Drivers, Firmware and Tools
Last Updated: 2022-05-24
Intel Trusted Execution Engine Introduction:
Built into many Intel Chipset-based platforms is a small, low power computer subsystem called the Intel Trusted Execution Engine (Intel TXE). This can perform various tasks while the system is booting, running or sleeping. It operates independently from the main CPU, BIOS & OS but can interact with them if needed. The TXE is responsible for many parts of an Intel-based system. Such functionality extends, but it's not limited, to Platform Clocks Control (ICC), Thermal Monitoring, Fan Control, Power Management, Overclocking, Silicon Workaround (resolves silicon bugs which would have otherwise required a new cpu stepping), Identity Protection Technology, Boot Guard, Rapid Start Technology, Sensor Hub Controller (ISHC), Wireless Display, PlayReady, Protected Video/Audio Path etc. Thus it is essential for it to be operational in order for the platform to be working properly.
Intel Converged Security Engine Introduction:
The evolution of Intel Trusted Execution Engine into a unified security co-processor, running x86 code under a Minix-based Operating System. It was first introduced in 2015 with the release of Skylake CPUs working alongside 100-series Sunrise Point Platform Controller Hub (PCH). The CSE hardware can run Management Engine (ME) 11+, Trusted Execution Engine (TXE) 3+ or Server Platform Services (SPS) 4+ firmware. So there are a total of three families of CSE-based firmware: CSME (CSE ME), CSTXE (CSE TXE) and CSSPS (CSE SPS). The CSE hardware is also capable of running other types of firmware such as Power Management Controller (PMC), Integrated Sensor Hub (ISH), Imaging Unit (iUnit), Clear Audio Voice Speech (cAVS), Wireless Microcode (WCOD) etc.
Intel Power Management Controller Introduction:
Handles all Platform Controller Hub (PCH) power management related activities, running ARC code on top of the CSE hardware. PMC administers power management functions of the PCH including interfacing with other logic and controllers on the platform to perform power state transitions, configure, manage and respond to wake events, aggregate and report latency tolerance information for devices and peripherals connected to and integrated into the PCH etc. It was first introduced in 2018 with the release of Coffee/Cannon Lake CPUs working alongside 300-series Cannon Point PCH.
Disclaimer:
All the software and firmware below comes only from official updates which were provided and made public by various manufacturers! The System Tools are gathered and provided with the sole purpose of helping people who are out of other viable solutions. Thus, they can be extremely helpful to those who have major problems with their systems for which their manufacturer refuses to assist due to indifference and/or system age.
Getting Started:
Intel (CS)TXE is a Hardware platform which runs Firmware, is monitored/configured by Tools and interfaces with the user via Drivers. To get started, you need at the very least to know what (CS)TXE firmware major and minor version your system is running. Such info can be retrieved in various ways but you can use the free system information and diagnostics tool HWiNFO > Motherboard > Intel ME/TXE > Intel ME/TXE Version. The format is Major.Minor, Build, Hotfix. Once you determine the system's (CS)TXE firmware major and minor version, you can install the latest Drivers from section A and update the (CS)TXE Firmware by following sequentially the relevant steps at Section B using the required Tools from Section C.
A. Intel TXEI Drivers
The latest v4 DCH drivers are usable with CSTXE 3-4 systems running under Windows 10 >= 1709. The latest v4 MSI drivers are usable with CSTXE 3-4 systems running under Windows 8, 10 <= 1703. The latest v3 drivers are usable with CSTXE 3 systems running under Windows 7. The latest v2 drivers are usable with TXE 2 systems running under Windows 7, 8, 10 or TXE 1 systems running under Windows 10. The latest v1 drivers are usable with TXE 1 systems running under Windows 7, 8. In order to check your current installed version, use Intel TXEInfo tool as instructed below.
Note: To extract the files below you need to use programs which support RAR5 compression!
A1. Intel TXEI Drivers and Software
These packages contain the Intel TXEI drivers with their respective software & system services. It is advised to install these to enable all the Engine-related functionality. Since the Intel TXEI Drivers and Software are OS version dependent, search and run "winver.exe" to determine your own.
