revoked Disabled Disabled
2nd OEM Key Hash size Enabled Enabled
2nd OEM RSA Key size Disabled Disabled
BSMM Anti Rollback Enabled Enabled
DAL OEM Signing Disabled Disabled
DNX Anti Rollback Enabled Enabled
EOM Flow Full Flexible
Error Enforcement Policy 0 Disabled Disabled
Error Enforcement Policy 1 Disabled Disabled
Flash Descriptor Verification Disabled Disabled
Glitch Detection Disabled Enabled Enabled
Glitch Detection Enabled Disabled Disabled
IDLM Anti Rollback Enabled Enabled
Intel PTT Encryption Key Not Revoked Not Revoked
Intel(R) Manageability HW Fuse Status Enabled Enabled
Intel(R) PTT Enabled Enabled
OEM ID 0x00 0x00
OEM KM Anti Rollback Enabled Enabled
OEM Key Manifest Disabled Disabled
OEM Key Revocation State Disabled Disabled
OEM Platform ID 0x00 0x00
OEM Secure Boot Policy 0x00 0x00
CPU Debugging Enabled Enabled
BSP Initialization Enabled Enabled
Protect BIOS Environment Disabled Disabled
Measured Boot Disabled Disabled
Verified Boot Disabled Disabled
Key Manifest ID 0x00 0x00
Force Boot Guard ACM Disabled Disabled
OEM key Hash RSA key size Enabled Enabled
PID Refurbish Counter 0x00 0x00
PMC Anti Rollback Enabled Enabled
PTT Lockout Override Counter 0x00 0x00
Persistent PRTC Backup Power Enabled Enabled
RBE Anti Rollback Enabled Enabled
ROT Anti Rollback Enabled Enabled
RPMB Monotonic Counters 0x00 0x00
RPMC Rebinding Disabled Disabled
RPMC Support Disabled Disabled
SOC Config Lock State Enabled Disabled
SPI Boot Source Enabled Enabled
SPIRAL CPU Disabled Disabled
Secure boot KM Anti Rollback Enabled Enabled
TXT Supported Disabled Disabled
UFS Boot Source Disabled Disabled
USB Port ID 0x00 0x00
uCode Anti Rollback Disabled Disabled
DNX SVN 0x03 0x00
IDLM SVN 0x00 0x00
OEM KM SVN 0x00 0x00
PMC SVN 0x00 0x00
ROT KM SVN 0x00 0x00
Secure boot ACM SVN 0x00 0x00
Secure boot BSMM SVN 0x00 0x00
Secure boot KM SVN 0x00 0x00
Ucode SVN 0x00 0x00
1st OEM Public Key Hash FPF 000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000
1st OEM Public Key Hash UEP 000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000
2nd OEM Public Key Hash FPF 000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000
2nd OEM Public Key Hash UEP 000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000
E:>
E:>memanufwin64
Intel (R) ME Manuf Version: 15.0.35.1951
Copyright (C) 2005 - 2021, Intel Corporation. All rights reserved.
MEManuf Operation Passed
E:>
Microsoft Windows [Version 10.0.26100.1742]
(c) Microsoft Corporation. All rights reserved.
C:\Windows\System32>e:
E:>fptw64 -d backup.rom -verbose
Intel (R) Flash Programming Tool Version: 15.0.35.1951
Copyright (C) 2005 - 2021, Intel Corporation. All rights reserved.
LPC Device Id: 4385.
Platform: Tigerlake Platform
General FW Information
FW Status Register1 0x94000245
FW Status Register2 0x39850106
FW Status Register3 0x00000020
FW Status Register4 0x00004000
FW Status Register5 0x00000000
FW Status Register6 0x40200000
Current FW State Normal
Flash Partition Table Valid
FW Memory State CM0 with UMA
FW Initialization Complete
BUP Loading state Success
FW Error Code No Error
FW Mode Of Operation Normal
SPI Flash Log Not Present
FW Loading Phase BringUp
FW Loading Phase Status CM0_MKHI_HANDLER_STOP
ME File System Corrupted No
RPMC status OK
Initializing SPI utilities
Reading HSFSTS register… Flash Descriptor: Valid
Region Limits as programmed into the SPI Registers
FREG0 - DESC Region:Base Address: 0x000000 Limit : 0x000FFF
FREG1 - BIOS Region:Base Address: 0x1000000 Limit : 0x1FFFFFF
FREG2 - CSME Region:Base Address: 0x003000 Limit : 0xFFFFFF
FREG3 - GbE Region:Base Address: 0x001000 Limit : 0x002FFF
FREG4 - PDR Region:Base Address: 0x7FFF000 Limit : 0x000FFF
FREG5 - Region:Base Address: 0x7FFF000 Limit : 0x000FFF
FREG6 - Region:Base Address: 0x7FFF000 Limit : 0x000FFF
FREG7 - Region:Base Address: 0x7FFF000 Limit : 0x000FFF
FREG8 - EC Region:Base Address: 0x7FFF000 Limit : 0x000FFF
FREG9 - Region:Base Address: 0x7FFF000 Limit : 0x000FFF
FREG10 - Region:Base Address: 0x7FFF000 Limit : 0x000FFF
FREG11 - Region:Base Address: 0x7FFF000 Limit : 0x000FFF
FREG12 - Region:Base Address: 0x000000 Limit : 0x000FFF
FREG13 - Region:Base Address: 0x000000 Limit : 0x000FFF
FREG14 - Region:Base Address: 0x000000 Limit : 0x000FFF
FREG15 - Region:Base Address: 0x000000 Limit : 0x000FFF
Address Limit 0x2000000 Maximum Memory 32768kB
--- Flash Devices Found ---
ID:0xC22019 Size: 32768KB (262144Kb)
Using hardware sequencing.