- TXEI Drivers and Software v2028.4.0.1091 DCH (Windows 10 >= 1709)
- TXEI Drivers and Software v2028.4.0.1091 MSI (Windows 8, 10 <= 1703)
- TXEI Drivers and Software v3.1.50.8289 (Windows 7)
- TXEI Drivers and Software v2.0.0.1094 (Windows 7, 8, 10)
- TXEI Drivers and Software v1.1.0.1064 (Windows 7, 8)
Note: TXEI Drivers and Software v2028.4.0.1091 DCH package includes v1924.4.0.1062 TXEI driver. TXEI Drivers and Software v2028.4.0.1091 MSI package includes v1924.4.0.1062 TXEI driver. TXEI Drivers and Software v3.1.50.8289 package includes v3.0.0.1115 TXEI driver. TXEI Drivers and Software v2.0.0.1094 package includes v2.0.0.1094 TXEI driver. TXEI Drivers and Software v1.1.0.1064 package includes v1.1.0.1064 TXEI driver.
A2. Intel TXEI Driver Only
These packages contain only the Intel TXEI Drivers without any additional software or system services. Installing these allows only very basic Engine-related functionality. Since the Intel TXEI Driver is OS version dependent, search and run "winver.exe" to determine your own.
- TXEI Driver v1924.4.0.1062 (Windows 8, 10)
- TXEI Driver v3.0.0.1115 (Windows 7)
- TXEI Driver v2.0.0.1094 (Windows 7, 8, 10)
- TXEI Driver v1.1.0.1064 (Windows 7, 8)
B. Intel (CS)TXE Firmware
SPI/BIOS Regions (FD/Engine/BIOS):
The SPI/BIOS chip firmware is divided into regions which control different aspects of an Intel-based system. The mandatory regions are the Flash Descriptor (FD), the (Converged Security) Trusted Execution Engine (CSTXE/TXE or Engine) and the BIOS. The FD controls read/write access between the SPI/BIOS chip regions and holds certain system hardware settings. The (CS)TXE holds the system's Engine firmware. For security reasons, the FD and Engine regions of the SPI/BIOS chip are usually locked so that no read/write access is allowed via software means. Since the FD controls that read/write access, it must be locked/protected so that it is not manually overwritten to allow unauthorized access to the firmware regions of the system's SPI/BIOS chip. The Engine region at the system's SPI/BIOS chip is also locked/protected due to the nature of the CSE/TXE co-processor, as explained at the Introductions above.
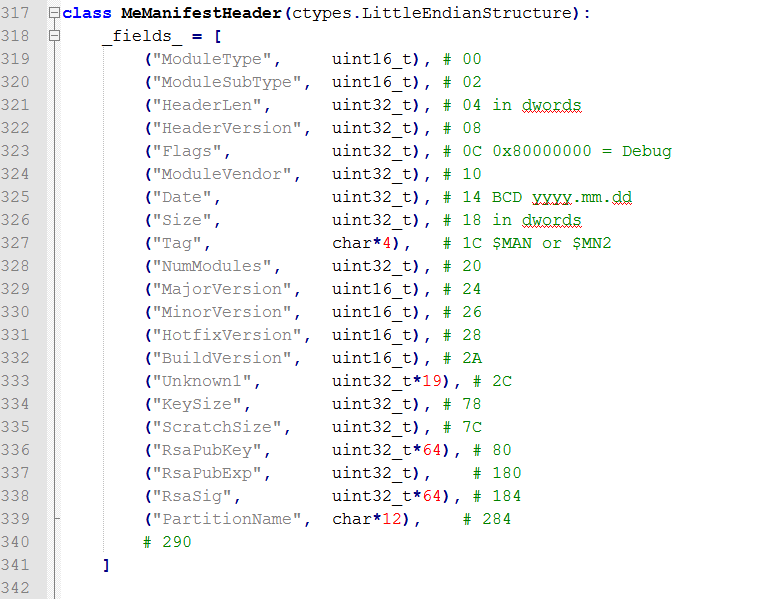
Engine Firmware Attributes (Family/Platform/SKU/Version):
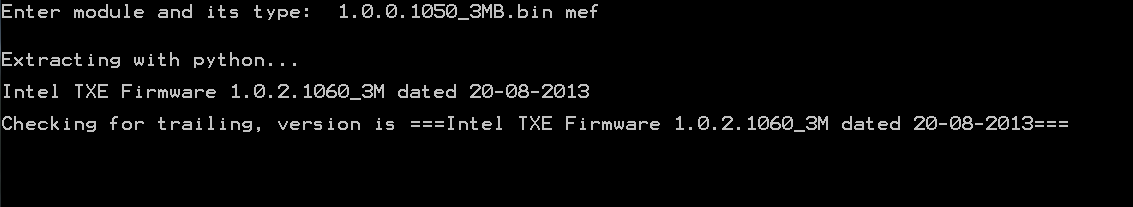
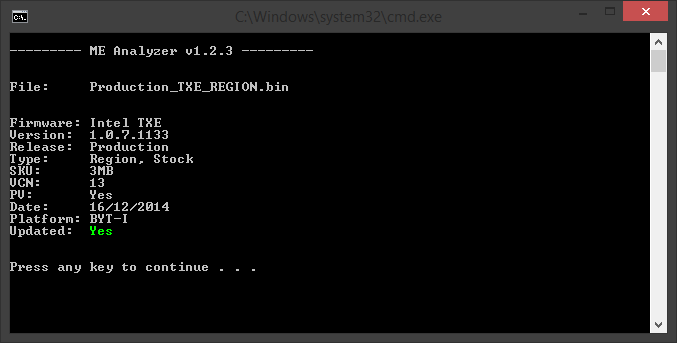
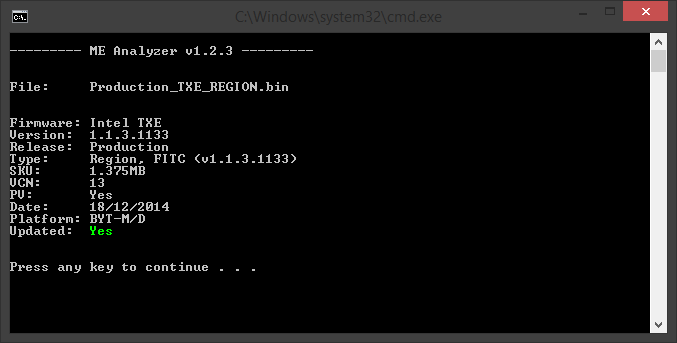
Intel (CS)TXE or Engine firmware is mainly categorized based on its target Chipset Family (i.e. Bay Trail, Apollo Lake, Gemini Lake etc), Type/SKU (i.e. 1.25MB MD, 1.375MB IT etc) and Version (i.e. 4.0.0.1245 = Major.Minor.Hotfix.Build). Be careful of what firmware your download relevant to your system. To understand your exact Chipset Family, (CS)TXE Type/SKU and (CS)TXE Version, you can usually run TXEInfo or TXEManuf tools with "-verbose" parameter. Otherwise, ME Analyzer can show you all the relevant information, after loading your SPI/BIOS image (Flash Descriptor + Engine + BIOS), when the latter is available. If a SPI/BIOS image is not available, run FWUpdate tool (when available) with parameter "-save fw.bin" and load the resulting "fw.bin" image into ME Analyzer instead. All the firmware below correspond to a specific Family which runs a specific (CS)TXE firmware version (example: For systems running CSTXE v4).
Engine Firmware Regions (RGN/EXTR):
The Type of each Engine/(CS)TXE firmware Region can be either Stock (RGN) or Extracted (EXTR). Stock are clean/stock/unconfigured images provided by Intel to OEMs. Extracted are dirty/extracted/configured images from various SPI/BIOS. The Engine firmware at the system's SPI/BIOS chip is always EXTR, generated by the OEM after configuring the equivalent RGN with the appropriate system settings.