Reading region information from flash descriptor.
Base: 0x00000000, Limit: 0x00000FFF
Base: 0x01000000, Limit: 0x01FFFFFF
Base: 0x00003000, Limit: 0x00FFFFFF
Base: 0x00001000, Limit: 0x00002FFF
DumpFlashToFile (backup.rom, 0x0, 0x0)…
- Reading Flash [0x2000000] 32768KB of 32768KB - 100 percent complete.
Writing flash contents to file “backup.rom”…
Memory Dump Complete
FPT Operation Successful.
E:>fptw64 -f backup.rom -verbose
Intel (R) Flash Programming Tool Version: 15.0.35.1951
Copyright (C) 2005 - 2021, Intel Corporation. All rights reserved.
LPC Device Id: 4385.
Platform: Tigerlake Platform
General FW Information
FW Status Register1 0x94000245
FW Status Register2 0x39850106
FW Status Register3 0x00000020
FW Status Register4 0x00004000
FW Status Register5 0x00000000
FW Status Register6 0x40200000
Current FW State Normal
Flash Partition Table Valid
FW Memory State CM0 with UMA
FW Initialization Complete
BUP Loading state Success
FW Error Code No Error
FW Mode Of Operation Normal
SPI Flash Log Not Present
FW Loading Phase BringUp
FW Loading Phase Status CM0_MKHI_HANDLER_STOP
ME File System Corrupted No
RPMC status OK
Initializing SPI utilities
Reading HSFSTS register… Flash Descriptor: Valid
Region Limits as programmed into the SPI Registers
FREG0 - DESC Region:Base Address: 0x000000 Limit : 0x000FFF
FREG1 - BIOS Region:Base Address: 0x1000000 Limit : 0x1FFFFFF
FREG2 - CSME Region:Base Address: 0x003000 Limit : 0xFFFFFF
FREG3 - GbE Region:Base Address: 0x001000 Limit : 0x002FFF
FREG4 - PDR Region:Base Address: 0x7FFF000 Limit : 0x000FFF
FREG5 - Region:Base Address: 0x7FFF000 Limit : 0x000FFF
FREG6 - Region:Base Address: 0x7FFF000 Limit : 0x000FFF
FREG7 - Region:Base Address: 0x7FFF000 Limit : 0x000FFF
FREG8 - EC Region:Base Address: 0x7FFF000 Limit : 0x000FFF
FREG9 - Region:Base Address: 0x7FFF000 Limit : 0x000FFF
FREG10 - Region:Base Address: 0x7FFF000 Limit : 0x000FFF
FREG11 - Region:Base Address: 0x7FFF000 Limit : 0x000FFF
FREG12 - Region:Base Address: 0x000000 Limit : 0x000FFF
FREG13 - Region:Base Address: 0x000000 Limit : 0x000FFF
FREG14 - Region:Base Address: 0x000000 Limit : 0x000FFF
FREG15 - Region:Base Address: 0x000000 Limit : 0x000FFF
Address Limit 0x2000000 Maximum Memory 32768kB
--- Flash Devices Found ---
ID:0xC22019 Size: 32768KB (262144Kb)
Using hardware sequencing.
Reading region information from flash descriptor.
Base: 0x00000000, Limit: 0x00000FFF
Base: 0x01000000, Limit: 0x01FFFFFF
Base: 0x00003000, Limit: 0x00FFFFFF
Base: 0x00001000, Limit: 0x00002FFF
WriteStartAddress : 0x00000000
WriteEndAddress : 0xFFFFFFFF
BiosStartAddress : 0x01000000
BiosEndAddress : 0x01FFFFFF
Need to disable BIOS Write Protection based on Address overlap …
FPRval 0x00000000
BIOS space write protection is Enabled
BIOS space write protection is Disabled
WriteFileToFlash( backup.rom, 0x0, 0x0 )…
WriteStartAddress : 0x00000000
WriteEndAddress : 0x01FFFFFF
MEStartAddress : 0x00003000
MEEndAddress : 0x00FFFFFF
Need to disable ME based on Address overlap …
Disabling the ME
Disabling the ME
. . . . . . . . . . . . . . . ME disabling time: 15.90 seconds.
Warning: Unable to detect if ME was disabled.
Do you wish to proceed with the flash write operation? <Y/N>: n
Error 239: User selected to cancel the operation.
FPT Operation Failed.
E:>
Ok, thanks for the info.
I can see that you have the default ME firmware installed (15.0.52.2700) for BIOS F11b which is good.