Engine Firmware Configuration (CODE/DATA):
The Engine Firmware Regions (RGN/EXTR) consist of two sections: CODE and DATA. CODE is the actual Engine firmware whereas DATA is where all the system-specific settings are stored, as configured by the OEM at the factory via Intel Flash Image Tool. The Engine firmware is not static as it holds system-specific configuration and can additionally be configured by the Engine co-processor itself while the system is running in order to provide the proper support and functionality. Any such changes are written into the DATA section of the Engine Region and the firmware is considered Initialized. That means that the DATA section can be in one of three states: Unconfigured, Configured or Initialized. Unconfigured means that the Engine firmware image is the stock one Intel provides and not configured by the OEM at all (RGN). Configured means that the OEM has applied model specific settings and the Engine region is ready for deployment (EXTR). Initialized means that the Engine region comes from a system which was already running and thus the Engine co-processor has further configured the DATA section to suit that particular system better (system specific or dirty EXTR).
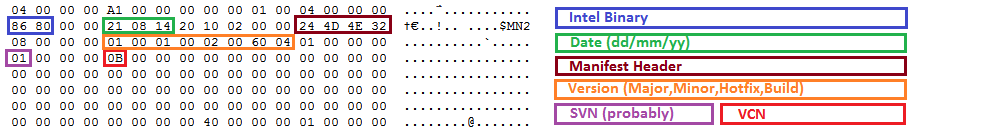
Engine Security Version Number (SVN):
All (CS)TXE firmware are defined by a Security Version Number (SVN) like 1,2,3 etc which is used to control the possible upgrade/downgrade paths provided by Intel's FWUpdate tool. The SVN gets incremented if there is a high or critical security fix that requires a Trusted Computing Base (TCB) recovery operation, a significant event in the life cycle of the firmware which requires renewal of the security signing keys in use. A downgrade to a lower SVN value via FWUpdate tool is prohibited whereas an upgrade to the same or higher SVN is allowed. For example if your current firmware has a SVN of 2, you can update to another firmware with SVN >= 2 (for example 3) but you cannot downgrade to another firmware with SVN < 2 (for example 1). Trying to flash a firmware with lower SVN will result in the error "The image provided is not supported by the platform" or similar. To view the SVN value of any (CS)TXE firmware, you can use ME Analyzer tool.
Engine Version Control Number (VCN):
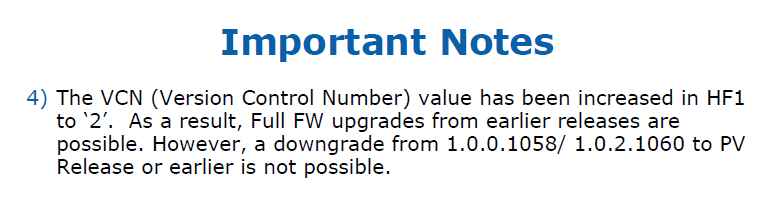
All (CS)TXE firmware are defined by a Version Control Number (VCN) like 1,2,45,193 etc which is used to control the possible upgrade/downgrade paths provided by Intel's FWUpdate tool. The VCN gets incremented if there is a security fix, a significant firmware change or a new feature addition. A downgrade to a lower VCN value via FWUpdate tool is prohibited whereas an upgrade to the same or higher VCN is allowed. For example if your current firmware has a VCN of 176, you can update to another firmware with VCN >= 176 (for example 193) but you cannot downgrade to another firmware with VCN < 176 (for example 174). Trying to flash a firmware with lower VCN will result in the error "The image provided is not supported by the platform" or similar. To view the VCN value of any (CS)TXE firmware, you can use ME Analyzer tool.
Engine Production Ready Status (PV):
All (CS)TXE firmware are defined by a Production Version/Ready Status (PV) which can be either Yes or No and is used to control the possible upgrade/downgrade paths provided by Intel's FWUpdate tool. The PV status is set to Yes when a firmware is validated/ready for use at Production platforms, thus when its status is Stable and not Beta, Alpha etc. An upgrade/downgrade from PV to non-PV firmware via FWUpdate tool is prohibited whereas upgrades/downgrades to the same PV or from non-PV to PV are allowed. For example if your current firmware has PV set to Yes, you can upgrade/downgrade to another firmware with PV set to Yes but you cannot upgrade/downgrade to another firmware with PV set to No. Trying to flash a firmware with incompatible PV will result in the error "The image provided is not supported by the platform" or similar. To view the PV status of any (CS)TXE firmware, you can use ME Analyzer tool.
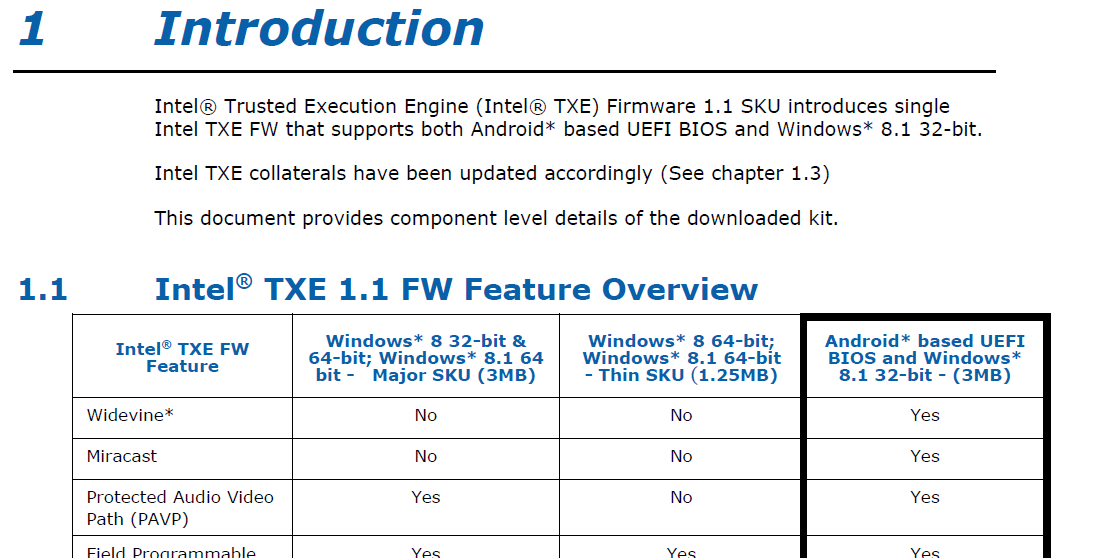
(CS)TXE Firmware SKUs:
TXE Firmware v1.0 is divided into two SKUs: Thin 1.25MB and Full 3MB. TXE Firmware v1.1 and v1.2 have combined the two previous SKUs into a single 1.375MB SKU. TXE Firmware v2.0 has a single 1.375MB SKU. CSTXE 3 has two SKUs based on Apollo Lake (APL) or Broxton (BXT) platform. CSTXE 4 has only one SKU for Gemini Lake (GLK) platform. To determine your SKU, ME Analyzer (by loading your SPI/BIOS image) or TXEInfo can help you sort most system specific details.
Engine Firmware Updating: There are two ways to upgrade or downgrade the Engine firmware, either via Intel FWUpdate tool or manually.
- The Intel FWUpdate tool is an official command line utility provided by Intel which uses the Engine co-processor itself to upgrade/downgrade the TXE firmware quickly and easily. FWUpdate tool requires that the Engine co-processor is operational and that its current Engine firmware region is healthy at the system's SPI/BIOS chip. To check if the Engine itself as well as its current firmware are healthy, you can use Intel TXEInfo and TXEManuf tools, as instructed below. FWUpdate tool also requires that the SVN, VCN and PV are not violated. FWUpdate tool does not require the user to have read/write access to the Engine firmware region of the system's SPI/BIOS chip, as dictated by the Flash Descriptor region permissions. Moreover, FWUpdate tool deals only with Engine CODE and does not require any prior Configuration (DATA). It can thus work with either RGN or EXTR Engine Regions. The basic usage is FWUpdLcl -f update_file_name.bin. You can see the entire supported parameters by displaying the utility's help screen via FWUpdLcl -?. Note that the name of the file to be flashed via FWUpdate does not matter.