MEInfoWin64 and MEManufWin64 are communicating with the ME micro-controller so the 2102.100.0.1044 MEI driver also appears to be working.
FPT is recognizing the platform as Tigerlake-H which is correct according to the heci.inf driver:
[Intel.NTamd64.10.0…17763]
; DisplayName Section DeviceId
%TEE_DeviceDesc1%=TEE_DDI_x64_NO_ICLS, PCI\VEN_8086&DEV_43E0 ;ME15.0 - TGL-H
You could try to write to the ME region, it will likely give you another error number if it is locked or inaccessible.
There is a chance it could corrupt the ME region so it is up to you if you want to take the risk.
If we assume that the backup made in the FPT is good, then nothing left than flashing. Of course risk is always on me.
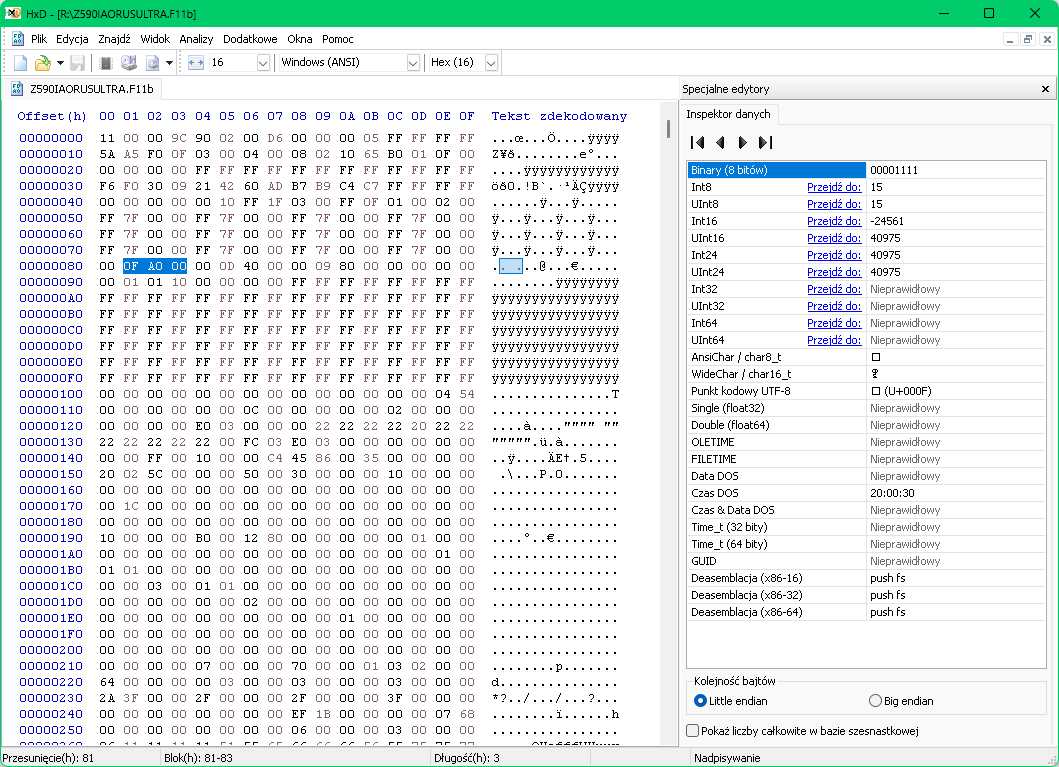
Could you please explain what do locks in descriptor region lock?
Unlocking all regions by changing 3 bytes to FF in line 80 works. All regions became read/write yes. What does removing this block affect in real use? Once I flash via FPT, which does not check what I upload, I could apply this modification. Is it helpful in my case?
Sorry for late reply, Cloudflare was down and I couldn’t access the site before work.
You should read the following thread (if you haven’t already);
[Guide] Unlock Intel Flash Descriptor Read/Write Access Permissions for SPI Servicing
The modifications will work but only after the modified BIOS has been flashed to the motherboard.
You will still need to bypass any currently present locks to flash the modified BIOS.
The guide above mentions some ways to unlock the flash descriptor but using a hardware programmer is usually the easiest.
I am preety sure you should not be sorry for late reply ![]()
I have read this topic several times. That is why I am asking about these locks - I have been little confused about need to unlock these.
And now we are closer to what I need to be sure ![]()
Like I have mentioned few rows above, I have done modifications successfully, and first step was always to make a backup with external programmer because it was very available from practical point of view. Now I will need to check if chip is really bga or it is just SOP-8 with legs to attach clip. Next I was removing locks and modify image and burn via FPT. But before I try clip way I will share what my plan is.
- There is official old beta bios without locks but it is unfortunatelly yet uncapsulated.
- Flash this uncapsulated (and unlocked) beta via Q-Flash+ because nor Q-Flash neither EfiFlash can not do this. (I asked you before if Q-Flash+ can burn modified bios, but forgot to ask if it can rollback to uncapsulated version).
- Remove locks on new capsulated image.
- Flash such file via FPT -SAVEMAC for sure.
I do not want to waste your time anymore, but do not know better master to ask ![]()