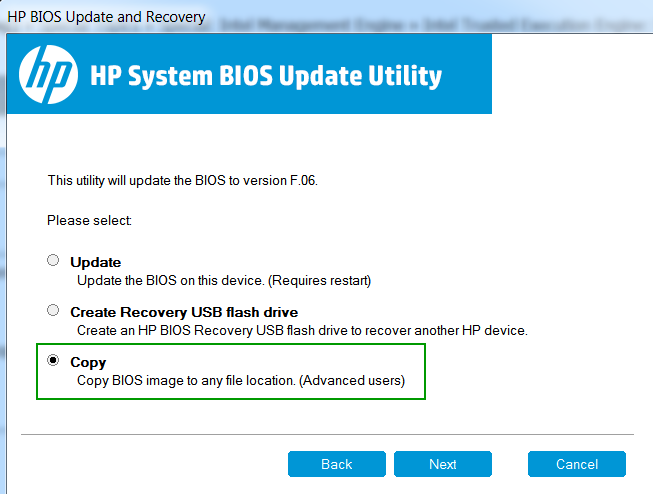
- In the event in which the usage of Intel FWUpdate tool is not possible, you can try to upgrade/downgrade the (CS)TXE firmware manually. Such cases include updating Converged Security Trusted Execution Engine (CSTXE) firmware, downgrading to Engine firmware which violate SVN, VCN or PV, repairing a corruption/problem etc. To upgrade/downgrade/repair manually, you need first & foremost to have read/write access to the Engine firmware region of the system's SPI/BIOS chip. To check if your FD is locked or to attempt to unlock it, follow the [Guide] Unlock Intel Flash Descriptor Read/Write Access Permissions for SPI Servicing. Once you have read/write access to the Engine firmware region of your system's SPI/BIOS chip, you can use any general purpose firmware flasher software such as Intel Flash Programming Tool, AMI AFU, Flashrom etc, which directly reads/writes the system's SPI/BIOS chip firmware. Before flashing, you must make sure that the Engine firmware region to be flashed back is Configured (EXTR) for your specific system via Intel Flash Image Tool (FIT). In order to do that, follow the [Guide] Clean Dumped Intel Engine (CS)ME/(CS)TXE Regions with Data Initialization. Never flash RGN or 3rd-party EXTR firmware to the Engine firmware region of the system's SPI/BIOS chip without first configuring them for your specific system (EXTR) via FIT. Since general purpose firmware software do not upgrade/downgrade/repair the Engine firmware region of the system's SPI/BIOS chip via the Engine co-processor itself, they are usually not restricted by the SVN, VCN and PV security measures. As long as you have read/write access to the Engine firmware region of the system's SPI/BIOS chip and a DATA Configured (EXTR) Engine firmware image, they should accomplish the desired action. Note however that some platforms have the current TCB SVN and/or ARB SVN value permanently set/fused/burned in the Chipset so you cannot downgrade their firmware with another which has lower TCB SVN and/or ARB SVN.
TXE 1 - 2 Updating:
Intel TXE v1 - v2 firmware can be updated easily & safely by using FWUpdate tool. Intel TXE v1.0 firmware (3MB & 1.25MB) can be upgraded to v1.1 or v1.2 firmware (1.375MB). However, the upgrade process can not be done via FWUpdate tool. Read more at "Engine Firmware Updating" above.
CSTXE 3 - 4 Updating:
Intel CSTXE v3 - v4 firmware do not have a FWUpdate tool. The CSTXE firmware updating is normally left to OEMs only, via two possible methods: Download & Execute (DnX, rarely used) or Capsule Update (normal SPI/BIOS image re-flash, most common). End-users who are looking to update their CSTXE firmware must follow the [Guide] Clean Dumped Intel Engine (CS)ME/(CS)TXE Regions with Data Initialization, provided that they first have a full SPI/BIOS image from their OEM or a system firmware dump. To be able to flash the updated SPI/BIOS image back (Capsule Update method), you need to have read/read access to the system's SPI/BIOS chip firmware. Read more at "Engine Firmware Updating" above.
B1. (Converged Security) Trusted Execution Engine - (CS)TXE
-
CSTXE 4
For CSTXE v4 -
CSTXE 3.1
For CSTXE v3.0 - v3.1 -
CSTXE 3.2
For CSTXE v3.2 -
TXE 2.1 1.375MB
For TXE 1.375MB v2.1 -
TXE 2.0 1.375MB
For TXE 1.375MB v2.0 -
TXE 1.2 1.375MB M/D
For TXE 1.375MB M/D v1.2 -
TXE 1.1 1.375MB M/D
For TXE 1.375 M/D v1.1 -
TXE 1.1 1.375MB I/T
For TXE 1.375 I/T v1.1 -
TXE 1.0 1.25MB M/D
For TXE 1.25MB M/D v1.0 -
TXE 1.0 1.25MB I/T
For TXE 1.25MB I/T v1.0 -
TXE 1.0 3MB M/D
For TXE 3MB M/D v1.0 -
TXE 1.0 3MB I/T
For TXE 3MB I/T v1.0
C. Intel (CS)TXE System Tools
The Intel (CS)TXE System Tools are used for creating, modifying, and writing binary image files, manufacturing testing, Intel (CS)TXE setting information gathering and Intel (CS)TXE firmware configuration and updating. These tools are not released to end-users but only to OEMs. The software below comes only from official updates which were provided and made public by various OEMs.
Flash Image Tool: Creates and configures a complete SPI image file which includes regions such as Flash Descriptor (FD), BIOS/UEFI, Intel (CS)TXE etc. The user can manipulate the completed SPI image via a GUI and change the various chipset parameters to match the target hardware.
Flash Programming Tool: Used to program a complete SPI image into the SPI flash device(s). FPT can program each region individually or it can program all of the regions with a single command. The user can also use FPT to perform various functions such as view the contents of the flash on the screen, write the contents of the flash to a log file, perform a binary file to flash comparison, write to a specific address block, program fixed offset variables etc.
Manifest Extension Utility: Used to generate a 3rd party Independent Update Partitions (IUP) which are compressed and signed by an external signing tool, such as OpenSSL. The signed contents may then be stitched into a SPI/BIOS image using the Intel Flash Image Tool (FIT).
Notice: Avoid using the Windows builds of very old (CS)TXE System Tools which either retrieve info (TXEInfo, TXEManuf, Flash Programming Tool) or modify the platform (FWUpdate, Flash Programming Tool) as they may not work properly on newer operating system versions. When available, it is advised to use either the DOS or EFI builds of said very old tools.
Notice: Avoid running the System Tools from paths which include non-English characters (i.e. Cyrillic, Chinese, Arabic, Greek) as it may cause them to crash or behave unpredictably.
C1. Identifying, Updating and Diagnosing Intel (CS)TXE Firmware
Those who are looking to update/downgrade their firmware should use TXEInfo, FWUpdate and TXEManuf tools for status information, updating and functionality checking accordingly. The information and instructions below apply to these three tools only and can be found inside the full Intel TXE System Tools Packages.
TXEInfo: Shows (CS)TXE and IUP info and checks that the Engine co-processor is operating properly on the software/firmware level. Make sure it doesn't report any errors. You can use "-verbose" parameter to get status info in more detail. The "GBE Region does not exist" warning is normal for systems that don't have an Intel GbE Controller, you can safely ignore it.
TXEManuf: Diagnostic tool which runs various manufacturing-line tests to ensure that the Engine co-processor is operating properly on the hardware level. It should report a "TXEManuf Operation Passed" or similar success message. You can use "-verbose" parameter to get diagnostic info in more detail.
FWUpdate: Used to effortlessly upgrade or downgrade the TXE 1 & 2 Engine firmware. Read more about FWUpdate tool at Section B.
C2. (CS)TXE System Tools
Note: To extract the files below you need to use programs which support RAR5 compression!
-
CSTXE System Tools v4
For CSTXE v4 -
CSTXE System Tools v3
For CSTXE v3 -
TXE System Tools v2
For TXE v2 -
TXE System Tools v1
For TXE v1